Jumpoint | RS Cloud
What is a Jumpoint?
A Jumpoint is a secure connection point used in Remote Support to facilitate access to remote systems without requiring direct public internet exposure, enabling secure, controlled remote sessions.
How is a Jumpoint useful in Remote Support?
A Jumpoint allows administrators to securely manage remote connections through internal networks or firewalls, ensuring protected access to remote systems while maintaining network security. BeyondTrust's Jump Technology enables a user to access computers on a remote network without having to pre-install software on every machine. Simply install a single Jumpoint agent at any network location to gain unattended access to every PC within that network.
How do I access the Jumpoint page?
- Use a Chromium-based browser to sign in to your Remote Support Cloud URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click Jump.
The Jump Clients page opens and displays by default. - At the top of the page, click Jumpoint.
The Jumpoint page displays.
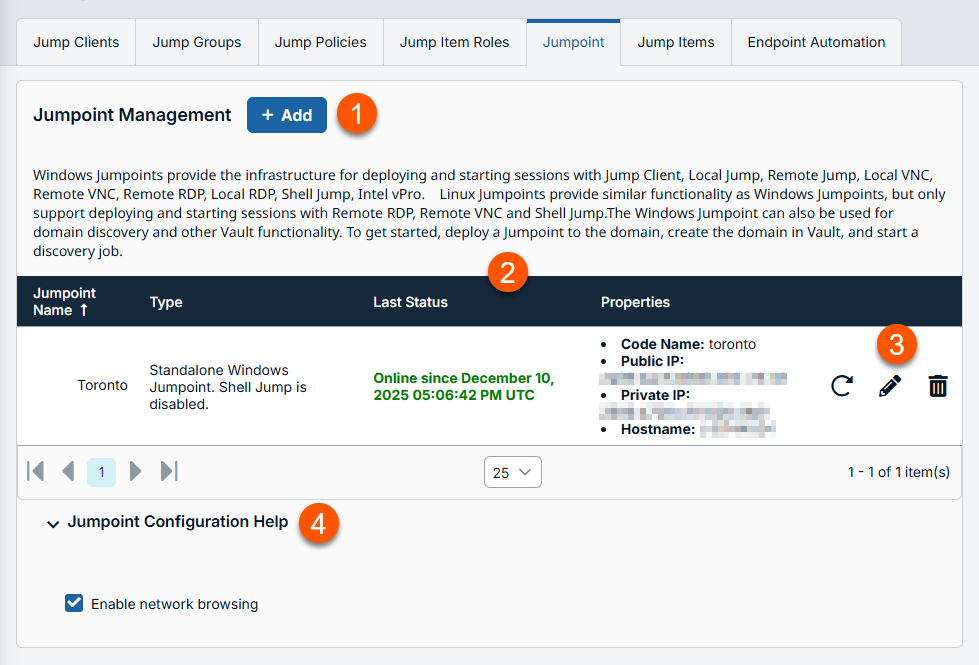
- Add: Adds a Jumpoint.
- Jumpoint columns: List Jumpoint columns.
Jumpoint columns
- Jumpoint Name: Unique name of the Jumpoint.
- Type: Displays the settings of the Jumpoint.
- Last Status: Displays the status in date and time of the Jumpoint.
- Properties: Displays the detailed information of the Jumpoint. For example, Hostname and IP addresses .
Jumpoint Management
BeyondTrust's Jump Technology enables a user to access computers on a remote network without having to pre-install software on every computer.
A Jumpoint allows a user to upload the Privileged Remote Access Endpoint Client software to computers on remote networks. The networks a Jumpoint provides access to are collectively called a Jump Zone.
TipWhen you select a system to host a Jumpoint, keep the following criteria in mind:
- The host system should be a system on the same local area network as the systems to which you wish to Jump.
- The host system should be a system with high availability.
The host system should not be a system already being used as a server. File servers, print servers, web server, email servers, etc. all make poor choices for Jumpoint host systems.
Jumpoints attempt to close any active network connections to the target system before attempting the Jump, for security purposes. A Jumpoint that coexists on such a server often reports "Network error disconnecting from host" messages when attempting to Jump, as it attempts to close a network connection but fails to do so because some other software is actively using that network connection.
Add new Jumpoint
-
From the top of the page, click Add.
The Add Jumpoint page displays. -
In the Name field, create a unique name to help identify this Jumpoint. This name should help users locate this Jumpoint when they need to start a session with a computer on its same network.
-
In the Code name field, create a code name for integration purposes. If you do not set a code name, one is created automatically.
-
In the Comments field, add comments to help identify the purpose of this Jumpoint.
-
In the Jumpoint Platform section, select either Windows or Linux as the operating system, and whether the Jumpoint is clustered or not. If Clustered is checked, you are able to add multiple, redundant nodes of the same Jumpoint on different host systems. This ensures that as long as at least one node remains online, the Jumpoint is available.
Important infoOnce the Jumpoint has been created, this option cannot be changed.
-
In the Disabled field, set this field to make the Jumpoint unavailable to make Jump connections. A disabled Jumpoint may still connect to the appliance, but is not usable by any users to perform Jump operations.
-
If you want users to be able to connect to SSH-enabled and Telnet-enabled network devices through this Jumpoint, set the Enable Jump Shell Jump Method checkbox.
-
If the Enable Protocol Tunnel Jump Method option is checked, users may make connections from their systems to remote endpoints through these types of Jumpoint.
If Network Tunnel Jump is enabled on your system, and the Enable Protocol Tunnel Jump Method is checked, there is an option to enter Managed IP Addresses for Protocol Tunnel Jump. You can enter multiple IP address ranges via Start IP and End IP fields. This allows using the Network Tunnel feature on networks without DHCP.
-
Under RDP Service Account, select the vault account to be used by the Jumpoint to run a user-initiated client on the RDP server. This lets you to collect additional event information from an RDP session started with this Jumpoint.
This account in used only if the Remote RDP Jump Item is configured to enable the Session Forensics functionality. This option is not available for Linux Jumpoints.
The RDP Service Account setting must not use a local admin account, and must use a domain admin account with privileges on the endpoint including access to remotely connect to the endpoint's C$ share, remotely create and start services on the endpoint machine, and access remote file systems.
For more information, see Remote Desktop Protocol shortcuts.
-
Check Enable Jump Zone Proxy to set up a Jumpoint to function as a proxy server. This allows it to proxy connections for Jump Items on the network that do not have a native internet connection, such as POS systems.
Using a Jumpoint as a proxy routes traffic only to the Appliance.
You can enable Jump Zone Proxy on either a standalone Jumpoint or a Jumpoint cluster. If you set up a Jumpoint cluster as a Jump Zone Proxy and an endpoint is connected to one Jump Zone Proxy, if that system goes down, the endpoint can connect to another Jump Zone Proxy in the cluster. Jump Zone Proxies are not supported for Atlas deployments.
-
Under Proxy Host, type the hostname of the computer on which this Jumpoint is to be installed.
The hostname should not start with http://or https://. IP addresses are not recommended as they might change. The Jumpoint automatically detects the hostname if one is not provided. If this is a clustered Jumpoint, this field does not appear, and the Jumpoint automatically detects the hostname on install. If the hostname changes, you may have to redeploy any Jump Items that use this Jumpoint as a proxy.
The proxy host and port should be set carefully since any Jump Item deployed using this Jumpoint as a proxy server uses the settings available to it at the time of deployment and are not updated should the host or port change. If the host or port is changed, the Jump Item must be redeployed.
In order for a Jumpoint to function as a Jump Zone Proxy, its host system cannot reside behind a proxy. The Jumpoint must be able to access the internet without having to supply proxy information for its own connection.
-
Under Proxy Port, type the port through which Jump Items connect to this Jumpoint. If the port changes, you may have to redeploy any Jump Items that use this Jumpoint as a proxy.
It is a best practice to make an exception in the Windows firewall for the port on which the proxy server listens for the process to accept connections.
-
Check Allow HTTP GET to enable HTTP connections to proxy to the Appliance. This is needed only if you want to use a browser to access Remote Support for Admins from behind the proxy.
-
Under Network restrictions > Restriction Type, set a network restriction for Jump connections using the following values:
Name Description No access restriction Lets Jump Item connections from any IP address. Deny access only for the following IP addresses Denies access to a connection by adding network address prefixes. Allow access only from the following IP addresses Limits the allowed connection by adding network address prefixes.
Netmasks are optional, and they can be given in either dotted-decimal or integer bitmask format. Entries that omit a netmask are assumed to be single IP addresses.
Group policies
This displays a listing of the group policies which allow users access to this Jumpoint. You can create Jumpoint memberships on the Users & Security > Group Policies page.
Allowed Users
You can configure allowed users for the group by doing the following steps:
- To add a user, search in New Member Name for users to add to this Jump Group.
- Select the user's role in the New Member Role dropdown to set their permissions specific to Jump Items in this Jump Group.
- You can select User's default to use the default Jump Item Roles set on the Users & Security > Group Policies page or the Users & Security > Users page. A Jump Item Role is a predefined set of permissions regarding Jump Item management and usage.
- In the New Member Jump Policy field, select the appropriate policy.
- Click Add.
- Existing Jump Group users are shown in the table, along with their assigned role and how the role was granted. You can filter the view by entering a string in the Filter by name text box.
- To edit a user's settings, click
 or to delete a user from the Jump Group, click
or to delete a user from the Jump Group, click  .
.
The edit and delete functionality may be disabled for some users. This occurs either when a user is added by using a group policy or when a user's system Jump Item Role is set to anything other than the No Access permission.
You can click the group policy link to modify the policy as a whole. Any changes made to the group policy apply to all members of that group policy.
To add groups of users to a Jump Group, go to the Users & Security > Group Policies page and assign that group to one or more Jump Groups.
You can click the user link to modify the user's system Jump Item role. Any changes to the user's system Jump Item role apply to all other Jump Groups in which the user is an unassigned member.
You also can add the individual to the group, overriding their settings as defined elsewhere
Edit a Jumpoint
- Find the Jumpoint you want to edit from the list, then click Edit
 .
. - Makes your changes, then click Save.
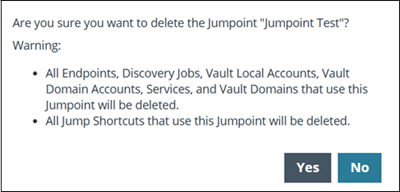
Delete a Jumpoint
-
Find the Jumpoint you want to remove from the list, then click Delete
 .
. -
The following message displays:
-
Click Yes.
Redeploy a Jumpoint
-
Select a Jumpoint from the list, then click the Redeploy button
 .
.
The following message displays: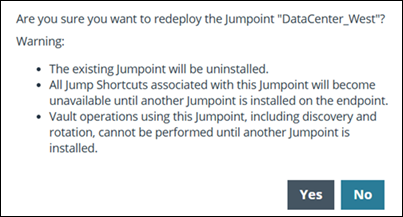
-
Click Yes.
Updated 15 days ago
