SSH Ephemeral Accounts integration | Entitle
Overview
Through the SSH Ephemeral Accounts integration option, ephemeral (temporary) users are created and given SSH access. After that, the users are deleted.
Prerequisites
The account with which you wish to integrate with Entitle can be either one of two options:
-
A root account that is capable of creating user accounts and modifying user files.
-
An alternative account with the privilege to execute specific executables (listed below) using sudo, without requiring a password:
-
cat– read file contents -
chmod– change who can read and write a file or directory -
chown– change the owner of a file or directory -
mkdir– create a directory -
mv– move a file -
rm– delete a file -
sed– stream editor to edit files (optional; see note below) -
tee– write to a file -
useradd– add a user -
userdel– delete a user
-
The privilege can be granted to the user by modifying the system's sudoers settings. Entitle highly recommends doing this with the
visudoexecutable (which requires an editor to be installed) to protect the Linux machine from becoming inoperable. -
Below is an example of modifying sudoers to allow passwordless execution for a single executable:
<username> ALL=(root) NOPASSWD: <executable path> -
The executable path can be identified by running
'which <executable name>.
The
sedcommand is provided as a workaround should the user become locked out after adding the account. If lockout does not occur, there is no need to runsedwith admin privileges. -
Should you need to allowlist this integration, these are the IP address ranges from which Entitle's service reaches the integration:
- Entitle EU (Cloud deployment)
- 34.243.199.171
- 54.216.133.226
- Entitle US (Pathfinder deployment)
- 52.45.229.219
- 54.88.235.213
- 3.224.15.134
General guidelines
- Entitle can manage two types of roles: Regular user access to the machine, and Sudo user access to the machine.
- In both cases, a temporary user will be created by the integration, of whom details will be returned to the user.
- However, only in the Sudo access case, the created user will also be added to the
/etc/sudoers.ddirectory. - Eventually, the created user will be deleted, along with the associated with its created files (if they exist).
End-user experience
This section outlines the employees’ experience requesting access to SSH with Entitle.
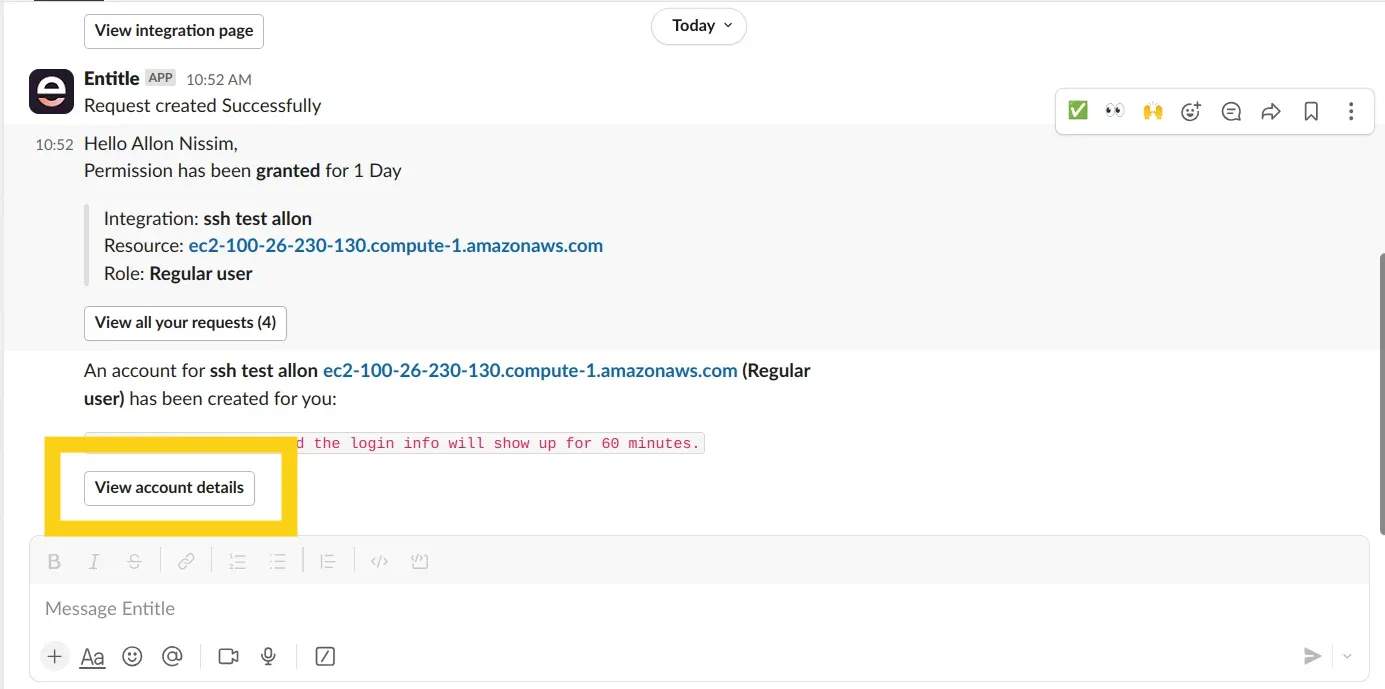
Upon receiving JIT access using Entitle, the employee will receive a pre-made command for accessing SSH via Teams/Slack.
-
The employee will click the View account details button.
-
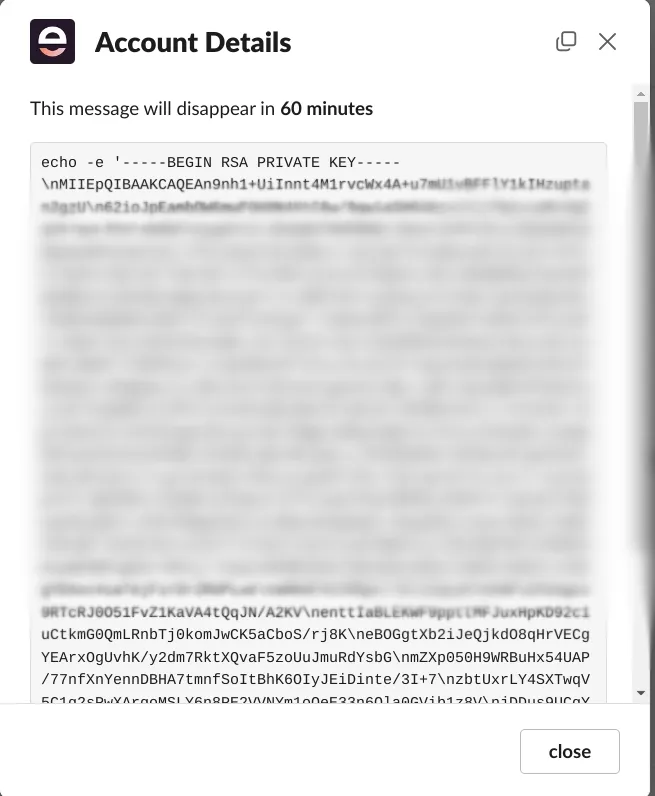
When opened, the employee will locate the SSH integration machine's key.
-
In your respective terminal, the employee will copy and paste the command:
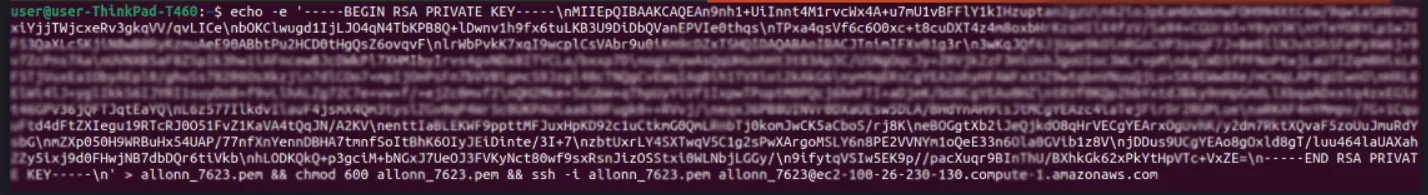
Microsoft Windows OS is yet to be supported by Entitle for SSH. The employee now has access to the designated machine.
Set up SSH to work with Entitle
All that is needed to integrate SSH with Entitle is the username and key of a Sudo user. One way of generating the key will be explained in the following steps; however, there are many other ways to achieve the same result.
Generate SSH keys
- Open the computer terminal.
- Generate an SSH key using the
ssh-keygencommand:
$ ssh-keygen- After running
ssh-keygen, you will receive two keys:id_rsaandid_rsa.pub(or the respective files you provided).In this guide, when prompted for the private key, provide the
id_rsafile. When prompted for the public key, provide theid_rsa.pubfile.To use the private key with Entitle, you need to replace all new lines with
\ncharacters. You can achieve this by usingsedcommand for Linux users only:
sed 's/$/\\n/' <key_path> | tr -d '\n'- Replace <key_path> with the name of your private key file.
- Below is an example of how a private SSH key will look.

Set up SSH key authentication on the target machine
- Open the terminal on the target machine.
- Navigate to the
/.sshdirectory for the specific user (e.g.,/home/username/.ssh). Keep in mind that this user is the same one you will set in the Example JSON configuration. - Within the
/.sshdirectory, create a file namedauthorized_keys, and paste the public key generated in step 2 to the authorized keys file. You can achieve this by echoing the public key into the file:
~ echo "public_key_content" > /home/username/.ssh/authorized_keysFailure to place the public key in the
authorized_keysfile will result in SSH authentication failure. This is because the private key does not match any public key.
Creating the integration in Entitle
-
Log in to Entitle and go to the Integrations page.
-
After clicking the Add Integration button, type SSH Ephemeral Accounts in the Application field.
-
Choose the Default Approval Workflow for your integration.
-
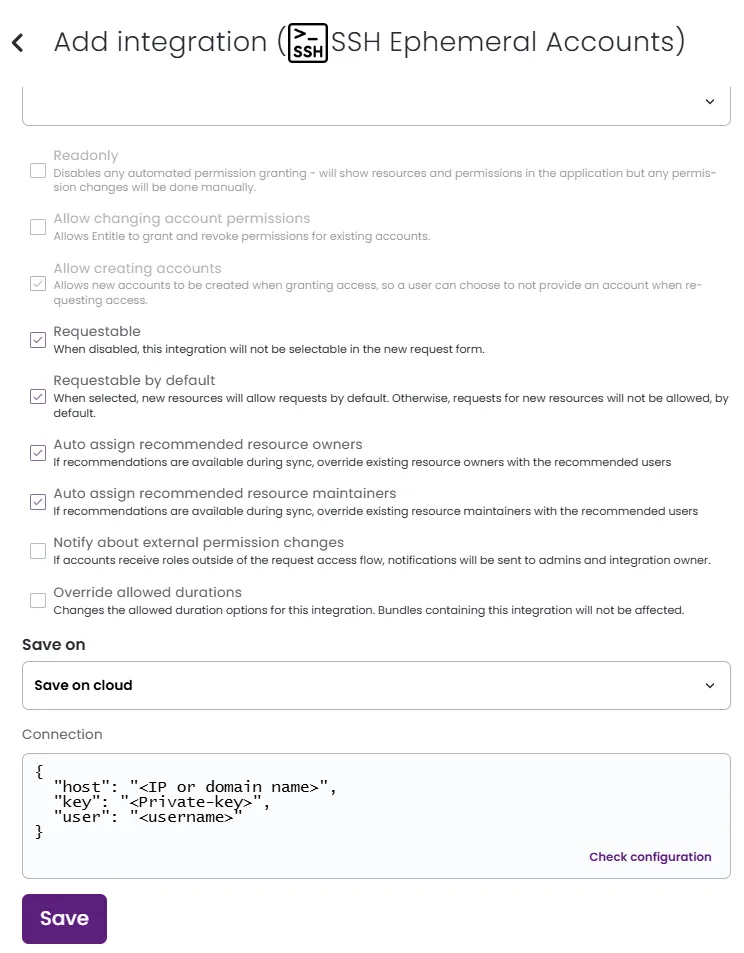
Don’t forget to set the Save on field with your configuration, i.e., your own hosted agent or Entitle’s cloud.
-
In the Connection JSON:
-
Assign the machine's IP address or domain name to the
hostfield. -
Paste the private key you previously generated, as the value for the
keyfield.In the Connection JSON, it's essential to swap each new line with
\ncharacter.Set the
userfield to the username to which the keys were mapped.Example connection JSON{ "host": "<IP or domain name>", "key": "<Private-key>", "user": "<username>" }
-
-
Click Save.
What's next?Make sure your setup is complete by testing your integration.
Updated 10 days ago
