Okta Access Management Guide
Overview
Okta provides cloud software that helps companies manage and secure user authentication into applications, and for developers to build identity controls into applications, website web services, and devices.
Entitle can manage the following resource types in Okta:
- Group membership – groups
- Custom roles – custom admin roles
- Administrative roles – admin roles
- Applications assignment
This page will provide you with instructions on how to Integrate Entitle with Okta.
General Guidelines
There are two ways to integrate Entitle with Okta:
- Service App Authentication (recommended) - Adding Entitle on Okta as a Service App/App Integration. In this option, Entitle will interact with Okta using the scoped OAuth 2.0 access token for machine-to-machine authentication. This is the recommended method because it is considered the most secure way to authenticate with Okta.
- API Token Authentication - an API token is generated in Okta and used by Entitle to authenticate. If you wish to manage your Okta applications using Entitle, API token authentication is the option to choose.
1. Service App Authentication
In this option, Entitle will interact with Okta using the scoped OAuth 2.0 access token for machine-to-machine authentication.
There are two permission scope options:
- Full functionality – To access all the features that Entitle provides, you must have a “Super Admin” role (the roles are derived from the user who creates the token) while creating the token, as only Super Admins are allowed by Okta to manage other users or groups that have admin privileges.
- Partial functionality - it is possible to use “Group Membership Admin” and “Report Admin” roles together to enable basic functionality. In this case, you won’t be able to give/revoke access or even read any admin roles. This includes adding users to groups with admin roles. To enable this option, you must set the “is_super_admin” option to 'false'.
It is also possible to restrict additional scopes by following the instructions in the section below.
Set Up Okta To Work With Entitle
If you want to create the token for Partial functionality option, make sure the token's Admin Role setting is configured as “Group Membership Admin” and “Report Admin” roles.
Create a new app integration
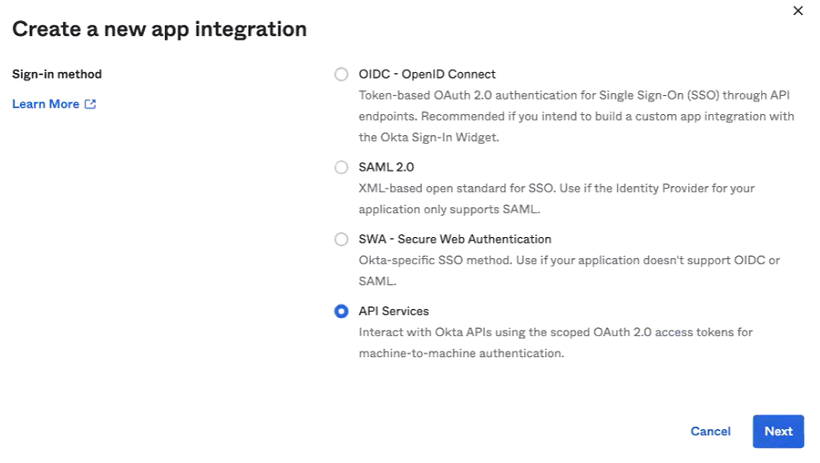
- On your Okta admin panel, go to Applications > Applications.
- Then click on Create a new App Integration.
- In this screen, select the API Services option and click Next.
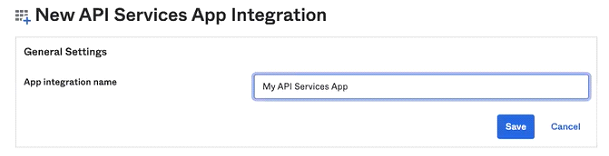
- In the App integration name field, enter a name for the app and click Save.
- Under Client Credentials, click the Copy button next to the Client ID and keep it for later.
- Then, under Client Credentials, click Edit.
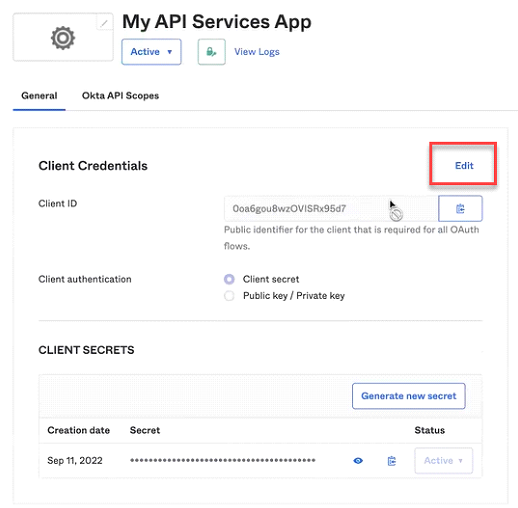
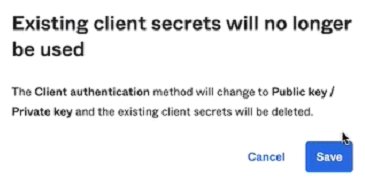
- In the Client authentication setting, select Public key/Private key.
- Under Public Keys, click Add Key.
- Click Generate new key.
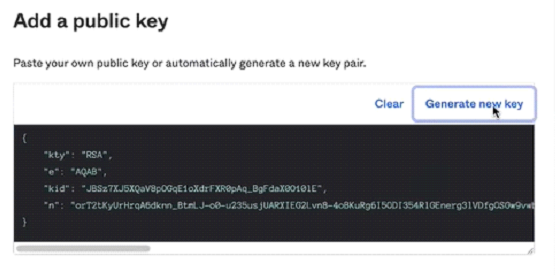
The private key is displayed on the screen.
- In the Private key section, click Copy to clipboard and click Done.
- Click Save and Save again to acknowledge the notice.
- Click the Okta API Scopes tab.
- Grant permissions to the following scopes:
okta.users.read
okta.users.manage
okta.groups.manage
okta.groups.read
- If you wish to manage admin roles as well, please add the following API scopes:
okta.roles.manage
okta.roles.read
- If you wish to manage applications assignments as well, please add the following API scopes:
okta.apps.read
okta.apps.manage
Step 2 – Configure the Service App details on Entitle (Entitle side)
At this point, you are ready to enter the App Integration details in Entitle. This step assumes that you have created a new Okta integration in Entitle. For more information on how to create a new integration, see the relevant section in the Entitle User Guide.
To configure the Service App on Entitle:
- As part of creating a new Okta integration in Entitle, on the Add Integration screen, click the Service App tab.
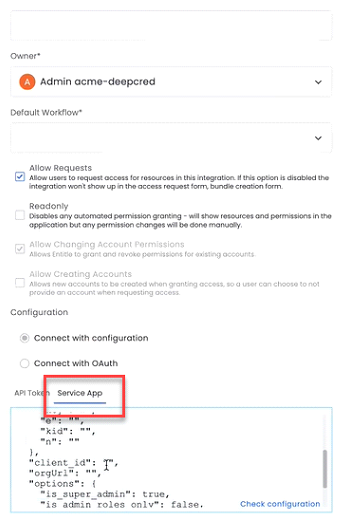
- In the configuration window add the following information between the double quotes:
- client_id – paste the client ID that you have saved in step 6 of the previous section.
- orgUrl – enter the full domain of your Okta admin-panel, including the ‘https://’ (e.g., https://xxxxx.okta.com).
- jwk – place the different segments of the previously saved private key between the double quotes of the corresponding segments.
- If you want to enable the Partial functionality option, under the options section, enter the value false _in the _is_super_admin option.
- If you want to restrict Entitle to manage only Admin Roles and Custom Admin Roles only (i.e., not group membership), under the options section, enter the value true in the is_admin_roles_only option.
- If you want Entitle to use Okta's "group constraints" feature, which enables granting specific roles within a particular group, enter the value true in the include_role_constraints option.
- If you have an API Access Management role in Okta and you want Entitle to manage this role, enter the value true in the api_acess_management option.
- Configure the required additional fields and click Save.
2. API Token Authentication
This process involves creating an API Token on the Okta side and then entering this token on the Entitle side. Each user with any admin privileges can create a token. However, the token will have the user’s permissions.
Entitle's permission scope options
There are two permission scope options:
- Full functionality – To access all the features that Entitle provides, you must have “Super Admin” role (the roles are derived from the user who creates the token) while creating the token, as only Super Admins are allowed by Okta to manage other users or groups that have admin privileges.
- Partial functionality - it is possible to use “Group Membership Admin” and “Report Admin” roles together to enable basic functionality. In this case, you won’t be able to give/revoke access or even read any admin roles. This includes adding users to groups with admin roles. To enable this option, you must set the “is_super_admin” option to 'false'.
It is also possible to restrict additional scopes by following the instructions in the section below.
Step 1 - Create an API Token (Okta side)
If you want to create the token for Partial functionality option, make sure the token's Admin Role setting is configured as “Group Membership Admin” and “Report Admin” roles.
To create an API token:
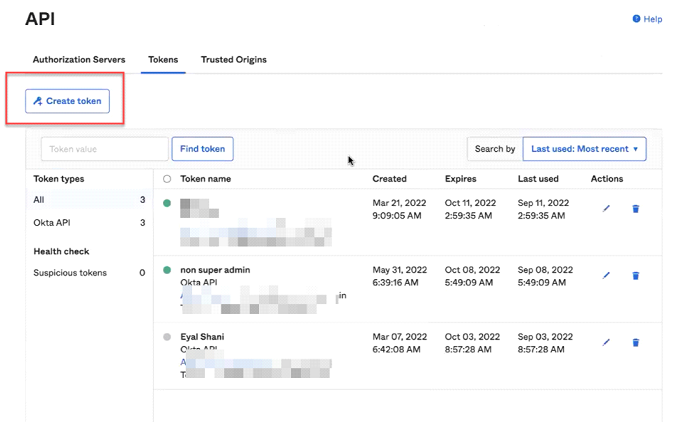
- On your Okta admin panel, go to Security > API > Tokens tab.
- Click on Create Token.
The following prompt is displayed:
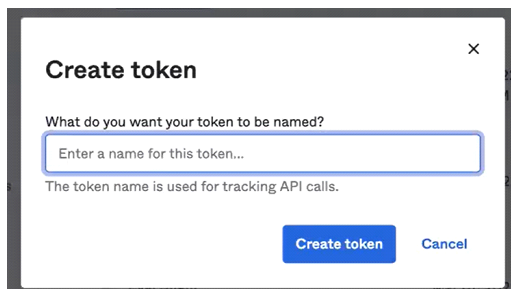
- Enter a name for the token.
- Click Create Token.
- Copy the token value by clicking the Copy button and proceed to the next section.
Step 2 – Configure the API Token on Entitle (Entitle side)
At this point you are ready to enter the API token in Entitle. This step assumes that you have created a new Okta integration in Entitle. For more information on how to create a new integration, see the relevant section in the Entitle User Guide.
To configure the API Token on Entitle:
-
As part of creating a new Okta integration in Entitle, on the Add Integration screen, scroll down to the Configuration section and select the Connect with configuration option.
-
In the configuration window make sure that the API Token is selected and add the following information between the double quotes:
- token – paste the previously saved API Token.
- orgUrl – enter the full domain of your Okta admin-panel, including the ‘https://’ (e.g., https://xxxxx.okta.com).
-
If you want to enable the Partial functionality option, under the Options section, enter the value false _in the _is_super_admin option.
-
If you want to enable the applications, under the Options section, enter the value true in the include_apps option.
-
If you want to restrict Entitle to manage only Admin Roles and Custom Admin Roles only (i.e., not group membership), under the Options section, enter the value true _in the _is_admin_roles_only option.
-
If you want Entitle to use Okta's "group constraints" feature, which enables granting specific roles within a particular group, enter the value true in the include_role_constraints option.
-
If you have an API Access Management role in Okta and you want Entitle to manage this role, enter the value true in the api_access_management option.
-
Configure the required additional fields and click Save.
The configuration should be as described below:
{
"orgUrl": "",
"token": "",
"manager_email_field_name": "",
"options": {
"is_super_admin": true,
"is_admin_roles_only": false,
"include_apps": false,
"include_role_constraints": true,
"api_access_management": true
}
}
Note
If you wish to manage applications assignments or administrative roles, and you added the required API scopes to your application in Okta, following steps 14, 15 in stage 1 - please make sure you set the
'is_admin_roles_only'and/or'include_apps'totrue.
Updated 9 months ago
