GitLab | Entitle
Overview
GitLab is a web-based DevOps platform that allows software development teams to collaborate, manage source code repositories, track issues, and automate the software delivery pipeline.
Entitle can manage groups (all versions) and projects (on-prem version only) in GitLab.
This page will provide you with instructions on how to integrate Entitle and GitLab.
General guidelines
To integrate your GitLab in Entitle, you will need to create a Personal Access Token.
Set up GitLab to work with Entitle
Stage 1: Obtain your GitLab domain
- Copy the domain you use to log in to GitLab.
- If you don’t use a self-hosted GitLab domain, the domain is https://gitlab.com.
Stage 2: Create a Personal Access Token
- In the upper-right corner, select your avatar.
- Select Edit profile.
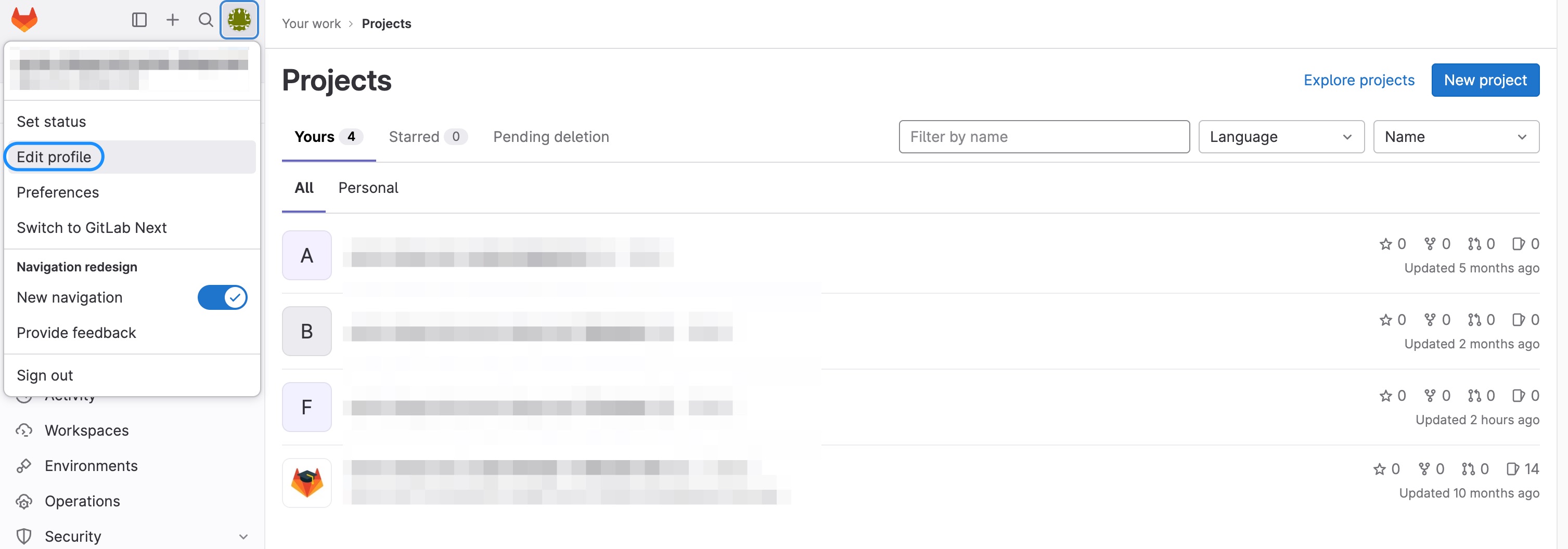
- On the left sidebar, select Access Tokens.
- Enter a name and expiry date for the token.
- The token expires on that date at midnight UTC.
- If you do not enter an expiry date, the expiry date is automatically set to 365 days later than the current date.
- Select the
apiscope. - Select Create personal access token, and copy it to your clipboard. You will need it for the configuration later on in this guide.
Entitle supports fetching user emails from GitLab:
This will be possible only if a GitLab user adds their email address under the Email or Public email fields on their Profile.
If the Email field is empty, Entitle will attempt to fetch the Public email instead.
If both the Email and Public email fields are empty, Entitle will not be able to fetch the user’s email.
Create the integration in Entitle
- Log in to Entitle and go to the Integrations page.
- After clicking the Add Integration button, type GitLab in the Application field.
- Don’t forget to set the Save on field with your configuration, i.e. your own hosted agent or Entitle’s cloud.
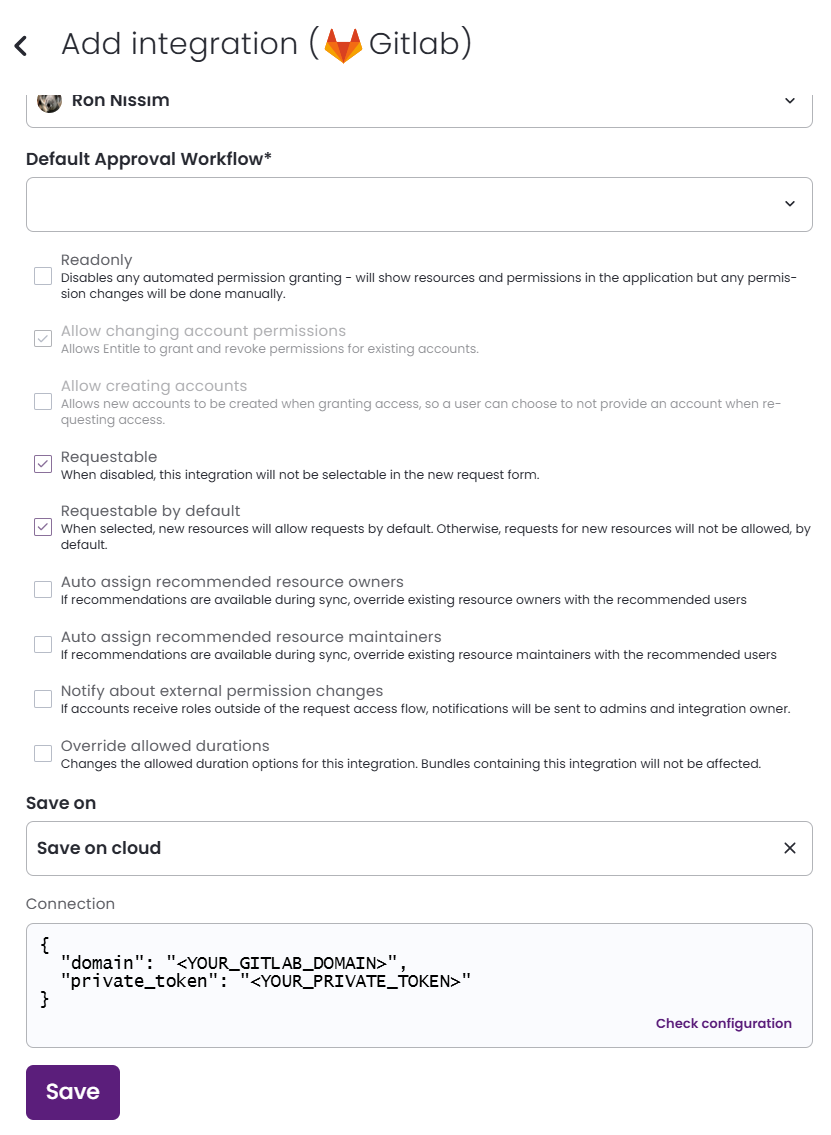
-
Under the
'domain'field, fill in your GitLab domain URL.- If you don’t use a self-hosted GitLab domain, fill in https://gitlab.com.
-
Under the
'private_token'field, fill in your Salesforce domain URL. -
Optional: Provide an SSL certificate
-
General Behavior
- If no certificate is provided,
verify=trueis the default behavior. - If
verify=falseis set, SSL verification is disabled, and the connection will work without a certificate. To setverify=false, use the below template for your configuration:{ "domain": "<YOUR-GITLAB-DOMAIN>", "private_token": "<YOUR-PRIVATE-TOKEN>", "options": { "ssl": { "verify": false } } {
- If no certificate is provided,
-
Public vs. Self-Signed Certificates
- Public certificates: No need to provide
ca_cert. - Self-signed certificates: You must provide
ca_cert.
In this case, you will need to ensure that the agent has access to the domain.
You can use the following script on yourcafile to get the correct format forcato provide:
#!/bin/bash # Check if the file path is provided if [ -z "$1" ]; then echo "Usage: $0 <path-to-ca.crt>" exit 1 fi # Read the file if [ ! -f "$1" ]; then echo "File not found: $1" exit 1 fi # Convert the file contents to a single line with \n instead of newlines crt_string=$(awk '{printf "%s\\n", $0}' "$1") # Print the result echo "$crt_string"
- Public certificates: No need to provide
-
To use a self-signed certificate, provide under the
"options"field"ca_cert"under"SSL"in the following format:options = { "ssl": { "ca_cert": "/etc/ssl/certs/custom_ca.pem" } } -
If not using a self-signed certificate,
ca_certis not required. -
If you don’t want to provide
ca_certbut would like Entitle to work, setverify=false. -
Set correct permissions using:
chmod +x convert_crt.sh then ./convert_crt.sh path-to/ca.crtExample Connection JSON with "options" field{ "domain": "<YOUR-GITLAB-DOMAIN>", "private_token": "<YOUR-PRIVATE-TOKEN>", "options": { "ssl": { "ca_cert": "/etc/ssl/certs/custom_ca.pem" } } }
-
-
Click Save.
What's next?Make sure your setup is complete by testing your integration.
Updated 15 days ago
