Oracle Database | Entitle
What is Oracle Database?
Oracle Database is a relational database management system (RDBMS) developed by Oracle Corporation. It enables organizations to store, manage, and retrieve data using SQL. The system provides features for maintaining data integrity, performing backups and recoveries, controlling access, and optimizing performance. Oracle Database can be deployed on-premises or in the cloud through Oracle Cloud Infrastructure (OCI).
How is this integration useful?
Integrating Oracle Database with Entitle automates access requests and approvals for database roles and privileges, reducing manual effort and improving operational efficiency. Enforcing least-privilege access within pluggable databases (PDBs) enhances security and simplifies compliance.
Entitle can only manage pluggable databases (PDBs), which are portable collections of schemas, schema objects, and non-schema objects that appear to an application as a separate database. The Container database (CDB) includes all the data files for the PDBs contained within it.
Entitle can manage the following resource types in pluggable databases (PDBs):
- Databases
- Roles
- Administrative privileges
- System privileges
- Tables (for visibility only)
Entitle supports the creation of ephemeral (temporary) accounts for this integration, enabling more secure Just-In-Time (JIT) access.
Types of privileges in Oracle
-
Administrative privileges — Administrative privileges are designed for commonly performed administrative tasks, such as backup and recovery operations. Oracle Database provides administrative privileges tailored to specific administrative tasks, such as the
SYSKMadministrative privilege for performing Transparent Data Encryption tasks.- Administrative privileges are available only when connecting to an on-premises Oracle database
- Only users who have the
SYSDBAprivilege will be able to manage administrative privileges.
-
System privileges - enable users to perform actions on schema objects. Examples of system privileges are the ability to create and update tables or tablespaces.
-
Roles - group several privileges and roles, so that they can be granted to and revoked from users simultaneously. You must enable the role for a user before the user can use it.
-
Object privileges - each type of object has privileges associated with it. Objects are schema objects, such as tables or indexes.
- Table privileges (for visibility only) - enable security at the DML (data manipulation language) or DDL (data definition language) level. DML operations are
DELETE,INSERT,SELECT, andUPDATEoperations on tables. DDL operations areALTER,INDEX, andREFERENCESoperations on tables and views.
- Table privileges (for visibility only) - enable security at the DML (data manipulation language) or DDL (data definition language) level. DML operations are
-
You can grant privileges to a user in two ways using Oracle Database:
-
Grant privilege to users explicitly - for example, you can explicitly grant user
Smiththe privilege to insert records into theemployeestable. -
Grant privilege to a role (a named group of privileges), and then grant the role to one or more users - for example, you can grant the privileges to select, insert, update, and delete records from the
employeestable to the role namedClerk, which in turn you can grant to usersSmithandRobert.
As roles allow for easier and better management of privileges, it is recommended to grant privileges to roles rather than to specific users.
-
Prerequisites
- Install Entitle’s agent using the Agent installation guide.
- Have an Oracle Database user with
SYSDBAprivilege for the integration with Entitle. If the user does not have this privilege, they must at least have aDBA(Database Administrator) role.- If a user has the
SYSDBAprivilege**, this privilege will surely be used in Entitle**. - Only users who have the
SYSDBAprivilege will be able to manageadministrative privileges.Important informationIn Oracle Database, the ability to grant the
SYSDBAprivilege to other users is restricted. Only users with theSYSDBAprivilege themselves can grant it to others:- SYS users.
- Users who have been granted the
SYSDBAprivilege. - Optional:
GRANT_ANY_PRIVILEGEprivilege. If not, the user will not be able to manage access to administrative privileges.
- If a user has the
- Choose one of the two operation modes supported by Entitle for Oracle Database: Standard or Mutual TLS.
TLS (Transport Layer Security) is an updated and more secure version of SSL (Secure Socket Layer).
- Standard: This mode supports both
tcpandtcpsprotocols:tcp: Standard communication using TCP over IP.tcps(default): Secure communication using TCP over IP with SSL (Secure Sockets Layer).
Iftcpsis chosen, only the customer authenticates the server. The server provides its certificate, which the client validates to establish a secure connection.
- Mutual TLS: Both the client and server authenticate each other. Each party presents and validates its certificates before establishing a secure connection, offering more security due to bidirectional authentication.
In Mutual TLS operation mode, the protocol is always tcps.
- Standard: This mode supports both
- Access to the following information in Oracle, depending on your selected mode of operation:
Standard mode- Required
- Username
- Password
- Host name
- Service (database) name
- Optional
- Port name
- Protocol
- SSL server distinguished name (DN)
Mutual TLS mode
- Required
- Username
- Password
- Host name
- Service (database) name
- Key decryption password
- Private key
- Certificate
- Optional
- Port name
- Protocol
- SSL server distinguished name (DN)
- Required
Connect to the Oracle Database
Connect to the database using an administrative user with SYSDBA privileges or the SYS user. This connection is typically established through SQL*Plus or another SQL client.
Create a user with SYSDBA privilege or DBA role
SYSDBA privilege or DBA roleSkip this step if you already have a user with the required SYSDBA privilege or a DBA role.
-
Use the
CREATE USERstatement to create a new user. Replaceusernameandpasswordwith your desired values. -
Grant
SYSDBAprivilege (recommended) orDBArole to the user:-
To grant the
SYSDBAprivilege, use theGRANT SYSDBA TOstatement: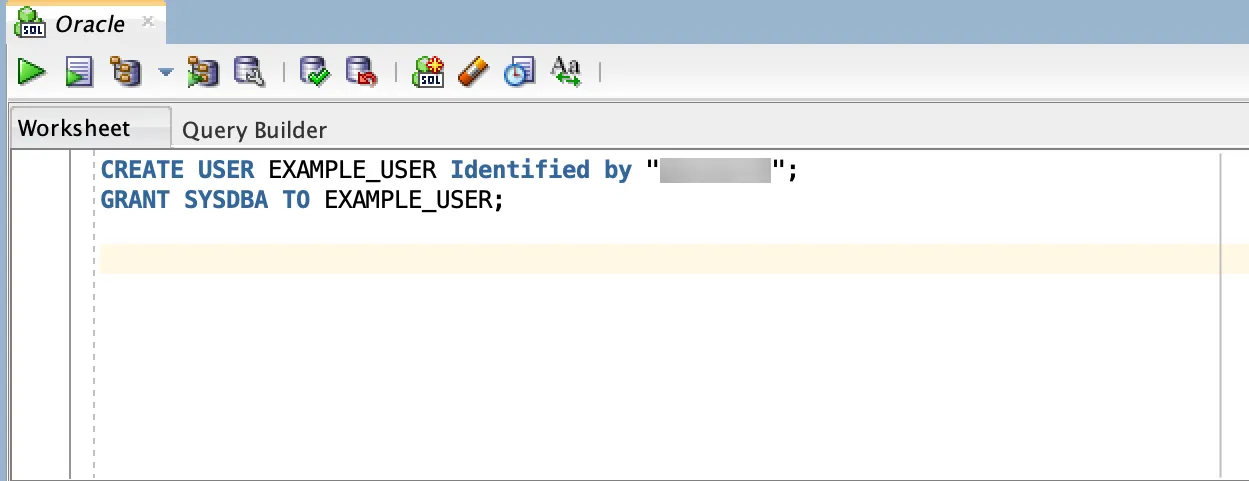
-
To grant a
DBArole to the user, use theGRANT DBA TOstatement: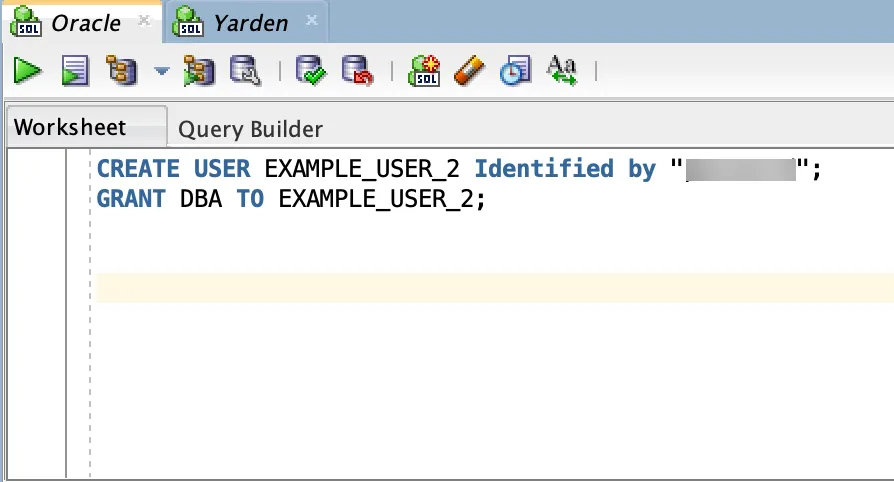
-
-
In the lower part of the screen, you will be able to see whether the user was created and if the privilege/role was granted.
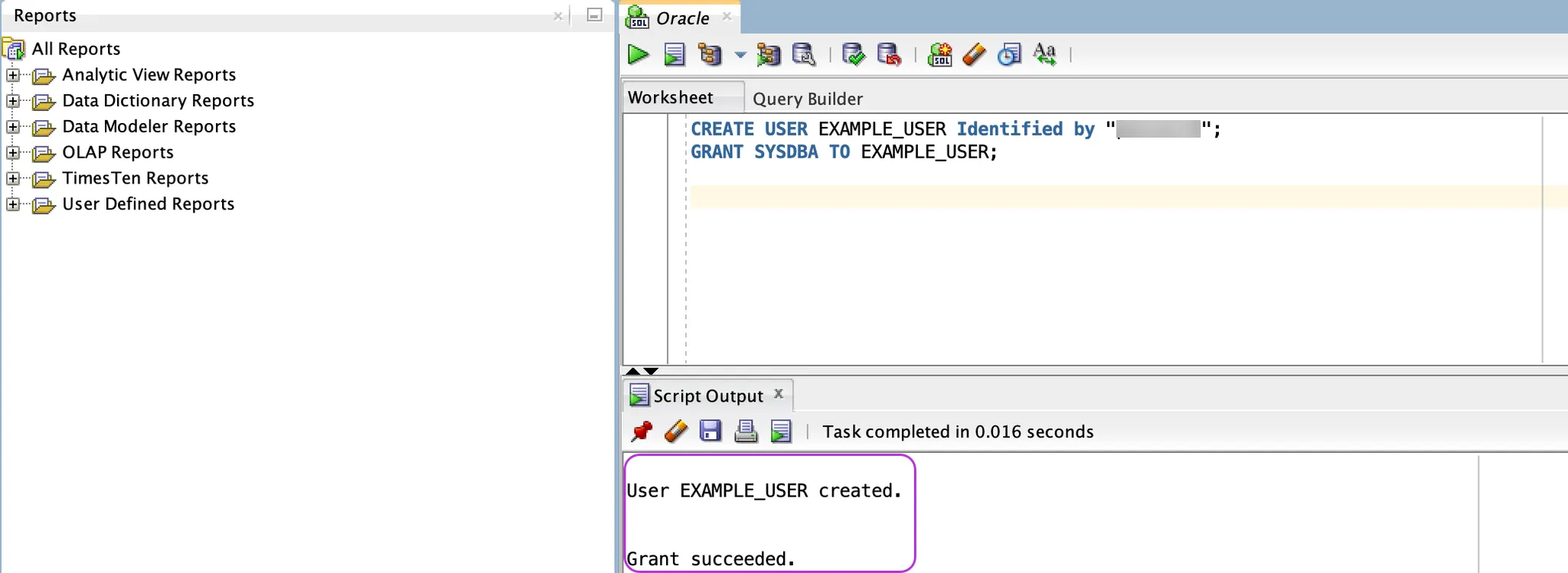
-
It is recommended to connect to the database using the new user account to verify that everything is functioning correctly.
Additional steps to set up Mutual TLS mode
The following steps are performed using the Oracle Cloud Infrastructure (OCI) Console.
Create a key decryption password
-
Log in to the OCI Console with a user who has admin privileges on the database
-
Click the left-side navigation menu and click Oracle Database > Autonomous Database.
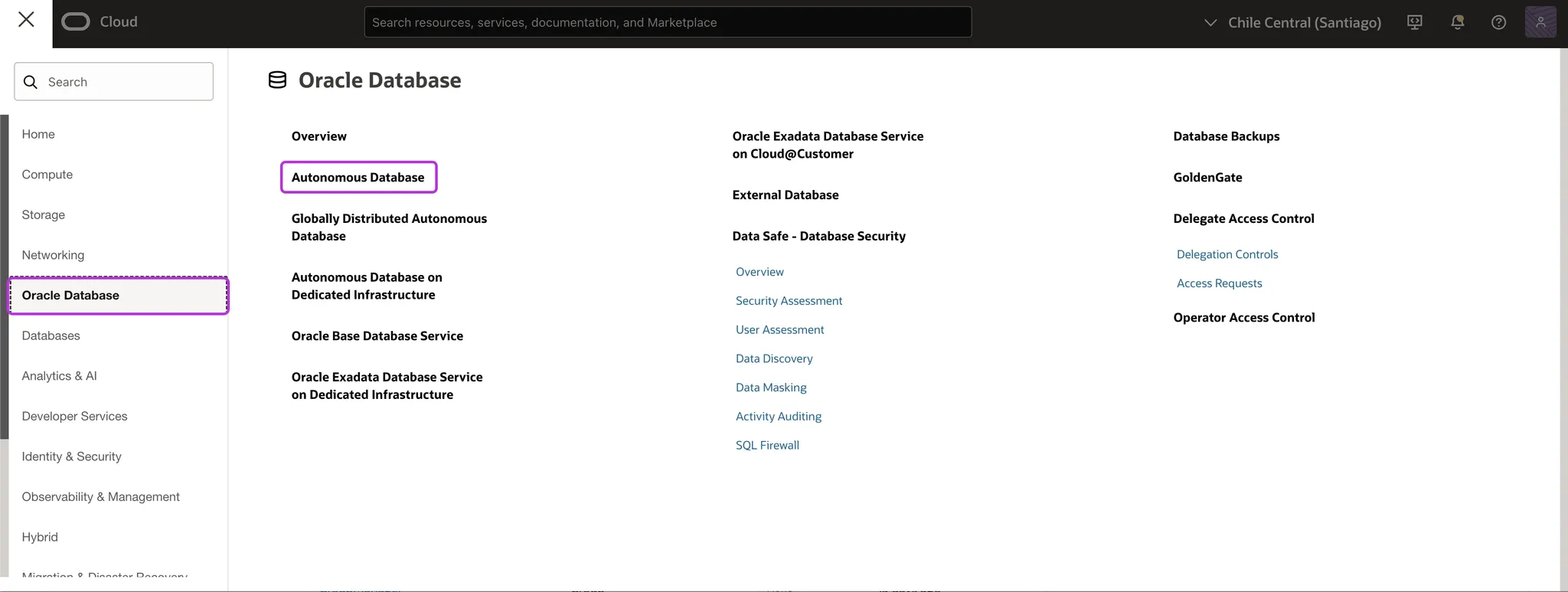
-
Select a database from the list.
-
In the Autonomous database details page, click Database connection.

-
In the Database connection page under the Download client credentials section, click Download wallet.
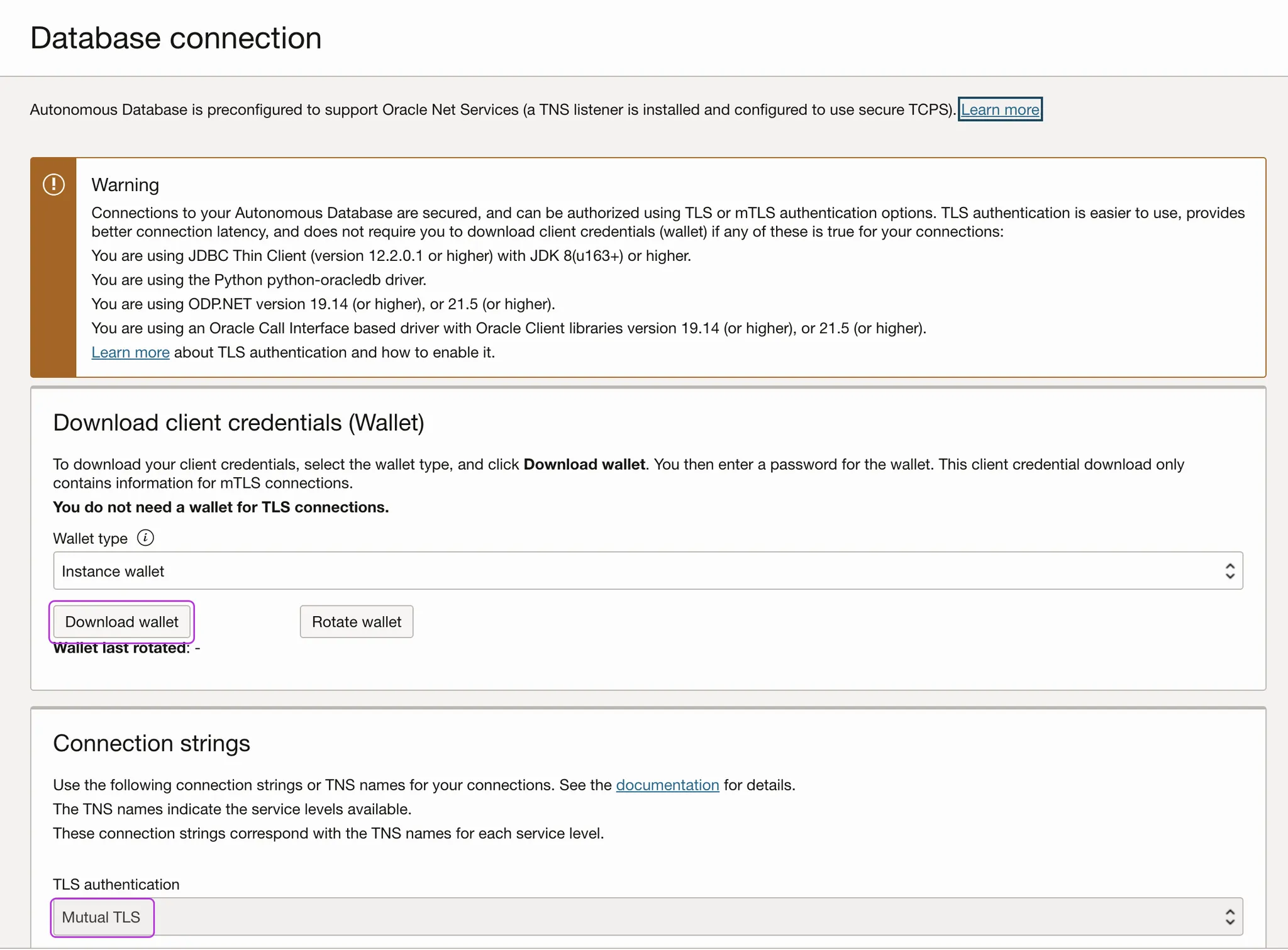
Under the Connection strings section, you can verify that the specific database's TLS authentication is indeed Mutual TLS, as needed for the integration with Entitle.
-
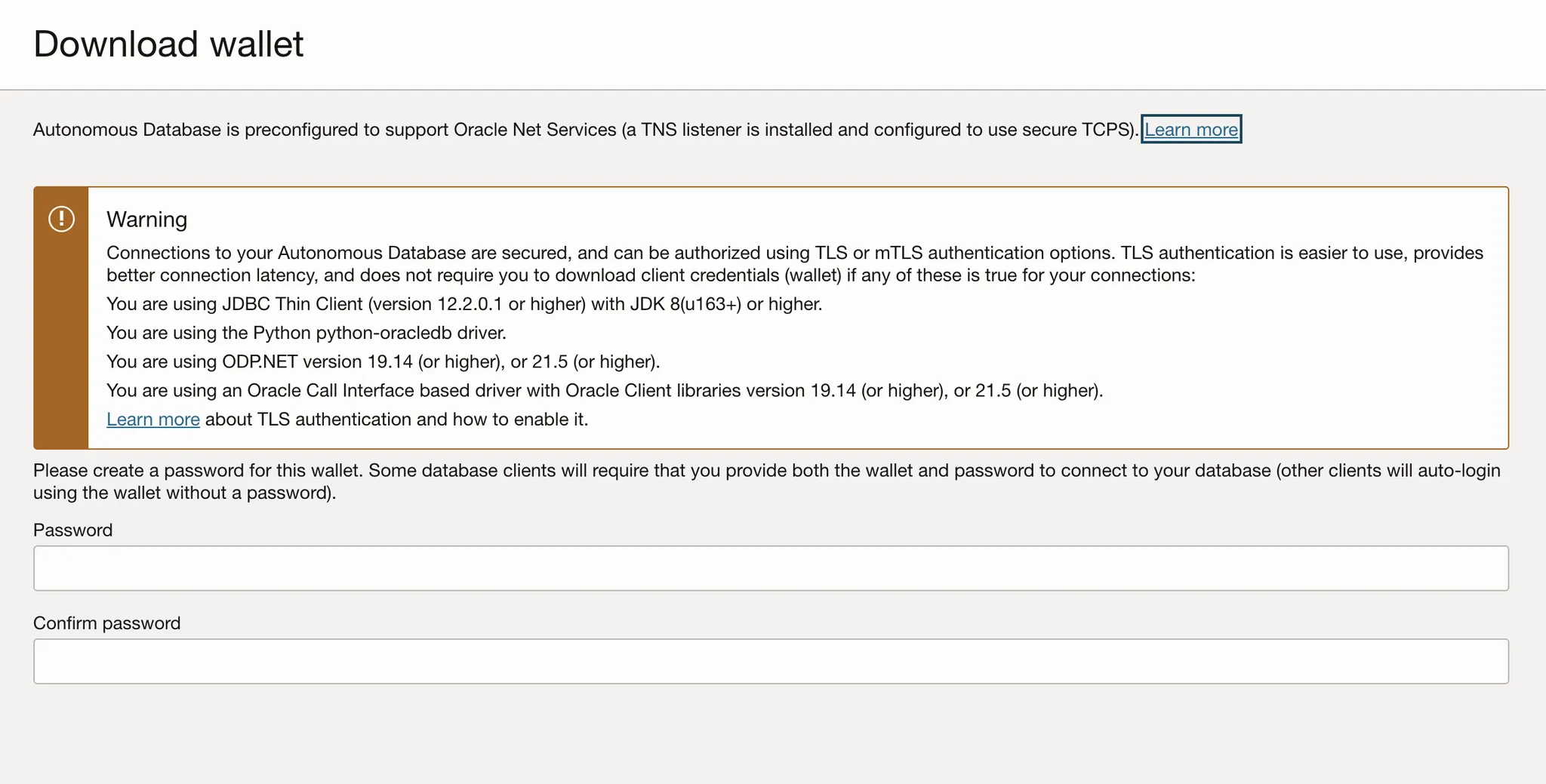
In the Download wallet page, create and confirm a password. Click Download.
Create a private key
-
Extract the contents of the ZIP folder, then open the
ewallet.pemfile from the extracted files.
-
Copy the private key for the configuration later on.
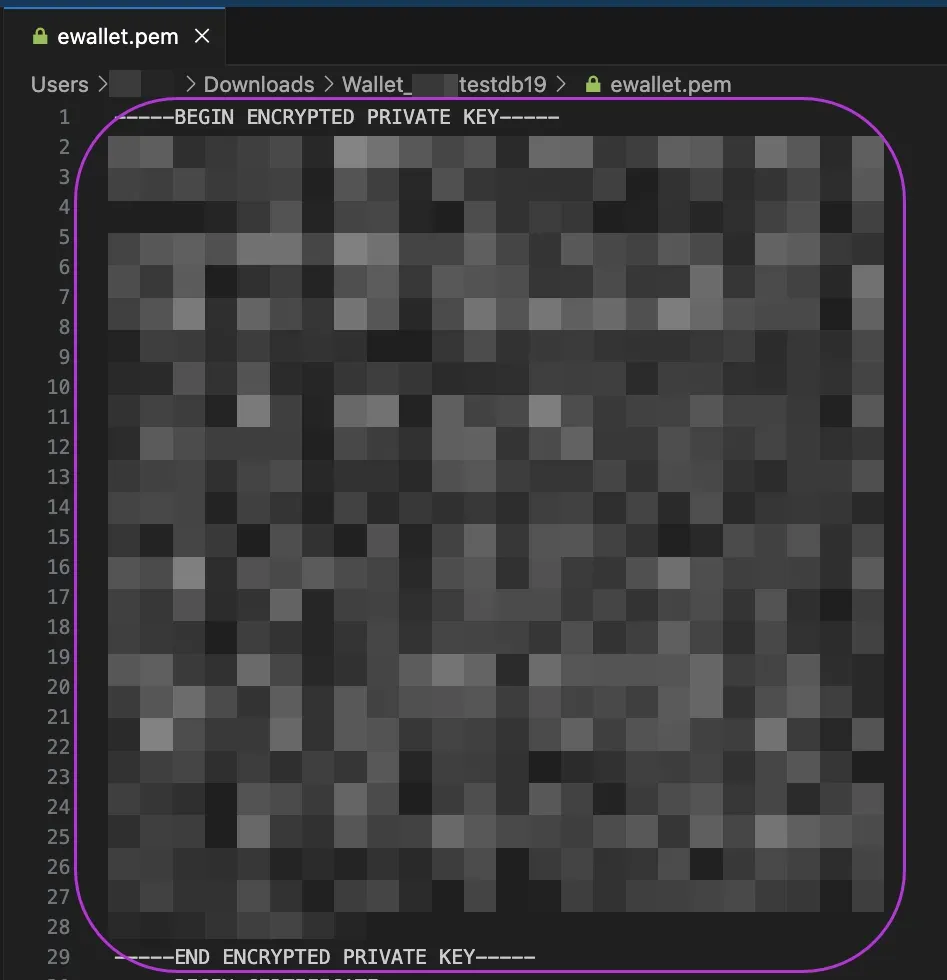
-
Run the appropriate command below (for Linux or Windows) to convert your private key into a single-line string with escaped newline characters. This is required because JSON strings do not support literal newline characters; they must be replaced with the ASCII character
\n.For Linux devices:
sed 's/$/\\n/' <key-path> | tr -d '\n'If the
sedcommand fails to replace the newlines with\n, you must do it manually before implementing it in the Entitle configuration.For Windows devices:
(Get-Content private.key) -join '\n'
Create a certificate
-
Locate the certificate and copy it from the same
ewallet.pemfile.
-
Apply the same process used for the private key to convert the certificate into a single-line string with escaped newline characters.
Create the integration in Entitle
- Log in to Entitle and go to the Integrations page.
- Click Add Integration.
- In the Application field, enter Oracle Database.
- In the Save on dropdown, select Entitle cloud or your hosted agent.
- In the connection JSON, add the following information:
Required fields for both modes:
username: Insert your Oracle Database username.password: Insert your Oracle Database password.host: Insert your instance host.service_name: Insert your service (database) name.Verify that the service name includes PDB and not CDB, as Entitle can manage only PDBs.
Required fields for Mutual TLS mode:key_decryption_password: Insert the password you created in the Create a key decryption password step.private_key: Insert the private key content.Remember to replace the newlines with
\n.certificate: Insert the certificate content.Remember to replace the newlines with
\n.
Optional fields for both modes:port: Insert your port number.If not provided, it will be set by default to 1521.
protocol: Specifies the communication method used between the client and the Oracle Database server.Reminders- In Standard operation mode, you can set the protocol to either
tcportcps. If not specified, it defaults totcps. - In Mutual TLS operation mode, the protocol is always
tcpsand does not need to be explicitly set in the configuration.
- In Standard operation mode, you can set the protocol to either
ssl_server_dn_match: Controls whether the client verifies the Distinguished Name (DN) in the server’s SSL certificate against the expected value in the connect descriptor:- Set to
trueto enforce a match between the server's DN and the service name. The connection fails if they don’t match. - Set to
falseto allow a mismatch. The connection will succeed, but an error is logged insqlnet.log.If not provided, it will be set by default to
true.
- Set to
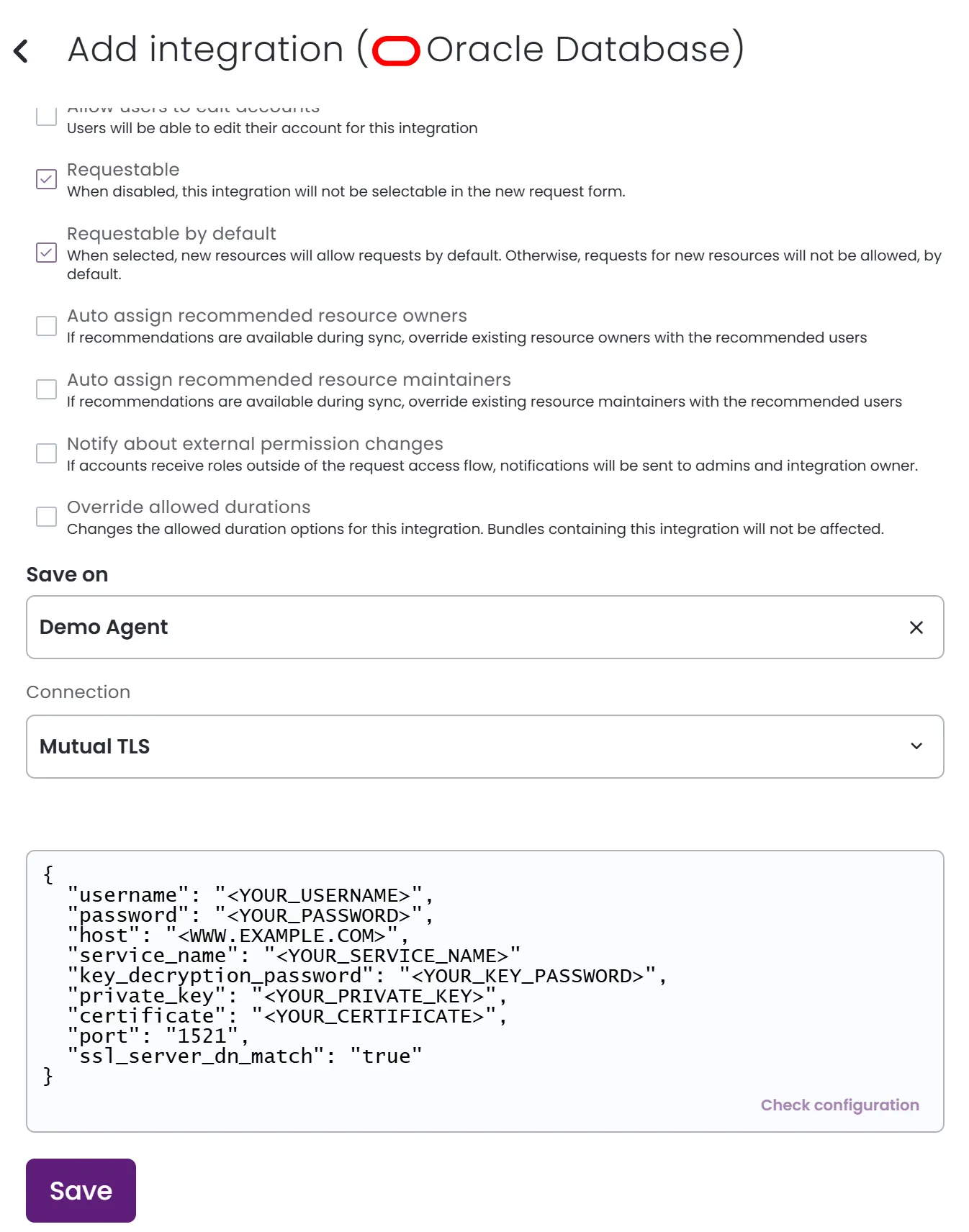
Example connection JSON{ "username": "<YOUR-USERNAME>", "password": "<YOUR-PASSWORD>", "host": "<WWW.EXAMPLE.COM>", "service_name": "<YOUR-SERVICE-NAME>", "port": "<PORT-NUMBER>" {optional}, "protocol": "tcp" or "tcps" {optional}, "ssl_server_dn_match": "true" or "false" {optional} }{ "username": "<YOUR-USERNAME>", "password": "<YOUR-PASSWORD>", "host": "<WWW.EXAMPLE.COM>", "service_name": "<YOUR-SERVICE-NAME>" "key_decryption_password": "<YOUR-KEY-PASSWORD>", "private_key": "<YOUR-PRIVATE-KEY>", "certificate": "<YOUR-CERTIFICATE>", "port": "<PORT-NUMBER>" {optional}, "ssl_server_dn_match": "true" or "false" {optional} }
- Click Save.
End-user experience
-
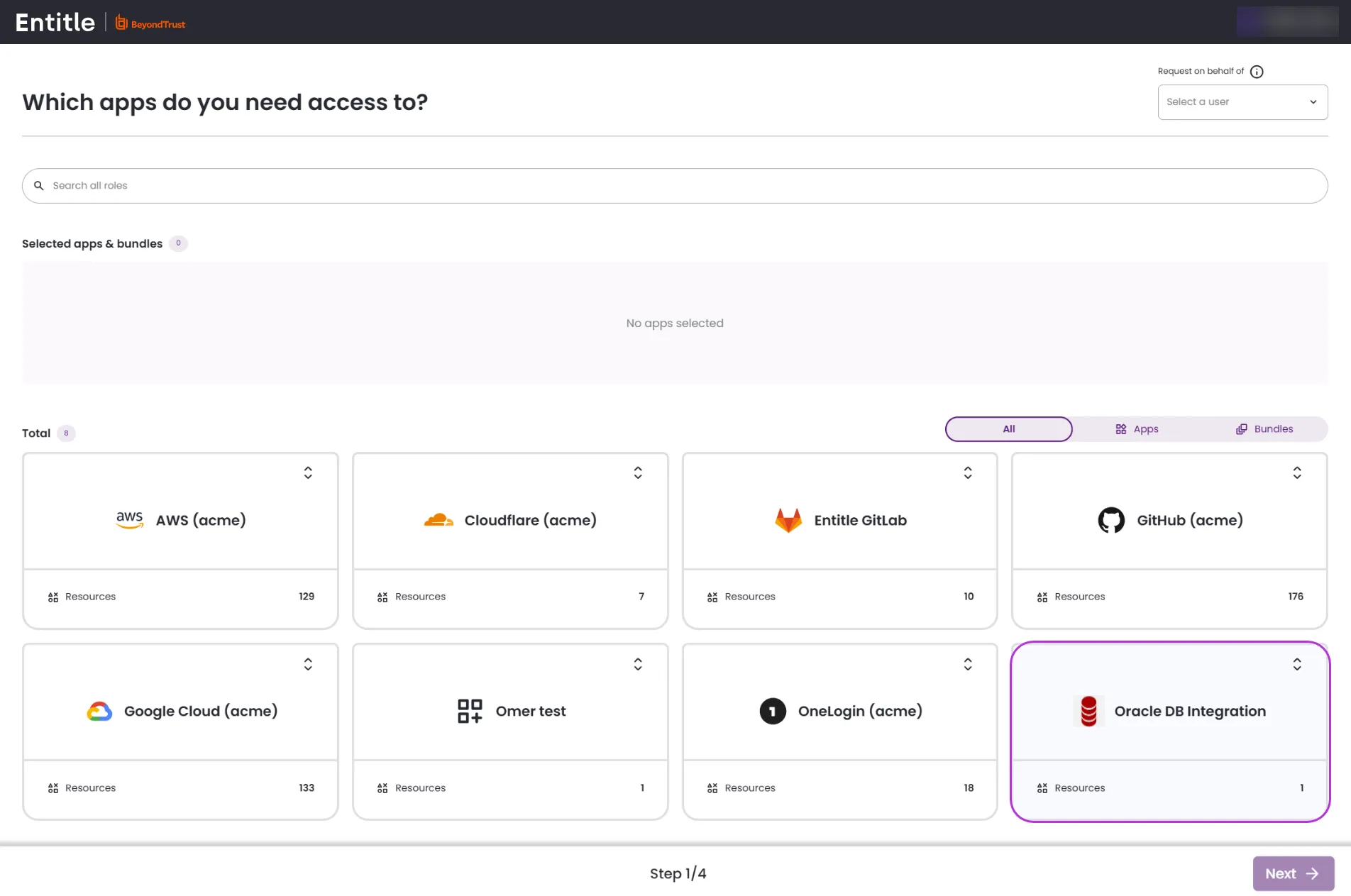
Log in to Entitle and click New Request.

-
Locate the Oracle Database application. Choose the resource and the role you would like to request access to. Click Next.

-
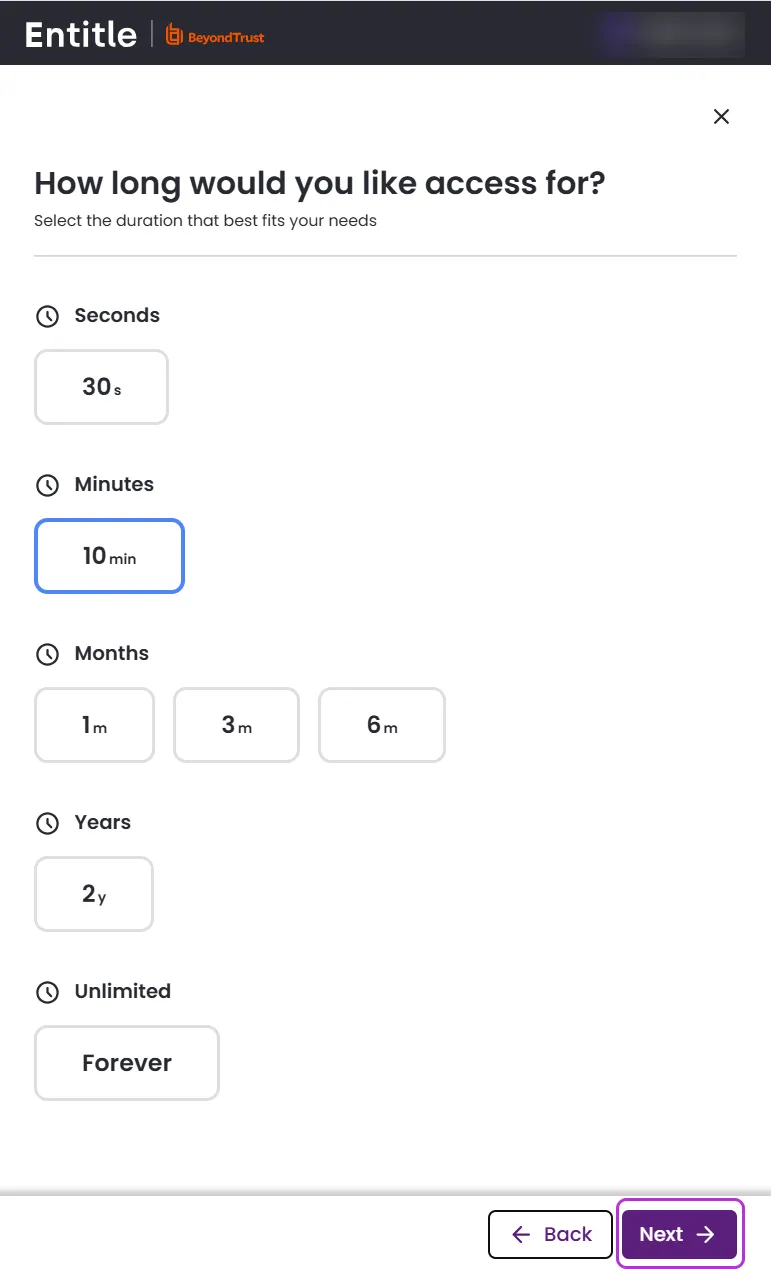
Choose the duration of your request and click Next.
-
Provide a reason for your request and click Review Request.
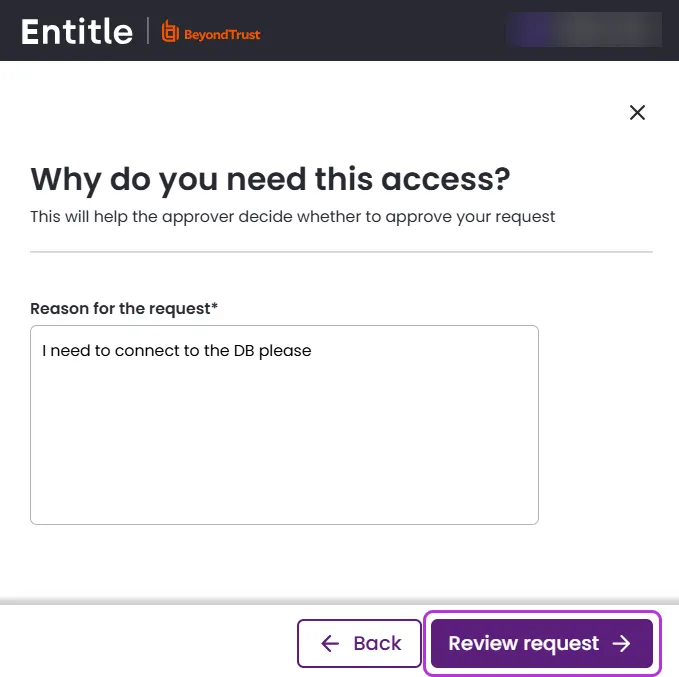
-
Review your request’s details and adjust if needed. Click Submit request.
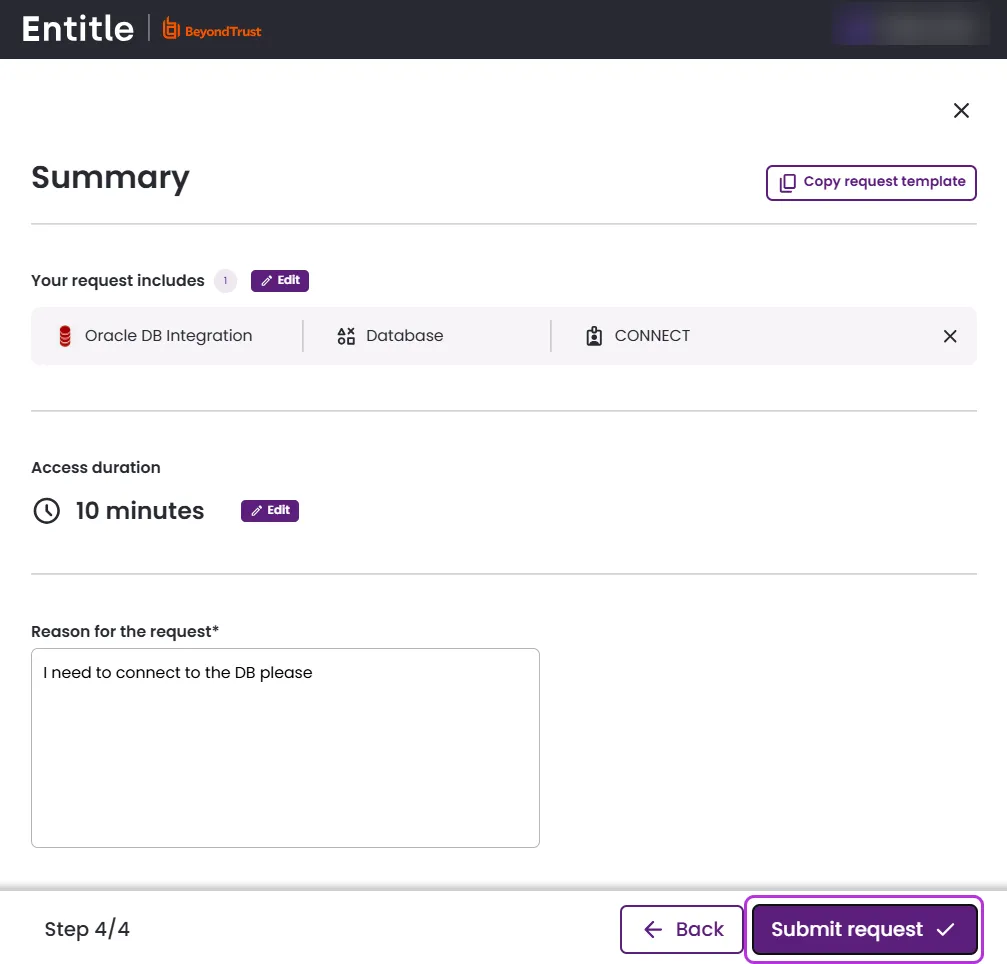
-
Your request is submitted and will be added to the My pending requests section.
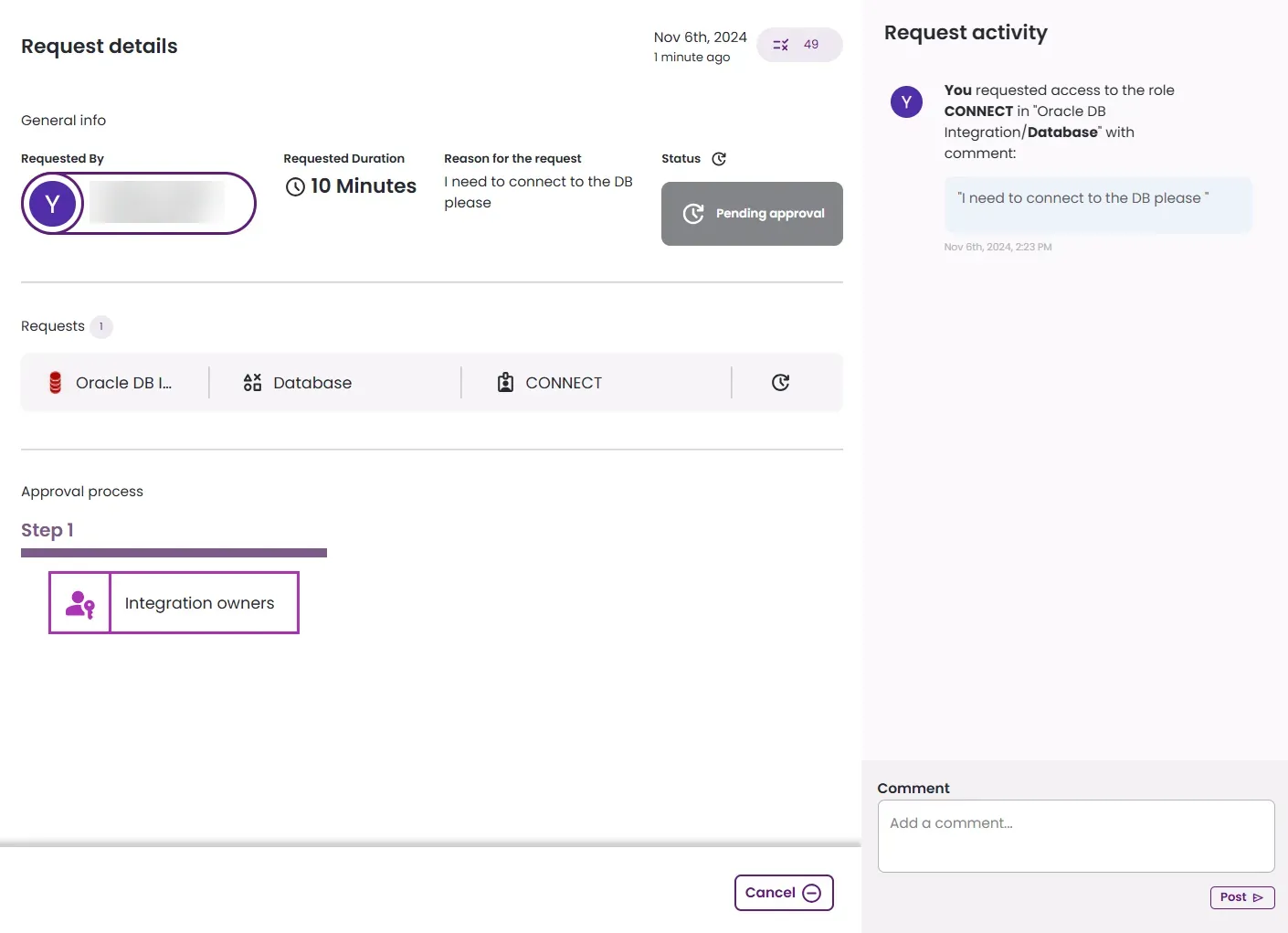
-
Once approved, you will be granted access to the specific role.
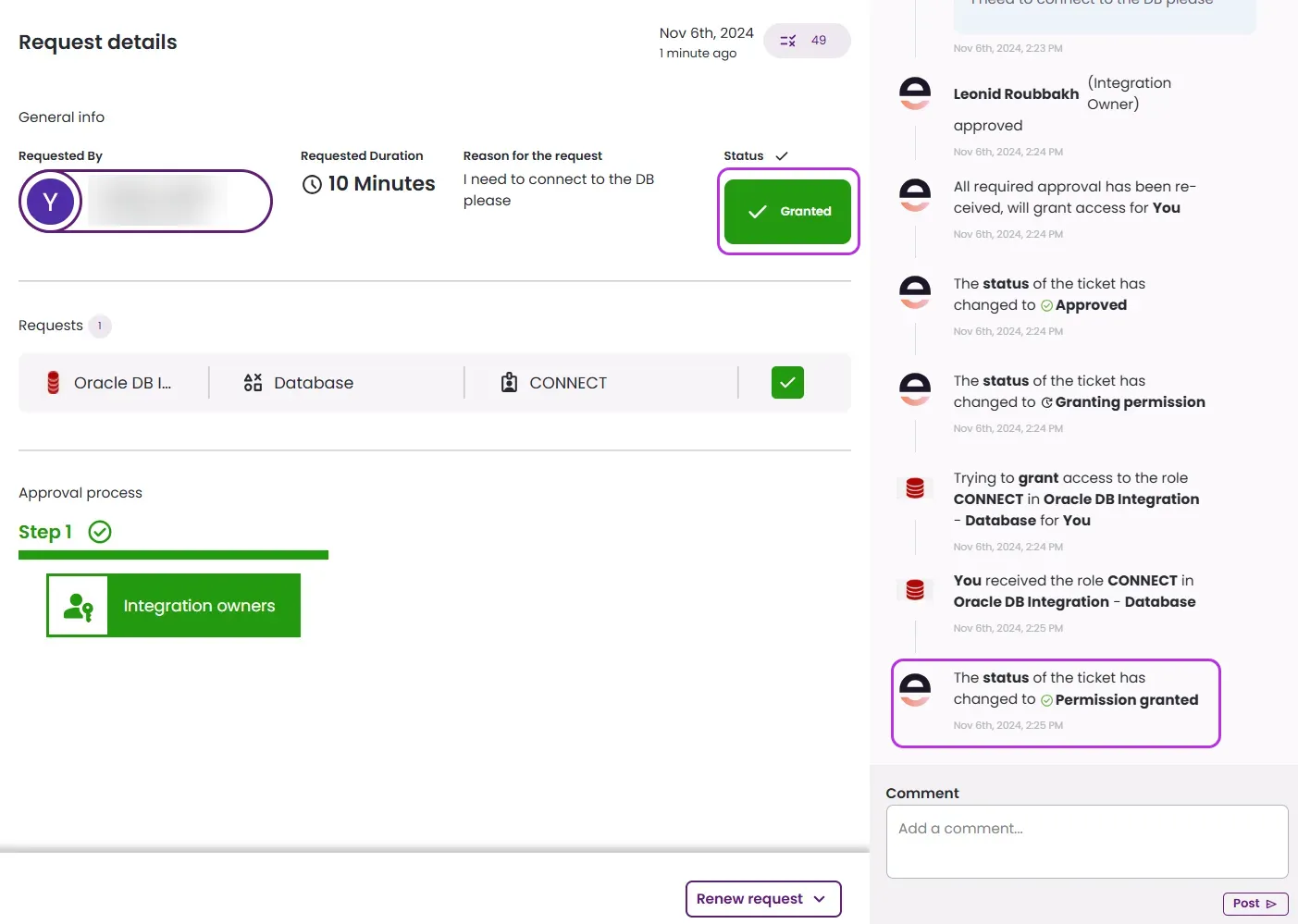
What's next?Make sure your setup is complete by testing your integration.
Updated 1 day ago
