JUMPOINT GUIDE | RS
What is Jump technology?
With BeyondTrust Jump Technology, authorized users can securely access and control remote computers, attended and unattended, as well as switches and other network devices in any network. Jump Technology is integral to the BeyondTrust software offerings. All sessions are logged for reporting and auditing. Because BeyondTrust Remote Support is licensed per active representative and not per remote system, Jump Technology is a cost-effective way to reach every device in your enterprise.
What is a Jumpoint?
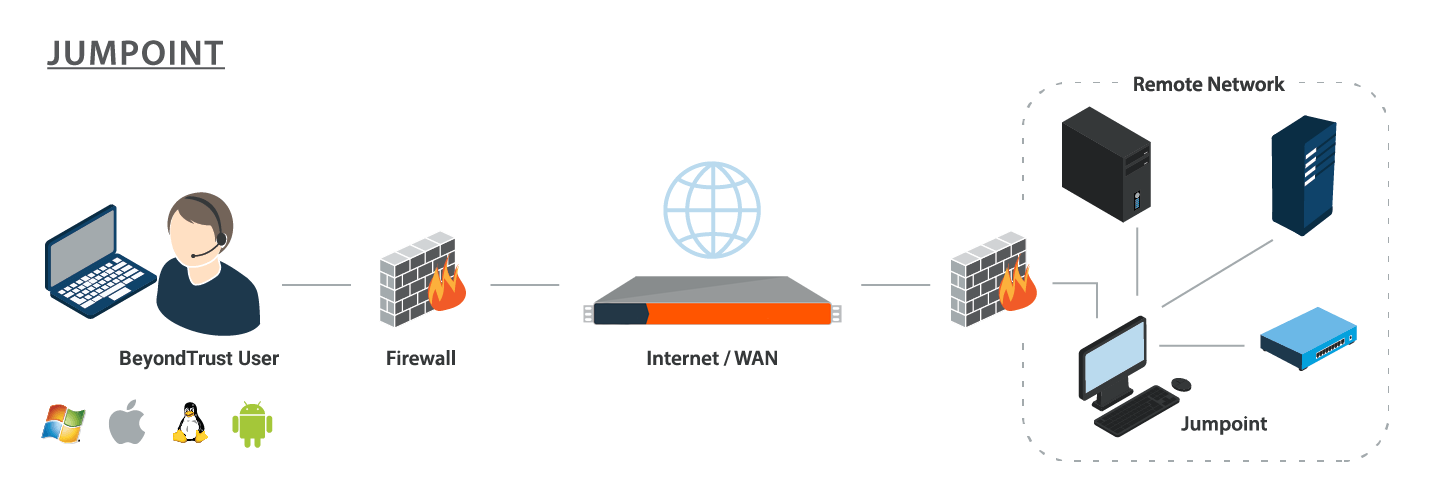
A Jumpoint acts as a conduit for access to computers on a known remote network. A single Jumpoint installed on a computer within a LAN is used to access multiple systems, eliminating the need to pre-install software on every computer you might need to access.
How are Jumpoints and Jump technology useful?
Within a LAN, the BeyondTrust user's computer can initiate a session to a system directly without using a Jumpoint, if appropriate user permissions are enabled. This is called a Local Jump. A Jumpoint is needed only for a Remote Jump when the BeyondTrust user's computer cannot access the target computer directly.
For more information on Jump Items for mobile devices, see the following:
- Use Jump Shortcuts to Access Unattended Computers from the Android Representative Console
- Use Jump Clients to Access Unattended Computers from the Android Representative Console
- Use Jump Shortcuts to Access Unattended Computers from the iOS Representative Console
- Use Jump Clients to Access Unattended Computers from the iOS Representative Console
Recommended steps for implementing BeyondTrust Jumpoints
When working with Jump Technology, there are a lot of moving parts. Here is a recommended order of implementation to make full use of your software.
- Add Jump Item Roles. Jump Item Roles determine how users are allowed to interact with Jump Items. These roles are applied to users by means of individual account settings, group policies, and when added to Jump Groups.
- Add Jump Policies. Jump Policies are used to control when certain Jump Items can be accessed by implementing schedules. Jump Policies are applied to Jump Items upon creation and can be modified from the representative console.
- Add Jump Groups. A Jump Group is a way to organize Jump Items, granting members varying levels of access to those items. Users are assigned to Jump Groups either individually, by means of group policy.
- Deploy Jumpoints. A Jumpoint acts as a conduit for unattended access to computers on a known remote network. A Jumpoint is necessary to use Remote Jumps, Remote RDP, Remote VNC, Shell Jumps, and Intel® vPro sessions. Local Jumps, Local RDP, and Local VNC can be performed to systems on the same local network.
- Create Jump Shortcuts. A Jump Shortcut is a quick way to start sessions with frequently accessed remote systems. Jump Items are created from the representative console or are imported from /login > Jump > Jump Items. When creating or importing Jump Items, be sure to set the Jump Group and Jump Policy to determine who can access the Jump Item and with what restrictions.
Updated 13 days ago
