Reports are curated by our Security Research experts and cover various aspects of identity security. Each report is designed to give you a clear and immediate understanding of your organization's identity security posture via visual aids such as heat maps, trend graphs, and detailed breakdowns.
Use Insights reports to quickly assess risk and focus on critical findings.
- From the top left of the page, click
 > Insights > Reporting.
> Insights > Reporting.
The Reports page displays.
- Alternatively, click
 > Reporting > Insights > Reporting.
> Reporting > Insights > Reporting.
- Navigation menu: Access BeyondTrust apps and their menus, and Pathfinder administration pages if you are assigned as an administrator.
- Header: Select a site or Administration from the menu, manage your profile, and change the display theme.
- Reports list: Expand the report category to view the reports in the category.
- Report tiles: Click a report tile to view the collected data. Use the report controls to bookmark, filter, export, or refresh the data.
- Report controls: Bookmark, filter, or export a report using the main controls at the top of the report.
- Widget controls: Select a tile and use widgets to minimize and maximize the tile display, filter, and export are some of the available actions.
| Name | Description |
|---|
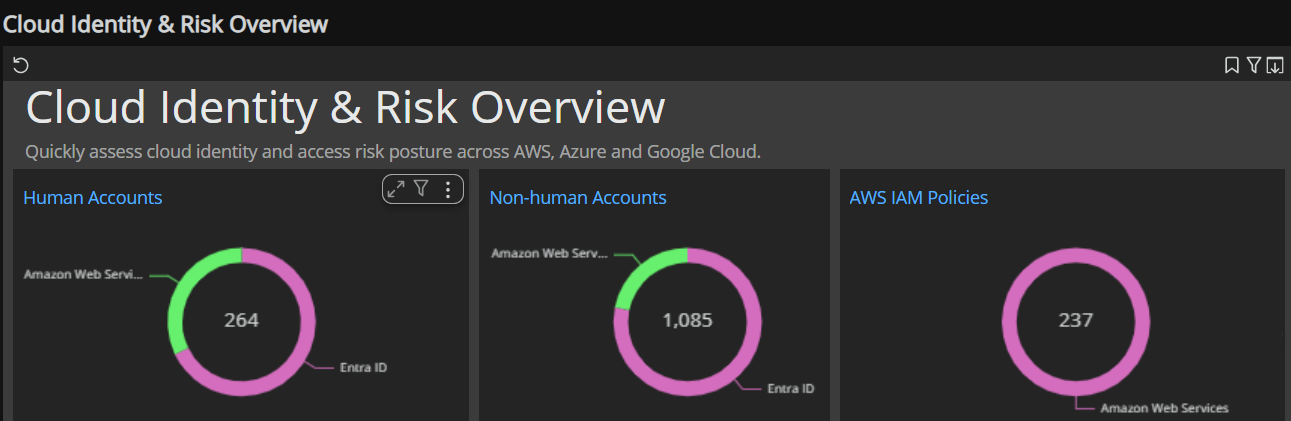
| Cloud Identity & Risk Overview | Quickly assess cloud identity and access risk posture across AWS, Azure and Google Cloud. |
| High Risk Accounts | Provides a comprehensive view of administrative accounts, privilege trends, account health, and security recommendations over time. |
| Identity Security Risk Assessment | A summary of the important findings from your environment. This report is broken down into sections relating to Human and Non-Human Account Privilege, Identity Risk & Hygiene and areas of Exposure which can help direct your efforts to secure your environment. |
| Identity Threats | Provides a detailed overview of detection and recommendation statuses, trends, and severities. |
| MITRE ATT&CK® | Threat activity mapped to the MITRE framework. |
| Name | Description |
|---|
| Local Accounts | Local accounts on computers, databases, and network devices by asset and account type. |
| SSH Keys | SSH Keys listed by computer, account name, local privilege, cipher type, and more. |
| Scanned Assets | Assets scanned by Password Safe and any collected information. |
| Users with Access to Endpoints | Every user with group or user-based access with local privilege and group paths. |
| Name | Description |
|---|
| Github Repo Overview | Overview of all of your repos, which repos are forked, as well as all of the security features applied to each repo. |
| Name | Description |
|---|
| Account Summary | Dashboard view of accounts collected by your configured connectors. |
| Detections | Detections in your environment. |
| Detections Trend | Detections tripped over time, enabling insight into trends from your environment. |
| Dormant Accounts | Accounts that have been dormant for 60 or more days. |
| Entitlement Summary | Fine-grained access entitlements collected such as authorizations, privileges, access rights, permissions or rules. |
| Group Access Explorer | Allows investigation of direct access that a group has in Active Directory. |
| Identity Summary | Summarization of Identities discovered from the configured connectors. |
| Inventory Summary | Dashboard view of accounts, identities, and entitlements. |
| Non-Human Identities | A centralized dashboard for tracking, analyzing, and managing interactions, behaviors, and attributes of non-human entities such as bots, AI agents, digital personas, or synthetic identities across platforms. |
| Recommendations | Recommendations in your environment. |
| Recommendations Trend | Recommendations over time that give you insight into trends in your environment. |
| Name | Description |
|---|
| Blank Passwords | Accounts with passwords that are blank. |
| Compromised Passwords | Accounts with passwords that are known to be compromised. |
| Password Health Overview | Shows an overall view into the health of Active Directory account passwords. |
| Shared Passwords | Grouping of accounts that share a password. |
| Name | Description |
|---|
| MITRE ATT&CK® Matrix | Provides an overview of findings mapped to MITRE tactics and techniques. |
| MITRE ATT&CK® Overview | Visualizes detected tactics, techniques, and threat actors to help security teams identify coverage gaps, understand adversary behavior, and prioritize defensive actions. |
| NIST 800-53 Overview | Overview of cybersecurity posture aligned with the NIST 800-53 Cybersecurity Framework. Tracks key controls across Identify, Protect, Detect, Respond, and Recover to support compliance, risk monitoring, and strategic security improvements. |
| Name | Description |
|---|
| Accounts Used for Tasks and Services on Computers | Directory and local accounts running services, scheduled tasks, and IIS application pool. Includes account privilege and compensating controls. |
| All Non-Human Accounts | All non-human accounts, including service accounts, and their true privilege. Includes Entra ID service principals and domain accounts. The report also shows the number of entities using the account and the most recent authentication or login. |
| Name | Description |
|---|
| Connector Data Health | Trend on collected data from connectors configured. |
Reports in this section are undergoing testing and feedback. Once finalized, the reports will have a permanent home in one of the above sections.
 > Insights > Reporting.
> Insights > Reporting. > Reporting > Insights > Reporting.
> Reporting > Insights > Reporting.

