Additional templates | EPM-WM Cloud
In addition to QuickStart templates, there are trusted app protection (TAP) templates and a Discovery template.
Import these templates using the import tool in Utilities.
Trusted App Protection (TAP)
The Trusted App Protection (TAP) policies offer an additional layer of protection against malware for trusted business applications, safeguarding them from exploitation attempts.
- Apply greater protection to key business applications including Microsoft Office, Adobe Reader, and web browsers, which are often exploited by malicious content.
- Prevent these applications from launching unknown payloads and potentially risky applications, such as PowerShell.
- Prevent untrusted DLLs being loaded by these applications, another common malware technique.
In our research, we discovered that malware attack chains commonly seek to drop and launch an executable or abuse a native Windows application such as PowerShell. A TAP policy prevents these attacks and compliments existing anti-malware technologies by preventing an attack from launching without relying on detection or reputation.
The TAP templates are preconfigured with Workstyles, App Groups, and Messages.
- Trusted Application Protection - High Flexibility (depends on the TAP policy you chose)
- Trusted Application Protection - High Security (depends on the TAP policy you chose)
Application Groups
Browsers
- Browsers - Trusted Exploitables
- Browsers - Untrusted child processes
Content Handlers
- Content Handlers - Trusted Exploitables
- Content Handlers - Untrusted child processes
Content Handlers are used to hold content rather than executables.
Messages
- Block Message
TAP policies
There are two TAP policies:
- High Flexibility: Use if your users must download and install or update software. The High Flexibility policy only validates the immediate child processes allowing a wider range of installers to run.
- High Security: Use if your users don't need to download and install or update software. The High Security policy checks that all child processes have either a trusted publisher, a trusted owner, a source URL, or a BeyondTrust Zone Identifier tag.
If child processes don't have any of these four criteria, they are blocked from running.
- Trusted publisher: A trusted publisher must be signed. The publisher certificate must be valid, in date, and not revoked.
- Trusted owner: A trusted owner is any owner that is in the default Windows groups Administrators, SystemUser, or TrustedInstaller.
- SourceURL: The source URL must be present. This is specific to browsers.
- BeyondTrust Zone Identifier tag: The BeyondTrust Zone Identifier tag must be present. This is applied when the browser applies an Alternate Data Stream (ADS) tag. This is specific to browsers.
Additionally,
- All processes on the block list are blocked irrespective of their publisher and owner.
- Known exploits are blocked by both TAP policies.
- TAP applications and their child processes must match all the criteria within the definitions provided in the Application Groups of the policy for the TAP policy to apply.
- Installers that spawn additional child processes are blocked by the TAP (High Security) policy if those child processes are using applications on the TAP block list, but would be allowed to run using the TAP (High Flexibility) policy.
Trusted apps
- Microsoft Word
- Microsoft Excel
- Microsoft PowerPoint
- Microsoft Publisher
- Adobe Reader 11 and lower
- Adobe Reader DC
- Microsoft Outlook
- Google Chrome
- Mozilla Firefox
- Microsoft Internet Explorer
- Microsoft Edge (Legacy and Chromium versions)
Precedence
After you import a TAP template:
- The Workstyle runs best as a priority rule and is placed first in the Workstyles list. The TAP Workstyle is the first to be evaluated by default. Once a Workstyle action is triggered, subsequent Workstyles aren't evaluated for that process.
- Running first ensures child processes of TAP applications (policy dependent) that do not have a trusted publisher, trusted owner, a source URL, or a BeyondTrust Zone Identifier tag are blocked from execution and that known exploits are blocked.
Modify a TAP policy
Use the approaches in this section (in either TAP policy) to modify the policy to address a legitimate use case being blocked by a TAP policy.
The TAP (High Security) policy is, by design, more secure and less flexible, as it blocks all child processes of a Trusted Application that do not have a trusted owner, trusted publisher, source URL, or BeyondTrust Zone Identifier. It is for these reasons more likely to require modification.
Change the policy to audit
You can change the TAP (High Security) policy Application Rules Action to Allow Execution and change the Access Token to Enforce User's Default Rights. Ensure Raise an Event is set to On and click OK.
Changing the TAP policy to Allow Execution effectively disables it. You do not get any protection from a TAP policy if you make this change.
If you make this change for the four Application Rules in the TAP (High Security) policy, TAP programs can execute as if the TAP (High Security) policy wasn't applied, but you can see what events are being triggered by TAP and make policy adjustments accordingly.
The event details include information on the Application Group and TAP application. This allows you to gather details to understand if it's a legitimate use case. You can perform some actions to incorporate the legitimate use case into the TAP (High Security) policy.
Use the high flexibility policy
If you are using the TAP (High Security) policy you can change to the TAP (High Flexibility) policy. This is useful if you have a use case where additional child processes of TAP applications are being blocked by the TAP (High Security) policy.
Edit the matching criteria
If your legitimate use case is running a specific command that is detailed in the event, you can add this to the matching criteria of the application that's being blocked. You can use the standard Endpoint Privilege Management for Windows matching criteria, such as Exact Match or Regular Expressions.
ExampleWebEx uses an extension from Google Chrome. We have catered for this in the policy using matching criteria.
This criteria says:
If the Parent Process matches the (TAP) High Security - Browsers Application Group for any parent in the tree.
and
The Product Description contains the string Windows Command Processor
and
The Command Line does NOT contain \.\pipe\chrome.nativeMessagingThe TAP policy (High Security) blocks the process.
Edit the Trusted Exploitable list
If your legitimate use case is using an application listed in either the Browsers - Trusted Exploitables or the Content Handlers - Trusted Exploitables list, you can remove it.
If you remove the app from either list, any browsers or content using that trusted exploitable to run malicious content are not stopped by the TAP (High Security) policy.
Remove application from Trusted Application Group
You can remove the application listed in the Trusted Browsers or Trusted Content Handlers groups.
If removed, the application is no longer protected either TAP policy.
Create an Allow rule
You can add an Endpoint Privilege Management for Windows Allow rule and place it higher in the precedence order than the TAP (High Security) policy.
Use an Allow rule with caution in this scenario. Your use case can run but the rule overrides any subsequent rules that apply to that application.
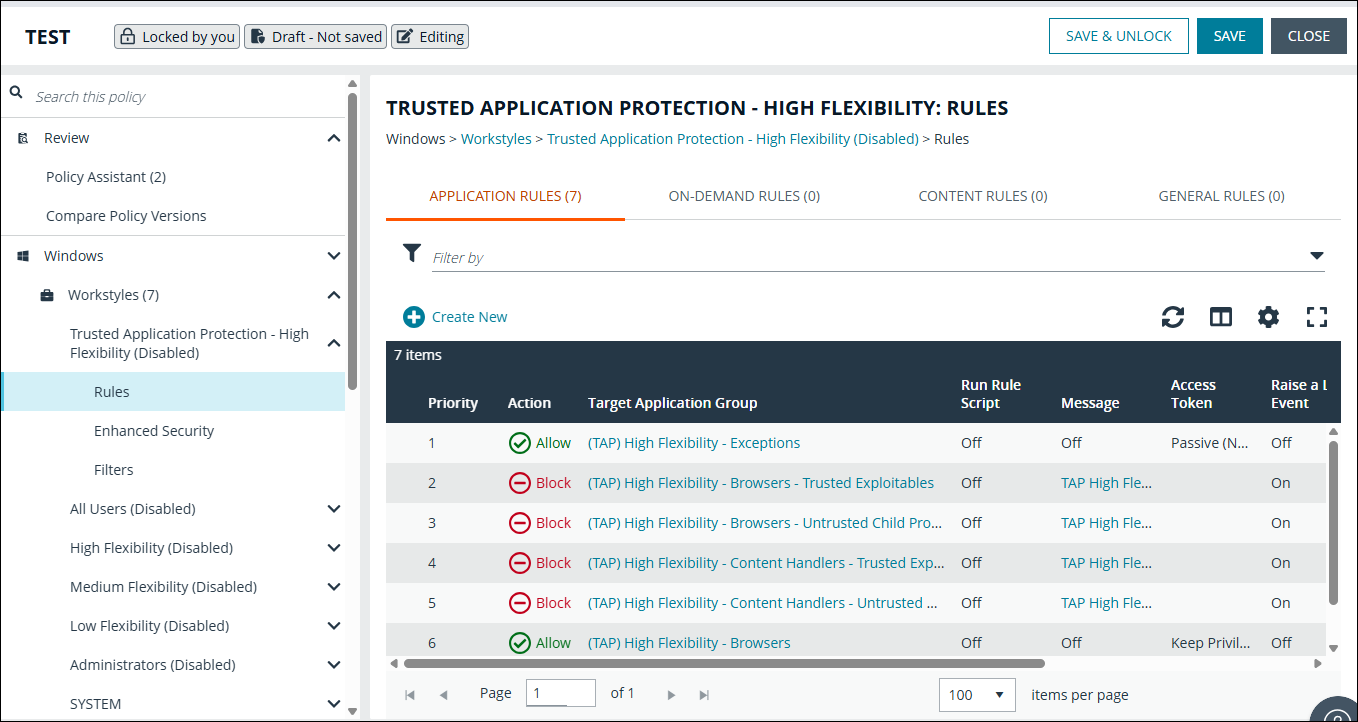
TAP block list
To view the list of applications blocked from being launched by trusted applications when TAP is enabled:
- After TAP High Flexibility or High Security is imported, expand the workstyle and select Rules.
- Select Application Rules.
- The list of applications (allowed and blocked) displays:
- (TAP) High Security - Browsers - Trusted Exploitables
- (TAP) High Security - Content Handlers - Trusted Exploitables
- (TAP) High Flexibility - Browsers - Trusted Exploitables
- (TAP) High Flexibility - Content Handlers - Trusted Exploitables
Use advanced parent tracking
With version 21.3 of EPM-W, advanced parent tracking (APT) tracks parent processes and increases the effectiveness of TAP policies while also reducing false positives from Windows PID re-use.
When processing rules, EPM-W attempts to determine the parent of a process through APT first. Following that, EPM-W uses other rule properties (like child inheritance) to rely on the information provided by Windows.
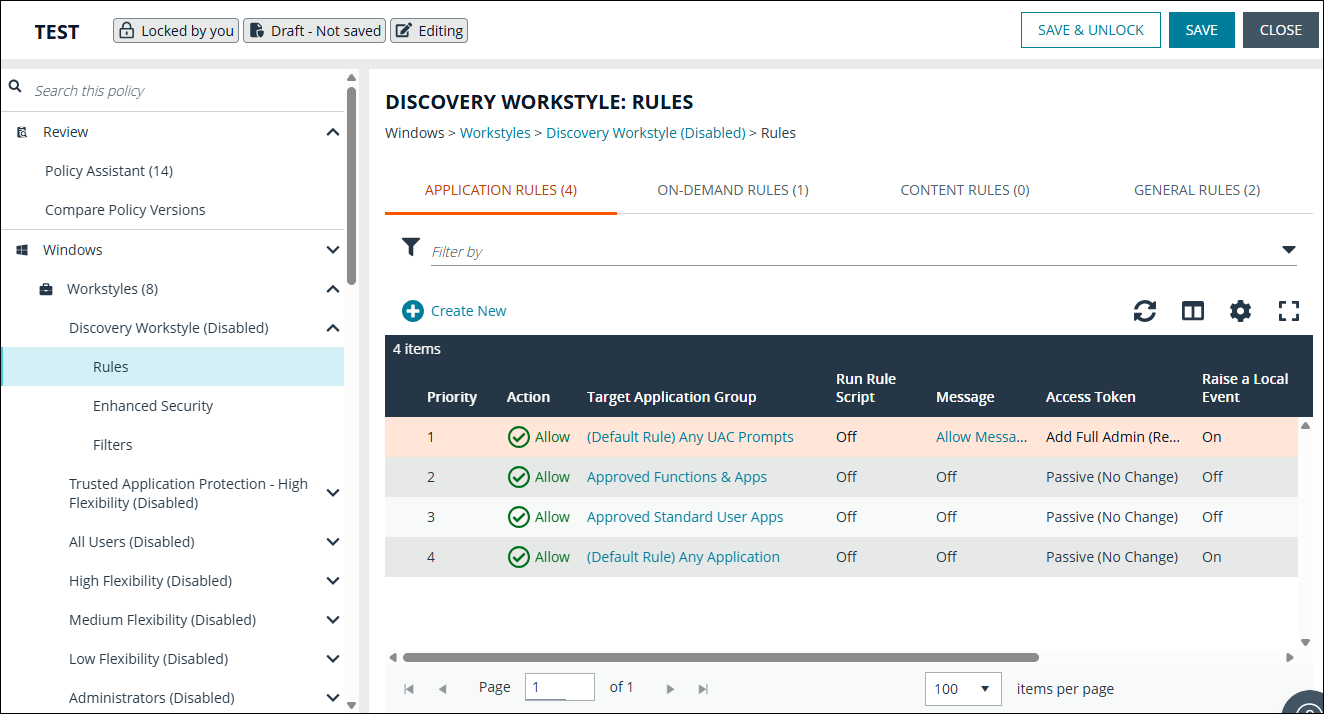
Discovery
The Discovery policy contains Workstyles, Application Groups, and messages to allow the discovery of applications that need administrative privileges to execute. This must be applied to administrator users and includes a preconfigured exclusion group (false positives) maintained by BeyondTrust.
This template policy contains the following configurations:
Workstyles
Discovery Workstyle
Application groups
- (Default Rule) Any Application
- (Default Rule) Any UAC Prompts
- Approved Standard User Apps
- Passive - All Users & Apps
Messages
Allow Message (Yes / No)
Updated 11 days ago
