Webhook settings | EPM-WM Cloud
Create a webhook to integrate a third-party ITSM provider to manage JIT application access requests.
EPM-WM can integrate with any third-party ITSM platform capable of receiving incoming webhooks.
Check out our BeyondTrust BeeKeepers Community for custom webhook documentation for these platforms:
Microsoft Teams, SendGrid, Slack, ServiceNow, JiraCloud Issue Management, Zendesk
Webhook events are captured in activity auditing.
A standard user requires delegated access to this feature. For more information, see User management.
Create a webhook
-
Select Configuration > Webhook Settings.
The Webhook Settings page displays with the available webhooks.
-
Click Create Webhook.
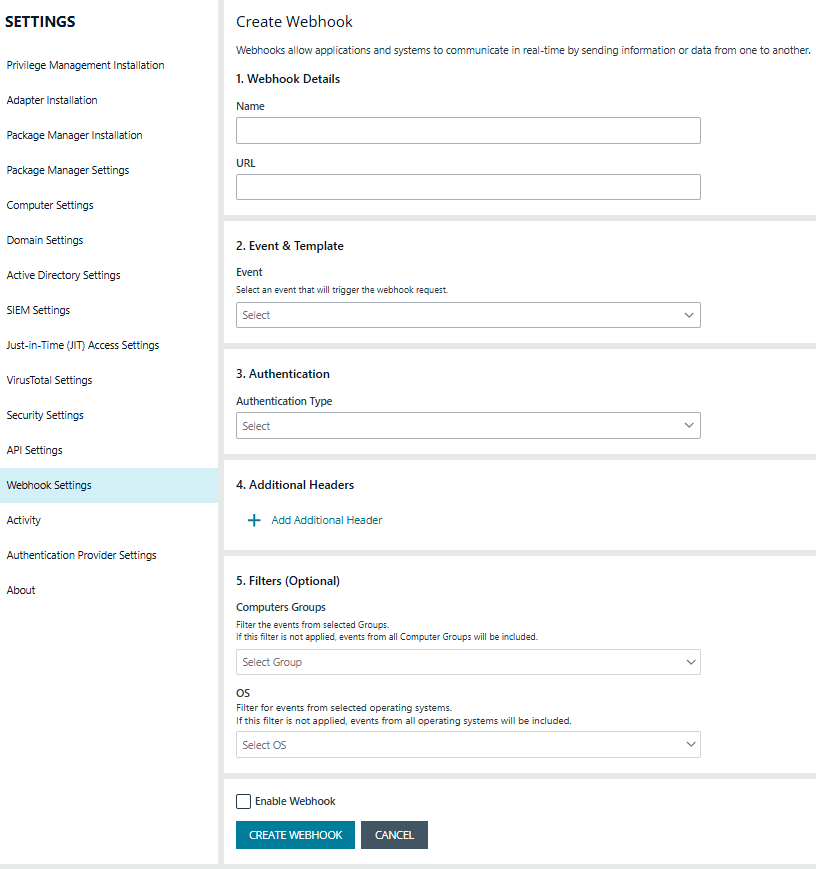
- Provide the following information:
- Name: Enter a name for this webhook.
- URL: Add a name and enter the URL to the ITSM tool.
- Event: The event configured for the webhook:
- JIT Application Access Ticket Created
- JIT Application Access Decision Updated
- Content Type: The content type for the template. For example, application/json.
- Add Template: Templates are used to customize the request body for a webhook and include the events to send to your ITSM platform.
Example template
The formatting of each JSON object is unique to each ITSM platform. For more information, see the documentation for your ITSM platform.
{
"EventType": "%%EventType%%",
"RequestId": "%%RequestId%%",
"TenantId": "%%TenantId%%",
"Timestamp": "%%Timestamp%%",
"requestInfo": {
"applicationType": "%%ApplicationType%%",
"action": "%%Action%%",
"workstyle": "%%Workstyle%%",
"reason": "%%Reason%%",
"user": "%%User%%",
"hostName": "%%HostName%%",
"trustedOwnership": "%%trustedOwnership%%",
"productDescription": "%%ProductDescription%%",
"driveType": "%%DriveType%%",
"btZoneIdentifierExists": "%%BtZoneIdentifierExists%%",
"productCode": "%%ProductCode%%",
"upgradeCode": "%%UpgradeCode%%",
"clsId": "%%ClsId%%",
"comDisplayName": "%%ComDisplayName%%",
"token": "%%Token%%",
"tokenAssignmentIsShell": "%%TokenAssignmentIsShell%%",
"uacTriggered": "%%UacTriggered%%",
"downloadSourceUrl": "%%DownloadSourceUrl%%",
"userLanguage": "%%UserLanguage%%",
"sha1Hash": "%%Sha1Hash%%",
"sha256Hash": "%%Sha256Hash%%",
"filePathObjectId": "%%FilePathObjectId%%",
"cmdArgs": "%%CmdArgs%%",
"publisher": "%%Publisher%%",
"productName": "%%ProductName%%",
"productVersion": "%%ProductVersion%%",
"fileVersion": "%%FileVersion%%",
"workstyle": "%%Workstyle%%",
"applicationGroup": "%%ApplicationGroup%%",
"message": "%%Message%%",
"messageId": "%%MessageId%%",
"hostType": "%%HostType%%",
"osName": "%%OsName%%",
"osVersion": "%%OsVersion%%",
"ComputerGroup": "%%ComputerGroup%%",
"GroupId": "%%GroupId%%",
"requestVersion": "%%RequestVersion%%",
"hostedFilePath": "%%HostedFilePath%%",
"parentProcess": "%%ParentProcess%%",
"storeAppName": "%%StoreAppName%%",
"serviceName": "%%ServiceName%%",
"serviceAction": "%%ServiceAction%%",
"authRequestUri": "%%AuthRequestUri%%",
"bundleInfoDescription": "%%BundleInfoDescription%%",
"reputationScoreDateTime": "%%ReputationScoreDateTime%%",
"reputationScore": "%%ReputationScore%%",
"reputationIntegrationType": "%%ReputationIntegrationType%%"
}
}- Authentication Type: The type of authentication used by the webhook:
None
Basic
Custom
OAuth – Client Credentials
* OAuth – Password - Additional headers:
- Name: The name of the additional header for the webhook request.
- Value: The key-value for the additional header. - Filters
- Computers Groups: Select a computer group from the list. If no filter is selected, all groups are included.
- OS: Select an OS from the group. If no OS is selected, all events are included.
- Select Enable Webhook to automatically enable the webhook after it is created.
- Select Save Webhook.
Webhook variables
Add variables to the JSON object in the webhook template. The variables provide additional information or context around the incident. The available variables depend on the type of event and are listed here.
JIT Application Access Ticket Created
| Variable | Description |
|---|---|
| Action | The action requested (macOS) applications only. RUN, SUDO, INSTALL or DELETE |
| ApplicationGroup | Name of the Application Group matched in policy. |
| ApplicationType | Application Type of the matched application. |
| AuthRequestUri | macOS application property: authorization right which the app is requesting or requires to run. |
| BtZoneIdentifierExists | Whether the matched file has a zone identifier indicating it was downloaded from the web. (True/False) |
| BundleInfoDescription | macOS application property: description of the app bundle. |
| ClsID | COM Class Identifier. |
| CmdArgs | Command line arguments passed when a process was launched. |
| ComDisplayName | COM Class Display Name. |
| ComputerGroup | Organizes computers that will be assigned the same policy. |
| DownloadSourceUrl | Source URL of the matched file, if downloaded. |
| DriveType | Drive type on which the matched file was stored. |
| Epmid | The Integer EPM JIT Application ID, can be used to access application details using EPM portal. |
| EventType | URM_Native_Ticket_Created |
| FilePathObjectId | The path to the matched file, or the object ID of COM Class. |
| FileVersion | File version property of the matched file. |
| GroupId | Computer Group unique internal system ID. |
| HostedFilePath | Windows process event property: path to the file loaded when launching a process. |
| Hostname | Agent Host Name stored in EPM. |
| HostType | Agent Host Type stored in PMC (for example. Windows, macOS) |
| Message | Name of the message shown by the matched rule in policy. |
| MessageId | ID of the message shown by the matched rule in policy. |
| OsName | Agent operating system name stored in EPM. |
| OsVersion | Agent operating system version stored in EPM. |
| ParentProcess | Windows process event property: path to the parent process of a launched process. |
| ProductCode | Product code GUID of .msi file. |
| ProductDescription | Product description property of the matched file. |
| ProductName | Product name property of the matched file. |
| ProductVersion | Product version property of the matched file. |
| Publisher | Publisher name property of the matched file. |
| Reason | Reason for request from the EPM end user. |
| ReputationIntegrationType | Type of reputation score integration. |
| ReputationScore | Reputation score at the time ticket was created. |
| ReputationScoreDateTime | Date and time the reputation score was captured. |
| RequestId | JIT Application Access request unique internal system ID. Required field to further communicate with EPM. |
| ServiceAction | Windows service event property: action performed on the service (for example, start, stop, pause, configure). |
| ServiceName | Name of the service where the request is triggered. |
| Sha1Hash | SHA1 hash of the matched file. |
| Sha256Hash | SHA256 hash of the matched file. |
| StoreAppName | Windows process event property: name of the store app launched. |
| TenantId | EPM Tenant ID. |
| TicketNumber | For example, EPM000001 |
| Timestamp | Date and time the ticket event was created, in UTC (for example, yyyyMMddTHHmmssZ). |
| Token | Name of the token to be applied by the matched rule in policy. |
| TokenAssignmentIsShell | Whether the rule matched was an On Demand rule. (True/False) |
| TrustedOwnership | Whether the matched file is located in a trusted location. (True/False) |
| UacTriggered | Whether Windows UAC was required to run or open the matched file. (True/False) |
| UpgradeCode | Upgraded code GUID of .msi file. |
| User | EPM end user |
| UserLanguage | EPM user’s language locale |
| Workstyle | Name of the Workstyle matched in policy |
JIT Application Access Ticket Updated
| Variable | Description |
|---|---|
| EventType | URM_NATIVE_DECISION_UPDATE |
| RequestId | JIT Application Access unique request internal system ID. Required field to further communicate with EPM. |
| TenantId | EPM Tenant ID. |
| TicketNumber | For example, EPM000001. |
| Timestamp | Date and time the decision event was created, in UTC (for example, yyyyMMddTHHmmssZ). |
| Decision | Approved or Denied. |
| DecisionTime | Date and time when a decision is made, in UTC (for example, yyyyMMddTHHmmssZ). |
| DecisionPerformedByUser | Name of the decision maker. |
| Duration | Number of seconds. |
JIT Admin Ticket Created
| Variable | Description |
|---|---|
| EventType | JIT_ADMIN_TICKET_CREATED |
| RequestId | JIT admin request internal system ID. Required field to further communicate with EPM. |
| TicketNumber | For example, EPM000001. |
| TenantId | EPM Tenant ID. |
| ComputerId | ID of the computer. |
| GroupId | ID of the computer group. |
| Reason | Message from end point user for escalation. |
| UserId | Endpoint user ID. |
| UserName | User name of endpoint. |
| DurationRequested | Duration request by endpoint user. |
| Timestamp | Datetime decision event created in UTC (for example, yyyyMMddTHHmmssZ). |
JIT Admin decision updated
| Variable | Description |
|---|---|
| EventType | JIT_ADMIN_TICKET_CREATED |
| RequestId | JIT admin request internal system ID. Required field to further communicate with EPM. |
| TicketNumber | For example, EPM000001. |
| TenantId | EPM Tenant ID. |
| StartTime | Start time of the admin access in UTC (for example, yyyyMMddTHHmmssZ). |
| EndTime | End time of the admin access in UTC (for example, yyyyMMddTHHmmssZ). |
| Decision | Approved or Denied. |
| DecisionTime | Datetime when a decision is made in UTC (for example, yyyyMMddTHHmmssZ). |
| DecisionPerformedByUser | Name of the decision maker. |
| Duration | Duration granted by decision maker. |
| DurationRequested | Duration request by endpoint user. |
| Timestamp | Datetime decision event created in UTC (for example, yyyyMMddTHHmmssZ). |
Send sample event
After creating the webhook, send a sample event to the ITSM to confirm the webhook is configured correctly.
- Select Configuration > Webhook Settings.
The Webhook Settings page displays. - Select the webhook in the list, and select
 > Send Sample Event.
> Send Sample Event.
Enable the webhook
When the webhook is ready for production:
- Select Configuration > Webhook Settings.
The Webhook Settings page displays. - Select the webhook, and select
 >Enable Webhook.
>Enable Webhook.
Clear the event queue
Remove all events from the queue.
- Select Configuration > Webhook Settings.
The Webhook Settings page displays. - Select the webhook in the list and select
 >Clear Event Queue.
>Clear Event Queue.
The Queued Events for the webhook drops to 0.
Delete the webhook
Delete a webhook.
- Select Configuration > Webhook Settings.
The Webhook Settings page displays. - Select the webhook in the list and select
 >Delete Webhook.
>Delete Webhook.
Updated 19 days ago
