Configuration: Claims-aware website | BI Cloud
What is a claims-aware website?
A claims-aware website is a BeyondInsight configuration that allows users to authenticate through a federated identity provider using SAML-based claims instead of the standard login page. When enabled, the website redirects users to a configured Federation Service, which issues authentication claims. These claims are then used by BeyondInsight to verify group membership and permissions. If the claims match a defined group with the proper access rights, the user is automatically logged in. Otherwise, the user is redirected to the standard BeyondInsight login page.
How is it useful?
A claims-aware website enables seamless, secure authentication through a federated identity provider using SAML claims. This allows organizations to centralize user authentication and leverage existing identity management systems, such as Active Directory Federation Services (ADFS) or Entra ID. It simplifies user access by bypassing the standard BeyondInsight login page for authorized users, automatically creating or updating accounts based on claim information, and ensuring users are assigned to the correct groups and permissions. This improves both security and user convenience while reducing administrative overhead.
Configure a claims-aware website to log in with SAML
You can configure a claims-aware website to bypass the current BeyondInsight login page and authenticate against any configured Federated Service that uses SAML to issue claims.
The claims-aware website is configured to redirect to a defined Federation Service through the web.config. Upon receiving the required set of claims, the user is redirected to the existing BeyondInsight website. At that point, it is determined if the user has the appropriate group membership to log in, given the claims associated with them.
If users attempting to access BeyondInsight have group claims matching a group defined in BeyondInsight, and the group has the Full Control permission to the Management Console Access feature, the user bypasses the BeyondInsight login screen. If the user is new to BeyondInsight, they are created in the system using the same claims information. The user is also added to all groups they are not already a member of that match in BeyondInsight, and as defined in the group claim information.
If the user is not a member of at least one group defined in BeyondInsight or that group does not have the Full Control permission to the Management Console Access feature, they are redirected to the BeyondInsight login page.
Create a BeyondInsight group
Create a BeyondInsight group and ensure the group is assigned the Full Control permission to the Management Console Access feature.
For more information, see Create a BeyondInsight local group.
Add relying party trust
After BeyondInsight is installed, metadata is created for the claims-aware website. Use the metadata to configure the relying party trust on the Federation Services instance.
The metadata is located in the following directory:
<Install path>\eEye Digital Security\Retina CS\WebSiteClaimsAware\FederationMetadata\2007-06\
When selecting a Data Source in the Add Relying Party Trust Wizard, select the FederationMetadata.xml generated during the install.
Set up claim rules
Claims rules can be defined in a number of different ways. The example provided is simply one way of pushing claims to BeyondInsight. As long as the claims rules are configured to include at least one claim of outgoing type Group (with Group claim matching exactly what is in BeyondInsight) and a single outgoing claim of type Name, then BeyondInsight has enough information to potentially grant access to the site to the user.
Claims-aware SAML
The following procedure demonstrates how to set up a claims-aware website using the Windows Identity Foundation (WIF) SDK.
- Start the Windows Identity Foundation Federation Utility.
- On the Welcome page, browse to and select the web.config file for BeyondInsight Claims Aware site. The application URI automatically populates.
- Click Next.
- Select Using an existing STS.
- Enter Root URL of Claims Issuer or STS.
- Select Test location. FederationMetadata.xml is downloaded.
- Click Next.
- Select a STS signing certificate option, and then click Next.
- Select an encryption option, and then click Next.
- Select the appropriate claims, and then click Next.
- Review the settings on the Summary page, and then click Finish.
Disable forms login
In environments where SAML, smart card, or claims-aware is configured, we recommend enabling the Disable Forms Login authentication option to disallow users from using the standard login form in BeyondInsight.
To disable forms login for existing users, enable this option directly on a user account as follows:
-
Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. -
From the left menu, click
 .
.
The Configuration page displays. -
Under Role Based Access, select User Management.
The User Management page displays. -
Select the Users tab.
-
Locate the user account in the grid.
-
Click
 > Edit User Details.
> Edit User Details. -
Under Authentication Options, check Disable Forms Login to enable the option.
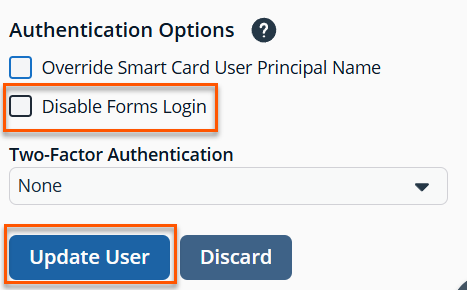
Contact BeyondTrust Support for assistance if you need to bulk-apply this setting to existing accounts.
To disable forms login globally for newly created directory accounts:
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays. - Under Authentication Management, select Authentication Options.
The Authentication Options page displays. - Under Forms Login Options, check the Disable Forms Login for new directory accounts option to enable it.
- Click Save.
Updated 28 days ago

