Configure RADIUS two-factor authentication | BI On-prem
What is RADIUS two-factor authentication?
RADIUS two-factor authentication is a security method that adds an extra layer of verification when users log in to BeyondInsight or Password Safe. It uses the RADIUS (Remote Authentication Dial-In User Service) protocol to communicate with an external authentication server, which can require a second factor—such as a one-time password (OTP), mobile app verification, or hardware token—on top of the regular username and password. This ensures that even if a password is compromised, unauthorized users cannot gain access without the second authentication factor.
How is it useful?
it significantly enhances security by requiring a second form of verification in addition to a password. This reduces the risk of unauthorized access, even if a password is compromised, and helps organizations protect sensitive systems and data. It also allows integration with existing RADIUS-compliant authentication servers, enabling centralized management of two-factor authentication policies across the organization.
You can configure two-factor authentication using a RADIUS server to log in to the BeyondInsight management console, Analytics & Reporting, and Password Safe.
In BeyondInsight, you must first configure the alias to represent the RADIUS server instance, and then select two-factor authentication settings for the user.
After you set up RADIUS two-factor authentication, users must log in to BeyondInsight or Password Safe using the configured two-factor authentication method.
Configure the RADIUS server
To configure the RADIUS server instance for two-factor authentication in BeyondInsight, follow the below steps.
-
Open a browser and enter the URL for your Password Safe instance: https://<hostname>/WebConsole/index.html.
-
Enter your username and password.
-
From the left menu, click
 .
.
The Configuration page displays. -
Under Authentication Management, select Radius two-factor authentication.
The RADIUS page displays. -
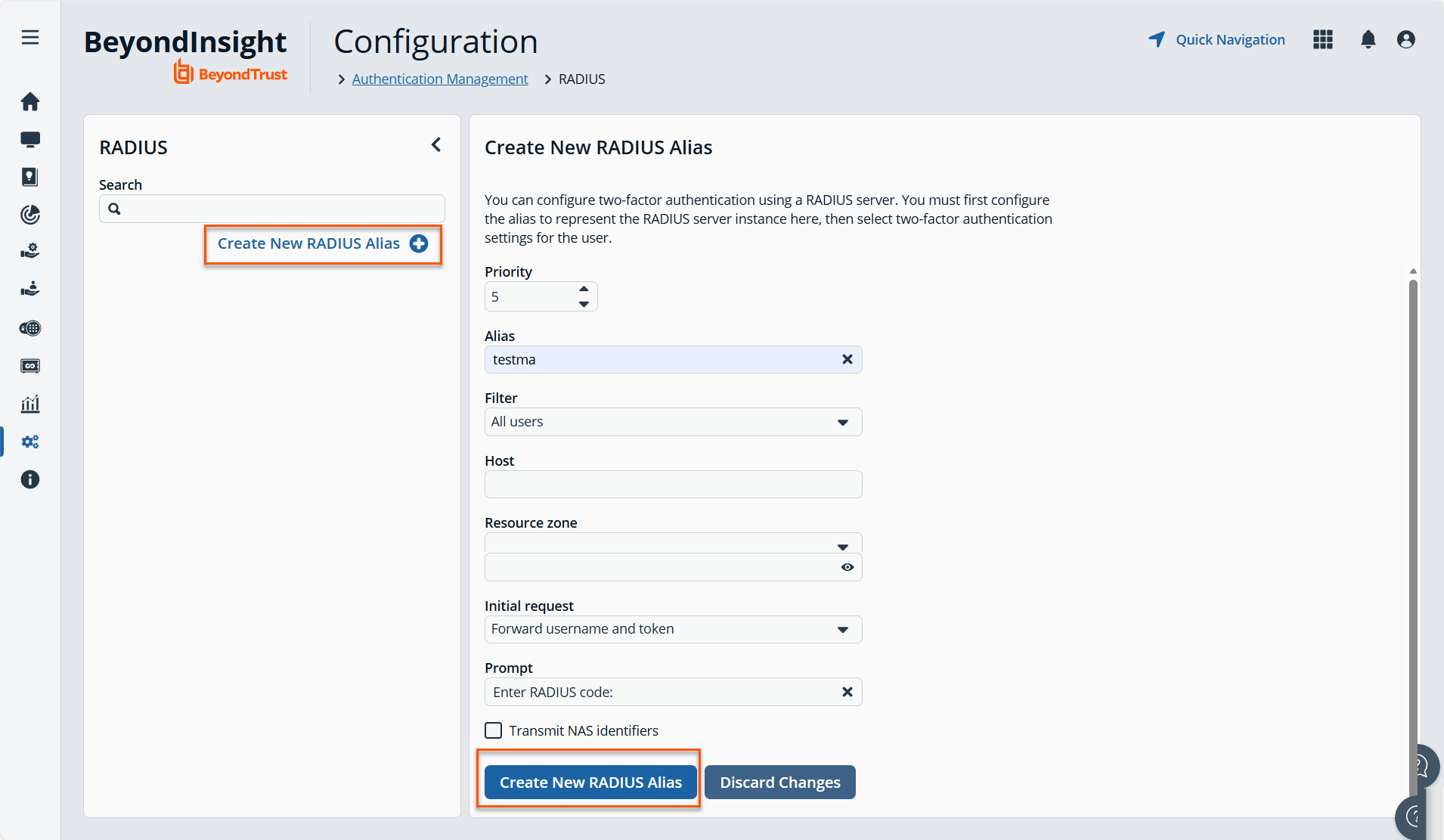
Click Create New RADIUS Alias.
-
Set the following:
- Alias: Provide a name used to represent the RADIUS server instance. This is displayed in the RADIUS server grid and must be unique.
- Filter: Select a filter that will be used to determine if this RADIUS server instance should be used. If you select one of the domain filters, you must enter a Value.
- Value: If one of the domain filters is selected, enter a value that will identify the domain. Enter a domain or comma-separated list of domains, depending on the setting selected for the filter.
- Host: Enter the DNS name or the IP address for your RADIUS server.
- Resource Zone: Select a Resource Zone to send RADIUS requests through. Traffic proxies through the Resource Broker and on to the on-prem RADIUS server.
- Authentication Mechanism: Select PAP, or MSCHAPv2 if applicable. MSCHAPv2 is supported only if the Duo proxy is configured to use a RADIUS client.
- Authentication Port: Enter the listening port that is configured on your RADIUS server to receive authentication requests. The default port is 1812.
- Authentication Request Timeout: Enter the time in seconds that you want BeyondInsight to wait for a response from the RADIUS server before the request times out. The default value is ten seconds.
- Shared Secret: Enter the shared secret that is configured on your RADIUS server.
- Initial Request: Provide the value passed to the RADIUS server on the first authentication request. Select from the following: Forward User Name (default), Forward User Name and Password, Forward User Name and Token.
- Prompt: Provide the first message that displays to the user when they log in to the application. This setting is available only when Forward User Name and Token is selected as the initial request value.
- Transmit NAS Identifiers: Enable this option if it is applicable to your environment. When this option is enabled, NAS identifiers are transmitted to permit access. In some cases, a RADIUS server does not permit access if NAS identifiers are not transmitted. BeyondInsight transmits its NAS IP Address and its NAS Identifier.
-
Click Create New RADIUS Alias.
If a Resource Zone is selected, traffic is routed over a Resource Broker. If no Resource Zone is selected, traffic is routed directly from the cloud.
Configure RADIUS two-factor authentication using Duo
This section is a high-level overview on the configuration required for BeyondInsight and Password Safe to work with a RADIUS infrastructure using Duo.
BeyondInsight and Password Safe can work with the following Duo configurations:
- RADIUS Auto
- RADIUS Challenge
- RADIUS Duo only
Configure two-factor for RADIUS Auto and RADIUS Challenge using Duo
Follow the steps outlined above in Configure the RADIUS server, using the following settings:
- For Alias, enter Duo.
- For Authentication Mechanism, select PAP.
- For Initial Request, select Forward User Name and Password.
Configure two-factor for a RADIUS Duo-only configuration
Follow the steps outlined above in Configure the RADIUS server, using the following settings:
- For Alias, enter Duo.
- For Authentication Mechanism, select PAP.
- For Initial Request, select Forward User Name and Token.
- For Initial Prompt, enter a message to display on the BeyondInsight login page to provide guidance to users on the information to enter. In this case, the user must enter the RADIUS code.
ExampleDuo-Only Login Page
After RADIUS two-factor authentication is configured, the login page for the end user varies, depending on the configured settings.
The screenshot shows a login page configured for Duo-only authentication. The user can enter a passcode to log in or select a device to send a code to. The user then enters the code on the login page.
Configure alternate directory attribute for RADIUS
To configure an alternate directory attribute for Active Directory and LDAP users for RADIUS authentication, follow the below steps.
This setting is optional.
Open a browser and enter the URL for your Password Safe instance: https://<hostname>/WebConsole/index.html.
- Enter your username and password.
- From the left menu, click
 .
.
The Configuration page displays. - Under Authentication Management, select Authentication Options.
The Authentication Options page displays. - Under RADIUS Two-Factor Authentication, set the following:
- Alternate directory attribute: Enter the Active Directory or LDAP attribute that is matched on the RADIUS server to identify the user account. This can be any attribute in Active Directory or LDAP. The default value is extensionName.
- Enable for new directory accounts: Click the toggle to enable this attribute for new accounts when they are discovered.
- Click Save.
Apply RADIUS two-factor authentication to user accounts
The type of two-factor authentication can be set on a user account when a new user is created or when editing an existing user account. You can enable RADIUS two-factor authentication for all new users from Authentication Options > RADIUS Two-Factor Authentication settings, as indicated in the above section.
- Open a browser and enter the URL for your Password Safe instance: https://<hostname>/WebConsole/index.html.
- Enter your username and password.
- From the left menu, click
 .
.
The Configuration page displays. - Under Role Based Access, select User Management.
The User Management page displays. - Select the Users tab.
- To create a new user, click Create New User. Select Create a New User.
- To edit an existing user, locate the user in the grid. Click
 > Edit User Details.
> Edit User Details.
- At the bottom of the user account settings, select RADIUS from the Two Factor Authentication dropdown.
Using multiple RADIUS servers
If you have multiple RADIUS servers, they are processed from the lowest priority to highest. The DUO server is first. If BeyondInsight connects to that server, no other servers are checked.
If BeyondInsight cannot connect to the first server (DUO), then a connection is attempted with the next server (DUO2) in the list (the next highest priority number). Each server is checked until a connection is made or all servers available have been tried.
Updated about 2 months ago

