Custom tokens | EPM-WM Cloud
A token is assigned to an application to change the privileges associated with the activity permitted for that application. Create a custom token to manually configure group membership, privileges, and process access rights.
Custom tokens can be used with on-demand rules, application rules, and content rules. By design, custom tokens only work for allow rules.
Changing the properties of an access token is designed for more advanced configurations.
Here are some scenarios on customizing the properties of a token:
- Run remote PowerShell commands and scripts with a custom token that removes the SeRemoteShutDown privilege. This prevents the commands and scripts from shutting down servers during core business hours, even if the command or script indicates to do so.
- Create a custom token to run an application with custom privileges configured in the token. The user can run the application but with modified privileges as configured in the token.
Create a custom token
You can select from a list of Windows access tokens as the foundation to creating the custom token. After selecting the token, customize the following properties: group, privileges, and process access rights.
- Groups: Add local or Active Directory domain groups to the token.
- Privileges: Add or remove privileges that will be applied to the application.
- Process access rights: The process access rights allow you to choose the rights other processes have over a process launched with that custom token.
Create a token
To create a token:
- Navigate to the policy and expand Windows.
- Select Custom Tokens.
- Click Create New Custom Token.
- Enter a name and description.
- Select the level of permissions for the token:
- Add Full Admin (Required for installers): Preselected Windows administrator privileges.
- Drop Admin Rights: Preselected Windows privileges that do not include administrator privileges.
- Blank: Select this option to personalize the privileges for the token.
- Click Create Token.
- On the main Custom Tokens page, select the token and click Edit from the menu.
- See the following sections for more details on the properties to configure.
Set integrity level and anti-tamper
Follow these instructions to fine-tune your token settings for optimal application performance and security:
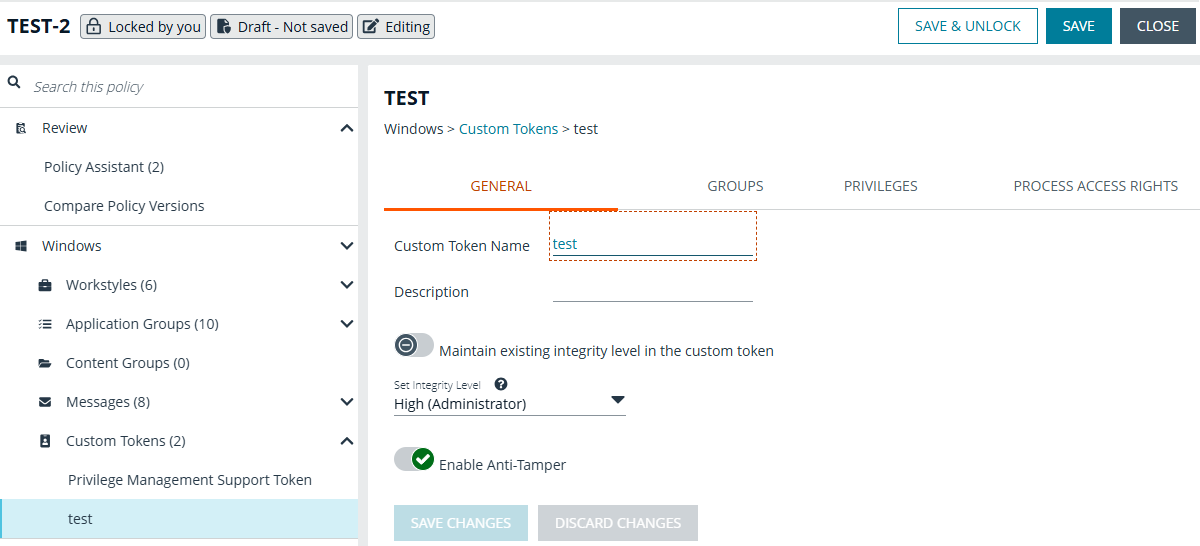
- Click the General tab.
-
Select an integrity level or select Maintain existing integrity level in the custom token to use the existing Windows integrity level for the selected token type.
- System: Included for completion and is not required.
- High: Set the integrity level associated with an administrator.
- Medium: Set the integrity level associated with a standard user.
- Low: Set the integrity level associated with protected mode (an application might fail to run or function in protected mode)
- Untrusted: Included for completion and is not required.
-
By default, anti-tamper protection is on. Anti-tamper protection prevents elevated processes from tampering with the files, registry, and service that make up the client installation. It also prevents any elevated process from reading or writing to the local policy cache.
Keep anti-tamper enabled, except in scenarios where elevated tasks require access to protected areas, such as when using an elevated logon script to update the local policy.
-
Click Save Changes.
Add group to custom token
There are two ways to add groups:
- Add local Active Directory domain groups
- Set up a connector that populates group information from your local Active Directory domains or your Microsoft Entra ID instance.
-
If you want the user to be the owner, regardless of the presence of the administrators group, select Ensure User is always the Token Owner.
By default, the owner of a custom token that includes the administrators group has the owner set to the administrators group. If the administrators group is not present in the custom token, then the user is set as the owner.
-
Select one of the following:
- Add Account: Add an account name and SID details. Click Add Account.
- Add Account from Search: Select a connector on the Add From AD Connectors page. The default connector is Built-In. Enter search criteria in the Account Name box to find a specific account. Select the account name, and then select Add.
If searching Microsoft Entra ID, a minimum of two characters is required to initiate the search. Use the search options, Contains or Starts with to narrow the scope of the search results.
Select privileges for custom token
On the Privileges tab, select the privileges to add to or remove from the custom token.
- Select a privilege, and then select
- Add Privilege to add the privilege to the custom token.
- Remove Privilege to remove the privilege to the custom token.
- To reset the default state of a privilege, select the privilege and select No Change.
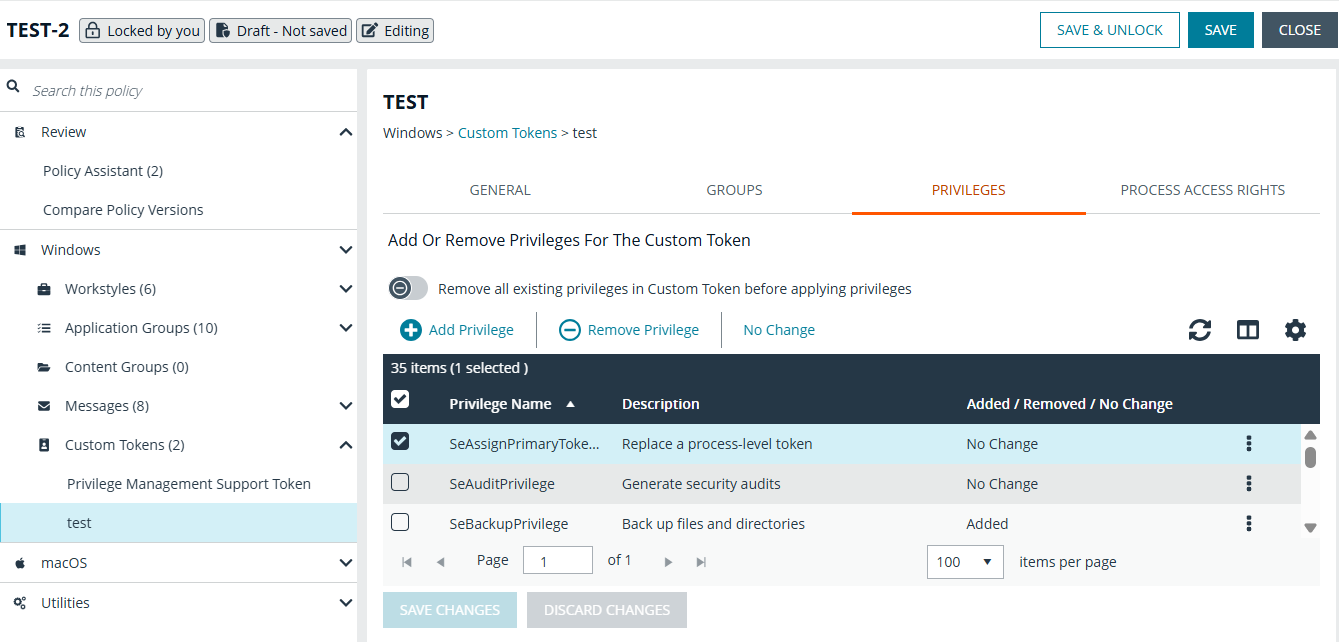
- Click Remove all existing privileges in Custom Token before applying privileges to clear all privileges in the custom token before applying privileges. If not selected, the privileges are added or removed from the user’s default custom token.
Enable process access rights
On the Process Access Rights tab, select the rights other processes have over a process launched with that Custom Token.
Tokens that include the administrators group have a secure set of access rights applied by default, which prevents code injection attacks on elevated processes initiated by processes running with standard user rights in the same session.
- Select a process access right, and then select
- Enable to enable the process access right on the custom token.
- Disable to disable the process access right on the custom token.
- Click Save Changes.
Access rights
| Access Rights | Description |
|---|---|
| GENERIC_HEAD | Read access. |
| PROCESS_CREATE_PROCESS | Required to create a process. |
| PROCESS_CREATE_THREAD | Required to create a thread. |
| PROCESS_DUP_HANDLE | Required to duplicate a handle using DuplicateHandle. |
| PROCESS_QUERY_INFORMATION | Required to retrieve certain information about a process, such as its token, exit code, and priority class. |
| PROCESS_QUERY_LIMITED_INFORMATION | Required to retrieve certain information about a process. |
| PROCESS_SET_INFORMATION | Required to set certain information about a process, such as its priority class. |
| PROCESS_SET_QUOTA | Required to set memory limits using SetProcessWorkingSetSize. |
| PROCESS_SUSPEND_RESUME | Required to suspend or resume a process. |
| PROCESS_TERMINATE | Required to terminate a process using TerminateProcess. |
| PROCESS_VM_OPERATION | Required to perform an operation on the address space of a process. |
| PROCESS_VM_READ | Required to read memory in a process using ReadProcessMemory. |
| PROCESS_VM_WRITE | Required to write to memory in a process using WriteProcessMemory. |
| READ_CONTROL | Required to read information in the security descriptor for the object, not including the information in the SACL. |
| SYNCHRONIZE | Required to wait for the process to terminate using the wait functions. |
Updated 26 days ago
