Assets: Overview | BI Cloud
What is an asset?
Assets refer to any IP addressable device that exists in your environment (that is, desktop machine, network device, or any of several supported platforms).
How is asset management useful?
Asset management is necessary for several reasons:
- Network Visibility & Inventory Management – Keeping track of all assets ensures that organizations have a clear understanding of what devices are connected to their network, preventing unauthorized or unknown devices from posing security risks.
- Security & Compliance – Identifying and monitoring assets helps enforce security policies, ensuring compliance with regulations and detecting vulnerabilities before they can be exploited.
- Risk Management – Understanding what assets exist allows organizations to assess risks associated with each device, apply necessary patches, and implement security measures to reduce potential threats.
- Incident Response – When a security incident occurs, knowing the assets in the environment helps in tracing the source of the issue, containing the attack, and implementing remediation steps.
- Lifecycle Management – Organizations can track asset lifecycles, plan for hardware refreshes, software updates, and decommission obsolete devices.
How do I access assets?
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Assets page displays.
The Assets home page
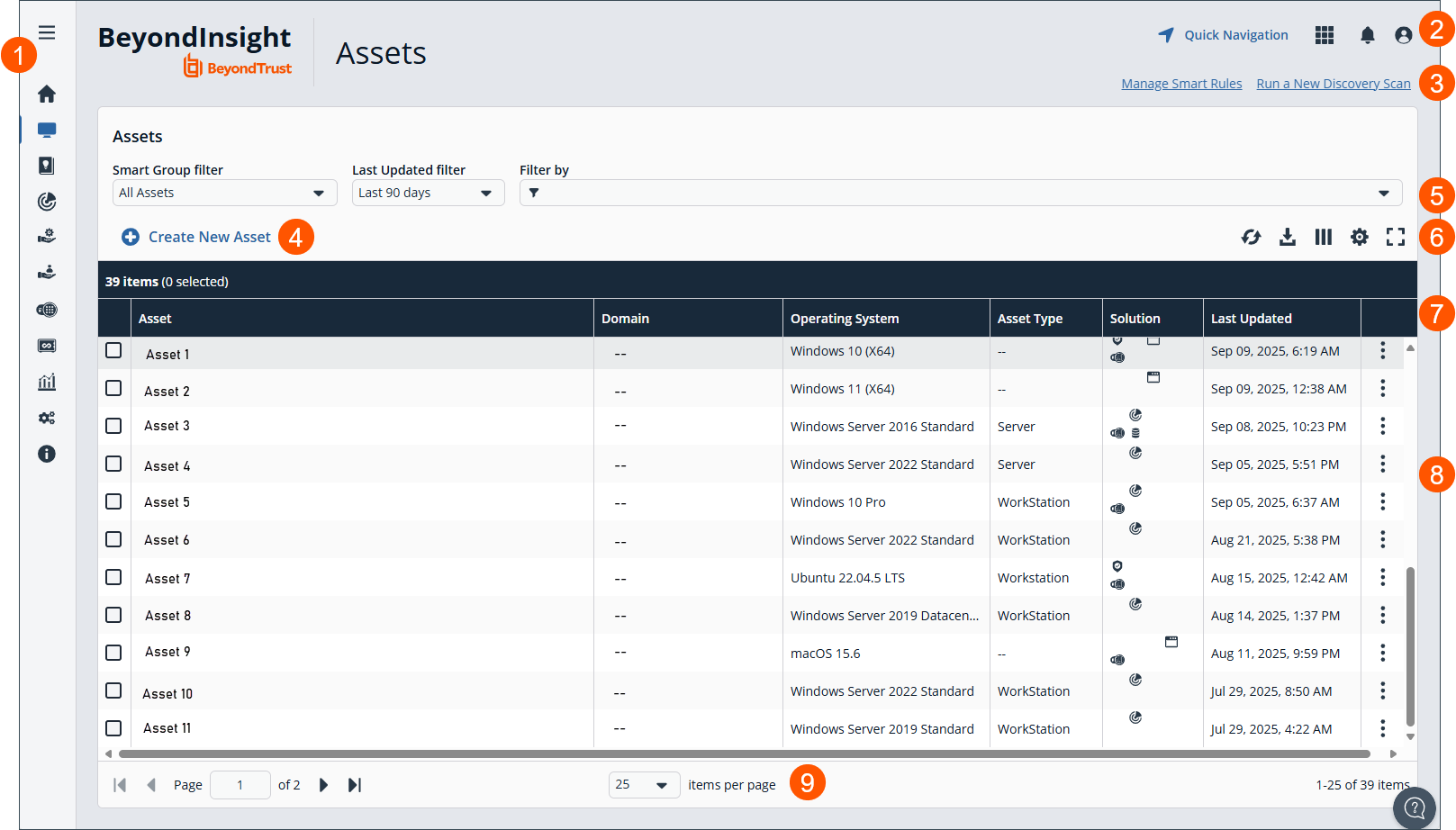
- Left menu: Easy access to all pages in BeyondInsight/Password Safe, including the Home, Assets, Smart Rules, Discovery Scanner, Management Systems, Managed Accounts, Password Safe, Secrets Safe , Analytics and Reporting, Configuration, and About pages.
- Header: Navigate to your favorite pages, view your notifications, access your connected apps, and set your account preferences.
- Select to Manage Smart Rules or Run a New Discovery Scan.
- Create New Asset: Click to create a new asset.
- Filters: Select a filter to refine your results.
Filter types
-
Smart Group filter: Filter by Smart Groups.
-
Last Updated filter: Filter by last updated timeframe.
-
Filter by: Filter by Asset, Domain, Operating System, Description, Asset Type, Solution, DNS Name, Workgroup, or IP Address.
-
- Grid display preferences: Set display preferences on the Assets grid using the following options represented by icons above the grid:
- Click
 to refresh the list,
to refresh the list,  to download the list to a .csv file,
to download the list to a .csv file,  to select which columns to display on the page,
to select which columns to display on the page,  to configure your page display, and
to configure your page display, and to expand the grid.
to expand the grid.
- Click
- Asset list columns: Not all columns display in the image above.
Column Names
-
Asset
-
Domain
-
Operating System
-
Description
-
Asset Type
-
Solution
-
Last Updated
-
Created
-
DNS Name
-
Workgroup
-
IP Address
-
- Assets grid: Displays information based on filter selections.
- List navigation options: Navigate in the Assets list.
Core concepts to understand before you add assets
Before you start to onboard assets to your environment, you should have a brief understanding of the following accounts and systems that are used.
| Account or System Name | Description |
|---|---|
| Functional account | A functional account is one that can access the system with the privileges required to manage and change passwords for shared accounts on the system. |
| Managed System | A managed system is a computer or device where one or more account passwords are to be maintained by Password Safe. Managed systems can be Windows computers, Unix or Linux computers, network devices, databases, firewalls, routers, iLO computers, and LDAP or Active Directory domains. For more information about managed systems, see Managed systems. |
| Managed Accounts | A managed account is an account on the managed system whose password is being stored and maintained through Password Safe. Typically, managed accounts are privileged accounts that can perform administrative tasks on the managed system. For more information about managed accounts, see Managed accounts. |
| Smart Rules | A Smart Rule is a query that you can use to organize assets into Smart Groups and manage Password Safe managed accounts. Use a Smart Rule to organize assets based on the filters selected. For more information about managed accounts, see Smart Rules. |
| Smart Groups | Smart Groups are a collection of managed assets, managed systems, or assets defined by a Smart Rule. For more information about managed accounts, see Smart Groups. |
| Role-based access | Explicitly assign permissions to groups on specific product features based on their role. Users are provisioned based on the permissions of their assigned groups. You want to start by creating a user group with either the Approver or Requestor role, then create an access policy to permit accounts to access the systems, applications, and sessions, and to request password releases. For more information about role-based access, see Role-based access. |
Add Assets to Password Safe Cloud
Once assets are managed by Password Safe, selected users can request access to them. For details on adding specific systems, search for the particular system using the Search field.
There are three ways to add systems and accounts to Password Safe:
- Add the asset manually.
- Run a Discovery Scan and then import the assets using an address group or directory query.
- Use API scripts.
To maintain a manageable database size, assets and scan data is purged every 30 days. We recommend running discovery scans at least every 30 days to refresh asset data.
Create a functional account
A functional account on a managed system is required to manage passwords for accounts on that managed system. The passwords for functional accounts cannot be retrieved through the Password Safe web portal.
Important informationDo not set up a functional account as a managed account. Functional accounts have built-in management capabilities and passwords might fail to synchronize, causing issues.
The settings vary, depending on the type and platform chosen.
-
From the left menu, click
 .
.
The Configuration page displays. -
Under Privileged Access Management select Functional Accounts.
The Functional Accounts page displays. -
Click + Create New Functional Account.
The Create New Functional Account panel displays. -
Select a type from the list.
-
Select a platform from the list.
DSS authentication and Automatic password management settings are not supported if you are using the pbrun jumphost elevated credential.
- Provide credentials and a description for the account.
- Provide an alias. The Alias value is shown in the selectors throughout Password Safe where you must select a functional account to use.
- Select a Workgroup, if applicable.
- If required, enable Automatic Password Management.
- Select the password policy and change frequency. This option enables automatic password changes for each managed system that this functional account is associated with at the designated frequency.
If the Automatic Password Management option is enabled, passwords are set immediately when a new functional account is added to Password Safe.They are changed during the next scheduled rotation.
- Click Create Functional Account.
Override a functional account password
Every managed system that uses a specific functional account has a unique password associated with that functional account. The password on the managed system might be out of sync with the password in Password Safe. You can override a functional account password from the Functional Account section in the Advanced Details of a managed system.
Add a managed system manually
Settings vary depending on the platform type. When an account is manually added to a managed system, the default configuration of the account is set to what is configured on the managed system.
There are two ways to add a managed system to Password Safe manually:
- From the left menu, click
 .
.
The Managed Systems page displays. - Click Create New Managed System.
- Complete the Create New Managed System form.
- Click Create Managed System.
OR
- From the left menu, click
 .
.
The Assets page displays. - Locate the asset you want to add to the managed system.
- Click
 > Add to Password Safe.
> Add to Password Safe. - Complete the Create New Managed System form.
- Click Create Managed System.
Below are the fields and settings with their descriptions that are available when creating a new managed system. The available fields change depending on the Entity Type and Platform for the system.
| Field / Setting | Description or Action |
|---|---|
| Entity Type | Type of system: Asset, Database, Directory, or Cloud. |
| Platform | The platform for the system based on the Entity Type. |
| Name | Unique name for the system. |
| Port | Default RDP port for new managed systems. |
| Instance Number (SAP only) | If you have added your System Application Products (SAP) environment to Password Safe management, provide the instance number. |
| Domain (Directory types only)** | Name of the Domain where the directory resides. |
| Description | Description for the system. |
| DNS Name | DNS name for the system. |
| IP Address | IP address for the system. |
| Allow Managed System to be an Application Host (non-Windows systems only)** | Toggle on or off to allow the system to be an application host. |
| NetBIOS Name (Windows, Active Directory, and LDAP systems only)** | Unique NetBIOS name for the system. |
| Workgroup | Select a pre-defined workgroup from the list. |
| Port | Enter a port number. |
| Automatic Password Change Options | Toggle Enabled to automatically check and update managed account passwords at a set frequency or after password releases. |
| Password Policy | Select a Password Safe password policy or use the default policy. The policy provides the requirements used by Password Safe to create passwords, such as password length and permitted characters. |
| Change Agent (available only when Endpoint Privilege Management is installed)** | Select Password Safe or Endpoint Privilege Management client from the list. |
| Elevation | Select an elevated account to run as: sudo, pmrun, pbrun, pbrun jumphost. If you are using pbrun jumpost, enter the IP address for the Privilege Management for Unix & Linux policy server that you want to connect to. SSH Key Enforcement Mode is not available if you are using pbrun jumphost. |
| Change Agent (available only when Endpoint Privilege Management is installed)** | Select Password Safe or Endpoint Privilege ManagementClient from the list. |
| Functional Account | Select a functional account from the list. If a functional account is not available, click the Create New Functional Account link. The link is located in two places, below the dropdown and within the dropdown list. This allows you to create a functional account without leaving the Managed Systems page. The Create New Functional Account link is available to users with the Password Safe Configuration Management feature permission. |
| Use Login Account for SSH Sessions | Create a login account to allow the user to open an SSH session in environments where remote shell access is not permitted, for instance the root account. Login Account: Select the account name. |
| Account Name Format (For Windows, Linux, Oracle, MS SQL Server, and Active Directory only)** | Select a format for the account name from the list: Domain\Account, UPN: accountName@domainName, or sAMAccountName: Account Name only. |
| Timeout | The timeout value determines the amount of time in seconds that a connection attempt to the managed system remains active before being aborted. In most cases, we recommend you use the default value (30 seconds). If there are problems with connection failures with the system, this value can be increased. |
| SSH Key Enforcement Mode | Verifies SSH host keys from a known host. You can import SSH keys from a host using a Smart Rule. Auto Accept Initial Key: The first key imported is automatically accepted. Any new key imported after the initial key must be manually accepted. Manually Accept Keys: SSH connections to the host are permitted for accepted keys only. If a new key is detected from the host, the key is stored in the database and an email is sent to the Administrators user group. The key must then be accepted or denied. |
| Default DSS Key Policy | If you are using DSS authentication for the system, select a key policy or use the default. |
| Release Duration | The duration that can be requested during the request process. The default value is 2 hours. When the Requested Duration (as entered by the user on the Requests page in the web portal) is exceeded, the session ends if the Force Termination option is enabled for the access policy. |
| Max Release Duration | The maximum length of time the requester is permitted to enter on the Requests page. Applies to password and session requests. The maximum length that can be set is 365 days. |
| Contact e-mail | Enter the email address where you want Password Safe system notifications to be sent. |
Add managed systems and accounts using Smart Rules
You can add assets to Password Safe using an asset-based Smart Rule.
- Before proceeding, consider the selection criteria to use to add the assets. There are several options available, including Operating System and Directory Query.
- SSH key enforcement is not supported when using the pbrun jumphost elevated credential. The settings display as available after pbrun jumphost is selected. However, the settings will not work with the elevated credential.
- From the left menu, click
 .
.
The Smart Rules page displays. - Select Asset from the Smart Rule type filter.
- Click + Create Smart Rule.
- Select a Category from the dropdown.
- Enter a Name and Description for the Smart Rule.
- Select a Reprocessing Limit from the dropdown to limit how often the Smart Rule processes.
Default means the Smart Rule processes when necessary. This is the preferred setting for less intensive processing. For more intensive processing select another option to restrict the Smart Rule to run once per selection.
A Smart Rule always processes when first saved or updated.
- Set the Selection Criteria under Include Items that match the following.
- Select filter criteria from the list.
- If required, click Add Another Condition.
- Select Manage Assets Using Password Safe under Actions.
- Select the Platform, Functional Account, and Account Name Format under Actions. Other settings may be left as defaults or changed as required.
- Click Add another action.
- Select Show managed account as Smart Group.
- Click Create Smart Rule.
- The Managed System Descriptions setting is available for Active Directory only.
- These settings are the same settings available when adding the system manually by creating a new managed system.
- To view contents of a Smart Rule when creating a new rule or editing an existing rule:
- Once the rule is saved, click View Results.
- You are taken to the associated grid, where the contents of the Smart Rule are listed.
- If the rule is actively processing, a banner displays letting you know that.
- View Results displays only if you have permissions to the grid corresponding to the Smart Rule, i.e.; Assets, Managed Accounts, Managed Systems.
- The Smart Rule must be saved with Show <entity> as Smart Group selected under Actions to view the results.
- Because the Smart Rule must process to display the contents in the grid, we recommend viewing the results using only the Show <entity> as Smart Group action and before adding additional actions that may make changes to accounts and assets in your network. Once you have confirmed the rule contains your desired items, you can then add additional actions to the Smart Rule.
Add Active Directory managed accounts using a Smart Rule
You can create a Smart Rule that discovers and adds Active Directory accounts to Password Safe, using the below procedure. The procedure also shows how to link domain accounts to the system.
A directory query and a domain should be created prior to creating a Smart Rule.
- From the left menu, click
 .
.
The Smart Rules page displays. - From the Smart Rule type filter list, select Managed Account.
- Click + Create Smart Rule.
- Select a Category from the dropdown.
- Enter a Name and Description for the Smart Rule.
- Select a Reprocessing Limit from the dropdown to limit how often the Smart Rule processes.
Default means the Smart Rule processes when necessary. This is the preferred setting for less intensive processing. For more intensive processing select another option to restrict the Smart Rule to run once per selection. - Select the Selection Criteria as applicable:
- Asset Smart Group: Select a Smart Group from the list.
- Child Smart Rule: Select a Smart Rule you want to filter the child Smart Rules from.
- Dedicated Account: Select an account filter from the list. Enter a keyword to search on.
- Directory Query: Choose to Include or Exclude accounts from Directory Query.
- Select a query from the list, or click Create New Directory Query to open the form and create a new query.
- Provide the frequency for the query to run. Leave the entry as 0 for a one time run.
- Enable the Discover accounts for Password Safe Management option to discover accounts when the Smart Rule processes.
- Select a Domain from the list.
- Managed Account Fields: This filter only applies to existing managed accounts.
- Select a filter: Account Name, Create Date, Description, Domain Name, Last Change Date or Last Change Result.
- Select an expression, and then enter a keyword to search on, for example, WIN for Windows.
- Managed System Fields: The Smart Rule is filtered according to the managed system you select.
- Select a filter: System Name, Create Date, Last Update Date.
- Select an expression, and then enter a keyword to search on, for example, WIN for Windows.
- Platforms: Select a platform or check Select All.
- User Account Attribute: Select the attribute from the list, and then provide the filter condition and value for that attribute. For each attribute filter, select Yes for Discover accounts for Password Safe Management, and then select a Smart Group to search in.
- Privilege: Select is one of or is not one of. Select All or one, or a combination of Administrator, Guest, or User.
- SID: Select an expression, and then enter a keyword to search on.
- Account Name: Select an expression, and then enter a keyword to search on.
- Password Age: Select an expression, and then select age parameters to search on.
- Select Manage Account Settings under Actions to add the accounts that match on the criteria to Password Safe. The settings are the same when you add the accounts manually.
- Additional properties can be set under Actions:
- Assign preferred Domain Controller on each Active Directory account: Select the Active Directory domain and Domain Controller from the lists.
- Assign workgroup on each account: Used with agent workgroups in multi-active deployments, this action enables you to define groups of accounts that will be assigned to specific password change agents. Select a workgroup from the list, or select Any.
- Link domain accounts to Managed Systems: When used with Directory Accounts filter criteria, this action creates a linked association between the directory accounts and the target asset Smart Groups for role-based access control.
- Link managed accounts to Remote Applications: Assigns the application(s) to any managed accounts that match the Session Criteria.
- Map Dedicated Accounts To: Use only when the Dedicated Accounts filter criteria is selected. This action identifies the group of user accounts that are used to match against the dedicated account mask condition.
- Send an email Alert: Select to send an email alert when the Smart Rule processes. The email contains a summary of the results the managed accounts matched by the Smart Rule and any changes since its last execution.
- Set attributes on each account: Select to assign an attribute to filter and sort managed accounts. When viewing the Smart Groups on the Managed Accounts page, the groups are organized based on the filters selected in the Smart Group. You can use the default attributes that are available or create an attribute on the Configuration page. When the Smart Rule runs, the attribute is applied to all managed accounts that match on the selected filter criteria.
- Click Add another action.
- Select Show managed account as Smart Group.
- Click Create Smart Rule.
Add Endpoint Privilege Management for Windows systems and local accounts into Password Safe
The integration between Password Safe and Endpoint Privilege Management for Windows (EPM) allows for agent-based local account password rotation and privileged account retrieval to run as actions for accounts on Windows systems where an EPM agent is running.
Prior to BeyondInsight 24.1, EPM agents could only use certificates to authenticate with BeyondInsight. You can download the certificate from Configuration > System > Downloads > Download Client Certificate in the BeyondInsight console. BeyondInsight configuration segments can be included in the EPM policy to enable policy management from one console and password policy from Password Safe.
Use installer activation keys to leverage OAuth authentication when configuring:
- Endpoint Privilege Management (EPM) agents that support OAuth communications.
- Discovery Scanner event client and central policy.
In Endpoint Privilege Management for Windows, features to support Password Safe integration include:
- Off-network account management: The EPM agent contacts Password Safe for password tests or password changes.
- Allow as Password Safe user: You can run an application using managed account credentials sourced from Password Safe.
Discover local accounts on EPM Windows systems
For 22.4 and later releases of Password Safe in conjunction with the Endpoint Privilege Management for Windows 22.9 EPM agent, discovery can be performed by the EPM agent on the EPM Windows system on a scheduled basis, eliminating the need to run a discovery scan in BeyondInsight. The EPM agent, running on a Windows system, publishes local user data to the Assets grid in BeyondInsight. You can then add the local accounts to Password Safe using a Smart Rule or add them manually.
For Password Safe releases prior to 22.4, you can add well-known local admin accounts into Password Safe using a Smart Rule, eliminating the need to run a discovery scan in BeyondInsight, as documented in the next section.
Add known local admin managed accounts using a Smart Rule
It can be useful in some cases to onboard well-known local admin accounts, such as the Windows administrator or the Linux root account, from endpoints into Password Safe without the need to run a discovery scan against the endpoints. You can create a managed system Smart Rule that uses the Create Managed Account on each system action to accomplish this.
One scenario in which this is useful is when you have Endpoint Privilege Management (EPM) clients in your environment. You can create a managed system Smart Rule to add local accounts as managed accounts from the EPM client endpoints so that a password rotation event exists when the EPM agent requests it. Having these preconfigured managed accounts saves time by not having to configure and run a discovery scan after the EPM agent makes the request.
Create the Smart Rule as follows:
- From the left menu, click
 .
.
The Smart Rules page displays. - From the Smart Rule type filter list, select Managed System.
- Click + Create Smart Rule.
- From the Category dropdown, select Managed Systems.
- Enter a name and description.
- Under Selection Criteria, select Asset Smart Group and All EPM Clients from the dropdowns.
- Under Actions, select Show managed system as Smart Group
- Click Add another action.
- Select Create Managed Account on each system.
- Leave the remaining settings for Actions as default or modify as required.
- Click Create Smart Rule.
- Administrator is the default account name, because that is standard for Windows systems. You can modify the name if you have configured something other than default standard local admin account name in your environment. You can also add multiple Create Managed Account on each system actions if you have additional local admin accounts you wish to manage with Password Safe.
- To view the contents of a Smart Rule when creating a new rule or editing an existing rule:
- Once the rule is saved, click View Results.
- You are taken to the associated grid, where the contents of the Smart Rule are listed.
- If the rule is actively processing, a banner displays letting you know that.
- View Results displays only if you have permissions to the grid corresponding to the Smart Rule, i.e.; Assets, Managed Accounts, Managed Systems.
- The Smart Rule must be saved with Show <entity> as Smart Group selected under Actions to view the results.
- Because the Smart Rule must process to display the contents in the grid, we recommend viewing the results using only the Show <entity> as Smart Group action and before adding additional actions that may make changes to accounts and assets in your network. Once you have confirmed the rule contains your desired items, you can then add additional actions to the Smart Rule.
For configuration of Assets, see Assets: Configure.
Updated 18 days ago

