Secret store | RS Pathfinder
What is the Secret Store page?
The Secret Store page in the appliance web interface allows you to securely manage and store encryption keys required for encrypting session data and other sensitive information on the appliance.
How is it useful to my organization?
This page enhances security by providing a centralized, encrypted repository for managing keys, ensuring data protection and compliance with security standards.
How do I access the Secret Store page?
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - From the main menu, click Remote Access > Appliance.
The Appliance page opens in a new tab, and the Status page displays by default. - At the top, click Security.
The Security page opens and the Certificates tab displays by default. - Click Secret Store.
The Secret Store page displays.
The Secret Store page
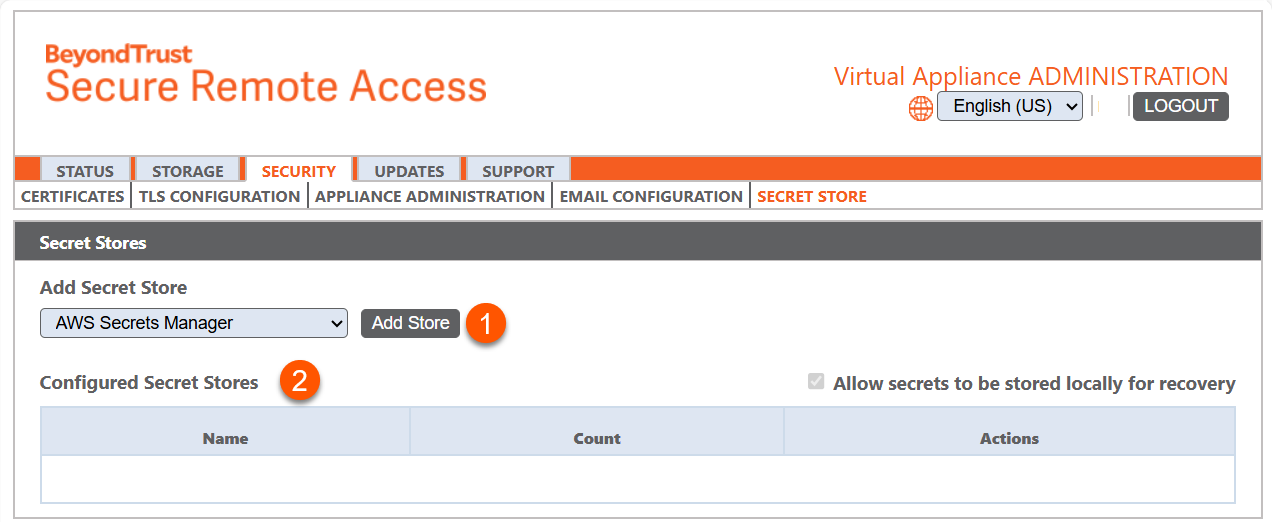
- Add Store: Adds a secret store.
- Secret Store list columns- The list of Secret Stores columns.
Secret Stores columns
-
Name: Unique name of the secret store.
-
Count: The number of the secret stores.
-
Actions: Displays status of the secret store.
-
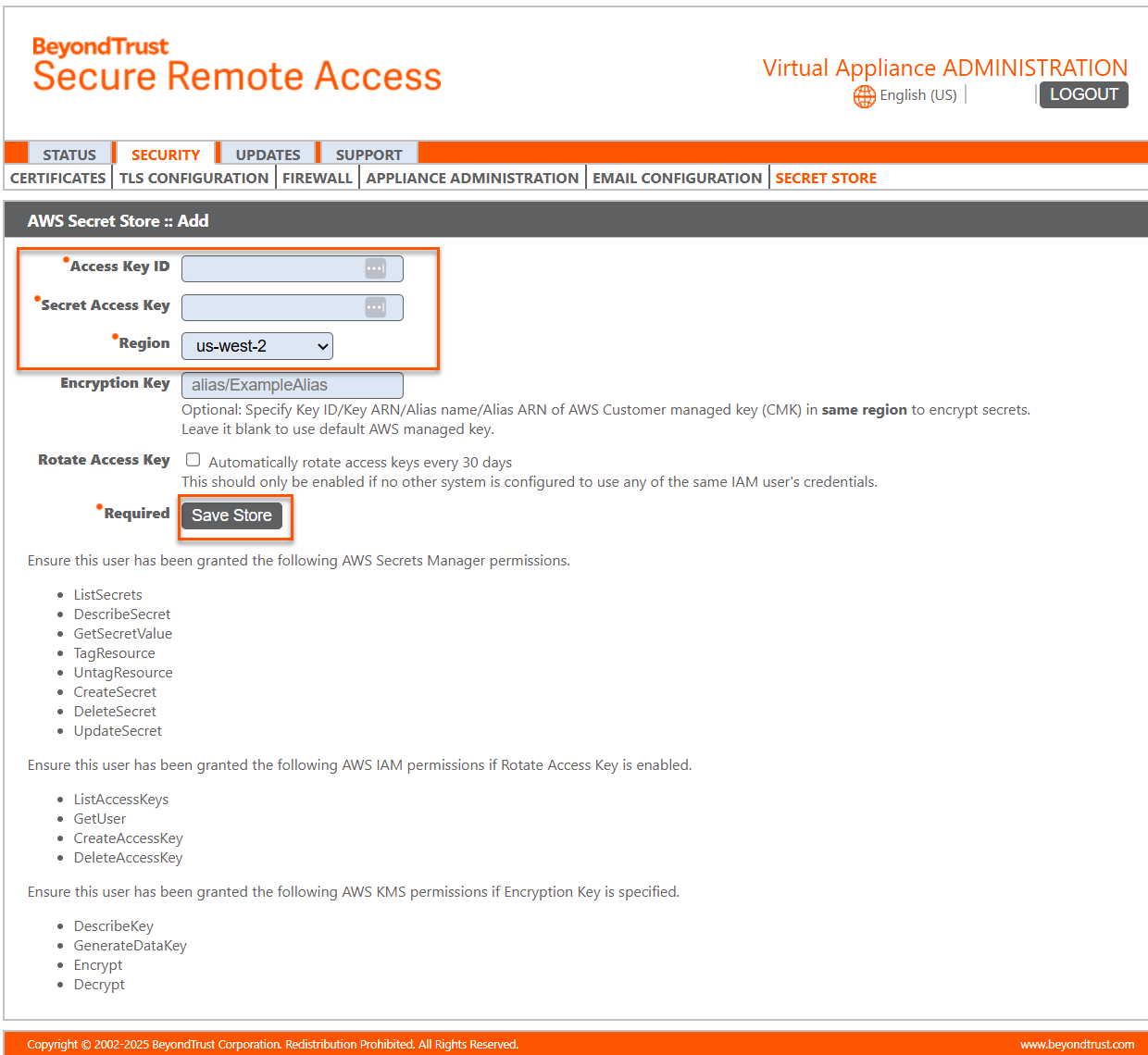
Add AWS Secret Store
Create and manage secret keys stored in AWS to securely store encryption keys and site data.
- To add a secret store, select the store from the dropdown, and then click Add Store.
- Provide the Access Key ID, Secret Access Key, and Region.
- Check the Rotate Access Key box only if you are not using any of the same IAM user's credentials in any other system.
- Click Save Store.
- It is also necessary for any firewall to allow outbound traffic to the IP addresses associated with the region endpoint used for the secret store.
- IP addresses may change. see the current list of IP addresses.
- For the list of endpoints, see AWS Secrets Manager endpoints and quotas.
- For added security, configure your AWS Identity and Access Management (IAM) Policy to limit access to resources matching BeyondTrust-* on the following permissions:
- DescribeSecret
- GetSecretValue
- TagResource
- UntagResource
- CreateSecret
- DeleteSecret
- UpdateSecret
For more information on managing AWS IAM Policies, see Managing IAM Policies.- If you delete the last remote store, a message displays indicating secrets will be moved locally.
Updated 15 days ago
