Policy Editor utilities | EPM-WM Cloud
Licensing
Endpoint Privilege Management for Windows requires a valid license code to be entered in the Policy Editor. If more than one policy is applied to a computer, you need at least one valid license code for one of those policies.
For example, you could add the Endpoint Privilege Management for Windows license to a policy that is applied to all managed endpoints, even if it does not have any Workstyles. This ensures all endpoints receive a valid license if they have Endpoint Privilege Management for Windows installed. If you are unsure, then we recommend you add a valid license when you create the policy.
- Go to the Policies page, and then select Edit & Lock Policy for the policy you want to edit.
- Expand the Utilities node.
- Click the Licenses node.
- Click Add.
- Enter the license key, and then click Add License.
Identity provider settings
- In the Policy Editor, expand Utilities.
- Click Identity Provider Settings.
- On the Identity Provider Settings panel, select an identity provider from the list: OIDC or RADIUS.
- Enter the following details for the identity provider:
- OIDC Settings
- Authority URI: The address of your identity provider.
- Client ID: Must match the same value configured for your identity provider's BeyondTrust application.
- Redirect URI: Must match the same value configured for your identity provider's BeyondTrust application. The format is http://127.0.0.1:port_number, where port_number is an open port on your network. The port_number is only needed if required by your identity provider.
- Proxy URI: (Windows only) Add a proxy server if you route your OIDC authentication through a proxy server.
- RADIUS Settings
- Authentication Mechanism: The authentication type that is required by your RADIUS server. Supported authentication mechanisms are MS-CHAPV2 or PAP.
- Host: The hostname of your RADIUS server.
- Port: The port number for connecting to your RADIUS server.
- Shared Secret: The secret key required by your RADIUS server.
- OIDC Settings
- Click Save RADIUS Settings or Save OIDC Settings depending on the type you selected.
After an identity provider is added you can configure any allow message type to use multifactor authentication.
For more information about adding identity providers, see Authentication provider settings.
Identity authentication
The identity authentication feature integrates EPM with Microsoft Entra ID. With this integration, EPM can determine the security groups a user belongs to and filter policies based on those user groups.
In this initial release, identity authentication is available on macOS and will be available on Windows in a future release.
- In the Policy Editor, expand Utilities.
- Click Identity Authentication.
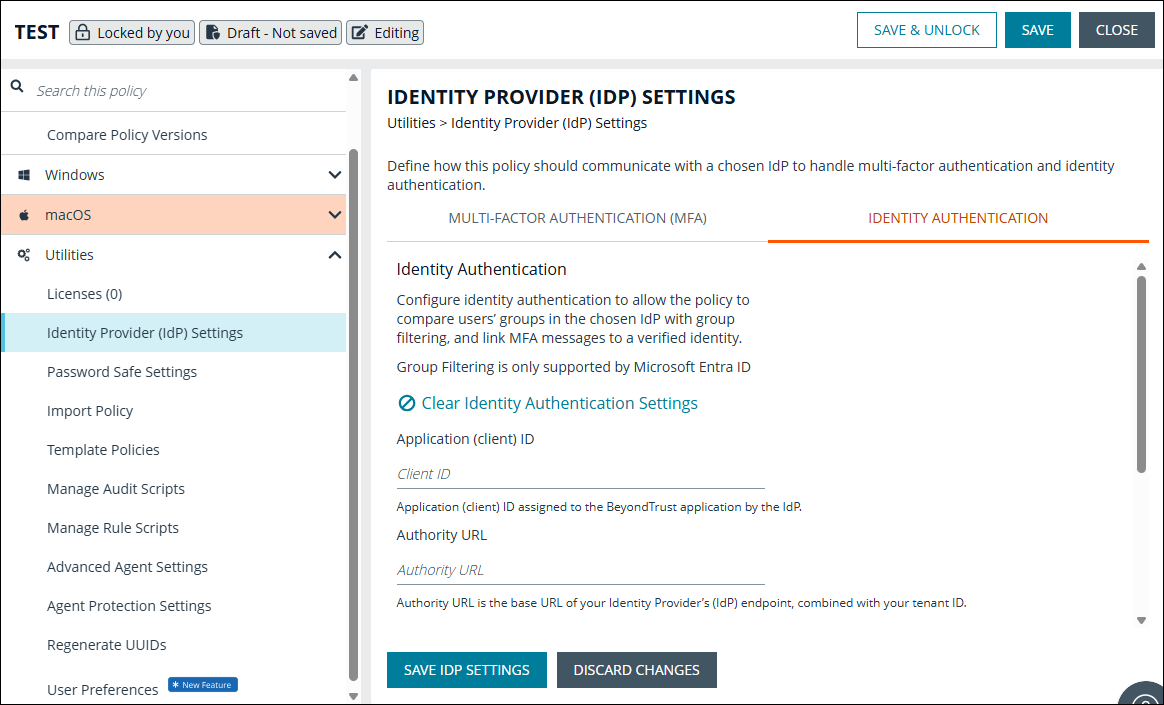
- Add the Application (client) ID. This value is created when you set up your Microsoft Entra ID app registration with EPM.
- Add the Authority URL. For Entra this is https://login.microsoftonline.com/organizations/v2.0/ or <https://login.microsoftonline.com/><Directory (tenant) ID>/v2.0/
Configuration in Microsoft Entra ID
When you register EPM as an app in Microsoft Entra ID, here are some important settings:
- In the Redirect URI section, select Public client/native (mobile and desktop) and enter:
- macOS: com.beyondtrust.pmfm://idp
- In the API Permissions section, add (and grant admin consent for) the following Graph API permissions as delegated scopes:
- User.Read
- profile
- openid
- GroupMember.Read.All
- Add a group claim, and be sure to select Groups assigned to the application and select Group ID.
- Configure groups in Entra ID. Go to your EPM app in Enterprise Apps in Entra ID and navigate to Users and groups. Add your EPM user groups used in the policy. Groups will be sent to EPM when users try to verify their identities.
Import policy
Endpoint Privilege Management policies can be imported to and exported from Group Policy as XML files, in a format common to other editions of Endpoint Privilege Management, such as the Endpoint Privilege Management ePO Extension. Policies can be migrated and shared between different deployment mechanisms.
- In the Policy Editor, expand Utilities.
- Select Import Policy.
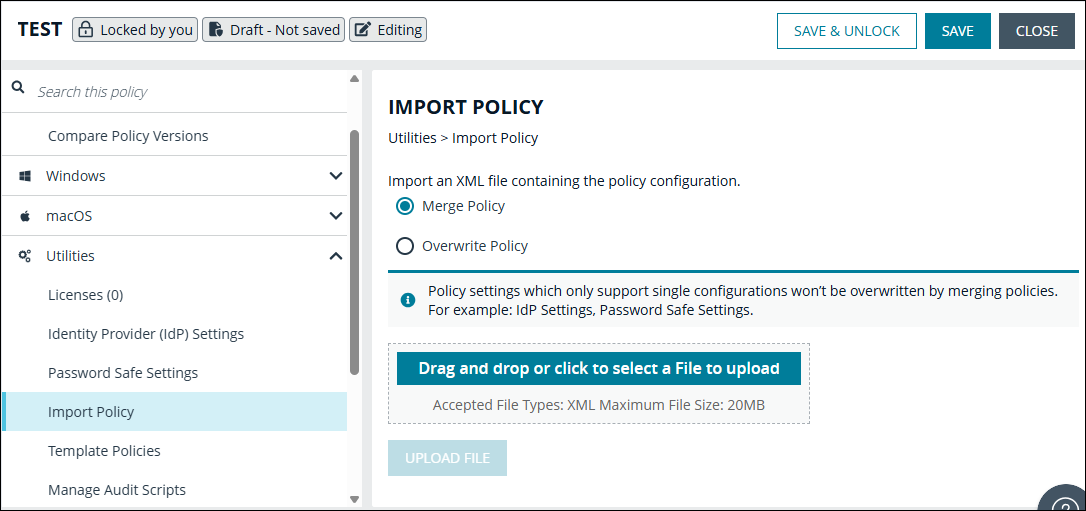
- Select one of the following:
- Merge Policy
- Overwrite Policy: If you select to overwrite, you can optionally select Export Existing Policy to save a copy before overwriting the policy.
- Drop the file onto the box or click inside the box to navigate to the file.
- Click Upload File.
Import template policy
You can import a template and merge or overwrite the settings in an existing template.
- In the Policy Editor, expand Utilities.
- Select Template Policies.
- Select one of the following:
- Merge Policy: Merges the configuration to the existing template.
- Overwrite Policy: If you select to overwrite, you can optionally select Export Existing Policy to save a copy before overwriting the policy.
- Select a template from the list: Discovery, QuickStart for Mac, QuickStart for Windows, Server Roles, TAP (High Flexibility), TAP (High Security).
- If you are merging, select Merge Template Policy to save the settings. If you are overwriting, select Overwrite Policy.
Manage audit scripts
When an application is allowed, elevated, or blocked, an event is logged to record details of the action. Actions are recorded in a third party tracking system by using audit scripts.
You can write audit scripts in Powershell or Javascript and configure the scripts using the Policy Editor.
- In the Policy Editor, expand the Utilities node.
- Select Manage Audit Scripts.
- Click Upload Script to expand the Upload Script panel.
- Click the following menus to further configure the script:
- Timeout Options
- Context Options
- Click inside the upload box to select the script.
Manage rule scripts
You can upload, view, and delete Power Rules in the Policy Editor.
The script must be a Windows PowerShell script in JSON format.
- In the Policy Editor, expand Utilities.
- Select Manage Rule Scripts.
- Click Upload Script to expand the Upload Script panel.
- Select a value from the Timout options list.
- Drag and drop the new script into the upload box or click to select a file.
- Click Upload Script to save your changes.
After a script is uploaded, you can delete or upload an updated script at any time.
Advanced agent settings
You can configure advanced agent settings to deploy additional registry based settings to endpoints that are running Endpoint Privilege Management for Windows and Mac.
- In the Policy Editor, expand Utilities.
- Select Advanced Agent Settings.
- Click Add to create a new setting.
- Type the desired value name.
- Select one of the following to designate the type:
- DWORD
- String
- Multi-String
- Click Create to confirm your changes and create the new setting, or Discard to delete your work.
Agent protection settings
Add agent protection to your endpoints to prevent admin users from tampering with the product, including stopping the services running or deleting its files from an endpoint.
EPM components protected and the level of protection are provided in the table.
| Action | EPM Component |
|---|---|
| Blocks uninstalls |
|
| Prevents stopping services |
|
| Blocks DLL injections |
|
| Blocks access to registry settings |
|
| File protection (deleting, moving, renaming, writing security attributes, or taking ownership) |
|
Set up protection
The setup is a two-part process:
- Generate public-private key pair.
- The public key is stored in a policy and distributed to all endpoint computers. The public key is automatically inserted into the policy when using MMC to create the key pair.
- The password-protected private key must be stored securely by the administrator. The private key and private key password are required when you want to disable agent protection.
- Enable protection.
Generate key pairs
To generate the key pair:
- In the Policy Editor, expand Utilities.
- Select Agent Protection Settings.
- Click Generate Key.
- Enter a password to encrypt the private key.
- Click Generate Key.
- The private key is automatically downloaded to the local computer. The file name is private.pem. The public key is automatically inserted into the policy.
Enable agent protection
Agent protection is enabled after the policy is deployed and loaded by the Windows computers.
To enable protection:
- In the Policy Editor, expand Utilities.
- Select Advanced Agent Settings.
- Click Add.
- Enter AgentProtectionState in the Name box.
- Select 64 bit.
- Ensure type is DWORD.
- In the Decimal box, set the value to 1. The Hex value automatically populates with the same value. There are three possible states: 0 = off, 1 = enabled, 2 = disabled.
Regenerate UUIDs
When importing and exporting policies from external sources, it can sometimes be necessary to regenerate the internal policy Universally Unique Identifier (UUID), so that Reporting manages the events correctly. For most normal scenarios in which this is required (policy duplication, for example), this is handled seamlessly.
However, duplication by importing a text XML file will not be covered because sometimes you will not want to regenerate the UUIDs, such as when restoring a policy from a backup.
- In the Policy Editor, expand Utilities.
- Select Regenerate UUIDs.
- Click the Regenerate UUIDs button.
A success message displays at the bottom center of the page.
User preferences
Customize the Policy Editor view for the menu and menu margin.
- In the Policy Editor, expand Utilities.
- Select User Preferences.
- Drag the slider to adjust the font size displayed for the menu.
- Drag the slider to adjust the menu margin (increase or decrease the spacing between menu items).
- Select Save Changes.
Updated 9 days ago
