Users & security | RS Pathfinder
What is the Users page?
The Users page allows administrators to manage individual user accounts, including creating, editing, and deleting accounts. It provides detailed control over user-specific settings, permissions, and roles within the Remote Support environment.
How is the Users page useful to my organization?
The Users page enables administrators to customize access and permissions for each user, ensuring security and proper role alignment. It also allows for efficient user management, helping to maintain compliance and support operational needs.
How do I access the Users page?
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - From the left menu, click Remote Support > Users & Security.
The Users page displays.
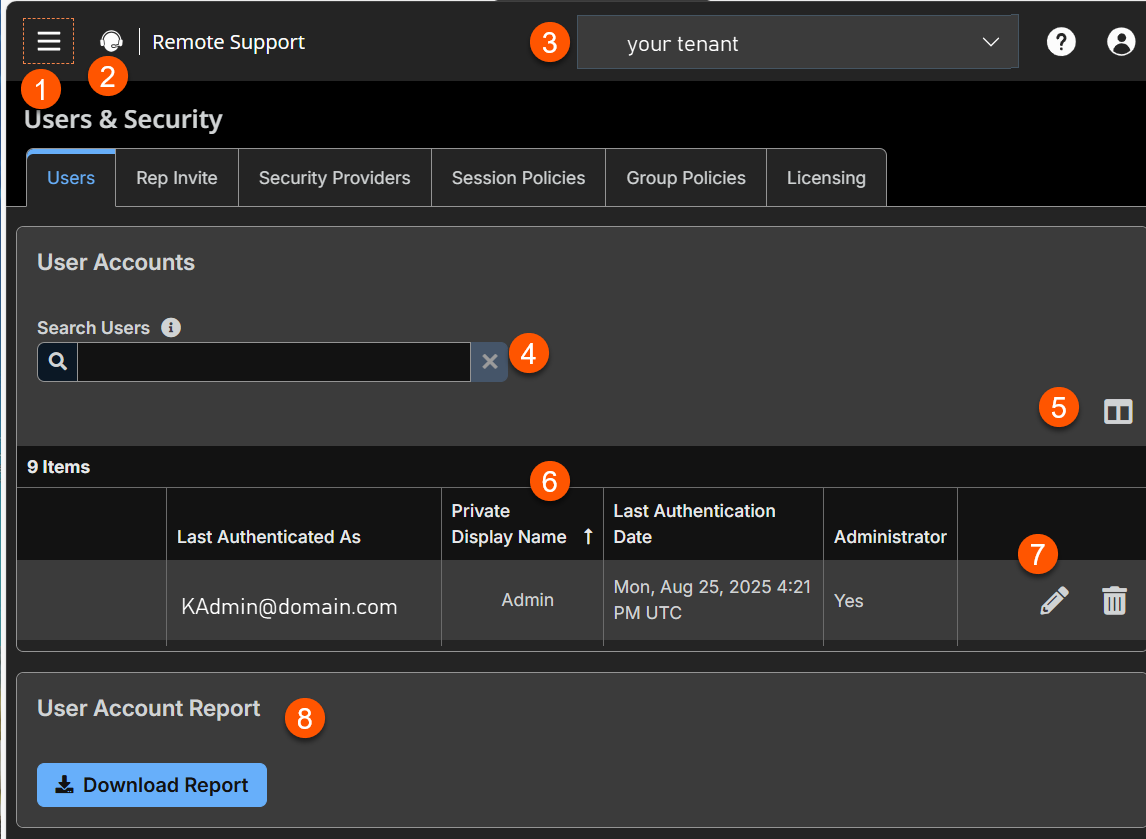
- Left menu: Easy access to all pages in Remote Support, including Status, Consoles & Downloads, My Account, Configuration, Jump, Vault, Console Settings, Users & Security, Reports, Public Portals, Dashboards, Management, and Appliance pages.
- Status: Opens the Status page.
- Header: Change your tenant site, manage your profile, and access documentation.
-
Filter: Search users based on Last Authenticated As, Display Name or Email Address.
-
Hide columns: Option to hide/display columns.
-
Users columns: The list of Users columns. Not all of the columns are displayed.
Users columns
- Last Authenticated As: The name of the user in the form of [email protected].
- Display Name: The full name of the account. For example, "John Smith".
- Last Authentication Date: The last date the user logged on.
- Administrator: Defines whether the user is an administrator which is defined in General Permission section of the Users & Security > Group Policies page. The value of the column is Yes or No.
-
Download Report: Generate a report for user accounts.
User accounts
This page is changed in Pathfinder. You can still search for users, edit the users, and obtain a user account report on the Users page. However, the ability to add new users and synchronize the users and groups associated with an external security provider is removed. There is now a single point of user management for all products hosted on Pathfinder. This is performed on the User Management page.
How to add, edit, or delete a user from Pathfinder
How to manage users
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Sign into the Administration tenant located in the upper-right hand corner with administrative permission.
- Click the hamburger menu
 in the upper left-hand corner of the window.
in the upper left-hand corner of the window. - In the User Administration section, click User Management.
The Organization Users page displays.
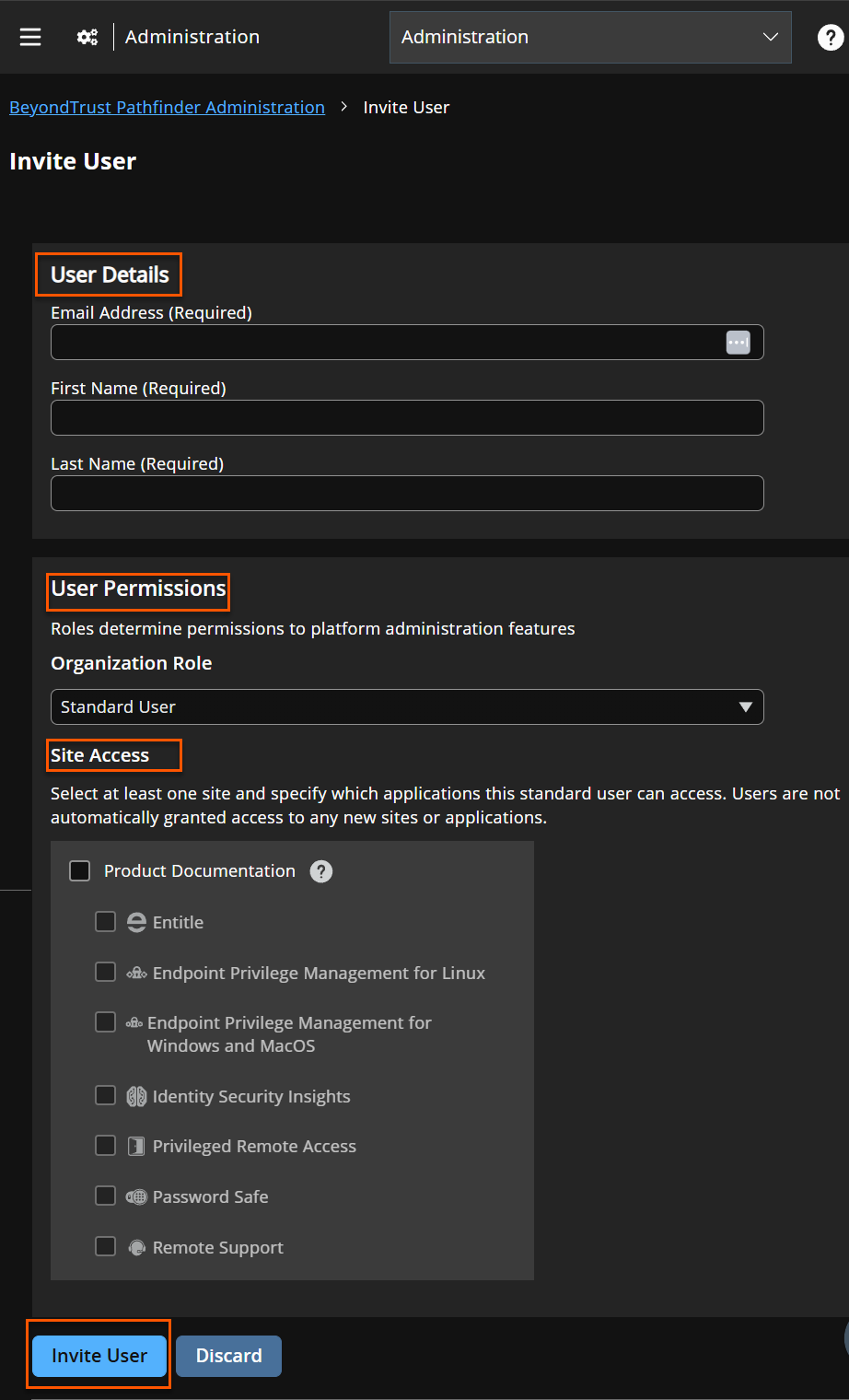
Add a new user
-
Click Invite User.
-
In User Details section, enter an Email Address, First Name, and Last Name. All fields are required.
-
In the User Permissions section, for Organization Role, select either Standard User or Administrator.
-
For Site Access, select the site(s) and at least one application you wish to grant user access to.
-
Click Invite User.
Edit a user
- From the list of users, click the ellipsis
 .
. - Click Edit User.
- Make the necessary changes, and then click Save Changes.
Delete a user
- From the list of users, click the ellipsis
 .
. - Click Delete User.
How to manage users in Remote Support
Search users
Search for a specific user account based on username, display name, or email address.
User account report
At the bottom of the page, export detailed information about your users for auditing purposes. Gather detailed information for all users, users from a specific security provider, or just local users. Information collected includes group policy and team memberships and permissions.
User settings
Memberships
Group policy memberships: Listing of the group policies to which the user belongs. This section allows you to search or select from a dropdown of Available Group Policies, and Add the policy to the user. Policies selected for the user display in a list which can be filtered. The user can be removed from one or more group policies by selecting the policy or policies and clicking Remove. The default policy cannot be selected. Unsaved changes to the list are identified as Addition or Removal. Changes can be undone by selecting the policy or policies and clicking Undo. If the user is a member of multiple group policies, the priority of the policies can be modified by selecting one or more policies and clicking Priority, at the upper right of the list. Group policies selected for a user can be edited by clicking the name of the policy in the list.
Other memberships do not display while a new user is being created. Once the new user has been saved, the other memberships appear, listing any to which the user may have been added, with links for updating these memberships and for reviewing or editing details about the memberships. See Edit a user for information on other memberships
Account settings
- Two factor authentication: log in with an authenticator app Select whether the user is required to log in using an authenticator app, or has the option to do so (default setting). If Required is selected, the next time the user tries to login to either the administrative interface or the representative console, a screen displays requiring the activation of two-factor authentication.
For more information on 2FA, see Two-factor authentication guide.
- Account never expires: If this option is selected, the account never expires.
- Account expiration date: Causes the account to expire on a given date.
- Account disabled: Disables the account so the user cannot log in. Disabling does NOT delete the account.
- Allowed to change their display names: Enables users to change their display names.
- Allowed to change their photo Enables users to change their avatar photos, which display on the /login administrative interface and in the customer client chat window.
- Allowed to show on public site: Displays the user's name on all public sites that have the representative list enabled.
- Comments: Add comments to help identify the purpose of this account.
- Passwordless authenticators: Listing of the passwordless authenticators registered for this user. Admins can view the name, type, registration timestamp, and last used timestamp. Admins can remove one or more authenticators from this list.
General permissions
- Administration
- Administrator: Grants the user full administrative rights.
- Allowed to administer Vault: Enables the user to manage all aspects of the BeyondTrust Vault add-on.
- Allowed to set passwords: Enables the user to set passwords and unlock accounts for non-administrative local users.
- Allowed to edit Jumpoints: Enables the user to create or edit Jumpoints. This option does not affect the user's ability to access remote computers via Jumpoint, which is configured per Jumpoint or group policy.
- Allowed to edit public site: Enables the user to create and modify public site configurations, edit HTML templates, view the translation interface, etc.
- Allowed to edit customer notices: Enables the user to create and edit messages used to notify customers, as they are requesting support, of broadly impacting IT outages.
- Allowed to edit file store: Enables the user to add or remove files from the file store.
- Allowed to edit canned messages: Enables the user to create or edit canned chat messages.
- Allowed to edit support teams: Enables the user to create or edit support teams.
- Allowed to edit Jump Groups: Enables the user to create or edit Jump Groups.
- Allowed to edit issues: Enables the user to create and edit issues.
- Allowed to edit skills : Enables the user to create and edit skills.
- Allowed to edit Support Button profiles: Enables the user to customize Support Button profiles.
- Allowed to edit canned scripts: Enables the user to create or edit canned scripts for use in screen sharing or command shell sessions.
- Allowed to edit custom rep links: Enables the user to create or edit custom links.
- Allowed to edit iOS profiles: Enables the user to create, edit and upload Apple iOS Profile content for distribution to iOS device users.
- Allowed to Edit Group Policy Memberships: Enables users to add or remove group policies for non-administrative users for the selected group policy.
Policies with administrative or add/remove group policy memberships permissions are not available. Administrators have access to all group policies.
- Reporting
- Allowed to view support session reports: Enables the user to run reports on support session activity, viewing only sessions in which they were the primary representative, only sessions in which one of their teams was the primary team or one of their teammates was the primary representative, or all sessions.
- Allowed to view support session recordings: Enables the user to view video recordings of screen sharing sessions and command shell sessions.
- Allowed to view license usage reports: Enables the user to run reports on BeyondTrust license usage.
- Allowed to view syslog reports: Enables the user to download a ZIP file containing all syslog files available on the appliance. Admins automatically have permissions to access this report. Non-admin users must request access to view this report.
- Allowed to view Vault reports: Enables the user to run reports on Vault activity, viewing all event data or only their event data.
Representative permissions
-
Allowed to provide remote support: Enables the user to use the representative console in order to run support sessions. If support is enabled, options pertaining to remote support will also be available. Disable this setting for presentation-only users.
-
Session management
-
Allowed to generate session keys for support sessions within the representative console: Enables the user to generate session keys to allow customers to start sessions with them directly.
For more information, see Generate a session key.
-
Allowed to generate access keys for sending iOS profiles: Enables the user to generate access keys to offer iOS content to iOS device users.
For more information, see iOS profile access key.
-
Allowed to manually accept sessions from a team queue: Enables the user to select and start sessions that are in one of their team queues.
For more information, see Accept a session to start support.
-
Allowed to transfer sessions to teams which they do not belong to: Enables the user to transfer sessions to teams other than their own. If disabled, user interaction is restricted solely to the user's assigned teams.
-
Allowed to share sessions with teams which they do not belong to: Enables the user to invite a less limited set of user to share sessions, not only their team members. Combined with the extended availability permission, this permission expands session sharing capabilities.
For more information, see Session tools.
-
Allowed to invite external support representatives: Enables the user to invite third-party users to participate in a support session, for the duration of that session only.
For more information, see Rep invite.
-
Remove representative from session after inactivity: Sets how long a session stays assigned to an inactive representative.
-
Allowed to use the get next session feature: Enables the user to start supporting the oldest queued session from all of their teams simply by clicking a button.
For more information, see Accept a session to start support.
-
Allowed to enable extended availability mode: Enables the user to receive email invitations from other users requesting to share a session even when they are not logged into the representative console.
For more information, see Extended availability .
-
Allowed to edit the external key: Enables the user to modify the external key from the session info pane of a session within the representative console.
For more information, see Session tools.
-
-
Equilibrium
- Allowed to opt out of session assignments: Enables the representative to mark himself or herself as unavailable for sessions to be assigned using Equilibrium.
- Do not assign sessions if the representative is participating in at least: Sets the least number of sessions the representative must be supporting before sessions will no longer be automatically assigned using Equilibrium.
- Do not assign sessions if the representative has been idle for at least: Sets the least amount of time the representative must have been idle before sessions will no longer be automatically assigned using Equilibrium.
For more information, see Equilibrium guide .
- Rep to rep screen sharing
- Allowed to show screen to other representatives: Enables the user to share their screen with another user without the receiving user having to join a session. This option is available even if the user is not in a session.
- Allowed to give control when showing screen to other representatives: Enables the user sharing their screen to give keyboard and mouse control to the user viewing their screen.
For more information, see Rep-to-rep screen share.
-
Legacy Support Buttons
These permissions only affect Legacy Support Buttons and will be removed in a future release. These permissions do not affect the user's ability to deploy a Jump Client with a Support Button profile selected.
- Allowed to deploy and manage Support Buttons in personal queue: Enables the user to deploy and manage personal Support Buttons. This setting affects deploying Support Buttons from both the web interface and the representative console. To deploy a Support Button from within a session, the Support Button Deployment session permission must also be allowed.
- Allowed to manage Team Support Buttons: Enable the user to modify the Support Buttons deployed to teams they are a member of. If the user is a team lead or manager, they can modify the personal Support Buttons of any team members as well.
- Allowed to change the public portal associated with Support Buttons: Enables the user to set the public portal through which a Support Button should connect. Because session policies may be applied to public portals, changing the portal may affect the permissions allowed in the session.
- Allowed to deploy team Support Buttons: Enables the user to deploy team Support Buttons for teams they are a member of. This setting affects deploying Support Buttons from both the web interface and the representative console. To deploy a Support Button from within a session, the Support Buttons Deployment session permission must also be allowed.
For more information, see
- Jump Technology
- Allowed Jump methods: Enables the user to Jump to computers using Jump Clients, Local Jump, Local VNC, Local RDP, Remote Jump, Remote VNC, Remote RDP, Shell Jump, and/or Intel vPro.
- Jump Item Roles: A Jump Item Role is a predefined set of permissions regarding Jump Item management and usage. For each option, click the Edit button to open the Jump Item Role in a new tab.
- The Default role is used only when Use User's Default is set for that user in a Jump Group.
- The Personal role applies only to Jump Items pinned to the user's personal list of Jump Items.
- The Teams role applies to Jump Items pinned to the personal list of Jump Items of a team member of a lower role. For example, a team manager can view team leads' and team members' personal Jump Items, and a team lead can view team members' personal Jump Items.
- The System role applies to all other Jump Items in the system. For most users, this should be set to No Access. If set to any other option, the user is added to Jump Groups to which they would not normally be assigned, and in the representative console, they can see non-team members' personal lists of Jump Items.
- The Endpoint automation role sets how a representative can use endpoint automation.
- Not allowed prevents them from seeing the Jump > Endpoint Automation tab altogether.
- A User can create new automation jobs with these restrictions:
- They are able to choose any existing Script Template but cannot edit the Script Template, Script Command, nor select or change the template accompanying Resources.
- The Script Template, Script Command, Operating System, and Resources fields are unavailable.
- They can run scripts only on Jump Items where their Jump Item Role includes the Start Sessions permission (set on the Jump > Jump Items Role page).
- An Administrator has full access and ability to create Jobs, Scripts Templates, and Resources.
For more information, see Jump Item Roles and Endpoint Automation.
- Representative console
- Idle timeout: Set how long the representative can be idle before being logged out of the representative console. This permission can use the site-wide setting or can override that setting.
Attended and unattended session permissions
-
Attended and unattended session policies
- Session policy: Set the prompting and permission rules that should apply to this user's sessions. Choose an existing session policy or define custom permissions for this user. If Not Defined, the global default policy will be used. These permissions may be overridden by a higher policy.
- Use the same permissions for unattended sessions: Enable to use the same permissions for both attended and unattended sessions. Disable to define attended and unattended permissions separately. You can also copy the permissions from one to the other.
- Description: View the description of a pre-defined session permission policy.
- Allow Elevated Access to Shells, Tools, and Special Actions on the Endpoint: Enable if desired, and if allowed by the Endpoint's platform.
-
Support tool prompting
For more information, see Desktop customer client user guide.
-
Prompting rules: Choose to ask the customer permission to use any of the support features below. Select No Prompting to never prompt, Always Prompt to always prompt, or Prompt for Some Tools to choose which permissions to prompt for. If Prompt for Some Tools is chosen, a Prompt Customer option will appear by each tool with the options to Never prompt or to Always prompt. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
-
Allowed to prompt once: If Screen Sharing: is set to View and Control and prompting is enabled, this option appears. Check the box to make the screen sharing prompt request access to all tools during the session, with no further prompts.
-
Prompting options: Set how long to wait for a response to a prompt before defaulting to the answer of Deny or Allow. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
-
Screen sharing
-
Screen sharing rules: Enable the user to view or control the remote screen. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
For more information, see Screen share.
-
Allowed to show their screen to the customer: Enables the user to share their screen with the customer during a support session. This option is available if View Only or View or Control is selected.
For more information, see Show my screen.
- Clipboard synchronization direction: This is option is available if View and Control is selected. Select how clipboard content flows between representatives and end users. The options are:
-
Not allowed: The representative is not allowed to use the clipboard, no clipboard icons display in the representative console, and cut and paste commands do not work.
-
Allowed from Rep to Customer: The representative can push clipboard content to the customer but cannot paste from the end user's clipboard. Only the Send clipboard icon displays in the representative console.
-
Allowed in Both Directions: Clipboard content can flow both ways. Both Push and Get clipboard icons display in the representative console.
-
For more information about the Clipboard Synchronization Mode, see Representative console on the Security page.
-
Allowed customer restrictions: Set if the user can suspend the remote system's mouse and keyboard input. The user may also prevent the remote desktop from being displayed. This is option is available if View and Control is selected. If Display, Mouse and Keyboard is the selected Customer Restriction, a check box is available to Automatically request a privacy screen on session start. Privacy screen is applicable only for sessions started from a Jump Client, a Remote Jump Item, or a Local Jump Item. We recommend using privacy screen for unattended sessions. The remote system must support privacy screen.
For more information, see Restricted customer interaction.
-
Application sharing prompt behavior: Set if a request for screen sharing should always or never prompt the customer to select applications to share, or if the user can choose whether to prompt for application sharing or not. Selecting Always or Rep Decides also allows you to predefine application sharing restrictions.
For more information, see Application sharing.
-
-
Annotations
- Annotation rules: Enables the user to use annotation tools to draw on the remote system's screen. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
For more information, see Annotations.
- File transfer
- File transfer rules: Enables the user to upload files to the remote system, download files from the remote system, or both. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
- Accessible paths on customer's filesystem: Allow the user to transfer files to or from any directories on the remote system or only specified directories.
- Accessible paths on representative's filesystem: Allow the user to transfer files to or from any directories on their local system or only specified directories.
For more information, see File transfer.
- Shell
- Shell rules: Enables the user to issue commands on the remote computer through a virtual command line interface. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
Shell access cannot be restricted for Shell Jump sessions.
For more information, see Command shell.
- System information
- System information rules: Enables the user to see system information about the remote computer. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
- Allowed to use system information actions: Enables the user to interact with processes and programs on the remote system without requiring screen sharing. Kill processes; start, stop, pause, resume, and restart services; and uninstall programs.
For more information, see System information.
- Registry access
- Registry access rules: Enables the user to interact with the registry on a remote Windows system without requiring screen sharing. View, add, delete and edit keys, search and import/export keys.
For more information, see Registry editor.
- Canned scripts
- Canned script rules: Enables the user to run canned scripts that have been created for their teams. Note that when the user is in view-only screen sharing, the customer receives a prompt to allow the script to run. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
For more information, see Command shell.
- Elevation
- Elevation rules: Enables the user to attempt to elevate the customer client to run with administrative rights on the remote system. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
For more information, see Elevate the customer client.
- Jump Clients pinning/unpinning
- Jump Clients pinning/unpinning rules: Enables the user to pin or unpin a Jump Client while in a session. Locations available for deployment depend on the Jump Client settings above. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
For more information, see Session tools.
- Chat
- Chat rules: Enables the user to chat with the remote customer. If Not Defined, this option will be set by the next lower priority policy. This setting may be overridden by a higher priority policy.
- Allowed to push URLs to the customer's web browser: Enables the user to enter a URL into the chat area and then click the Push URL button to automatically open a web browser to that address on the remote computer.
- Allowed to send files using the chat interface: Enables the user to send files via the chat interface.
For more information,
- Session termination behavior
- When the session ends, automatically: If unable to reconnect within the time you set by Reconnect Timeout, choose what action to take. To prevent an end-user from accessing unauthorized privileges after an elevated session, set the client to automatically log the end user out of the remote Windows computer at session end, to lock the remote computer, or to do nothing. These rules do not apply to browser sharing sessions.
- Allow users to override this setting per session: You can allow a user to override the session termination setting from the Summary tab in the console during a session.
Availability settings
- Full support license pool: Choose the license pool to which this representative should belong. When this representative logs into the representative console, a license is consumed from the designated license pool. If None is selected, the representative will be able to log in to the representative console only if one or more licenses are left unassigned to license pools and are available.
- Skills: Designates the skills assigned to this user. When using skills match for Equilibrium, sessions will be assigned to the user best skilled to handle a particular issue.
For more information, see Assign skills to reps.
- Login schedule
- Restrict representative log in to the following schedule: Set a schedule to define when users can log in to the representative console. Set the time zone you want to use for this schedule, and then add one or more schedule entries. For each entry, set the start day and time and the end day and time. If, for instance, the time is set to start at 8 am and end at 5 pm, a user can log in at any time during this window but may continue to work past the set end time. They will not, however, be allowed to log back in after 5 pm.
- Force logout when the schedule does not permit login: If stricter access control is required, check this option. This forces the user to log out at the scheduled end time. In this case, the user receives recurring notifications beginning 15 minutes prior to being disconnected. When the user is logged out, any owned sessions will follow the session fallback rules.
Updated 7 days ago
