SAML | RS On-prem
What is SAML in the B Series Appliance?
SAML (Security Assertion Markup Language) in the B Series Appliance /appliance web interface enables Single Sign-On (SSO) authentication. It allows users to log in once using their organization’s identity provider (IdP) instead of managing separate credentials for the B Series Appliance. By integrating with an external IdP, the B Series Appliance supports secure, centralized access control and simplifies the authentication process.
How is it useful to my organization?
Using SAML for authentication streamlines the login process, improving security and reducing the need for multiple passwords. It ensures that user credentials are managed centrally, simplifying user administration. Organizations can also enforce more robust authentication policies through their IdP, helping meet security and compliance requirements while improving the overall user experience.
To use SAML authentication, you must have an identity provider such as Okta, OneLogin, Microsoft Entra ID, or ADFS.
How do I access the SAML page?
- Use a Chromium-based browser to sign in to your B Series Appliance. The URL is provided in the BeyondTrust welcome email and includes your site URL followed by /appliance.
- From the top menu, click Users.
The Users page opens and displays by default. - At the top of the page, click SAML.
The SAML page displays.
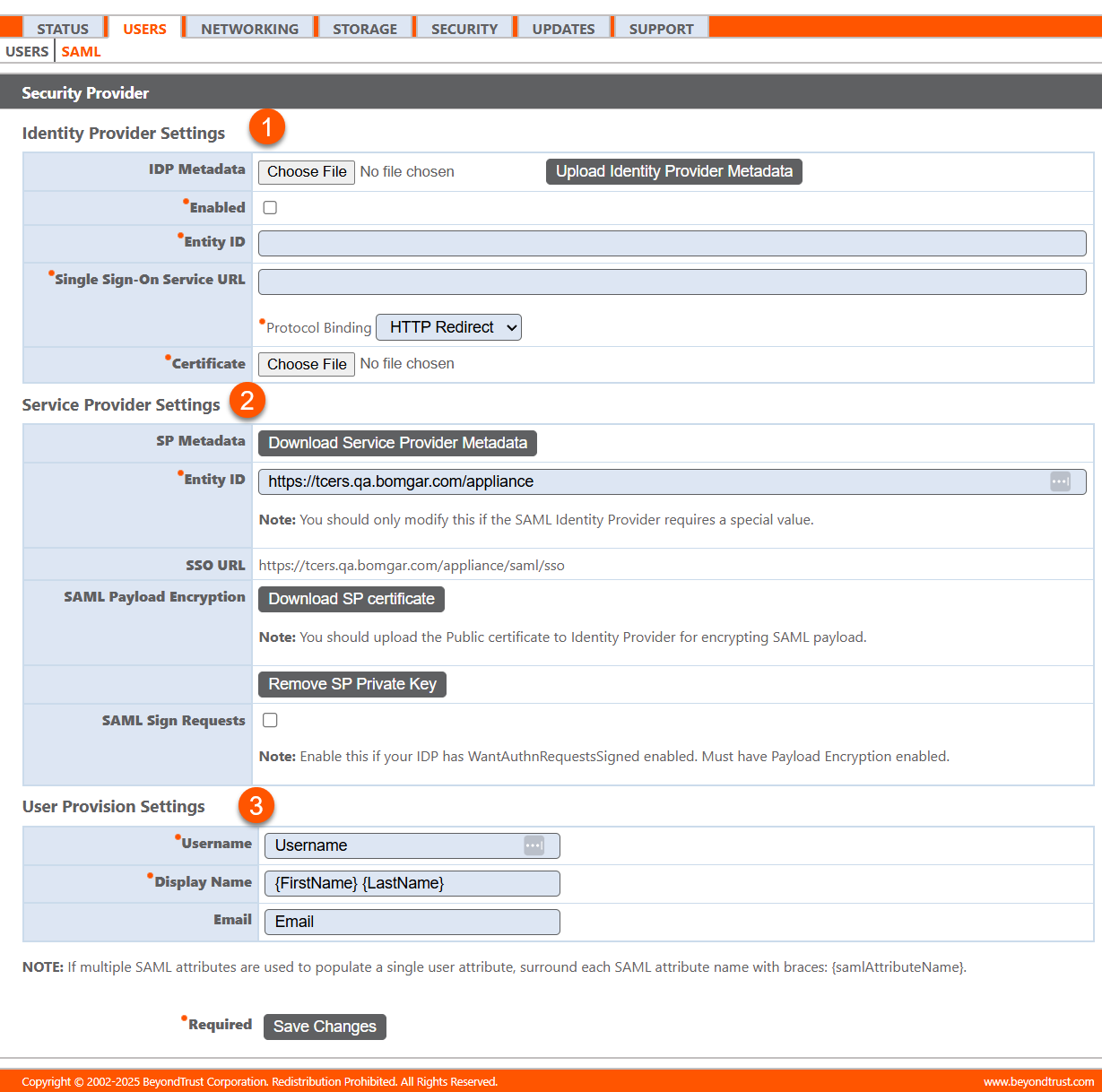
- Identity Provider Settings: Configure an Identity Provider.
- Service Provider Settings: Configure settings for a service provider.
- User Provision Settings: Configure settings for a user provision.
Configure SAML for the B Series Appliance
Identity provider settings
- IDP metadata: If available from your identity provider (IDP), upload the XML file containing configuration details required for SAML integration.
This automatically fills in the Entity ID and Single sign-on service URL fields.
The Entity ID may be called Audience URI in your identity provider.
- Enabled: Activate or deactivate SAML authentication for user logins.
- Entity ID: The unique identifier assigned to the identity provider in the SAML configuration.
- Single sign-on service URL: The URL used by the identity provider to handle authentication requests from the appliance.
- Protocol binding: The communication method used to send authentication requests and responses between the appliance and the identity provider.
- Certificate: Upload a digital certificate to establish a secure connection between the B Series Appliance and the identity provider.
Service provider settings
- Download service provider metadata: Download the metadata file that includes information about the service provider's configuration for integration with the identity provider.
- Entity ID: The unique identifier for the service provider, used to identify the application within the SAML authentication process.
In your identity provider, Entity ID may be called Audience URI, Identity provider issuer, or Issuer URL.
- SSO URL: The URL used by the identity provider to initiate the single sign-on (SSO) process, directing users to authenticate.
In your identity provider, SSO URL may be called Single Sign-On Service URL or SAML 2.0 Endpoint.
- SAML payload encryption: Choose the encryption method for SAML payloads.
- None: Do not encrypt the payload. This is the default option.
- Generate private key: Automatically generate a private key for encryption.
When you click Save changes, the page refreshes to show a Download SP certificate button. Download the generated certificate, then upload it to your identity provider.
To remove this private key, click Remove SP private key. - Upload private key: Upload an existing private key to encrypt the payload.
Choose the certificate file and enter its password, if needed.
You must upload the same certificate to your identity provider.
- SAML sign requests: Check to enable signing of SAML authentication requests. Uncheck to stop signing them.
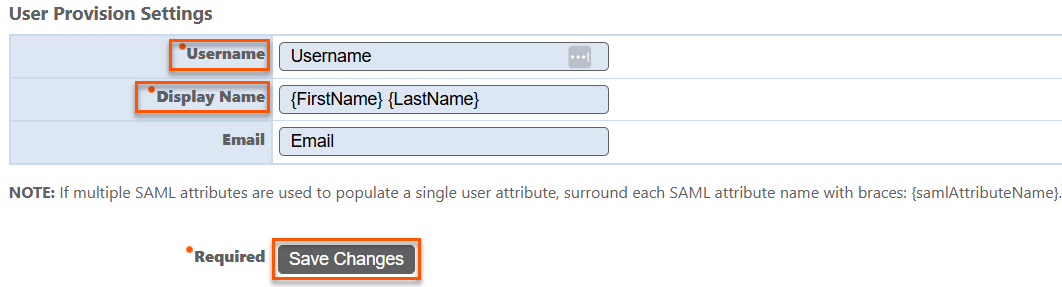
User provision settings
- Map the Username, Display Name, and Email to the corresponding attributes in your identity provider.
- Click Save Changes to save the SAML configuration.
Now, on the /appliance login page, users see a link to Use SAML Authentication below the Login button. Users who have been assigned to the application created in your IDP can click this link to log in. If they are not already signed into the IDP, they will be redirected to the IDP to log in before being redirected back to /appliance.
Updated 16 days ago
