Role-based access | PS Cloud
What is role-based access?
Role-based access assigns permissions and access rights to users based on their roles and responsibilities within an organization. Rather than granting individual permissions to each user, access is managed through predefined roles and groups.
How is it useful?
In BeyondInsight and Password Safe, this model helps ensure that users only have access to the systems and functions necessary for their job.
- Group permissions: Permissions are assigned when you create a group. Permissions are system-wide and provide access to various components of the BeyondInsight infrastructure. There are permissions that are specific to accessing and using features of the Password Safe application.
- Password Safe roles: The roles define the actions that Password Safe users can take when using the Password Safe web portal for password releases or access to applications.
Group features
The following table provides information on the Password Safe features that you can assign to your groups.
| Feature | Full Control permission assigned |
|---|---|
| Password Safe Account Management | Grants permissions to the following features on the Managed Accounts page:
|
| Password Safe Admin Session | Allows non-ISA users access to the Admin Session feature in Password Safe. Using an Admin Session allows administrators to open ad-hoc RDP / SSH sessions without going through the request process. |
| Password Safe Bulk Password Change | Use the bulk password change feature on the Managed Accounts page. |
| Password Safe Agent Management | Grant a user administrator permissions to the Configuration > Privileged Access Management Agents page. |
| Password Safe Configuration Management | Grant a user administrator permissions to the Configuration > Privileged Access Management page. |
| Password Safe Policy Management | Grant a user administrator permissions to the Configuration > Privileged Access Management Policies page. |
| Password Safe Role Management | Manage roles provided they have the following permissions: Password Safe Role Management and User Accounts Management. |
| Password Safe System Management | Users can manage systems on the Managed Systems page, including:
Password Safe Account Management is needed with Password Safe System Management to manage Password Safe accounts. Full Control is required for both. |
| Smart Rule Management - Managed Account | Users can create and edit Managed Account Smart Rules. |
| Smart Rule Management - Managed System | Users can create and edit Managed System Smart Rules. |
| Secrets Safe | Users can access the Secrets Safe feature. |
In addition to Password Safe features permissions, users need the following general permissions:
| Asset Management | Read, create, and delete assets and databases. |
|---|---|
| Management Console Access | Access to sign on to the management console. |
Password Safe roles
In Password Safe, a role is the connection between a Password Safe user account and a managed system. A role defines what the user or group can do with respect to that managed system. Roles are assigned to Smart Groups, and the roles that you can assign depend on the Smart Group type, as follows:
- Asset Smart Group: The ISA and Auditor roles may be assigned.
- Managed Account Smart Group: The Requestor, Approver, Credentials Manager, Recorded Session Viewer, and Active Session Reviewer roles may be assigned.
| Role | Description |
|---|---|
| Requester | Allows users to submit a request to retrieve managed passwords or remote session connection files. When assigning the Requester role, you must select an access policy. |
| Approver | Allows users to approve requests for the release of managed passwords or remote session connection files. Typically, system administrators and network engineers are assigned to this role. In peer approval environments, users may be both approvers and requestors. In this case, a user cannot approve their own requests when dual control is enforced. |
| Information Security Administrator (ISA) | Allows users to setup managed systems and accounts.The ISA role provides the functionality required for security help desk personnel. User with the ISA role can delegate limited authority to those responsible for resource management. This role enables a user to bypass every workflow and security measure, like approval workflows or checked out accounts. If another user has an account checked out and the password is known by this user, an ISA user can view the password. ISA users are not permitted to use the Admin Session feature. |
| Auditor-Sessions | Allows user to watch live and recorded sessions. You do not have access to the Password Safe reports. |
| Auditor-Reports | Allows user access to the Password Safe reports. You do not have access to watch live and recorded sessions. |
| Credentials Manager | Allows users to set credentials using the PUT ManagedAccounts/{accountId}/Credentials API. |
| Recorded Session Reviewer | Allows users to view and take action on completed recorded Password Safe sessions, including:
|
| Active Session Reviewer | Allows users to view and take action on active Password Safe sessions, including:
|
On all systems where a user is granted the ISA role, the user can change the following system details:
- Grant users/groups roles to the managed system.
- Review password release and session requests.
- Add and change accounts on managed systems.
- Assign a system to a collection (provided the ISA role is granted to the user for both the system and the collection).
- Remove their ISA role from a system.
Create a group and assign roles
- You cannot assign roles to the BeyondInsight Administrator.
- Roles are only available to BeyondInsight features.
-
Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. -
From the left menu, click
 .
.
The Configuration page displays. -
Under Role Based Access, select User Management.
The User Management page displays. -
Select the Groups tab.
-
Click + Create New Group.
-
Select Create a New Group.
-
Enter a name and description for the group.
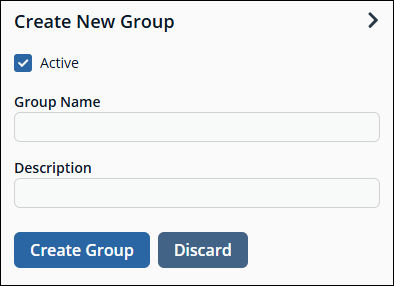
- Click Create Group.
The <group name> page displays. - Assign users to the group:
- Under Group Details, select Users.
- From the Show dropdown , select Users not assigned.
- Filter the list of users displayed in the grid by Type, Username, Name, Email, and Domain, if necessary.
- Select the users you wish to add to the group.
- Click Assign User above the grid.
- Assign features permissions to the group:
- Under Group Details, select Features.
- Filter the list of features displayed in the grid using the Show and Filter by dropdown lists.
- Select the features you wish to assign permissions to.
- Click Assign Permissions.
- Select Assign Permissions Read Only or Assign Permissions Full Control.
- Assign Smart Groups permissions and roles to the group:
- Under Group Details, select Smart Groups.
- Filter the list of Smart Groups displayed in the grid using the Show and Filter by dropdown lists.
- Select the Smart Group or groups you wish to assign permissions to.
- Click Assign Permissions.
- Select Assign Permissions Read Only or Assign Permissions Full Control.
- Select the Smart Group you wish to assign Password Safe roles to.
- Click
 > Edit Password Safe Roles.
> Edit Password Safe Roles. - Select the role(s). If selecting Requestor, also select an access policy from the dropdown.
- Click Save Roles.
Quarantine user accounts
You can turn on the quarantine feature as a preventative measure when suspicious activity is detected. When quarantine is turned on, the user account can no longer sign in to the console or API, and any active sessions are terminated immediately.
The difference between account lockout and account quarantine is that account lockout cannot terminate sessions.
Turn on the setting at the user account level as follows:
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays. - Under Role Based Access, select User Management.
The User Management page displays. - Select the Users tab.
- Locate the user account in the grid.
- Click
 > Edit User Details.
> Edit User Details. - Check the Account Quarantined option to enable it.
- Click Update User.
Set the refresh interval on the quarantine cache
You can set the length of time that passes before the cache is updated with the user accounts from the database. The quarantine is only applied to the user account after the cache is updated.
The user can remain logged in and sessions remain active up until the refresh interval time passes (and the cache is updated with the quarantine status).
-
Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. -
From the left menu, click
 .
.
The Configuration page displays. -
Under System, select Site Options.
The Site Options page displays. -
Under Session, enter the number of seconds that pass before the cache is updated with the most recently discovered quarantined user accounts.
The default value is 600 seconds (10 minutes). The maximum value is 1200 seconds (20 minutes).
-
Click Save.
Configure API access
When using the Password Safe API, the group where the users are assigned must permit access to the API. Additionally, any managed accounts that must be accessible by the API must also be configured.
Configure group with API access
A BeyondInsight user has API access if at least one of the user groups they belong to has API access enabled.
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays. - Under Role Based Access, select User Management.
The User Management page displays. - Select the Groups tab.
- Locate the group in the grid.
- Click
 > View Group Details.
> View Group Details. - Under Group Details, select API Registrations.
- Check the API registrations to save to the group.
Enable API setting for managed account
You must turn on API access for a Password Safe managed account to be accessible to the API methods.
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Managed Accounts page displays. - Locate the account in the grid.
- Click
 > Edit Account.
> Edit Account. - Scroll down and expand Account Settings.
- Toggle the API Enabled option on.
- Click Update Account.
Restrict access to Password Safe Login page
When using SAML, smart card, or claims-aware authentication to access the Password Safe web portal, you might not want users to sign in directly to the web portal URL. You can disable direct access to the Password Safe web portal URL for Active Directory, LDAP, and local BeyondInsight users by enabling the Disable Login Forms setting. Users must then always provide the SAML, smart card, or claims-aware credentials before gaining access to the web portal.
The following procedure assumes the group and user are already created.
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays. - Under Role Based Access, select User Management.
The User Management page displays. - Select the Users tab.
- Locate the user account in the grid.
- Click
 > Edit User Details.
> Edit User Details. - Under Authentication Options, check Disable Login Forms to enable it.
Configure approvals
You can control the number of approvers required for a requester. You can also control the number of approvers required for each access type: View Password, RDP, and SSH. This is configured in an access policy, which can then be assigned to a group when assigning Password Safe roles to the group.
- Any of the approvers in the group can approve the request. If other subsequent approvers click the link, they will see that the request has already been approved. Other approvers can, however, override the approval and deny the request. If a request is denied by one approver, no approvers can subsequently override and approve. It is not possible to deny the request once the schedule window has actually begun.
- For more information, see Configure a group and assign roles.
Use a managed account as a credential
You can use a managed account for the credential when you are configuring queries and user groups for Active Directory and LDAP.
You cannot delete a managed account if it is used as a credential for a user group. You can delete a managed account used as a credential for a directory query; however, the query will no longer run. You must select another credential for the query to run again.
Configure the managed account
Before you configure the query or group, the managed account must be in place and specific settings must be selected.
When you configure the managed account settings, be sure to select the Allow this account to be used in BeyondInsight and Directory Queries option.
If there are several managed accounts organized in a Smart Group, select Enable Accounts for AD/LDAP queries in the Smart Rule.
For more information on creating user accounts, see Configuration: User accounts.
Important informationDisable the Change Password After Release option on the managed account, because log files can grow significantly in a short time when using managed account credentials with a directory query.
Configure the query
Active Directory and LDAP queries can use a managed account as a credential.
An Active Directory or LDAP group can use a managed account as the credential. When you create the group, the managed account is listed as a credential.
For more information on creating queries, see Create a directory query.
Configure LDAP groups
Before logging in to Password Safe using LDAP, you must configure an LDAP group.
For more information on creating and configuring groups, see Configuration: Groups.
Real time authorization
Real time authorization allows administrators to remove users from groups while they are logged in with a directory account and use the registry key to perform an additional check to ensure that the user still has access to the password at the time they requested it. This puts the user through the log in process every time a password is requested.
Enable the following registry key to turn on this feature:
HKLM\SOFTWARE\BeyondTrust\PBPS\EnableCheckoutAuthorization
After the user is removed from the group, they receive the following error message when they request password access: Missing required Password Safe role.
Sessions Tab
Session management allows users to monitor, and administrators to control, active logins. Each login generates a session record, which can be viewed and managed in different areas of BeyondInsight.
Administrators have the option to end any or all active user sessions at any time, such as after updating group permissions. This ensures that users are forced to sign in again so their updated permissions take effect immediately.
When session limiting is enabled, if a user logs in to another session, all other active sessions for that user are automatically logged out. Logged-out sessions do not display an immediate message. Instead, the user is redirected to the login screen the next time they attempt to perform an action.
View Sessions
Each login creates an associated session record. You can view these records in two places.
Admin view:
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays. - Under Role Based Access, select User Management.
The User Management page displays. - Select the Sessions tab.
- Locate the session in the grid.
- Click
 > View Details.
> View Details.
Deleting your own active session will result in having to sign in again to perform further actions.
Self-service view:
- From the header section located at the top right of any page in BeyondInsight, click
 > Account Settings.
> Account Settings.
The Account Settings page opens. - Select Sessions under My Account.
- Locate the session in the grid.
- Click
 > View Details.
> View Details.
The Self-service view only displays the current user's active sessions.
Configure Session Behavior
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays. - Under System, select Site Options.
The Site Options page displays. - Under Sessions , two options are available:
- Limit Management Console sessions to one at a time per user
- Limit Workforce Passwords sessions to one at a time per user
- Select options.
- Click Save.
Updated 29 days ago

