Smart Rules in Password Safe | PS On-prem
What are Smart Rules?
A Smart Rule is a filter that you can use to organize assets into Smart Groups. Use an asset-based Smart Rule to organize assets based on the filters selected.
What are Smart Groups?
Smart Groups are groups, created by non-administrators, that contain assets. These Smart Groups are automatically associated with:
- Read permissions for all groups the group creator is a member of
- Full Control permissions for all groups the user is a member of, and where the user has the Asset Management and Smart Rule Management permissions for
How are Smart Rules useful?
When you use a Smart Rule to register assets as Smart Groups, you can run Discovery Scans and monitor and view assets. Smart rules can:
- Save time: Automate actions based on vulnerability findings or asset changes saves time for IT and security teams.
- Ensure consistency: Actions are taken consistently, reducing the risk of human error or missed steps in critical processes.
- Reduce risk: By automating responses to vulnerabilities and security issues, Smart Rules help reduce the time window in which systems remain vulnerable.
- Enhance compliance: Smart Rules help ensure that remediation efforts align with compliance requirements, automating compliance workflows and reporting.
- Improve your security posture: Automating security processes leads to quicker identification and remediation of risks, improving overall security.
You can use Smart Groups to add assets, systems, and accounts into Password Safe management. The Smart Rule filters that you configure for the Smart Groups determine the assets that are added as managed systems and managed accounts in Password Safe.
There are four types of Smart Rules available with a Password Safe license: Asset, Managed Account, Managed System, and Policy User.
You can use Smart Rules to add the following types of assets:
- Systems
- Network Devices
- Databases
- Local Linux and Windows accounts
- Active Directory accounts
- Dedicated accounts
The settings in a Smart Rule override the settings configured on the managed system.
How do I access Smart Rules?
- Open a browser and enter the URL for your Password Safe instance: https://<hostname>/WebConsole/index.html.
You may need to accept a pre-login message, if one has been configured on your instance.
- Enter your username and password.
- From the left menu, click
 .
.
The Smart Rules page displays.
The Smart Rule page
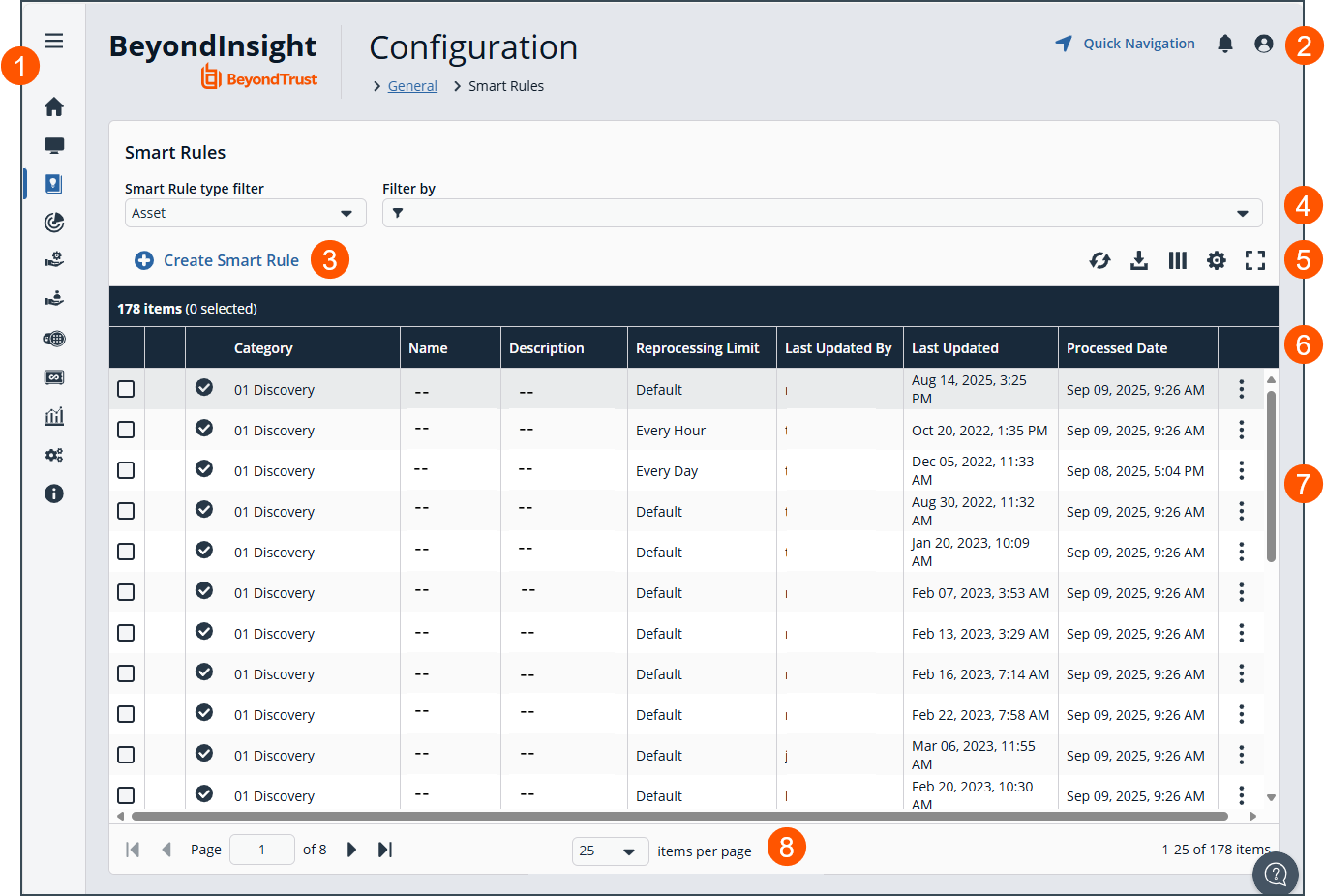
- Left menu: Easy access to all pages in BeyondInsight/Password Safe, including the Home, Assets, Smart Rules, Discovery Scanner, Management Systems, Managed Accounts, Password Safe, Secrets Safe , Analytics and Reporting, Configuration, and About pages.
- Header: Navigate to your favorite pages, view your notifications, and set your account preferences.
- Create Smart Rule: Click to create a new Smart Rule.
- Filters: Select a filter to refine your results.
Filter types
-
Smart Rule type filter: Filter by Asset, Managed Account, or Managed System,
-
Filter by: Filter by Locked, Status, Category, Name, Description, Reprocessing Limit, Last Updated By, Last Updated, or Action.
-
- Grid display preferences: Set display preferences on the Smart Rules grid using the following options represented by icons above the grid:
- Click
 to refresh the list,
to refresh the list,  to download the list to a .csv file,
to download the list to a .csv file,  to select which columns to display on the page,
to select which columns to display on the page,  to configure your page display, and
to configure your page display, and to expand the grid.
to expand the grid.
- Click
- Smart Rules list columns: Not all columns display in the image above.
Column Names
-
Category
-
Name
-
Description
-
Reprocessing Limit
-
Last Updated By
-
Last Updated
-
Processed Date
-
Processing Status
-
Last Attempt
-
Average Time (min)
-
Successful Attempts
-
Failed Attempts
-
- Smart Rules grid: Displays information based on filter selections.
- List navigation options: Navigate in the Smart Rule list.
Predefined Smart Groups
By default there are Smart Groups already defined and created.
The following tables list Smart Groups useful in Password Safe environments.
Asset based Smart Groups
| Smart Group | Category | Definition |
|---|---|---|
| All Assets in Password Safe | Assets and Devices | All assets under Password Safe management. |
| Recent Assets not in Password Safe | Assets and Devices | All assets discovered in the last 30 days that have not yet been added to Password Safe. |
| Recent Non Windows Assets not in Password Safe | Assets and Devices | All non Windows assets discovered in the last 30 days that have not yet been added to Password Safe. |
| Recent Windows Servers not in Password Safe | Servers | Windows servers discovered in the last 30 days that have not yet been added to Password Safe. |
| Recent Virtual Servers not in Password Safe | Virtualized Devices | Virtualized server assets discovered in the last 30 days that have not yet been added to Password Safe. |
Managed system Smart Rules
| Smart Rule | Category | Definition |
|---|---|---|
| Database Managed Systems | Types | Database Managed Systems |
| Directory Managed Systems | Types | Directory Managed Systems |
| Cloud Managed Systems | Types | Cloud Managed Systems |
| Asset Managed Systems | Types | Asset Managed Systems |
| All Managed Systems associated with BeyondInsight Assets | Managed Systems | All Managed Systems associated with BeyondInsight Assets |
| All Managed Systems not associated with BeyondInsight Assets | Managed Systems | All Managed Systems not associated with BeyondInsight Assets |
| All Managed Systems | Managed Systems | All Managed Systems |
| Recently Added Managed Systems | Managed Systems | Managed Systems added less than 30 days ago |
Managed accounts Smart Groups
| Smart Group | Definition |
|---|---|
| All Managed Accounts | All accounts managed by Password Safe. |
| Recently Added Managed Accounts | Filters on managed accounts added less than 30 days ago. |
| Database Managed Accounts | Filters on the database platform and includes SQL Server and Oracle platforms. |
| Hardware Device Managed Accounts | Filters on hardware devices including Dell DRAC and HP iLO platforms. |
| Linux Managed Accounts | Filters on the Linux platform. |
| Mac Managed Accounts | Filters on the macOS platform. |
| Unix Managed Accounts | Filters on the Unix platform. |
| Windows Managed Accounts | Filters on the Windows platform. |
Considerations when designing Smart Rules
- The filter criteria is processed hierarchically. When creating the filter structure, place the filters that reduce the largest number of entities at the top of the hierarchy.
- When adding Active Directory accounts using a directory query, ensure the query is as restrictive as possible. For example, configure the query on a smaller set of data in your environment.
- When adding assets to Password Safe, be cautious about creating more than one Smart Rule with the same systems or accounts. If the Smart Rules have different actions, they will start continually overwriting each other in an endless loop.
- There can be delays when a Smart Rule depends on external data source, such as LDAP, as processing can take longer. For example, a directory query that uses the discover accounts feature (managed account Smart Rule) or discover assets feature (asset-based Smart Rule).
Smart Rule processing
A Smart Rule processes and updates information in Smart Groups when certain actions occur, such as the following:
- The Smart Rule is created, or edited and saved.
- A timer expires.
- You manually kick off the processing by selecting the Smart Rule from the grid on the Smart Rules page, and then click Process.
The Process action from the grid on the Smart Rules page does not apply to managed account and managed system Quick Group Smart Rules, because these only run once upon creation and cannot be triggered to run again.
- A Smart Rule with Smart Rule children triggers the children to run before the parent completes.
- Managed account Smart Rules with selection criteria Dedicated Account process when a change to a mapped group is detected. This can occur in the following scenarios:
- A new user logs on.
- The group refreshes in Active Directory by an administrator viewing or editing the group in Configuration > Role Based Access > User Management.
Change the processing frequency for a Smart Rule
By default, Smart Rules process when asset changes are detected. The assets in the Smart Rule are then dynamically updated. For Smart Rules that require more intensive processing, you might want Smart Rules to process less frequently.
To provide more restrictive processing, you can select alternate frequency settings to override the default processing. The Smart Rules process in the selected time frame (for example, the rule processes once a week).
When creating a new Smart Rule or updating an existing one, select your desired frequency from the Reprocessing limit list in the Details section.
A Smart Rule is always processed when first saved or updated.
View and select Smart Rules processing statistics
The Smart Rules grid displays some processing statistics by default. Additional Smart Rules processing statistics, such as Processed Date, Successful Attempts, and Failed Attempts are available and can be displayed in the Smart Rules grid.
To add this information to the grid:
-
From the left menu, click
 .
.
The Smart Rules page displays. -
Click
 above the grid.
above the grid. -
Click the desired column to add that information to the grid.
- Check marks indicate columns currently displayed.
- You can remove a displayed column by clicking the column name in the Column chooser list.
- If there are more columns displayed than can fit in the width of the screen, a scroll bar appears at the bottom of the grid. It may be necessary to scroll sideways to view any additional columns.
Use dedicated account Smart Rule
A dedicated account Smart Rule allows you to dynamically map dedicated administrative accounts outside of BeyondInsight to users in a BeyondInsight group. This allows a lower privileged BeyondInsight user to access a higher privileged user's account temporarily while using Password Safe.
The below procedures provide instructions for configuring BeyondInsight users with the ability to access a dedicated directory account's credentials, using a query matching on directory attributes. Once configured, the users are able to request a password checkout for the dedicated account from the Password Safe portal. The user can then access resources using the dedicated account credentials.
You must configure the following in BeyondInsight:
- Create a directory query to retrieve the directory account as well as its attributes.
- Create a Smart Rule to run the directory query to find the account and its directory attributes, and add it as a managed account in Password Safe.
- Create a Smart Rule to map the dedicated account to a user group in BeyondInsight.
- Assign user group permissions to the two newly created Smart Rules.
Create the directory query
- From the left menu, click
 .
.
The Configuration page displays. - Under Role Base Access select Directory Queries.
- Click + Create New Directory Query, and complete form:
- Directory Type: Leave as Active Directory.
- Title: Provide a meaningful name that allows for easy identification of the query.
- Credentials: Select a credential that has permissions to query the directory user accounts.
- Query Target: Provide the LDAP path to the target.
- Scope: Leave as This Object and All Child Objects.
- Object Type: Select User Objects.
- Dynamically refresh results each use: Leave enabled.
- Basic Filter: Provide the name of the dedicated account.
- Click Create Directory Query.
Create the Smart Rule to run the directory query and add managed account
This example is specific to managed accounts. Similar instructions apply for the other rule or entity types
- From the left menu, click
 .
.
The Smart Rules page displays. - Select Managed Account from the Smart Rule type filter dropdown.
- Click + Create Smart Rule.
- Configure the Smart Rule as follows:
- Category: Select Managed Accounts.
- Name: Provide a meaningful name that allows for easy identification of the Smart Rule.
- Selection Criteria:
- Select Directory Query from the dropdown.
- Leave Include accounts from Directory Query selected.
- Select the directory query created in above steps.
- Leave Discover accounts for Password Safe Management enabled.
- Select the Domain from the dropdown.
- Actions:
- Select Manage Account Settings from the dropdown and set its related options as desired.
- Add another action and select Show managed account as Smart Group from the dropdown.
- Add another action and select Link domain accounts to Managed Systems from the dropdown, and then select your desired Asset or Managed System Smart Group from the dropdown.
- Click Create Smart Rule.
- To view the contents of a Smart Rule when creating a new rule or editing an existing rule:
- Once the rule is saved, click View Results.
- You are taken to the associated grid, where the contents of the Smart Rule are listed.
- If the rule is actively processing, a banner displays letting you know that.
- View Results displays only if you have permissions to the grid corresponding to the Smart Rule, i.e.; Assets, Managed Accounts, Managed Systems.
- The Smart Rule must be saved with Show <entity> as Smart Group selected under Actions to view the results.
- Because the Smart Rule must process to display the contents in the grid, we recommend viewing the results using only the Show <entity> as Smart Group action and before adding additional actions that may make changes to accounts and assets in your network. Once you have confirmed the rule contains your desired items, you can then add additional actions to the Smart Rule.
Create the Smart Rule to map the dedicated account to the user group
- From the left menu, click
 .
.
The Smart Rules page displays. - Select Managed Account from the Smart Rule type filter dropdown.
- Click + Create Smart Rule.
- Configure the Smart Rule as follows:
- Category: Select Managed Accounts.
- Name: Provide a meaningful name that allows for easy identification of the Smart Rule.
- Selection Criteria:
- Select Dedicated Account from the dropdown.
- Select Directory Attribute Match from the dropdown.
- Select the directory attribute you wish to match.
- Actions:
- Select Show managed account as Smart Group from the dropdown.
- Add another action and select Map Dedicated Accounts to from the dropdown.
- Select the applicable User Group to map to.
- Click Create Smart Rule.
- To view the contents of a Smart Rule when creating a new rule or editing an existing rule:
- Once the rule is saved, click View Results.
- You are taken to the associated grid, where the contents of the Smart Rule are listed.
- If the rule is actively processing, a banner displays letting you know that.
- View Results displays only if you have permissions to the grid corresponding to the Smart Rule, i.e.; Assets, Managed Accounts, Managed Systems.
- The Smart Rule must be saved with Show <entity> as Smart Group selected under Actions to view the results.
- Because the Smart Rule must process to display the contents in the grid, we recommend viewing the results using only the Show <entity> as Smart Group action and before adding additional actions that may make changes to accounts and assets in your network. Once you have confirmed the rule contains your desired items, you can then add additional actions to the Smart Rule.
Assign user group permissions to the Smart Rules
- From the left menu, click
 .
.
The Configuration page displays. - Under Role Based Access, click User Management.
The User Management page displays. - Select the Groups tab.
- Locate the user group in the grid
- Click
 > View Group Details.
> View Group Details. - In the Group Details pane, click Smart Groups.
- In the Smart Group Permissions pane, select the two dedicated account smart groups you created.
- Click Assign Permissions above the grid.
- Select Assign Permissions Read Only.
From the Smart Rules page, process the two newly created smart groups. After processing, the dedicated account discovered by the directory query is listed on the Managed Accounts page. Users belonging to the group you chose to map the dedicated account to are indicated in the Mapped to User column. You might need to add this column to the grid using the Column Chooser button above the grid.
Use an Entra ID Smart Rule
An Entra ID Smart Rule enables Password Safe to automatically discover Entra ID accounts. This allows privileged accounts in Entra ID to be managed, including password rotation and check-in and check-out.
Follow the steps below to discover Entra ID accounts.
- From the left menu, click
 .
.
The Smart Rules page displays. - Select Managed Account from the Smart Rule type filter dropdown.
- Click + Create Smart Rule.
- From the Smart Rule Type filter dropdown, select Managed Account.
- Click Create Smart Rule.
- From the Category dropdown, select Managed Accounts.
- Enter a Name and Description.
- From the Category dropdown, select Managed Accounts.
- Enter a Name and Description.
- Set Selection Criteria as:
- Microsoft Entra ID Query:
- There are two matching options available for discovering Entra ID accounts: Group Name and User Principle Name. Use a Group Name match to discover all accounts that are a member of the specified group. Use a User Principle Name match to allow a partial name match.
- If using a Group Name, equals is the only match option. Enter the Group Name.
- If using a User Principle Name, select starts with or ends with and enter the name.
- Set the value for how many hours for rerunning the query.
- Discover accounts in Microsoft Entra ID synced from on-premise - includes Entra ID accounts synced from on-premises Entra ID, as well as Azure-only accounts.
- Leave Discover accounts for Password Safe Management checked.
- Select an Entra ID domain from the dropdown.
- Add additional selection criteria and groups, as required.
- Microsoft Entra ID Query:
- Set Actions as:
- Show managed account as Smart Group.
- Add other actions as required to manage settings or work with the managed account.
- Click Create Smart Rule.
- To view the contents of a Smart Rule when creating a new rule or editing an existing rule:
- Once the rule is saved, click View Results.
- You are taken to the associated grid, where the contents of the Smart Rule are listed.
- If the rule is actively processing, a banner displays letting you know that.
- View Results displays only if you have permissions to the grid corresponding to the Smart Rule, i.e.; Assets, Managed Accounts, Managed Systems.
- The Smart Rule must be saved with Show <entity> as Smart Group selected under Actions to view the results.
- Because the Smart Rule must process to display the contents in the grid, we recommend viewing the results using only the Show <entity> as Smart Group action and before adding additional actions that may make changes to accounts and assets in your network. Once you have confirmed the rule contains your desired items, you can then add additional actions to the Smart Rule.
Use Quick Groups
For a simpler way to organize managed accounts, you can group them using a Quick Group. The default processing time on a Quick Group is Once.
- From the left menu, click
 .
.
The Managed Accounts page displays. - From the Smart Group filter dropdown, select an existing smart group in which the managed accounts are members.
- Check the boxes for the managed accounts that you want to add to the Quick Group.
- Click Add to Smart Group above the grid.
- Select a group from the Smart Group dropdown or create a new one by typing in the name and clicking Add as New Option.
- Select Quick Groups from the Category dropdown.
- Leave the default description or enter a new one.
- Click Add Selected Accounts To Smart Group.
- Your new smart group is now available in the Smart Group filter dropdown.
Remove accounts from a Quick Group
- From the left menu, click
 .
.
The Managed Accounts page displays. - From the Smart Group filter dropdown, select an existing smart group in which the managed accounts are members.
- Check the boxes for the managed accounts that you want to remove from the Quick Group.
- Click Remove From Smart Group above the grid.
Edit a Managed System Quick Group
- From the left menu, click
 .
.
The Managed Systems page displays. - Select Managed System from the Smart Rule type filter.
- Locate the Quick Group in the grid.
- Click
 > Edit Smart Rule.
> Edit Smart Rule. - Make your changes, and then click Save Changes.
Deactivate a Managed System Quick Group
- From the left menu, click
 .
.
The Managed Systems page displays. - Select Managed System from the Smart Rule type filter.
- Locate and select the Quick Group in the grid.
- Click Deactivate above the grid.
You cannot add or modify filters or actions for Quick Groups.
Manually add managed systems to Smart Groups
Managed systems do not have a Quick Group category; however, the concept and process is essentially the same as it is for managed accounts.
- From the left menu, click
 .
.
The Managed Systems page displays. - From the Smart Group filter dropdown, select an existing Smart Group in which the managed systems are members.
- Check the boxes for the managed systems that you want to add to the Quick Group.
- Click Add to Smart Group above the grid.
- Select a group from the Smart Group dropdown or create a new one by typing in the name and clicking Add as New Option.
- Select a Category from the dropdown.
- Leave the default description or enter a new one.
- Click Add Selected Systems To Smart Group.
- Your new smart group is now available in the Smart Group filter dropdown.
Remove a managed system from a Smart Group
- From the left menu, click
 .
.
The Managed Systems page displays. - Select the Smart Group from the Smart Group filter.
- Check the boxes for the managed systems that you want to remove from the group.
- Click
 above the grid.
above the grid.
Edit Smart Rules
-
From the left menu, click
 .
.
The Smart Rules page displays. -
Locate the smart rule in the grid.
-
Click
 > Edit Smart Rule.
> Edit Smart Rule. -
Make the necessary changes.
-
Click Save Changes.
- To view the contents of a Smart Rule when creating a new rule or editing an existing rule:
- Once the rule is saved, click View Results.
- You are taken to the associated grid, where the contents of the Smart Rule are listed.
- If the rule is actively processing, a banner displays letting you know that.
- View Results displays only if you have permissions to the grid corresponding to the Smart Rule, i.e.; Assets, Managed Accounts, Managed Systems.
- The Smart Rule must be saved with Show <entity> as Smart Group selected under Actions to view the results.
- Because the Smart Rule must process to display the contents in the grid, we recommend viewing the results using only the Show <entity> as Smart Group action and before adding additional actions that may make changes to accounts and assets in your network. Once you have confirmed the rule contains your desired items, you can then add additional actions to the Smart Rule.
Delete Smart Rules
-
From the left menu, click
 .
.
The Smart Rules page displays. -
Locate and select the smart rule in the grid.
-
Click
 above the grid.
above the grid.
- Built in Smart Rules cannot be deleted. These are identified by the Lock icon.
- A Smart Rule that is used in another Smart Rule cannot be deleted or marked as inactive.
Audit Smart Rules
To audit new or edited Smart Rules:
- From the left menu, click
 .
.
The Configuration page displays. - Under General, click User Audits.
The User Management page displays. - Select Section from the Filter by dropdown.
- Select Smart Rule from the Section dropdown.
- Click
 to the right of the Smart Rule.
to the right of the Smart Rule.
- If a Smart Rule is added, the Add Details pane displays with all added information.
- If a Smart Rule is edited, the Edit Details pane displays with all edited information.
Updated 28 days ago

