Configuration | BI Cloud
What is configuration within Password Safe?
Configuration refers to setting up and customizing Password Safe's features, components, or settings to meet specific requirements or preferences.
How is configuration useful?
Configuring Password Safe tailors the product to a user's specific needs.
How do I access the Configuration page?
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Configuration page displays.
The Configuration page
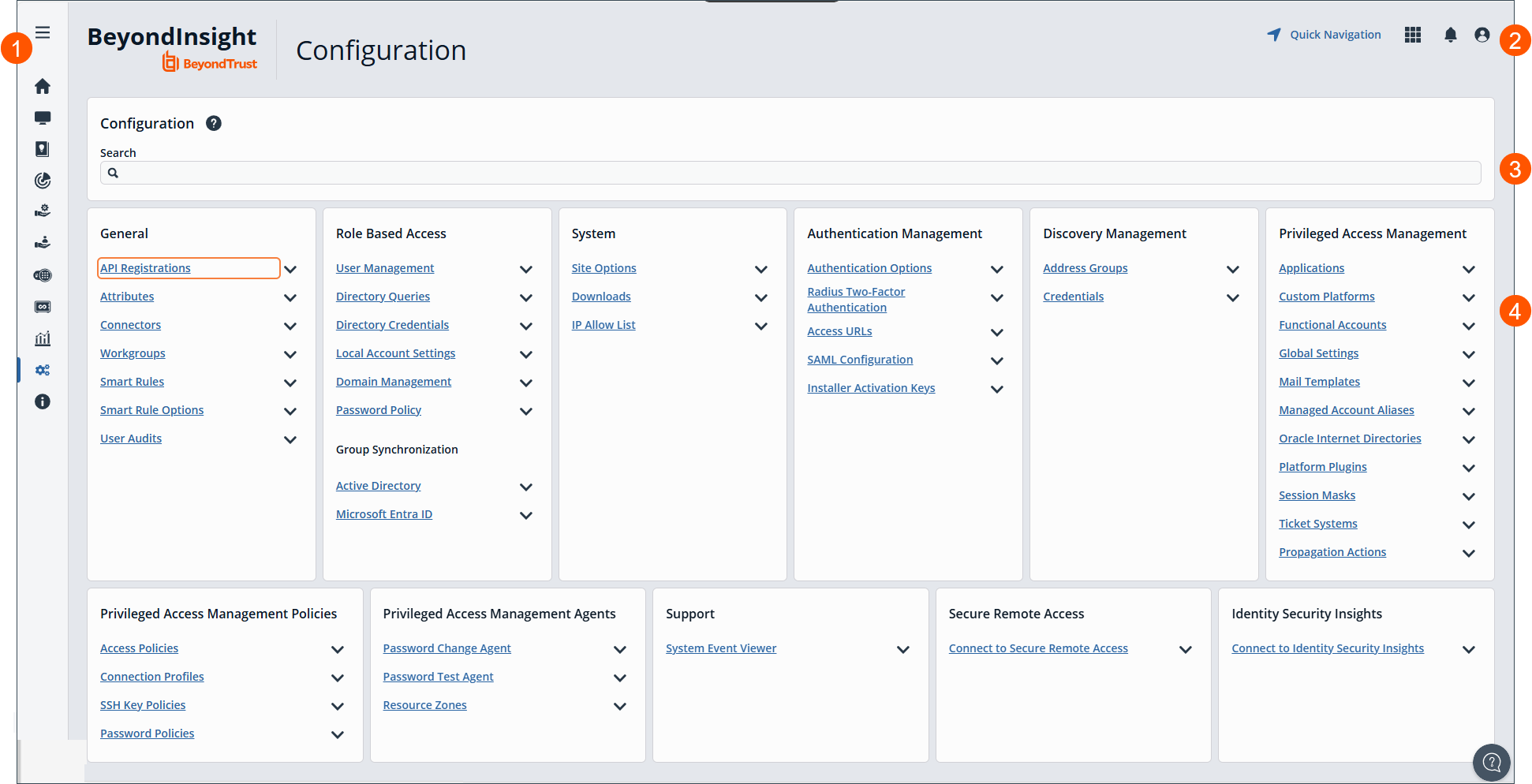
- Left menu: Easy access to all pages in BeyondInsight/Password Safe, including the Home, Assets, Smart Rules, Discovery Scanner, Management Systems, Managed Accounts, Password Safe, Secrets Safe , Analytics and Reporting, Configuration, and About pages.
- Header: Navigate to your favorite pages, view your notifications, access your connected apps, and set your account preferences.
- Search: Search for a configuration item or
- Select a configuration item from the body of the page.
Configure a cloud connector
-
Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. -
From the left menu, click
 .
.
The Configuration page displays. -
Under General, select Connectors.
The Connectors page displays. -
In the Connectors pane, click Create New Connector.
-
Provide a name for the connector.
-
Select a Connector Type from the list.
-
Click Create Connector.
-
Enter the connector information in the right pane:
-
For AWS cloud connections, required fields are: Region, Access Key ID, and Secret Access Key ID.
Instances associated with the region are displayed in the Connection Test Results section.
-
For Azure, required fields are: Region, Client ID, Client Server, Tenant ID, and Subscription ID.
-
For Google Cloud, required fields are Server (the region), Project Name (the project ID), and the Key File. Upload the key that you downloaded from the Google Cloud.
-
Hyper-V server, required fields are: Server (IP address), Username, and Password.
-
For Rackspace, required fields are Account Type, Username, and API Key.
-
-
After you configure the connector, click Test Connector to ensure the connector works.
-
Click Create Connector.
After you create a cloud connector, you can run a scan and review the results to determine what cloud assets were discovered..
Cloud connector Smart Groups
You can create Smart Groups based on the cloud connectors that you are using.
- Use a browser to sign in to your BeyondInsight/Password Safe URL.
This URL is provided in the BeyondTrust welcome email and includes your site URL followed by /login. - From the left menu, click
 .
.
The Smart Rules page displays. - Click Create Smart Rule.
- Select a category, and then enter a name and description.
- Under Selection Criteria, select Cloud Assets.
- Select the cloud connector type to filter on (AWS, Azure, Hyper-V).
- For AWS, click Select AWS Instance Types to pick specific instance types.
- For AWS, Azure, and Google, check the Use Private IP Address box to scan internal IP addresses.
- Under Actions, select Show asset as Smart Group.
- Click Create Smart Rule.
Configure BeyondInsight AWS connector
This section provides information on setting up an Amazon AWS connector, including details on the AWS configuration.
Set up a policy
- Log in to the AWS Management Console.
- Select Identity & Access Management.
- Select Policies from the Details menu.
- Select Create Policy.
- Select Create Your Own Policy.
- Enter a policy name and description.
- Paste the following JSON into Policy Document:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"elasticloadbalancing:DescribeLoadBalancers",
"ec2:DescribeInstances",
"ec2:DescribeRegions",
"ec2:DescribeInstanceStatus",
"ec2:DescribeImages"
],
"Resource": "*"
}
]
}For "Resource": "*", you must determine what JSON is required for your current needs. You may also need a condition with this, such as if you want only the dev group to have access to certain instances.
Grant access to a third party (optional)
The ARN and External Name fields are for granting access to a third party. For more information, see How to Use an External ID When Granting Access to Your AWS Resources to a Third Party.
After you configure the AWS settings, you can create the AWS Scan Target Collector connector and Smart Group in the BeyondInsight console.
When creating, editing, or viewing the connector, the Cloud Scan Targets grid only shows results immediately after a test is completed. The targets are not automatically loaded into the BeyondInsight UI each time the connector is viewed or edited.
Updated 21 days ago

