Approval workflows | Entitle Pathfinder
Overview
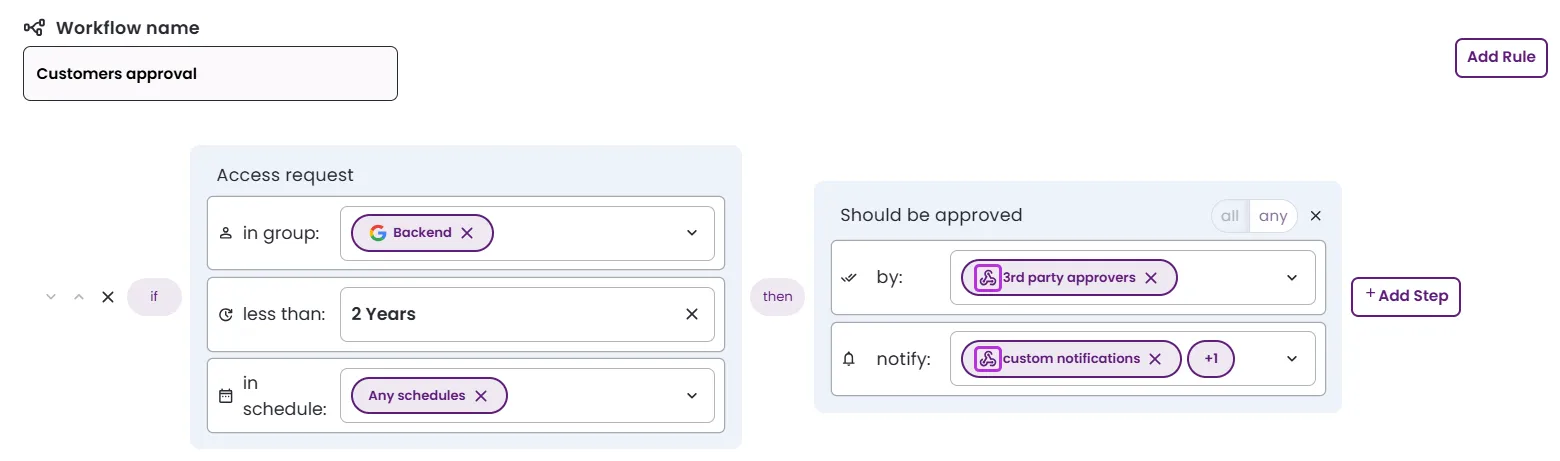
Approval workflows define the Just-in-Time (JIT) permissions approval process in Entitle. When a user requests access, the workflow determines whether approval is required, which conditions apply, who must approve, and how long access is granted. A single workflow can support multiple JIT components, including integrations, resources, roles, and bundles.
How approval workflows work
- Rules and evaluation: Each approval workflow contains one or more rules. Every rule includes:
- A condition (if) defines when the rule applies.
- An approval process (then) defines how the request is approved.
Rules are evaluated in order from top to bottom. The first rule whose condition is met determines the approval process for the request.
- Approval steps: The approval process inside a rule can include multiple steps, each representing an approver or approval action. Steps run sequentially. Each step can use one of two operators:
- Any: Any approver in the step may approve.
- All: All approvers in the step must approve.
Avoid assigning specifically named individuals when possible. Use managers, groups, roles, schedules, or other abstract approver types to ensure scalability.
Approver Types
Entitle includes several approver types you can use in workflow steps.
- Team member: Any user who shares the same manager as the requester. For requests made on behalf of another user, this refers to users sharing the manager of the user receiving access. If no direct manager exists, any Entitle admin may approve.
- Direct manager: The manager of the user requesting access. For requests made on behalf of another user, this refers to the manager of the user receiving access.
- Automatic Approval: The step is approved automatically, without human intervention.
- Resource maintainer / integration maintainer: A secondary administrator of the resource or integration. Multiple maintainers may be assigned, including IdP groups. For bundles, this means the maintainer of each included resource or integration.
- Resource owner / integration owner: The primary owner of a resource or integration. For bundles, this means the owner of each included resource or integration.
- Group: Any member of an IdP group at the time of request. If someone requests access on behalf of another user and belongs to the approval group, the step is automatically approved.
- Schedule: Any member of an on-call schedule or on-call group. If someone requests access on behalf of another user and is currently on-call, the step is automatically approved.
- Slack channel: Any member of a selected Slack channel. Channel members can approve or decline the request directly from Slack.
- Specific user: Any user in the tenant. Start typing to see available users.
- Webhook: Third-party code that acts as the approver.
For more information on webhooks, see Webhook-based approvals.
When using Team or Schedule approvers, only users currently on-call can request access. This design ensures that only active responders can request access.
To allow all schedules (not just on-call users) to request access, create a group containing all schedule members and use that group instead.
View and manage approval workflows
View role access to the Approval Workflows page
See which roles can perform each action.
ImportantThis page is accessible only to Super Admins, Tenant Admins, Admins, and Read-Only Admins.
| Actions | Super Admin | Tenant Admin | Admin | Read-Only Admin |
|---|---|---|---|---|
| Access approval by webhooks | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable |
| Create approval workflows | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Visible but deactivated: Action is shown but cannot be clicked |
| Search, sort, and filter | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable |
| Edit approval workflows | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Visible but deactivated: Action is shown but cannot be clicked |
| Delete approval workflows | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Visible but deactivated: Action is shown but cannot be clicked |
- Sign in to app.beyondtrust.io with your credentials. The BeyondTrust Pathfinder Home displays.
- At the top right of the page, select your site from the drop-down.
- Select the Entitle tile from your list of available applications.
- From the top left menu, select Approval workflows.
The Approval workflows page lists all existing workflows in your organization, including their name, approval steps, and the total number of roles and bundles associated with each.
This screen has four main functionalities:
- Edit and delete approval workflows
- Search, sort, and filter approval workflows
- Add a new approval workflow
- Set up webhook-based approvals
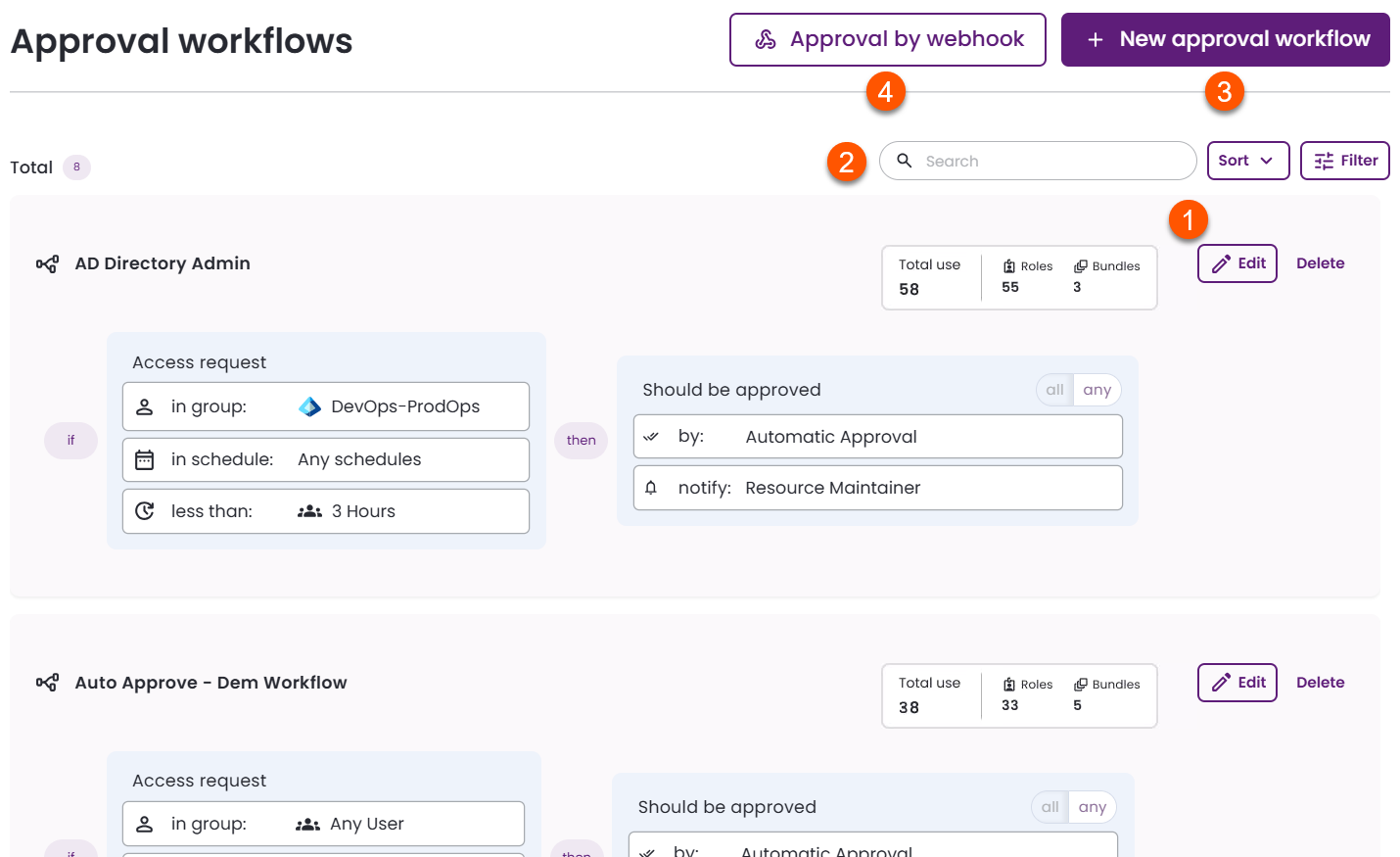
Edit and delete approval workflows
-
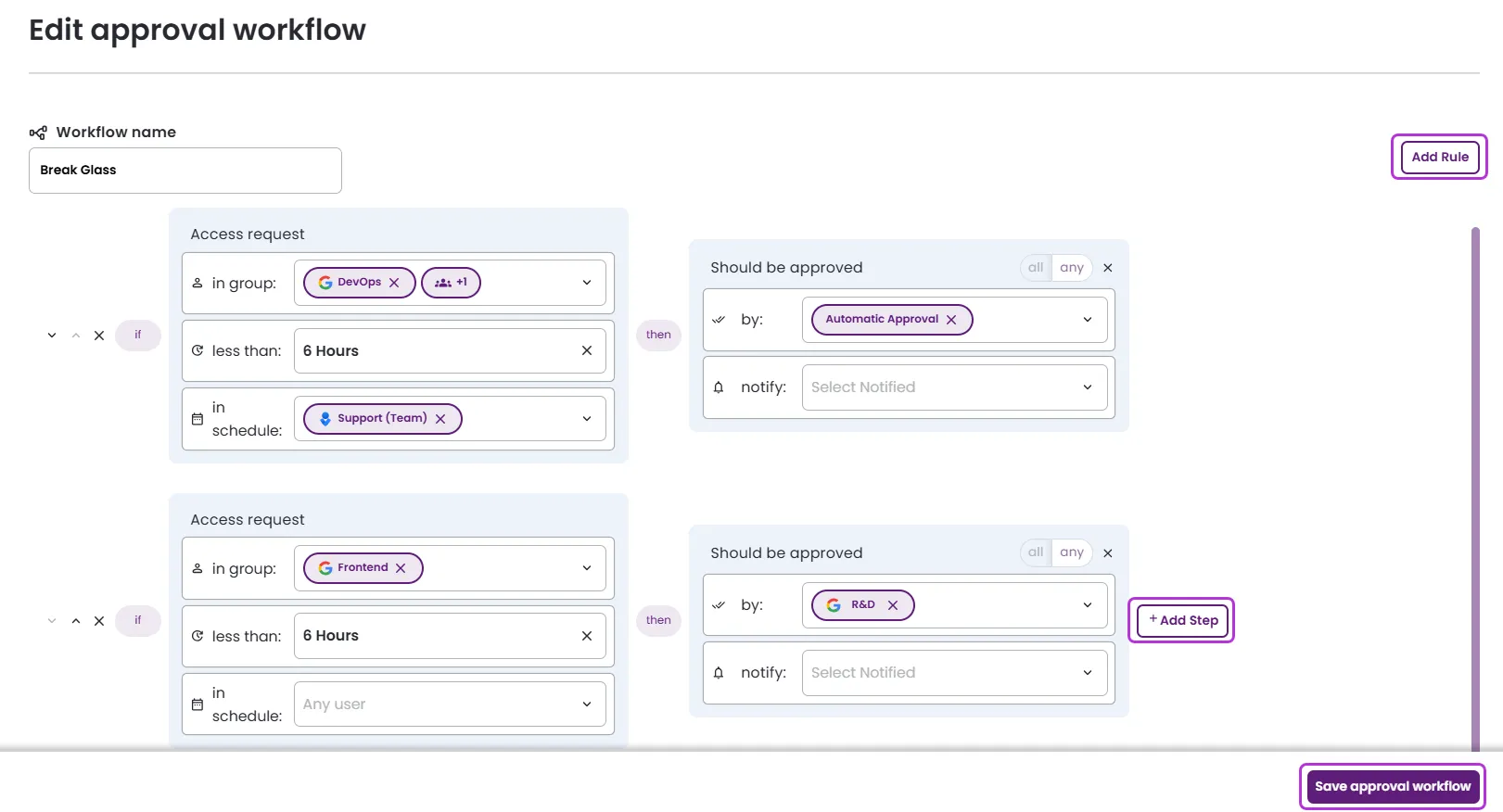
Edit approval workflow: You can modify the workflow name, access request conditions, and approval steps. You can also add or remove rules and steps, and change rule order using the arrows at the left. After making changes, click Save approval workflow.
-
Delete an approval workflow: On the Approval workflows page, locate the workflow you want to remove, then click Delete. Confirm the deletion in the pop-up. If an approval workflow is in use, it cannot be deleted.
Search, sort, and filter approval workflows
- Search by:
- Workflow name
- Sort options:
- Name
- Number of steps (sorts by the highest step count present in any rule in each workflow)
- Last added
- Filter options:
- Name
- IdP group
- On-call group
- Approval by webhook
- Request duration
- Usage
Add a new approval workflow
- On the Approval workflows page, click New approval workflow.
- Choose a name for your workflow.
- Define one or more rules, including their conditions and approval steps.
- In group: Select a group from which users must be selected, or default to any.
- Less than: Select a maximum duration for requests.
- In schedule: Select a schedule or on-call group that the selected user must belong to, or default to any.
- Should be approved by: Select who must approve the request. You can specify one or more users, groups, Slack channels, webhooks, or schedules.
- Notify: Select who should be notified of the request. You can specify one or more users, groups, Slack channels, webhooks, or schedules.
When Slack channels are selected as approvers or notification recipients, notifications are posted as threaded messages. The initial message supports team discussion within the thread before a decision is made. All subsequent updates for the same access request, including approver actions, admin approvals, and automatic approvals, are posted to the same Slack thread to provide a complete history. If a Slack channel is configured as both an approver and a notifier, only a single approval message is posted to avoid duplicate notifications.
- Order the rules as needed.
- Click Save approval workflow.
The newly created approval workflow appears on the Approval workflows main page.
Set up webhook-based approvals
View role access to the Approval by Workflows page
See which roles can perform each action.
ImportantThis page is accessible only to Super Admins, Tenant Admins, Admins, and Read-Only Admins.
| Actions | Super Admin | Tenant Admin | Admin | Read-Only Admin |
|---|---|---|---|---|
| Create webhooks | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Visible but deactivated: Action is shown but cannot be clicked |
| Edit webhooks | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Visible but deactivated: Action is shown but cannot be clicked |
| Delete webhooks | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Visible but deactivated: Action is shown but cannot be clicked |
| View associated approval workflows | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable | Allowed: Action is available and clickable |
Configure approvals by webhook (advanced)
Approval workflows support both third-party code approvals and advanced webhook notifications. Approval by webhook allows you to extend Entitle's built-in approver types with your organization's specific approval mechanisms, such as customer approvals or certification services.
- On the Approval workflows screen, click Approval by webhook.
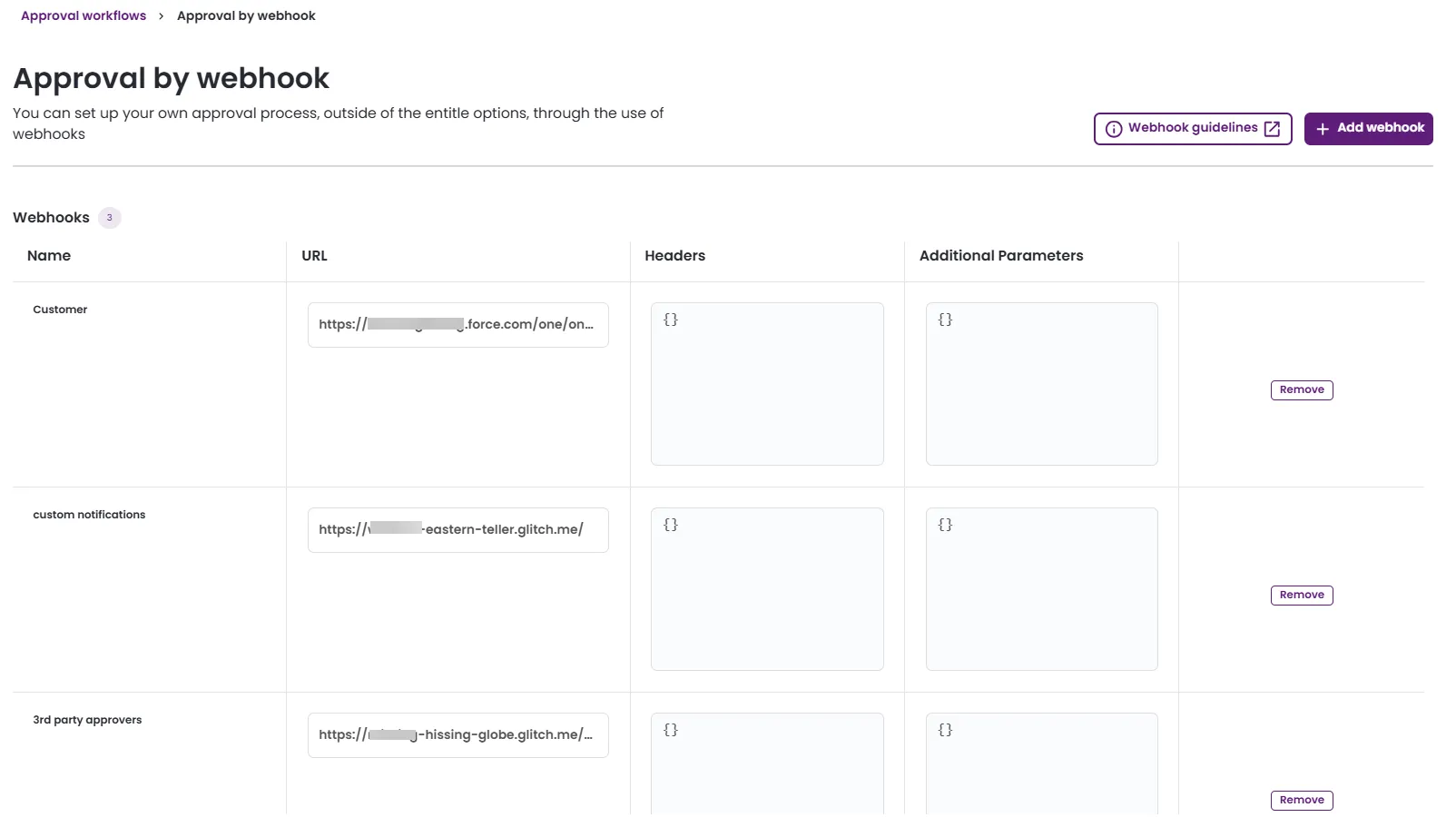
- Click Add webhook, and insert your webhook details.
- Name: Enter a name to identify your webhook.
- URL: Insert your webhook URL. Make sure it adheres to the Approval webhook structure.
- Headers: Any value set in this field will be added to the request header as is.
- Additional parameters: Any value set in this field will be added to the request body as is.
Important information
The following keys are forbidden:
stageNumber,stageAmount,token, andaccessRequest.
Use a webhook in a workflow
- After the webhook is registered, go to the Approval workflows page and either add or edit a workflow.
- Add the webhook to the workflow as either an approver or a notification recipient.
- Save the workflow to apply the changes.
This example shows both configurations (indicated by the webhook icon).
Webhook Request Structure
When a webhook is triggered as part of an approval step, Entitle sends a JSON payload similar to this:
{
stageNumber: 1,
stageAmount: 3,
accessRequest: {
behalfOf: {
id: "51907709-306b-4587-a89a-4c1a3f8d081f",
email: "[[email protected]](mailto:[email protected])",
},
duration: 15768000,
id: "054283fe-f1b4-4bdc-b54e-2adba50f079a",
justification: "I need it",
number: 114,
roles: [
{
isPrerequisite: false,
id: "a7b1e5be-d2bb-4891-a446-406b74ba7b3f",
name: "role1",
resource: {
id: "f40d54f4-1483-431f-bbe1-ce6e19a792eb",
name: "resource 1 name",
integration: {
id: "e5eb6b93-5735-4a65-97fc-5f11e29b9566",
name: "manuella",
application: {
name: "Manual",
},
},
},
},
],
status: "waitingForApproval",
targets: [
{
type: "role",
role: {
id: "a7b1e5be-d2bb-4991-a446-406b74ba7b3f",
name: "requested role",
},
},
{
type: "bundle"
bundle: {
id: "a7b1e5be-d2bb-4991-a446-406b74ba7b3f",
name: "requested bundle",
},
}
] Field meanings:
stageNumber– The current step number in the approval process.stageAmount– The total number of approval steps in the access request.token– A unique identifier used to authenticate and link a specific webhook workflow request with its corresponding response. This token is required only when the webhook acts as an approver, not when it is used for notifications.accessRequest– The access request details.
Webhook response structure
Your webhook returns its approval decision – approve or decline – by sending an HTTP POST request to the accessRequests/reply endpoint.
The response should include the following parameters:
{
"type": "approve" | "decline",
"token": "token received from webhook data"
}
Example cURLcurl -X POST <https://api.entitle.io/webhooks/v1/approvalRequests/reply> -H "Content-Type: application/json" -d '{ "type": "approve", "token": "c14f9c92-87bd-4a2e-9f13-2e7c4a1d5b8e" }'
Important informationIf Entitle repeatedly fails to deliver webhook requests, the webhook is automatically disabled. While disabled, new approval steps intended for that webhook are escalated to Entitle administrators.
Updated 5 days ago