Map directory credentials to a domain | BI Cloud
What is a directory credential?
A directory credential is a username and password (or other authentication data) that provides access to an account within a directory service, such as Microsoft Active Directory (AD), LDAP, or Azure AD.
How is it mapping a directory credential useful?
Mapping a directory credential provides secure, automated, and fault-tolerant access to directory services, ensuring BeyondInsight can reliably authenticate users and manage accounts.
Domain management allows you to map a default primary directory credential and an optional fallback credential as preferred binding credentials used for account resolution against domains in your environment when logging in to BeyondInsight.
If credentials are not mapped, or both mapped credentials fail, BeyondInsight attempts login following the legacy process of not using mapped credentials.
Follow these steps to add or edit primary and secondary credentials for a domain:
-
Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. -
From the left menu, click
 .
.
The Configuration page displays. -
Under Role Based Access, select Domain Management.
The Domain Management page displays. -
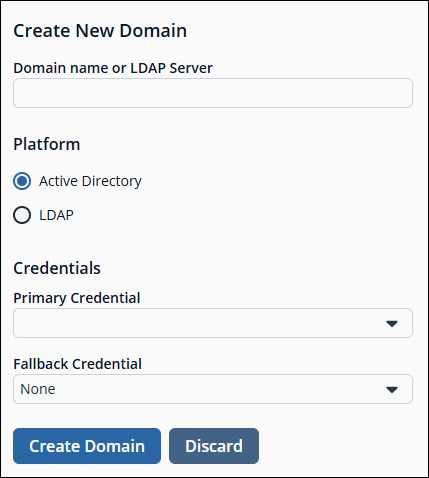
Click Create New Domain + to create a new one.
-
Provide the name of the domain or LDAP server.
-
Select the type of platform.
-
Select a Primary Credential from the dropdown.
-
Select a Fallback Credential from the dropdown.
-
Click Create Domain.
-
To edit credentials for an existing domain, select the domain from the left pane, make your edits, and then click Save Domain.
Primary and fallback credentials can include Password Safe managed accounts.
When domain management is configured for a domain and user selects the domain when logging into BeyondInsight, the specified primary and fallback credentials are used to resolve their account. The credentials used for authentication are shown in the Login Details for the specific login activity on the Configuration > General > User Audits page.
Updated 20 days ago

