EPM Windows and Mac | BI On-prem
When an Endpoint Privilege Management license is detected in BeyondInsight, you can view Endpoint Privilege Management events, file integrity monitoring events, and session details for monitored systems, from the BeyondInsight console. You can also view and deploy Endpoint Privilege Management policies, and view Endpoint Privilege Management agents.
If the Endpoint Privilege Management Web Policy Editor (WPE) is installed and configured you can view the details for each policy, unlock policies, edit policies, and delete policies.
If Endpoint Privilege Management Reporting is installed and configured, you can view dashboards and reports which may assist you with managing and auditing Endpoint Privilege Management activity in your environment.
The following sections provide details on using each of the above mentioned Endpoint Privilege Management features from the BeyondInsight console.
View Endpoint Privilege Management reports
Endpoint Privilege Management Reporting includes a rich set of dashboards and reports designed to simplify the centralized management and auditing of Endpoint Privilege Management activity throughout the desktop and server estate.
A report is a dashboard or a table, and is a generic term used to describe any form of data displayed in Endpoint Privilege Management Reporting. You can click on links within reports to see the data at greater levels of granularity. These are referred to as drilldowns.
A dashboard is a report, which at the top level, presents you with a series of charts and summarized data. Some dashboards have sub-reports that are presented as charts or tabular data. All dashboards have a Microsoft Windows view to display events from Windows endpoints. Some dashboards and reports also have a macOS view.
The below sections describe each of the dashboards, and the reports and event data accessible from each view.
Endpoint Privilege Management Reporting is not installed out of the box in BeyondInsight. For BeyondInsight releases prior to 23.1, contact your BeyondTrust representative for assistance with installing the Endpoint Privilege Management Reporting feature in your BeyondInsight environment.
Navigate the Endpoint Privilege Management reporting interface
The Endpoint Privilege Management Reporting interface allows you to switch between dashboards and reports and to filter data as required. This section covers the Endpoint Privilege Management Reporting interface elements and how to export a specific report.
Navigation panel
The side navigation panel takes you to each top-level dashboard and the reports in that dashboard. Reports that are post-fixed with All indicate the data is in tabular form.
Dashboard and reports panel
This is the area where dashboards and reports are displayed. A dashboard is a report with multiple charts covering a wide range of data. A report is a summary table or a page focused on a particular entity.
The graphical elements of a dashboard or report are interactive. You can click on a chart to view the data at an additional level of granularity.
Filter panel
Each dashboard and report has a panel above its table, chart, or graph area that displays the applied filters and a Filters dropdown. When you select the Filters dropdown, a Filters box appears where you can select filters to filter data based on various event properties. The Filters box also provides a link to select Advanced Filters, allowing for more granular report data. The filters displayed in the box are unique and relevant to the specific dashboard and report.
For example, if you want to filter the Summary report to include only a specific Workstyle:
- From the Summary dashboard, click the link to open the report to filter.
- Click the Filters dropdown.
- Click the Advanced Filters link.
- Select the Workstyle you are interested in from the dropdown.
- Click Apply Filters.
- The report data for that specific Workstyle displays in the table.
The filter options match text on substrings; partial or complete words can match on a filter.
Certain filter options support comma-separated values so you can specify a list of filter values. For example, to restrict the results to three users, enter user1,user2,user3 in the User Name field.
Multiple "!" strings are accepted. For example, "!L-CZC13127L30l,!L-CNU410DJJ7"
Any text field supports wildcards, comma-separated values (CSV), and the Does Not Match(!) options:
| Filtering Effect | Filter Panel Operator | Effect |
|---|---|---|
| List separator | Comma (,) | Value1,value2,value3 |
| Wildcard | % | part% part%part2,part3%part4 |
| Negation or "Not" | ! | !value !value1,!value2 |
When filtering tabular reports such as the Users > All table, an applied filter is displayed at the top of the table. To remove a filter, click on the x next to the filter text.
Export reports
You can export reports to a CSV file by clicking the Export to CSV button in the filter panel above the report.
Exported data is based on the data currently displayed in the report.
Use quick filters and advanced filters
Use quick filters
Below are descriptions of commonly used quick filter options available from the Filters dropdown.
The quick panel on the left pane displays a set of predefined filters relevant to the current dashboard or report to refine the data.
| Name | Description |
|---|---|
| Platform |
|
| Time Range | This is the time range in which the actions are audited. For example, you can filter by the number of elevated actions in the last 24 hours in the Actions > Elevated report. You can choose from:
|
| Time First Reported | This is the time range filtered by the date the application was first entered in the database. For example, you can filter on the new Windows applications by publisher that were first reported in the last 7 days in the Discovery > By Publisher report. You can choose from:
|
| Time First Executed | This is the time range the application was first executed. For example, you can filter on the new Windows applications, by type, that were first executed in the last 30 days in the Discovery > By Type report. You can choose from:
|
| Target Type | This filter allows you to filter by a type of target. For example, you can filter on the applications canceled in the time range in the Actions > Canceled report. You can choose from:
|
| Action | This filter allows you to filter by a type of action. For example, you can filter on the services elevated in the time range in the Target Types > Services report. You can choose from:
|
| Application Type | This filter allows you to filter by application type. For example, you can filter by applications that are executables used in the time range in Target Types > Applications. You can choose from:
|
| Event Category | This filter allows you to filter by the category of the event. For example, you can filter by process events only that occur in the time range in the Events > All report. You can choose from:
|
| Elevate Method | Allows you to filter by the elevation method used. For example, in the Discovery > Requiring Elevation report, you can filter by new applications which were accessed using on-demand elevation within the time range. You can choose from:
|
| Path | Allows you to filter by the path. For example, to filter on applications that were launched from the System path. You can choose from:
|
| Source | The media source of the application. For example, was the application downloaded from the internet or is it from removable media? You can choose from:
|
| Challenge / Response | Allows you to filter by challenge/response events. For example, you can filter the application that required elevation on those applications launched following a completed challenge/response message. You can choose from:
|
| Admin Rights | Allows you to filter by the admin rights token. You can choose from:
|
| Authorization | Allows you to filter by authorization. You can choose from:
|
| Ownership | Allows you to group by the type of owner. You can choose from:
|
| Rule Match Type | Allows you to filter on the type of matching. You can choose from:
|
Use advanced filters
Below are descriptions of commonly used filter options available from the Advanced Filters link in the Filters box.
| Name | Description |
|---|---|
| Action |
There are nine actions to choose from:
|
|
Activity ID |
Each Activity Type in Endpoint Privilege Management has a unique ID. This is generated in the database as required. For example, if you are in the Target Types dashboard and drill down in the Top 10 Activities chart, the Events > All report opens. If you look in the top advanced filter you will see that the Activity ID is populated. |
|
Admin Rights Required |
There are three options to choose from:
Allows you to filter if Admin Rights are required, not required, or both. For example, if you are in the Discovery > All report and set the side quick filter to Admin Rights, only applications that required admin rights are listed. |
| Agent Version | The version of the Endpoint Privilege Management agent. |
|
Application Desc |
A text field that allows you to filter on the application name. For example, in the Discovery report you can filter by paint in the Application Desc field. This filters applications that contain the string paint in the description. |
|
Application Group |
A text field that allows you to filter by Application Group. You can obtain the Application Group from the Policy Editor. It is also available in some reports such as Process Detail, which is accessed from Events All. |
|
Application Type |
A text field that allows you to filter by application type. You can obtain the application type from the Policy Editor. It's also available in some reports such as Process Detail, which is accessed from Events All. |
| Auth Methods | The type of authentication method selected in the Policy Editor. Multiple values can be present and are comma separated. Possible values: Identity Provider, Password, Challenge Response, Smart Card, and User Request. |
| Auth User Name | The name of the user that authorized the message. |
| Browse Source URL | The source URL of the sandbox. |
| Browse Destination URL | The destination URL of the sandbox. |
| Chassis | The physical form of the endpoint. Other is a virtual machine. |
|
Command Line |
A text field that allows you to filter on the command line. It is also available in some reports such as Process Detail that is accessed from Events > All. |
| Context |
This field is used by Reporting. You do not need to edit it. |
|
Date Field to filter on |
There are three options to choose from:
|
| Default UI Language | The default language of the endpoint. |
| Device Type |
The type of device that the application file was stored on. You can select from:
|
|
Distinct Application ID |
This field is used by Reporting. You do not need to edit it. |
|
Elevation Method |
There are five options to choose from:
These allow you to filter events by the type of elevation used. |
| Event Number |
This field is used by Reporting. You do not need to edit it. This number assigned to the event type. |
|
External Source |
There are four options to choose from:
These allow you to filter by the type of external source that the application file came from. |
|
File Name |
You can filter by a partial file name string if required. For example, in the Process Detail report. |
|
File Version |
You can filter on the file version in the Advanced View of the Process Detail report. |
|
GPO Name |
You can filter on the Group Policy Object (GPO) name in some of the advanced reports such as Process Detail. |
|
Host Name |
This field allows you to filter by the name of the endpoint the event came from. |
| Idp Authentication user name | The credential provided when adding an Identity Provider authorization message in the Policy Editor. |
| BeyondTrust Zone Identifier | The BeyondTrust Zone Identifier. This tag persists, to allow you to filter on it even if the ADS tag applied by the browser is removed. |
|
Ignore "Admin Required" Events |
This field is used by Reporting. You do not need to edit it. |
|
Just Discovery Events |
This field is used by Reporting. You do not need to edit it. |
|
Message Name |
The name of the message that was used. |
| Message Type |
The type of Message:
|
|
Number to Get |
The number of rows to get from the database. |
| Operating System Type |
The type of operating system:
|
| Operating System | The operating system of the client machine. |
|
Parent PID |
The operating system process identifier of the parent process. |
| PID | The operating system process identifier. |
|
Product Name |
The product name of the application. |
|
Product Version |
The product version of the application. |
|
Program Files Path |
Sets the Program Files path used by the Discovery > By Path report. |
|
Publisher |
The publisher of the application. |
|
Range End Time |
The end time of the range being displayed. |
|
Range Start Time |
The start time of the range being displayed. |
|
Request Type |
The type of request:
|
|
Row Limit |
The maximum number of rows to be retrieved from the database. |
|
Rule Match Type |
Rule Match Type:
|
|
Sandbox |
The sandboxed setting:
|
| Rule Script Affected Rule |
True when the Rule Script (Power Rule) changes one or more of the Default Endpoint Privilege Management rules, otherwise false. |
| Rule Script File Name | The Rule Script (Power Rule) file name on disk if applicable. |
| Rule Script Name | The name of the assigned Rule Script (Power Rule). |
| Rule Script Output | The output of the Rule Script (Power Rule). |
| Rule Script Publisher | The publisher of the Rule Script (Power Rule). |
| Rule Script Result |
The result of the Rule Script (Power Rule). This can be: <None> Script ran successfully [Exception Message] Script timeout exceeded: <X> seconds Script execution canceled Set Rule Properties failed validation: <reason> Script execution skipped: Challenge Response Authenticated Script executed previously for the parent process: Matched as a child process so cached result applied Script execution skipped: <app type> not supported Script execution skipped: PRInterface module failed signature check Set RunAs Properties failed validation: <reason> |
|
Rule Script Status |
The status of the Rule Script (Power Rule). This can be: <None> Success Timeout Exception Skipped ValidationFailure |
| Rule Script Version | The version of the assigned Rule Script (Power Rule). |
|
Shell or Auto |
Whether the process was launched using the shell Run with Endpoint Privilege Management option or by normal means (opening an application):
|
| Source URL | The source URL (where the file was downloaded from). |
|
System Path |
Sets the system path used by the Discovery > By Path report. |
| Target Description | This field allows you to filter by the target description. |
|
Target Type |
The type of target that triggered the event:
|
| Trusted Application Name |
The trusted application that triggered the event. |
| Trusted Application Version | The trusted application version number. |
|
Trusted File Owner |
Whether the file owner of the target file is trusted. To be a trusted owner the user must be in one of the following Windows groups:
|
|
UAC Triggered |
Whether or not Windows UAC was triggered:
|
|
User Name |
The user name of the user who triggered the event. |
|
User Profiles Path |
Sets the User Profiles path used by the Discovery > By Path report. |
| Workstyle | The name of the Workstyle that contained the rule that matched the application. |
Overview of EPM reporting dashboards
Reporting includes several high level dashboards that summarize the Endpoint Privilege Management events. You can access the following from the side navigation panel.
| Dashboard | Description |
|---|---|
| Summary Dashboard | Displays bar charts for the most important activity that has occurred in the selected time period. Typically this information can result in Workstyle changes or investigation of anomalies. The charts allow you to view details when you click an action, either on a chart or in the legend. The bar charts are separated by Windows and Mac Events by Action. |
| Events Dashboard | Summarizes information about the types of events raised in the specified time frame. It also shows the time elapsed since a host raised an event. |
| Discovery Dashboard | Summarizes all the unique applications discovered. It differentiates between those that used elevated privileges and those that ran with standard privileges. This dashboard only shows new application items in the chosen time interval. For example, the Discovery dashboard can answer the question what’s new this week and how is it affecting my users? The Discovery reports listed below the Discovery dashboard display the data from different angles such as by the location or publisher of the executable or the type of the executable. |
| Actions Dashboard | Summarizes audited items categorized by the type of action taken. This allows you to focus on the topic of interest. For example, elevation or blocking. The Actions reports show audits only of the selected type (Elevated, Blocked, Passive, Canceled, Other). |
| Target Types Dashboard | Lists all the Endpoint Privilege Management activity over the specified time interval by target type. The report lists the targets in tabular form sorted by user count. You can click the targets in the list to view dashboard charts showing Users, Hosts, and Process activities and actions over a specified period of time. |
| User Experience Dashboard | Displays how users interacted with Messages, Challenge/Response dialog boxes, and the Shell (On-Demand) menu. |
| Privileged Logons Dashboard | Displays how many accounts with Standard rights, Power User rights, and Administrator rights generated logon events filtered by the time frame. |
| Privileged Account Management Dashboard | Displays any blocked attempts to modify privileged accounts over the specified time interval. |
| Trusted Application Protection Dashboard | Summarizes all the Trusted Application Protection incidents. Incidents are defined as a child process blocked from running because it matched the rules in the Trusted Application Protection policy or a DLL blocked from loading by a Trusted Application because it did not have a trusted owner or trusted publisher. |
Summary dashboard
The Summary dashboard displays bar charts for the most important activity that has occurred in the time period defined by the quick filter. The legends to the right of the charts display totals for the shown activities. You can use this information to inform Workstyle development or to show anomalous user behavior in your organization.
A warning message might display on the Summary page if there is a backlog of event processing. Verify your database configuration is set up to manage processing a large number of events.
The Summary dashboard includes the following tables:
| Table | Description |
|---|---|
| Applications Discovered | The total number of newly discovered Applications filtered by the type of user rights required:
|
| User Requests | The total number of User Requests filtered by the type of request:
|
| Admin logons, by users, on endpoints | Summarizes the number of admin logons, the number of users, and the number of endpoints used. Admin Logons are shown in the Administration table. Click the number next to the OS icon to show details. |
| Trusted Application Protection | The number of Trusted Application (TAP) incidents, how many users, and how many endpoints were affected. TAP events are shown in the Incidents table. Click the number next to the OS icon to show details. |
| Attempts to modify privileged groups | The number of blocked attempts to modify privileged groups. Attempts to modify privileged groups are shown in the Administration table. Click the number next to the OS icon to show details. |
| Application run from external sources | The number of applications run from external sources. Applications Run from external sources are shown in the Applications table. Click the number next to the OS icon to show details. |
| Activities blocked | The number of applications blocked. Click the chart or legend to open the Target Types All report with the Filter by Action filter applied. |
| Applications used On-Demand privileges | The number of applications launched using on-demand privileges. Click the chart or legend to open the Target Types All report with the Shell or Auto filter applied. Shell indicates that on-demand privileges were used. |
| UAC matches | The number of applications that triggered User Account Control (UAC). UAC events are shown in the Incidents table. Click the number next to the OS icon to show details. |
Events dashboard
This report shows information about the types of events raised over the specified time period. It also shows the time elapsed since a host raised an event.
| Chart | Description |
|---|---|
| Events over the last (time interval) | A column chart showing the number of the different Event types filtered by the time period. Clicking the chart opens the Events All report with the Filter by Event Category filter applied. |
| Event Types | A chart showing the number of events received filtered by the Event type. Clicking the chart opens the Events All report with the Event Number filter applied. |
| By Category | A chart displaying the events received filtered by category. Clicking the chart opens the Events All report with the Filter by Event Category filter applied. |
| Time since last endpoint event | A chart showing the number of endpoints in each time since last event category. |
Events all report
The following columns are available for the Windows and macOS Events All table:
- Event Time: The time of the event.
- Event Category: The category of the event.
- Platform: The platform where the event occurred.
- Description: The description of the event.
- User Name: The user name of the user who triggered the event.
- Host Name: The host name where the event was triggered.
- Workstyle: The Workstyle containing the rule that triggered the event.
- Event Type: The type of event.
Some of these columns allow you to drill down to additional information:
- Event Time: opens the event report listing all of the fields for that event.
- Description: opens the Applications Report.
- User Name: opens the User Report.
- Host Name: opens the Host Report.
- Workstyle: opens the Workstyle Report.
Process detail report
The Process Detail report provides a higher level of detail for Process events than the Events > All table. Other event categories are not shown in this table.
The following columns are available for the Windows and macOS Process Details table:
- Start Time: The start time of the event.
- Platform: The platform where the event occurred.
- Description: The description of the application.
- Publisher: The publisher of the application.
- Application Type: The type of application.
- File Name: The name of the file.
- Command Line: The command line of the process that triggered the event.
- Product Name: The product name of the application.
- Product Version: The product version of the application.
- Trusted Application: The name of the trusted application.
- Trusted Application Version: The version of the trusted application.
- Group Policy Object: The name of the Endpoint Privilege Management policy (Windows only).
- Workstyle: The name of the Workstyle that the event was triggered from.
- Message: The message name if the event triggered a message.
- Action: The action associated with the event.
- Application Group: The Application Group the application assignment rule belongs to.
- PID: The process identifier of the process.
- Parent PID: The parent process identifier.
- Parent Process File Name: The parent process file name.
- Shell / Auto: Whether the process was triggered on-demand or automatically (Windows only).
- UAC Triggered: Whether user account control was triggered (Windows only).
- Admin Rights Required: Whether or not admin rights were required (Windows only).
- Authorization Required: Whether or not authorization rights were required (macOS only).
- User Name: The name of the user who triggered the event.
- Host Name: The name of the host where the event was triggered.
- Rule Script File Name: The name of the Rule Script (Power Rule).
- Rule Script Affected Rule: True when the Rule Script (Power Rule) changed one or more of the Default Endpoint Privilege Management rules, otherwise false.
- User Reason: The reason given by the user if applicable.
- COM Display Name: The COM name if applicable (Windows only).
- Source URL: The URL of the event if applicable (Windows only).
- BeyondTrust Zone Identifier: The BeyondTrust Zone Identifier if present.
- Uninstall Action: This can be None, Uninstall, Change/Modify, or Repair.
- Auth Methods: The type of authentication method selected in the Policy Editor. Multiple values can be present and are comma separated. Possible values: Identity Provider, Password, Challenge Response, Smart Card, and User Request.
- Idp Authentication User Name: The credential provided when adding an Identity Provider authorization message in the Policy Editor.
Export events to CSV file
The number of items that can be displayed at one time might be limited by the browser display. Click Export to CSV to enter the number of rows to export to the CSV file.
All event filters are saved to the file.
Add applications to a policy
If Endpoint Privilege Management Reporting UI 23.4 or a later version is installed and configured, you can add applications to an Endpoint Privilege Management policy directly from the Events dashboard, using the Add to Policy feature.
To add an application from an event to an Endpoint Privilege Management policy:
- Select the event or multiple events, and then click Add to Policy above the grid.
- You are taken to the Endpoint Privilege Management Policy Editor. Select the policy and application group from the dropdowns, and then click Add and Edit or Add and Close.
Discovery dashboard
This dashboard displays information about applications discovered by the Reporting database for the first time. An application is first discovered when an event is received by the Endpoint Privilege Management Reporting database. The Discovery dashboard displays events from Windows and macOS operating systems.
Windows uses the terminology of Admin Rights and macOS uses the terminology of Authorization.
The Discovery dashboard displays the following charts:
| Chart | Description |
|---|---|
| Applications first reported in the specified time frame | A chart showing the number of applications discovered, filtered by the types of rights or authorization detected: For Windows:
For macOS:
|
| Types of newly discovered applications | A chart showing the number of applications discovered by the type of application. The types are different for Windows and macOS operating systems. Click the chart to open the Discovery dashboard report with the Admin Rights Required filter applied. |
The Discovery dashboard has the following tables:
| Table | Description |
|---|---|
| New applications with admin rights detected | A list of discovered applications that are running with admin rights. This list is ordered by the number of users. Click View all to see the full list. Click any of the applications in the list to open the Discovery dashboard report with the Admin Rights Required and Matched filter applied. |
| New applications with admin rights not detected (top 10) | A list of discovered applications that are running with standard, not admin rights. This list is ordered by the number of users. Click View all to see the full list. Click any of the applications in the list to open the Discovery dashboard report with the Admin Rights Required and Matched filter applied. |
| New applications with admin rights detected (by type) | A list of the types of applications that required admin rights that were newly discovered within the time interval. They are ordered by the total number of applications for each type. Click View all to see the full list. Click any of the applications in the list to open the Discovery dashboard report with the Admin Rights Required and Matched filter applied. |
| New applications with admin rights not detected (by type) | The types of applications that did not require admin rights that were newly discovered within the time interval. They are ordered by the total number of applications for each type. Click any of the applications in the list to open the Discovery dashboard report with the Admin Rights Required and Matched filter applied. |
Discovery reports
The following reports are available from the navigation panel, under the Discovery dashboard. A description of each is in the below sections.
- Discovery By Path
- Discovery By Publisher
- Discovery By Type
- Discovery Requiring Elevation
- Discovery From External Sources
- Discovery All
Discovery by path
This table displays the discovered applications grouped by path. Where there is more than one application per path, click + to expand the entry to examine each application.
The following columns are available for the Windows and macOS Discovery By Path table:
- Path: The path of the applications.
- Description: The description of the application.
- Publisher: The publisher of the applications.
- Name: The product name of the application.
- Type: The type of application.
- Version: The version number of a specific application.
- # Users: The number of users.
- Median # Processes / User: The median number of processes per user.
- # Hosts: The number of hosts.
- # Processes: The number of processes.
- # Applications: The number of applications.
- Date first Reported: The date the application was first entered in the database.
- Date first Executed: The first known date the application was executed.
Some of these columns allow you to drill down to additional information:
- Description: Opens the Applications report for that application.
- # Users: Displays a list of users the application events came from.
- # Hosts: Displays a list of hosts the application events came from.
- # Processes: Displays the Events All table and lists the events received in the time period for the selected application.
Discovery by publisher
This table displays the discovered applications grouped by publisher. Where there is more than one application per publisher, click + to expand the entry to examine each application.
The following columns are available for the Windows and macOS Discovery By Publisher table:
- Publisher: The publisher of the applications.
- Description: The description of the application.
- Name: The product name of the application.
- Type: The type of application.
- Version: The version number of a specific application.
- # Users: The number of users.
- Median # Processes / User: The median number of processes per user.
- # Hosts: The number of hosts.
- # Processes: The number of processes.
- # Applications: The number of applications.
- Date first Reported: The date the application was first entered in the database.
- Date first Executed: The first known date the application was executed.
Some of these columns allow you to drill down to additional information:
- Description: Opens the Applications report for that application.
- # Users: Displays a list of users the application events came from.
- # Hosts: Displays a list of hosts the application events came from.
- # Processes: Displays the Events All table and lists the events received in the time period for the selected application.
Discovery by type
This table displays applications filtered by type. When there is more than one application per type, click + to expand the entry to see each application.
The following columns are available for the Windows and macOS Discovery By Type table:
- Type: The type of application.
- # Users: The number of users.
- Median # processes / user: The median number of processes per user.
- # Hosts: The number of hosts.
- # Processes: The number of processes.
- Applications: The number of applications.
- Date first reported: The date the application was first entered in the database.
- Date first executed: The first known date the application was executed.
Expanding the application type in the table, displays the following columns:
- Description: The description of the application.
- Publisher: The publisher of the applications.
- Name: The product name of the application.
Some of these allow you to drill down to additional information:
- Description: Opens the Target Types > Applications report which is filtered to that application.
- # Users: Displays a list of users the application events came from.
- # Hosts: Displays a list of hosts the application events came from.
- # Processes: Displays the Events All table and lists the events received in the time period for the selected application.
Discovery requiring elevation
This table displays the applications that were elevated or required admin rights.
The following columns are available for the Windows and macOS Discovery Requiring Elevation table:
- Description: The description of the application.
- Publisher: The publisher of the application.
- Name: The product name of the application.
- Type: The type of application.
- # Users: The number of users.
- Median # Processes / User: The median number of processes per user.
- # Hosts: The number of hosts.
- # Processes: The number of processes.
- Version: The version number of a specific application.
- Elevate Method: The type of method used to elevate the application: All, Admin account used, Auto-elevated, or on-demand.
- Date First Reported: The date the application was first entered in the database.
- Date First Executed: The first known date the application was executed.
Some of these allow you to drill down to additional information:
- Description: Opens the Target Types > Applications report filtered to that application.
- # Users: Displays a list of users the application events came from.
- # Hosts: Displays a list of hosts the application events came from.
- # Processes: Displays the Events All table and lists the events received in the time period for the selected application.
- Elevate Method: Displays the Events All table with an extra Elevate Method column.
Discovery from external sources
This table displays all applications that originated from an external source such as the internet or an external drive.
The following columns are available for the Windows Discovery from External Sources table:
- Description: The description of the application.
- Publisher: The publisher of the application.
- Name: The product name of the application.
- Type: The type of application.
- Source: The source of the application.
- # Users: The number of users.
- Median # Processes / User: The median number of processes per user.
- # Hosts: The number of hosts.
- # Processes: The number of processes.
- Version: The version number of the application.
- Date First Reported: The date the application was first entered in the database.
- Date First Executed: The first known date the application was executed.
Some of these allow you to drill down to additional information:
- Description: Opens the Applications report for that application.
- # Users: Displays a list of users the application events came from.
- # Hosts: Displays a list of hosts the application events came from.
- # Processes: Opens the Events All table and lists the events received in the time period for the selected application.
Discovery all
This table lists all applications discovered in the time period, grouped by the application description so that if multiple versions of the same application exist, they are grouped on the same line. Click + in the Version column to expand the list.
The following columns are available for the Windows and macOS Discovery All table:
- Description: The description of the application.
- Publisher: The publisher of the application.
- Name: The product name of the application.
- Type: The type of application.
- Version: The version number of the application.
- # Users: The number of users.
- Median # Processes / User: The median number of processes per user.
- # Hosts: The number of hosts.
- # Processes: The number of processes.
- Date First Reported: The date the application was first entered in the database.
- Date First Executed: The first known date the application was executed.
- Name: The product name. This is hidden by default but you can select it from the Actions > Choose Columns menu.
Some of these columns allow you to drill down to additional information:
- Description: Opens the Applications report for that specific application.
- # Users: Displays a list of users the application events came from.
- # Hosts: Displays a list of hosts the application events came from.
- # Processes: Displays the Events All table.
Actions dashboard
The Actions dashboard breaks down the application activity by the type of action. It also lists the most active targets.
The Actions dashboard has the following charts:
| Chart | Description |
|---|---|
| All actions over the specified time frame | A chart showing the number of targets filtered by the type of action for each time frame for all target types. The types of action are:
|
| Distinct target count by target type | A chart showing the target count for each target type, filtered by the type of action. The targets types are:
|
| Top 10 targets | A chart showing the ten most used targets by process count. Click the chart to open the Events All report with the Action and Target Description filters applied. |
Target types dashboard
The Targets Types report lists all targets for all actions over a specified period of time in a tabular format. Click the target in the Description column to view a dashboard containing charts showing the activity and actions for the target.
| Chart | Description |
|---|---|
| Actions over the last (time interval) | A chart showing the number of processes for each action for the target. The actions are listed in the legend to the right of the chart. Click the action to open the Events / All report to view the events for that action and target. |
| Top 10 Users | A chart showing the 10 most common activities by process count for users. Click the chart to open the Events / All report to view the events for that user, action, and target. |
| Top 10 Hosts | A chart showing the 10 most common activities by process count for hosts. Click the chart to open the Events / All report to view the events for that host, action, and target. |
| Run Method | A chart showing the count and percentage for activities by run method (Shell or Automatic) count for hosts. Click the chart to open the Events / All report to view the specific events by run method. |
| Discovery - Admin Rights | A chart showing the count and percentage for activities that did not require admin rights. Click the chart to open the Events / All report to view the specific events that did not require admin rights. |
Trusted application protection dashboard
You can access this dashboard from the Summary dashboard. Click the number listed in the Incidents table, under TAP. This dashboard shows information about Trusted Application Protection (TAP) incidents. A TAP incident occurs when a child process of a trusted application is blocked due to a trusted application policy or when a DLL is prevented from loading by a trusted application because it lacks a trusted owner or publisher.
There are no advanced filters for the Trusted Application Protection dashboard.
| Chart | Description |
|---|---|
| Trusted Application Protection incidents over the time period. | A column chart showing the number of incidents filtered by the trusted application. Click the chart to open the Process Details report with Time Range filter applied. |
| Trusted Application Protection incidents, by application | A table listing each trusted application, the number of TAP incidents, the number of targets, the number of users, and the number of hosts affected. Click the Incidents number to open the Process Details report with the Trusted Application Name filter applied. Click the Targets number to open the Targets > All table with the Trusted Application Name filter applied. |
| Top 10 targets | The top 10 targets for TAP incidents. Click the Target to open the Application report with the Application Type and Distinct Application ID filters applied. Click the Incident number to open the Process Details report with the Distinct Application ID filter applied. Clicking the Users or Hosts number opens the Users or Hosts list, respectively. |
Users dashboard
The following dashboards are available from the navigation panel under Users. Overviews for each are described in the below sections.
- User Experience
- Privileged Logons
- Privileged Account Management
User experience dashboard
This dashboard shows how users interacted with Messages, Challenge/Response dialog boxes, and the Shell (On-Demand) menu.
| Chart | Description |
|---|---|
| User Experience over the time period | A chart showing the percentage of users that experienced each interaction type filtered by the specified time period. Click the chart to display a list of users presented with that interaction. |
| Message Distribution | A chart showing how many users are in the defined categories of messages per time period. Click the chart to display a list of users in that category. |
| Messages per action type | A table showing message types displayed for Allowed and Blocked actions. Click the prompts, notifications or counts, or table to open the Events All report with the Action and Message Type filters applied. |
Privileged logons
This dashboard shows how many accounts with Standard rights, Power User rights and Administrator rights generated logon events filtered by the time frame.
| Chart | Description |
|---|---|
| Privileged Logons over the last (time interval) | A chart and table showing the number of logons by the account types over time. Click the chart to open the User Logons table with the Show Administrator Logons, Show Power User Logons and Show Standard User Logons filters applied. |
| Logons by Account Privilege | A chart showing the total number of logons filtered by the different account types. Click the chart to open the User Logons table with the Show Administrator Logons, Show Power User Logons and Show Standard User Logons filters applied. |
| Logons by Account Type | A chart showing the total number of logons filtered by domain accounts and local accounts. Click the chart to open the User Logons table with the Account Authority filter applied. |
| Top 10 Logons by Chassis Type | A chart showing the total number of logons filtered by the top 10 chassis types. Click the chart to open the User Logons table with the Chassis Type filter applied. |
| Top 10 Logons by host Operating System | A chart showing the total number of logons filtered the top 10 host operating systems. Click the chart to open the User Logons table with the OS filter applied. |
| Top 10 Accounts with Admin Rights | A chart showing the top 10 accounts with admin rights that have logged into the most host machines. Click the chart to open the User Logons table with the User Domain and User Name filter applied. |
| Top 10 hosts with Admin Rights | A chart showing the top 10 host machines logged on to by the most users with admin rights. Click the chart to open the User Logons table with the Host Name, Show Administrator Logons filter applied. |
Privileged account management
This dashboard shows any blocked attempts to modify privileged accounts over the specified time interval.
| Chart | Description |
|---|---|
| Privileged Account Management over the last (time interval) | A chart breaking down the privileged account management events by time period. Click the chart to display the Privileged Account Management table with the Time Range filter applied. |
| Table showing users blocked, hosts blocked, applications blocked, and total blocked modifications | A table showing the number of users, hosts, applications blocked, and the total number of blocked events within the specified time frame. Click the count numbers to open the Privileged Account Management table. |
| By Privileged Group | A chart showing the privileged account modification activity blocked by Windows group name. Click the chart to open the Privileged Account Management table with the Group Name filter applied. |
| Top 10 applications attempting account modifications | A chart showing the privileged account modification activity that was blocked, broken down by the Application Description. Click the chart to open the Privileged Account Management table with the Application Description filter applied. |
| Top 10 users attempting account modifications | A chart showing the top 10 users who attempted modifications. Click the chart to open the Privileged Account Management table with the User Name filter applied. |
| Top 10 hosts attempting account modifications | A chart showing the top 10 hosts attempting privileged account modifications. Click the chart to open the Privileged Account Management table with the Host Name filter applied. |
Events
You can view Endpoint Privilege Management events on the Endpoint Privilege Management Events page.
This feature is available only when an Endpoint Privilege Management license is detected.
You can view and download all events for monitored systems and you can select an event to view more details about that specific event. You can also generate rules and create exclusions from listed events.
To view events, generate rules, create exclusions, and download events, follow the below steps:
- From the left menu in the BeyondInsight console, click Endpoint Privilege Management.
- By default, displayed events are filtered by the Discovery Scanners Smart Group. Select a Smart Group from the Smart Group filter dropdown to view events for that Smart Group.
- To further filter the displayed events, use the Create Date filter, or Filter by criteria.
- For additional details about an event, click the vertical ellipsis for the event, and then select View Details. A window opens displaying details related to Endpoint Privilege Management, the rule, and the application.
- To create an exclusion or generate a rule from an event, click the vertical ellipsis for the event, and then select the appropriate exclusion or rule type to generate.
- Click the Download all (down arrow) button above the grid to download the events to a CSV file.
Depending on the configuration of your grid and selected columns, not all event details may be visible.
Exclusions can also be created from the Exclusions page.
Exclude Endpoint Privilege Management events
You can create exclusions to prevent recording unnecessary endpoint events. You can create and manage exclusions for Endpoint Privilege Management on the Endpoint Privilege Management Exclusions page.
Create an Endpoint Privilege Management exclusion
-
In the BeyondInsight console, go to Configuration > Privileged Desktop Management > Endpoint Privilege Management Exclusions.
-
Click Create Exclusion above the grid.
-
Select the Exclusion Type.
-
Enter the Exclusion Details.
-
Click Create Exclusion.
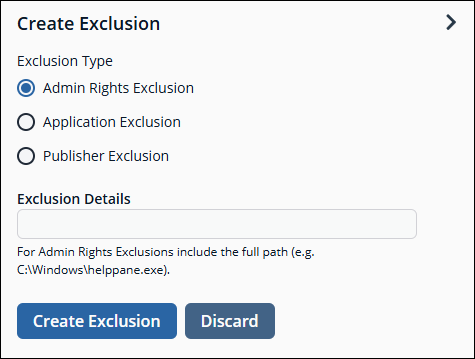
Exclusions can also be created from selected events on the Events page.
Manage exclusions
- Use the filters above the grid to filter the list of exclusions by the date they were created, as well as the exclusion details and type of exclusion.
- To edit or delete an exclusion, click the vertical ellipsis for the exclusion, and then select Edit Exclusion or Delete Exclusion.
Policies
Using BeyondInsight with Endpoint Privilege Management for Windows and Mac:
- Deploy Endpoint Privilege Management policies to assets and policy users.
- View a list of policies.
- Manage the global priority for the policies (in single-tenant environments only).
- With the appropriate permissions, manage all areas of policy, including view, unlock, edit, and delete.
Endpoint Privilege Management features are only available when an Endpoint Privilege Management license is detected.
Install Endpoint Privilege Management Policy Editor
There are two ways to deploy the Policy Editor:
- U-Series appliance: Starting in U-Series software version 4.2, the appliance is the preferred on-premises platform. Activate and manage the Policy Editor using the appliance software.
- First time setup: Endpoint Privilege Management in Run the U-Series Appliance deployment and configuration wizard.
- Updates: Configure U-Series Appliance features.
- Software installs: This option is used less frequently in favor of the appliance. For installation instructions when using the software install, see Install Policy Editor in BeyondInsight Instances.
View Endpoint Privilege Management policies
- From the left menu in BeyondInsight, select Policies under Endpoint Privilege Management.
- To filter the list of displayed policies, select the criteria from the Filter by list above the grid. Available filter options are:
- Policy Name
- Locked
- Locked By
- Policy Version
- Policy Workgroup
- Powered by
If you select Filter by > Locked, you can then select Locked or Unlocked as the filter criteria. If a policy is locked, this indicates that a user currently has it locked by a policy editor. The ability to lock, unlock, and edit policies in BeyondInsight is planned for a future release. If the Policy Editor is installed in your BeyondInsight instance, and you have sufficient permissions, you can unlock a policy that is locked by another user, and then lock the policy so you can edit it.
You can see who added, modified, or deleted a policy from the Configuration > General > User Audits page. Click the i button for a specific activity to view details.
Deploy policies using a Smart Rule
Use a Smart Rule to deploy policy to assets or policy users.
- From the Smart Rules page in BeyondInsight, select Asset or Policy User from the Smart Rule type Filter dropdown, and then click Create Smart Rule.
- Select your desired Selection Criteria.
- Under Actions, select Deploy Endpoint Privilege Management Policy from the dropdown.
- Click Select Policies for Deployment.
- Select the policies using the Add Policy button (plus sign) next to the policy.
- Use the arrow buttons to arrange the policies. The higher in the list the higher the priority of the policy. Alternatively, use the global priority feature to set the priority. If the global priority feature is active, you cannot set the priority using the arrow buttons.
- To use the arrows to change priority settings, select Configure Global Priority to deactivate the feature.
- Click Accept Changes.
We recommend setting policy priority using the global policy priority feature.
Manage global priority for Endpoint Privilege Management policies
If multiple Smart Rules contain the same asset and there is a different policy priority set in each Smart Rule, the Endpoint Privilege Management agent does not know the policy with top priority on that asset. In this case, a different policy can take precedence each time the agent processes the Smart Rules.
To prevent this, we recommend setting a global priority to process all policy Smart Rules and serve all policies across all applicable Smart Rules to the Endpoint Privilege Management agent as per the defined global priority order.
The global policy priority feature is supported only in single-tenant BeyondInsight installations. This feature is disabled in multi-organization environments.
The global policy priority feature is enabled by default on new installations of BeyondInsight 21.1 or later. It is not enabled by default when upgrading BeyondInsight versions prior to 21.1 to the 21.1 release or later releases.
Enable global policy priority as follows.
-
From the left menu in BeyondInsight, select Policies under Endpoint Privilege Management.
-
Click Configure Global Priority Policy, or if this is your first time using the global policy priority feature, click Configure Now in the banner that displays at the top of the page.
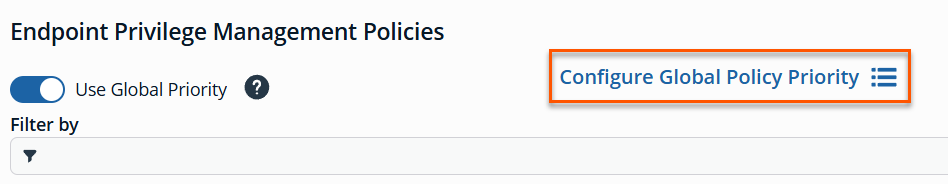
- Select the policies using the plus sign next to the policy and set their priorities using the arrows. Alternatively, you can manually specify the priority number in the box for the policy, and then click the plus sign.
All policies must be prioritized to enable the Use Global Priority option. Also, any policies added to BeyondInsight after global policy priority is enabled, are not available for assignment in Smart Rules until a priority is explicitly set for them here.
- Click Save Priority.
- The banner at the top of the page now indicates a global policy priority has been configured. Click the toggle to enable the Use Global Priority option.
- A confirmation message displays. Click Enable Global Policy Priority in the message box.
- Global policy is enabled, Smart Rule prioritization is disabled, and the policies display in the grid with their assigned priority.
Endpoint Privilege Management Web Policy Editor Components
Use the Endpoint Privilege Management Policy Editor to:
- Create policies in BeyondInsight, eliminating the need to use a standalone policy editor.
- View the properties of a policy
- Lock and unlock a policy
- Edit the policy configuration
- Delete a policy
Policy users must be assigned permissions to use the Endpoint Privilege Management feature:
- Read and write permissions to create, view, lock (or unlock), edit, and delete policies.
- Read-only permissions to only view policy information.
Policy editor components
Workstyles
Workstyles are used to assign Application Rules for a specific user, or group of users.
The Policy Editor in BeyondInsight supports integration with Microsoft Entra ID. Filters can be used in Workstyles to query Entra ID groups and users. Only one Entra ID tenant per organization is supported. For this integration to work, you must create an Entra ID directory credential in BeyondInsight.
Application groups
Application Groups are used by Workstyles to group applications together to apply certain Endpoint Privilege Management behavior.
Content groups
Content groups are used by Workstyles to group content together to apply certain Endpoint Privilege Management behavior.
Messages
Messages are used by Workstyles to provide information to the end user when Endpoint Privilege Management has applied certain behavior that you've defined and need to notify the end user.
Utilities
The WPE provides some useful tools to help with managing policies, including an import policy tool and a license management tool.
Use the QuickStart for Windows or Mac template
To get started quickly using the Policy Editor, create a new policy using either the QuickStart For Windows template, or the Quickstart For Mac template.
The QuickStart templates for Windows and Mac policies contain Workstyles, Application Groups, Messages, and Custom Tokens configured with Endpoint Privilege Management and Application Control. The QuickStart policy is designed from BeyondTrust’s experiences of implementing the solution across thousands of customers, and is intended to balance security with user freedom. As every environment is different, we recommend you thoroughly test this configuration to ensure it complies with the requirements of your organization.
Customize the QuickStart policy
Before deploying the QuickStart policy to your users, you must make some company-specific customizations to the standard template.
At a minimum you must:
- Configure the users or groups that can authorize requests that trigger messages.
- Assign users and groups to the high, medium, and low flexibility Workstyles.
- Populate the Block - Blocked Apps Application Group with any applications that you want to block for all users.
- Set your shared key so you can generate a Endpoint Privilege Management Response code.
QuickStart template summary
This section provides information about the properties for the Windows and Mac QuickStart templates, including the Workstyles and Application Groups that comprise the template.
WorkStyles
All users
This Workstyle contains a set of default rules that apply to all standard users regardless of the level of flexibility they need.
The All Users Workstyle contains rules to:
- Block any applications in the Block - Blocked Apps group.
- Allow Endpoint Privilege Management Support tools.
- Allow standard Windows and Mac functions, business applications, and applications installed through trusted deployment tools to run with admin rights.
- Allow approved standard user applications to run passively.
High flexibility
This Workstyle is designed for users that require a lot of flexibility, such as developers.
The High Flexibility Workstyle contains rules to:
- Allow applications that are in the Add Admin – High Flexibility group to run with admin rights.
- Allow known business applications and operating system functions to run.
- Allow users to run signed applications with admin rights.
- Allow users to run unknown applications with admin rights once they confirm that the application should be elevated.
- Allow unknown business application and operating system functions to run on demand.
Medium flexibility
This Workstyle is designed for users that require some flexibility, such as sales engineers.
- Allow applications that are in the Add Admin – Medium Flexibility group to run with admin rights.
- Allow known business applications and operating system functions to run.
- Allow users to run signed applications with admin rights once they confirm that the application should be elevated.
- Prompt users to provide a reason before they can run unknown applications with admin rights.
- Allow unknown business application and operating system functions to run on demand.
- Restricted OS functions that require admin rights are prevented and require support interaction.
Low flexibility
This Workstyle is designed for users that don't require much flexibility, such as helpdesk operators.
- Allow applications that are in the Add Admin – Low Flexibility group to run with admin rights.
- Prompt users to contact support if a trusted or untrusted application requests admin rights.
- Prompt users to contact support if an unknown application tries to run.
- Allow known approved business applications and operating system functions to run (Windows only).
Administrators
This Workstyle provides visibility on the Administrator accounts in use in the environment.
The Administrators Workstyle contains general rules to:
- Capture user and host information.
- Block users from modifying local privileged group memberships.
Application groups
The Application Groups that are prefixed with (Default) or (Recommended) are hidden by default and do not need to be altered. Click the Show Hidden button above the grid to see all Application Groups.
- Add Admin – All Users (Business Apps): Contains applications that are approved for elevation for all users, regardless of their flexibility level.
- Add Admin – All Users (Windows Functions): Contains operating system functions that are approved for elevation for all users.
- Add Admin – High Flexibility: Contains the applications that require admin rights that should only be provided to the high flexibility users.
- Add Admin – Low Flexibility: Contains the applications that require admin rights that should only be provided to the low flexibility users.
- Add Admin – Medium Flexibility: Contains the applications that require admin rights that should only be provided to the medium flexibility users.
- Block - Blocked Apps: This group contains applications that are blocked for all users.
- Passive - Allowed Functions & Apps: Contains trusted applications, tasks and scripts that should execute as a standard user.
- Passive - High Business Apps: Contains trusted applications, that should execute as a high flexibility administrative user.
- Passive - Low Business Apps: Contains trusted applications, that should execute as a low flexibility administrative user.
- Passive - Medium Business Apps: Contains trusted applications, that should execute as medium flexibility administrative user.
- (Default) Any Application: Contains all application types and is used as a catch-all for unknown applications.
- (Default) Any Trusted & Signed UAC Prompt: Contains signed (trusted ownership) application types that request admin rights.
- (Default) Any UAC Prompt: Contains application types that request admin rights.
- (Default) Privilege Management Tools: This group is used to provide access to a BeyondTrust executable that collects Endpoint Privilege Management for Windows troubleshooting information.
- (Default) Child Processes of TraceConfig.exe: Contains application types that request to run child processes of TraceConfig.exe.
- (Default) Signed UAC Prompt: Contains signed (trusted ownership) application types that request admin rights.
- (Recommended) Restricted Functions: This group contains OS applications and consoles that are used for system administration and trigger UAC when they are executed.
- (Recommended) Restricted Functions (On Demand): This group contains OS applications and consoles that are used for system administration.
- (Default) Trusted Parent Processes: Contains trusted applications that request to run parent processes.
Messages
The following messages are created as part of the QuickStart policy and are used by some of the Application Rules:
- Allow Message (Authentication): Asks the user to provide a reason and enter their password before the application runs with admin rights.
- Allow Message (Select Reason): Asks the user to select a reason from a dropdown menu before the application runs with admin rights.
- Allow Message (Support Desk): Presents the user with a challenge code and asks them to obtain authorization from the support desk. Support can either provide a response code or a designated, authorized user can enter their login details to approve the request.
- Allow Message (Yes / No): Asks the user to confirm that they want to proceed to run an application with admin rights.
- Block Message: Warns the user that an application has been blocked.
- Block Notification: Notifies the user that an application has been blocked and submitted for analysis.
- Notification (Trusted): Notifies the user that an application has been trusted.
Use the server role template
The Server Roles policy contains Workstyles, Application Groups, and Content Groups to manage different server roles such as DHCP, DNS, IIS, and print servers.
Server roles template summary
This template policy contains the following elements.
WorkStyles
- Server Role - Active Directory - Template
- Server Role - DHCP - Template
- Server Role - DNS - Template
- Server Role - File Services - Template
- Server Role - Hyper V - Template
- Server Role - IIS - Template
- Server Role - Print Services - Template
- Server Role - Windows General - Template
Application groups
- Server Role - Active Directory - Server 2008R2
- Server Role - DHCP - Server 2008R2
- Server Role - DNS - Server 2008R2
- Server Role - File Services - Server 2008R2
- Server Role - General Tasks - Server 2008R2
- Server Role - Hyper V - Server 2008R2
- Server Role - IIS - Server 2008R2
- Server Role - Print Services - Server 2008R2
Content groups
- AD Management
- Host Management
- IIS Management
- Printer Management
- Public Desktop
Manage Endpoint Privilege Management Policies: Web Policy Editor
Create a policy
- From the left menu, select Policies under Endpoint Privilege Management.
- Click Create Policy + above the grid.
- Enter a name for the policy and select a Workgroup from the list.
- Click Create Policy.
- Select one of the following:
- QuickStart for Windows: A preconfigured template with Workstyles, Application Groups, messages, and Custom Tokens already configured.
- QuickStart for Mac: A preconfigured template with Workstyles, Application Groups, and messages already configured.
- Server Roles: The Server Roles policy contains Workstyles, Application Groups, and Content Groups to manage different server roles such as DHCP, DNS, IIS, and print servers.
- Blank: Select to configure a policy from scratch. There are no preconfigured settings in this template.
The Policy Editor opens to the Workstyles page. At this point you must configure the Workstyle, Application Groups, Application Rules and other policy configuration as required for your organization. The templates and their configuration components are described in more detail in the below sections.
For quick access to the Workstyles Summary page, click the hyperlink for the Workstyle name.
View a policy
- From the left menu, select Policies under Endpoint Privilege Management.
- Click the vertical ellipsis for the policy you wish to view, and then select View Policy.
- The Policy Editor opens in Read Only mode.
If you wish to edit the policy, click the Policy List link at the top of the page to go back to the main Policies page where you can select the policy to edit and lock it.
- Use the options in the left navigation to view the following policy information:
- For Windows policies:
- Workstyles
- Application Groups
- Content Groups
- Messages
- For macOS policies:
- Workstyles
- Application Groups
- Messages
- Utilities:
- Licenses
- Import Policy
- Template Policies
You can also filter the contents displayed in each grid using the Filter By list above the grid.
Edit a policy
When you edit a policy, the policy is locked. Other policy administrators cannot access the policy to change the properties when the status is Locked. The policy is unlocked when changes are saved or discarded.
- From the left menu, select Policies under Endpoint Privilege Management.
- Click the vertical ellipsis for the policy you wish to edit.
- If a policy is locked, the Unlock Policy action displays in the menu. Click to unlock the policy.
- Select Edit and Lock Policy.
- In the Policy Editor, go to the policy property you want to change and make your edits.
- Click Save to save a draft of the policy. Clicking Save allows you to keep the Policy Editor open to continue changing the policy.
- Once the policy is updated, click Save and Unlock to save a new revision of the policy, or Discard Changes to remove changes.
- If Discard Changes is selected, you are prompted to Continue Editing or Discard Changes.
- (Optional). On the Save and Unlock dialog box, you can enter Annotation notes about the policy changes. You can also check the Auto Assign Policy to Groups? box, to automatically assign the latest revision to groups the policy is currently assigned to.
The Auto Assign Policy to Groups? option is only available when the groups are currently on the latest policy. If they are on an older version, only the Annotation notes option is displayed.
You can export a policy and import a policy to overwrite the existing one while viewing a policy in read-only mode and while editing a policy in read/write mode. Select Utilities > Import Policy from the left navigation, click Overwrite Policy, and then click Export Existing Policy to export. Drop a file in the box to upload a new policy and then click Upload File.
Policy Users
Create and view Smart Rules for Endpoint Privilege Management policy users
You can manage user-based policies for Endpoint Privilege Management users with Smart Rules, and view the policy users with the assigned policies.
This feature is only available when an Endpoint Privilege Management license is detected.
To deploy policies to users, you must first create rules and policies in the Endpoint Privilege Management Policy Editor, and then create applicable Smart Rules to deploy the policies to policy users.
Create a policy user Smart Rule
When a policy is deployed using a policy user-based Smart Rule, only the policy rules set in the User Configuration Rule Management section of the policy are processed by Endpoint Privilege Management clients that receive the policy. Policy deployment is controlled by the specifications in the Smart Rule.
A policy user-based Smart Rule can deploy policies to Windows Active Directory domain users and local users that are not part of a domain. Create the Smart Rules as follows:
- From the left menu in BeyondInsight, click Smart Rules.
- Select Policy User from the Smart Rule type filter dropdown.
- Click Create Smart Rule. A new window opens.
- Select Policy Users for the category.
- Provide a Name and Description for the policy.
- Select a Reprocessing Limit from the dropdown to set how often the Smart Rule runs.
- In the Selection Criteria section, select and add your desired filters to add the Endpoint Privilege Management accounts.
- To onboard local policy users, use the User Account Attribute filter after discovering users via scans. Then use their privilege attribute or their name for the Selection Criteria.
- In the Actions section, select and add the following actions:
- Add Policy Users: Adds users to BeyondInsight.
- Deploy Endpoint Privilege Management Policy: Deploys policies to the user accounts.
- Mark each policy user for removal: Deletes the user accounts from the Smart Group.
- Show as Group: Displays the Smart Rule as a Smart Group on the Policies page.
- Click Create Smart Rule.
View policy users
After the Smart Rule processes, you can view policy users on the Policy Users page. This page shows the policies assigned and applied.
- To view the page, click Policy Users on the Home page, or from the left menu under Endpoint Privilege Management.
- Displayed policy users are filtered by the selected Smart Group filter.
- Displayed policy users can also be filtered by other criteria.
- Displayed policy users can be downloaded, and the grid view can be modified.
Depending on the configuration of your grid and selected columns, not all policy user details may be visible.
- To remove a user from a policy, click the vertical ellipsis for the user, and select Delete Policy User.
Agents
View Endpoint Privilege Management agents
Agents are assets with Endpoint Privilege Management installed. You can view and download Endpoint Privilege Management agents on the Endpoint Privilege Management Agents page.
This feature is only available when an Endpoint Privilege Management license is detected.
To view the Endpoint Privilege Management Agents
- From the left navigation in BeyondInsight, click MENU.
- Under Endpoint Privilege Management, click Agents.
You can also access the Endpoint Privilege Management Agents page from the Assets page by clicking the Endpoint Privilege Management link at the top of the page.
- By default, displayed agents are filtered by the Discovery Scanners Smart Group. Select a Smart Group from the Smart Group filter to view agents for that Smart Group.
- To further filter the displayed agents, use the Last Updated filter, or Filter by criteria.
- Click the Download All button above the grid to download the list of agents to a CSV file.
Depending on the configuration of your grid and selected columns, not all agent details may be visible.
File Integrity Management
View Endpoint Privilege Management file integrity monitoring
You can view file integrity monitoring events using Endpoint Privilege Management. File integrity monitoring captures events related to created, edited, or deleted items in folders, according to the created rules.
This feature is only available when an Endpoint Privilege Management license is detected.
To view file integrity monitoring events:
- From the left navigation in BeyondInsight, click the MENU.
- Under Endpoint Privilege Management, click File Integrity Monitoring.
- By default, displayed events are filtered by the Discovery Scanners Smart Group. Select a Smart Group from the Smart Group filter to view events for that Smart Group.
- To further filter the displayed events, use the Create Date filter, or Filter by criteria.
- Click the Download All button above the grid to download the events to a CSV file.
Grid Configuration is not available for this grid.
Depending on the configuration of your grid and selected columns, not all file monitoring event details may be visible.
Session Monitoring
Monitor Endpoint Privilege Management sessions
You can view session details and replay sessions using Endpoint Privilege Management.
This feature is only available when an Endpoint Privilege Management license is detected.
View session details
- In the BeyondInsight Console, click the MENU.
- Under Endpoint Privilege Management, click Session Monitoring.
- By default, displayed sessions are filtered by the Discovery Scanners Smart Group. Select a Smart Group from the Smart Group filter to view sessions for that Smart Group.
- To further filter the displayed sessions, use the Filter by criteria above the grid.
- For additional details about a session, click the vertical ellipsis for the session, and then select View Details.
- Click the Download All button above the grid to download the sessions to a CSV file.
Depending on the configuration of your grid and selected columns, not all session details may be visible.
Session replay
- Follow the steps above to select a session.
- Click the vertical ellipsis for the session, and then select View Session... . View Session... is also available when viewing all session details.
- A new page opens, showing some details of the session, a list of the Events and when they occurred (which can be searched), and a slideshow of the session.
- Buttons under the slideshow control session playback. You can change the speed of session playback by selecting a different Slideshow Delay.
- You can download an image of any session view by clicking the Snapshot button.
Updated 13 days ago

