Authentication provider settings | EPM-WM Cloud
EPM-WM supports OpenID Connect authentication. You can change your authentication provider from the default AzureB2B to OIDC, or update your OIDC settings, without having to contact Support.
You must first set up an EPM-WM instance in your OIDC provider. Steps are provided in the section below.
Configure an authentication provider
When you start from the default configuration, use this procedure to set up the configuration.
Important informationIf you choose to configure OIDC, you cannot revert to the default settings.
To set up an OIDC provider:
-
Select the Configuration menu, and then click Authentication Provider Settings.
-
Click Enable OpenID Configuration. After you complete and save the configuration, this switch no longer appears on this page.
-
Enter information for the following:
- Provider URL: Domain for the authentication. Currently supports Microsoft, Okta, Google, and Ping Identity.
- Client ID: The client ID.
- Client Secret: Secret key.
Setting might vary depending on the provider. The screen capture shows Ping Identity.
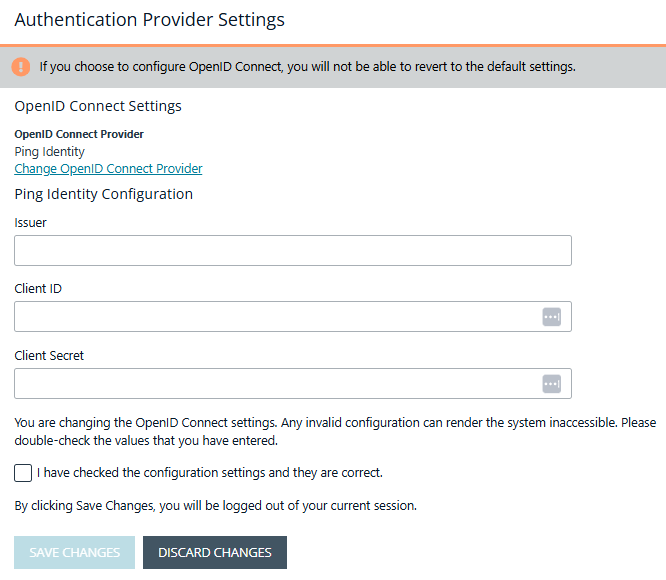
-
Check the box. We recommend reviewing the settings you configured. You can potentially lock yourself out of the system if the settings are incorrect. The Save Changes button is only available after you check the box.
-
Click Save Changes.
Important informationYou will be logged out of the EPM-WM console. Once logged out, you need to log back in within 15 minutes, because there is a timer on the page. If you do not log in before the timer expires, the authentication provider settings revert to the previous settings and the new settings are not saved.
If you log on before the timer expires, the newly added authentication provider settings are retained.
EPM-WM OIDC workflow for new customers
Here is the workflow to get up and running with EPM-WM using OIDC authentication.
- You will receive an email from BeyondTrust after the request is processed.
- In the email, click the link to open the BeyondTrust OpenID Setup page.
- Enter the OIDC information: domain, client ID, and client secret. Click Save Setup. The credentials are saved.
- The Endpoint Privilege Management login page opens. Click Log In.
- EPM-WM opens to the Home page.
Add EPM-WM to OIDC provider
EPM-WM supports Microsoft Entra ID, Okta OpenID, Google Identity, and Ping Identity Connect providers. The following sections provide a high-level overview on adding the EPM instance to your respective authentication provider. For complete instructions, refer to the provider's documentation.
The migration to OIDC will work when the email address sent from Okta or Entra ID matches for existing users. If email addresses are different or the domain name is not on the list of allowed domains in EPM, then the authentications will fail.
Google Identity
For step-by-step instructions on configuring Google Identity as your OIDC provider, visit OpenID Connect. After that configuration is complete, go to Configure an authentication provider.
- In APIs & Service for Google Cloud:
- Create the OAuth Consent Screen.
- The authorized domain must be beyondtrustcloud.com, a top-level domain, not a subdomain.
- You need the openid scope, optionally add email and profile.
- If a test user is added, remember the email for configuration steps in EPM.
- Create an OAuth 2.0 client
- The Authorized JavaScript origin URLs:
https://cbsi.pm.beyondtrustcloud.com
https://cbsi-services.pm.beyondtrustcloud.com - The Authorized redirect URIs:
https://cbsi-services.pm.beyondtrustcloud.com/oauth/signin-oidc
https://cbsi-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc
- The Authorized JavaScript origin URLs:
- Note the Client ID and Client Secret for later.
- Create the OAuth Consent Screen.
- In EPM-WM:
- Add your domain in Configuration > Domain Settings.
This domain is in the test email Google Account used earlier or other domains needed for invites. - Create a local user for the Google Account in User Management. This is the test email you used in Google Cloud earlier.
- Configure Authentication Provider Settings under Configuration.
- Select Google from the OpenID Connect Provider list.
- The Provider URL for Google is https://accounts.google.com.
- Enter in the Client ID and Client Secret from Google Cloud.
- Check the box I have checked the configuration settings and they are correct.
- Click Save Changes.
- Log in with your Google Account.
- Add your domain in Configuration > Domain Settings.
Microsoft Entra ID
- Log into your Microsoft Entra ID (formerly Azure AD) tenant.
- In the menu, click App Registrations.
- Click New Registration.
- Enter a Name.
- Under Supported account types, select Accounts in this org directory only.
- Enter the Redirect URI. While providing this now is optional and can be changed later, a value is required for most authentication scenarios.
- From the dropdown list, select the Web platform.
- Enter https://<deployment>-services.pm.beyondtrustcloud.com/oauth/signin-oidc where deployment is the name of your EPM tenant. For example, https://example-services.pm.beyondtrustcloud.com/oauth/signin-oidc
- Click Register.
- After EPM registers, select Authentication in the menu.
- Add the following to the Redirect URIs: https://<deployment>-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc where deployment is the name of your EPM-WM tenant.
- Go to Manage > API Permission, and then select Grant admin consent.
- Select Certificates & secrets in the menu.
- Click New client secret, and copy the value. The value is visible until you leave the web page. When generating a new secret, you must select an expiry for the secret. We recommend selecting Recommended: 6 months
After you add EPM to Microsoft Entra ID, you can get the information you need to set up the OpenID Connect authentication. The EPM OIDC setup wizard requires these values: OpenID Domain, OpenID Client ID, and Open ID Client Secret.
Make note of these values before proceeding to step 13. - On the app registration Overview page, copy the client ID and the tenant ID.
- OpenID Domain: https://login.microsoftonline.com/<Directory (tenant) ID> . The directory or tenant ID uses the format 31b8dbb9-fb8b-437a-8920-f23c8e0188b1.
- OpenID Client ID: Application (client) ID.
- OpenID Client Secret: This is the Value ID.
Okta
Supported features
The EPM-WM and Okta integration allows logging into EPM platform using SP-initiated SSO flow.
Configure the integration
-
Access your Okta instance.
-
Navigate to Applications, and then click the Browse App Catalog button.
-
Search for an app called BeyondTrustPrivilege Management Cloud - Windows and Mac.
-
Click Add Integration.
-
Click Done.
-
While in the new application, navigate to Sign On, and then click Edit.
-
Navigate to the Advanced Sign-on Settings and provide the Base Service URL which follows the format https://{_deployment_}-services.pm.beyondtrustcloud.com. (deployment is the name of your EPM tenant.) Click Save.
-
After you add the EPM App to Okta, you can get the information you need to set up the OpenID Connect authentication.
-
You must get the following information from the Edit page:
- Domain or Issuer, for example, https://dev-12345.okta.com
- Client ID
- Client Secret
Confirm the domain name configured in Okta. This domain name might be different than the domain configured for your email address. For example, while the domain managed in Okta might be domain.com, the email address might be [email protected]. Both pieces of information are required.
- Log in to your EPM instance to complete the configuration. Navigate to Configuration and then Authentication Provider Settings.
- Select Okta for the OpenID Connect Provider.
- Provide the domain or issuer URL, client ID, and client secret.
- Save and test the configuration.
Ping Identity
We currently support PingOne, the SaaS service from Ping Identity.
-
Start up your Ping Identity instance.
-
In the menu, click Connections, and then click Applications.
-
At the right of the Applications title, click the plus sign (+) to add an application.
-
Enter a name for the application (required), and then add a short description (optional).
-
Select OIDC Web App and click Save.
-
Click the Configuration tab.
-
To edit the configuration, click the pencil/edit icon.
-
Under Redirect URLs, click + Add, and then add the sign-in and sign-out URLs. If you are modifying an existing instance, you might need to open the General section dropdown first.
- Sign-in redirect URL: https://{_deployment_}-services.pm.beyondtrustcloud.com/oauth/signin-oidc
- Sign-out redirect URL: https://{_deployment_}-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc
where deployment is the name of your EPM tenant.
-
Under Token Endpoint Authentication Method, select Client Secret Post, and then click Save.
-
Click the Resources tab.
-
To edit the resource, click the pencil/edit icon.
-
In the Scopes list, click the + next to profile openID to add it to the Allowed Scopes. You can also filter the list of options by OpenID to access this option.
-
Click Save.
-
To close the panel, at the top right of the Edit panel, click the X.
-
At the right of the new application entry, toggle the switch to on to give access to users.
-
Click the Configuration tab again. For the EPM OpenID Connect set-up wizard, you need to copy the following information from the Configuration page:
- Issuer: Prefix the protocol HTTPS://
- Client ID
- Client Secret
Change authentication provider
After you set up an OIDC provider (Microsoft, Okta, or Ping Identity), you might need to switch to another one at some point.
To change your existing OIDC settings:
- Click the Configuration menu, and then select Authentication Provider Settings.
- Click Change OpenID Connect Provider.
- Select a different provider, and then enter the Provider URL (or Issuer), Client ID, and Client Secret information.
- Review your settings, and then check the verification box.
- Click Save Changes.
Important informationYou will be logged out of the EPM-WM console. Once logged out, you need to log back in within 15 minutes, because there is a timer on the page. If you do not log in before the timer expires, the authentication provider settings revert to the previous settings and the new settings are not saved.
If you log on before the timer expires, the newly added authentication provider settings are retained.
Updated about 1 month ago
