Managed Accounts | BI On-prem
What are managed accounts?
Managed accounts are user accounts which are local or Active Directory accounts on the managed system.
How are managed accounts useful?
Managed accounts provide centralized control, security, and automation for user accounts on managed systems.
How to access managed accounts
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email. - From the left menu, click Managed Accounts.
The Managed Accountspage opens and displays.
The Managed Accounts page
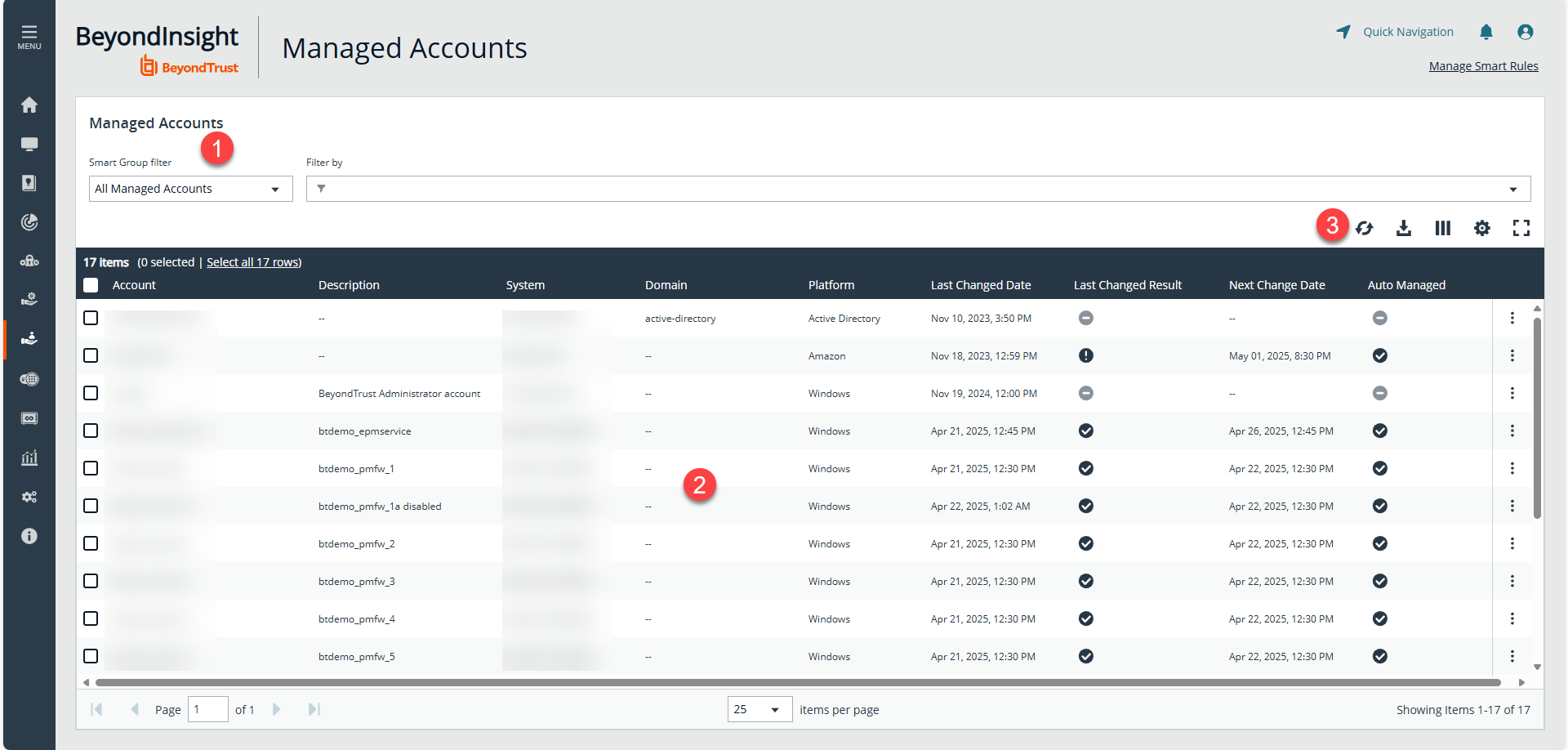
- Filters: Select an item in the filter dropdowns to filter information.
- Managed System grid: Displays information based on filter selections.
- Grid display preferences: Set display preferences on the Assets grid using the following options represented by icons above the grid:
- Refresh: Refresh the grid display.
- Download all: Download all assets in the grid to an Excel spreadsheet.
- Columns Chooser: Select the columns to change the column headings and information displayed in the grid.
- Grid Configuration: If available, choose the grid layout: Compact, Default, or Expanded.
- Expand Grid: Enlarge the display area. When selected, the icon changes to Collapse Grid. Click it to collapse the grid back to its original display.
View managed accounts
Create and Manage User Accounts
User accounts create the user identity that BeyondInsight uses to authenticate and authorize access to specific system resources. You can create local BeyondInsight users, as well as add Active Directory, Entra ID, and LDAP users into BeyondInsight.
You can also add application users, which are used to represent applications that interface with the public API. Application users cannot log in to the BeyondInsight console. They can only authenticate and interact with the public API.
A user account must be a member of a BeyondInsight user group because permissions to features are assigned at the group level. If a user is not a member of any groups in BeyondInsight, the user cannot log in to the console, and application users cannot authenticate with the public API.
Create a BeyondInsight local user account
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click the Users tab to display the list of users in the grid.
-
Click Create New User above the grid.
-
Select Create a New User.
-
Provide a First Name, Last Name, Email, and Username for the new user. These fields are required.
You may use an email address for the username.
- Provide a password and confirm it.
The password must meet the complexity requirements as defined by your default password policy, defined at Configuration > Role Based Access > Password Policy.
- Optionally, enter the user’s contact information.
- Optionally, set an Activation Date and an Expiration Date for the user account.
These dates are based on UTC time on the BeyondInsight server and are considered during the user's login attempt. The attempt fails if the user account is not yet active or if the expiration date has passed.
- Check User Active to activate the user account.
- Leave the Account Locked and Account Quarantined options unchecked.
- Check the two Authentication Options, if applicable:
- Override Smart Card User Principal Name: When enabled, a BeyondInsight user with a smart card that has a different Subject Alternative Name is able to log in to BeyondInsight. The smart card is mapped to the user.
- Disable Login Forms: When enabled, SAML users are prevented from using the standard BeyondInsight log in form and authenticate with a configured identity provider. Check this option only if SAML is configured in your environment.
- Select a Two-Factor Authentication method and mapping information, if applicable.
- Click Create User.
The user is created and User Details > Groups displays. - Filter the list of groups displayed by type, name, or description and select a group.
- Click Assign Group above the grid.
The user must belong to at least one group
- To remove the user from a group:
- Select Assigned Groups from the Show dropdown, and then select a group.
- Click Remove Group above the grid.
Update default password policy for local users
The default password policy defines the password complexity requirements for local BeyondInsight users. This includes the minimum and maximum length of the password and the type of characters required and permitted in the password. Update the default password policy as follows:
- From the left sidebar, click Configuration.
- Under Role Based Access, click Password Policy.
- Enter a name for the policy and an optional description.
- Set the minimum and maximum password length.
- Set the types of characters to be used: uppercase, lowercase, numeric, and non-alphanumeric.
- Toggle the Enforce Minimum Characters To Change option to enable it. This compares the previous password to the new password when a user is updating their password via their account settings change password function.
- Optionally, increase the Minimum Characters To Change. The default is 8 and cannot be decreased.
- Click Update Password Policy to save the policy.
Add an active directory user
Active Directory users can log in to the management console and perform tasks based on the permissions assigned to their groups. The user can authenticate against either a domain or domain controller.
Active Directory users must log in to the management console at least once to receive email notifications.
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click the Users tab to display the list of users in the grid.
-
Click Create New User above the grid.
-
Select Add an Active Directory User.
-
Select a credential from the list.
If you require a new credential, click Create a New Credential to create a new credential. The new credential is added to the list of available credentials.
- If not automatically populated, enter the name of a domain or domain controller.
- After you enter the domain or domain controller credential information, click Search Active Directory. A list of users in the selected domain is displayed.
For performance reasons, a maximum of 250 users from Active Directory is retrieved. The default filter is an asterisk (*), which is a wild card filter that returns all users. Filter by user name to refine the list.
Example
Sample filters:
- a returns all group names that start with a.
- _d returns all group names that end with d.
- _sql returns all groups that contain sql in the name.
- Click Search Active Directory.
- Select a user, and then click Add User.
- Assign at least one group to the user.
Add an Entra ID user
Entra ID users can log in to the management console and perform tasks based on the permissions assigned to their groups. The user can authenticate against either a domain or domain controller.
Entra ID users must log in to the management console at least once to receive email notifications.
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click the Users tab to display the list of users in the grid.
-
Click Create New User above the grid.
-
Select Add a Microsoft Entra ID User.
-
Select a credential from the list.
If you require a new credential, click Create a New Credential to create a new credential. The new credential is added to the list of available credentials.
For performance reasons, a maximum of 250 users from Entra ID is retrieved. The default filter is an asterisk (*), which is a wild card filter that returns all groups. Filter by user name to refine the list.
Example
Sample filters:
- a returns all group names that start with a.
- _d returns all group names that end with d.
- _sql returns all groups that contain sql in the name.
- Click Search Microsoft Entra ID.
- Select a user, and then click Add User.
- Assign at least one group to the user.
Change the preferred domain controller for active directory user accounts
The preferred domain controller for a user is set by the group they are in, provided that the group was created with the propagate option turned on, and that this action happened before the user was set up.
If you want to change the preferred domain controller for a user, edit the user, select an appropriate credential, and then select a different preferred domain controller from the list.
Any future change to the preferred domain controller at the group level can overwrite this setting if the propagate switch is turned on.
Add an LDAP user
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click the Users tab to display the list of users in the grid.
-
Click Create New User above the grid.
-
Select Add an LDAP User from the list.
-
Select a credential from the list.
If you require a new credential, click Create a New Credential to create a new credential. The new credential is added to the list of available credentials.
- Click Fetch to load the list Domain Controllers, and then select one.
- To filter the user search, enter keywords in the user filter or use a wild card.
- Click Search LDAP.
- Select a user, and then click Add User.
- Assign at least one group to the user.
Add an application user
Application users represent applications that interface with the BeyondInsight public API. Application users cannot log in to the BeyondInsight console. They can only authenticate and interact with the public API, using Client ID and Client Secret for credentials within the OAuth client credential flow.
An API Registration type of API Access Policy must be assigned to an application user, and is used for processing IP rules. To create an application user:
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click the Users tab to display the list of users in the grid.
-
Click Create New User above the grid.
-
Select Add an Application User from the drop-down list. The Create New Application User screen displays.
-
Add a username.
-
Under API Access Policy, select the policy.
-
Copy the information from the Client ID and Client Secret fields for later use.
-
Click Create User.
-
Assign the user to a group that has the required permissions to access BeyondInsight and Password Safe features.
- Click the vertical ellipsis for the user, and then select View User Details.
- From the User Details pane, click Groups.
- Locate the group, select it, and click Assign Group above the grid.
Recycle the client secret for an application user
When editing an application user, you have an option to recycle their secret. Once recycled, you can copy or view the new secret. When a secret is recycled and the user account is updated with this change, the previous client secret is no longer valid.
To recycle the secret for an application user:
- From the left sidebar, click Configuration.
- Under Role Based Access, click User Management.
- Click the Users tab.
- Locate the application user in the grid.
- Click the ellipsis to the right of the user, and then select Edit User Details.
- Click the Recycle icon to the right of the Client Secret.
- Click Recycle on the confirmation message that displays.
- Copy the new secret for later use.
- Click Update User.
View and update OAuth secret expiry
The user's secret will eventually expire. The Users grid has an OAuth Secret Expiry column, which you can use to view what is close to expiring. The default duration of a client secret is 365 days. You can adjust the lifetime of the secret from the Authentication Options configuration area in BeyondInsight. Updating this value only changes the secret expiry date for new application users and recycled client secrets. Older secrets cannot be updated.
To view the OAuth Secret Expiry for an application user:
- From the left sidebar, click Configuration.
- Under Role Based Access, click User Management.
- Click the Users tab.
- Locate the application user. The OAuth Secret Expiry column lists the date and time that a client secret for that user expires.
To update the duration for client secrets:
- From the left sidebar, click Configuration.
- Under Authentication Management click Authentication Options.
- Under Application User Authentication Settings, enter the new duration of the client secret in the Client Secret Expiry field.
- Click Update Application User Authentications Settings.
Edit a user account
Administrators can edit user details such as change the name, username, email, and password, update active status, lock and unlock the account, and update multi-factor authentication settings as follows:
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click Users to display the list of users in the grid.
-
Optionally, filter the list of users displayed in the grid using the Filter By dropdown.
-
Select a user, click the vertical ellipsis button, and then select Edit User Details.
-
In the Edit User pane, update the details as required, and then click Update User.
Add user to groups
- From the User Management page, click the Users tab to display the list of users in the grid.
- Optionally, filter the list of users displayed in the grid using the Filter by dropdown.
- Select a user or multiple users, and then click the Add User to Groups button above the grid.
- Search for the group or groups, and then select the group or groups to assign currently selected users to the selected groups.
If a group already contains all of the selected users, a check mark is displayed next to the group name.
Delete a user account
Administrators can delete user accounts as follows:
-
From the left sidebar, click Configuration.
-
Under Role Based Access, click User Management.
-
Click the Users tab to display the list of users in the grid.
-
Optionally, filter the list of users displayed in the grid using the Filter by dropdown.
-
For local accounts, select the user, click the Delete button above the grid, and then click Delete to confirm.
-
For directory accounts, select the user, click the vertical ellipsis, select Delete User, and then click Delete to confirm.
For auditing purposes, if a user account is linked to any Password Safe session recordings, you cannot delete the account; however, you may disable the account.
Directory accounts may be deleted only if they do not belong to any groups.
Work with managed accounts
Managed accounts are user accounts which are local or active directory accounts on the managed system.
View managed accounts
When viewing managed accounts, you can change the number of items displayed on the page using the Items per page dropdown at the bottom of the grid. You can use the filters above the grid to filter the list by smart group and the various attributes listed in the Filter by dropdown.
View managed account details
After the account is added to Password Safe management, you can:
- Review the attributes and settings assigned to the account, such its identifying details, settings, and policies.
- View managed systems linked to the account.
- View Smart Groups associated with the account, as well as their last process date and processing status.
- See which accounts are synced to the managed account.
- View a list of password changes and the reason for each change.
To view details on a specific managed account:
- From the Managed Accounts page, click the vertical ellipsis for the account.
- Select Go to Advanced Details.
- Managed account details, such as identification information, account settings, policies and attributes are displayed under Details & Attributes for quick access.
- To see more granular details, click through the tabs in the Advanced Details pane to view details on each topic.
Click the View Managed System link above the grid to view the advanced details for the managed system associated with the managed account. To return to the advanced details for the managed account, click the View Managed Account link.
Delete managed accounts
Managed accounts can be deleted, except for synced accounts. A message is displayed if an account cannot be deleted.
- From the menu, select Managed Accounts.
- Select the account or multiple accounts you want to delete, and then click the Delete button above the grid.
- Click Delete on the confirmation message.
Unlink managed accounts
You can unlink managed accounts from managed systems; however, this applies to Active Directory accounts only. If accounts included in the unlink selection are not domain accounts, no action is taken on those accounts.
- From the menu, select Managed Accounts.
- Select the account or multiple accounts you want to unlink, and then click the Unlink button above the grid.
- Click Unlink on the confirmation message.
Change passwords for managed accounts
- From the menu, select Managed Accounts.
- Select the account or multiple accounts for which you want to change the password, and then click the Change Password button above the grid.
- Click Change Password on the confirmation message.
Configure subscriber accounts
Subscriber Accounts vs. Synced Accounts
- A parent account can have one or more synced accounts connected to it.
- A child account is considered a subscriber account of its parent.
You can view synced accounts in the Managed Account Details section of the parent account.
In the Managed Accounts API, child accounts are labeled as subscriber accounts, and include the ID of their parent account.
To enable Password Safe to update the account automatically, Automatic Password Management must be turned on for both the subscriber account and the associated managed system.
Any managed account can be synced to multiple accounts. These synced accounts become subscribers to the managed account. The managed account and all of its subscribers always share an identical password. When the password of the managed account or any of the subscriber accounts is changed, Password Safe automatically changes the password of the primary managed account and all of its subscribers to a new password.
To allow Password Safe to update the account, Automatic Password Management must be enabled for both the subscriber account and its associated Managed System
Once an account is synchronized as a subscriber account, settings modifications are limited to:
- Enable API
- Allow for scanning
- Application
To sync an account:
- From the Managed Accounts page, click the vertical ellipsis button for the account.
- Select Go to Advanced Details.
- Under Advanced Details, click Synced Accounts.
- Select the account or multiple accounts that you want to sync.
- Click Sync Accounts above the grid.
- To remove a synced account, select the account, and then click the Unsync Accounts button above the grid.
Configure password reset for managed account users
You can grant managed account users permission to reset the password on their own managed account, without granting them permission to reset passwords on other managed accounts. You can do this by creating a group, adding the managed account to the group, and then assigning permissions and the Credential Manager role to the group.
-
In the BeyondInsight console, go to Configuration > Role Based Access > User Management.
-
From the Groups tab, click Create New Group.
-
Select Create a New Group.
-
Provide a name and description for the group, and then click Create Group.
-
From the Group Details pane, select Users.
-
Select users to add to the group, and then click Assign User above the grid.
-
From the Group Details pane, select Features.
-
Select the Management Console Access and Password Safe Account Management features, and then click Assign Permissions.
-
Select Assign Permissions Read Only. Do not grant Full Control.
-
From the Group Details pane, select Smart Groups.
-
Filter the list of Smart Groups by Type > Managed Account.
-
Select the Smart Group that contains the applicable managed accounts.
-
Click the vertical ellipsis button for the Smart Group, and then select Edit Password Safe Roles.
-
Select the Credentials Manager role, and then click Save Roles.
The managed account user can now log in to the console and reset the password for the managed account:
- Go to the Managed Accounts page.
- Select the account.
- Click the vertical ellipsis button for the account.
- Select Change Password.
Use a managed account as a Discovery Scan credential
A managed account can be used as a credential when configuring a Discovery Scan.
Once the Scanner option is enabled, the key must be specified again if the account is edited. It may be the same key or a new one.
The following credential types are supported:
- Windows,
- SSH
- MySQL
- Microsoft SQL Server.
The following platforms are supported:
- Windows
- MySQL
- Microsoft SQL Server
- Active Directory
- Any platform with the IsUnix flag (AIX, HP UX, DRAC, etc.)
To add the managed account as a scan credential:
- From the Managed Accounts page, click the vertical ellipsis button for the account.
- Select Edit Account.
- Expand Scanner Settings.
- Click the toggle to enable the scanner.
- For the Scanner Credential Description, enter a name for the account that can be selected as the credential when setting up the scan details. The name is displayed on the Credentials Management dialog box when setting up the scan.
- Assign and confirm a key so that only users that know the key can use the credential for scanning.
- Click Update Account.
The Managed Account password can be up to 256 characters, however the password is limited to the length supported by the target platform. With scan credentials, keep in mind the password length limitations on that endpoint.
For more information on configuring credentials, see Add Credentials for Use in Scans.
Managed account aliasing
Aliases are accessible using the API only. Account mappings can be changed without affecting the alias name. At least one managed account is required to be mapped for the alias to be active; when an alias has two or more managed accounts mapped, it is considered to be highly available. An account can only be mapped to one alias. Managed account aliases can be accessed from Configuration > Privileged Access Management > Managed Account Aliases.
Create a new alias
- Navigate to Configuration > Privileged Access Management > Managed Account Aliases.
- Click Create New Alias +.
- Enter a name, and then click Create Alias.
The new alias appears in the grid under Account Mappings, which displays all aliases ready to be mapped. New aliases show as Unmapped until they are associated with accounts.
Each managed account can only be mapped to a single alias.
You can use the dropdown to select which accounts to display: All Accounts, Mapped, or Unmapped Accounts only.
The Filter-by allows you to filter accounts by System, Account Name, Account Status, or Last Changed Date.
To unmap an account, select the account and click the broken link icon.
Mapped accounts have three status values:
- Active: The account credentials are current and can be requested.
- Pending: The account credentials are current but the password is queued to change.
- Inactive: The account password is changing.
The list of mapped accounts is rotated in a round-robin fashion, typically in order of last password change date. The preferred account, or the account whose status is active and has the oldest change date, is returned on the Alias API model.
Updated 16 days ago

