Databricks | Insights
Important informationThird-party documentation is subject to change. Updates might not be reflected in BeyondTrust documentation. For the most up-to-date information, visit the websites linked in this topic.
Prerequisites
- Account Admin role in Databricks account
- Admin role in all Databricks workspaces
- MANAGE access to all workspaces' secret scopes.
Create Databricks connector
- From Insights Home, select
 > Connectors.
> Connectors.
The Connectors page displays. - Click Total configured.
- Click Create Connector and select Databricks from the list.

- Provide a human-readable name for the Databricks connector in the Name field in Step 1.
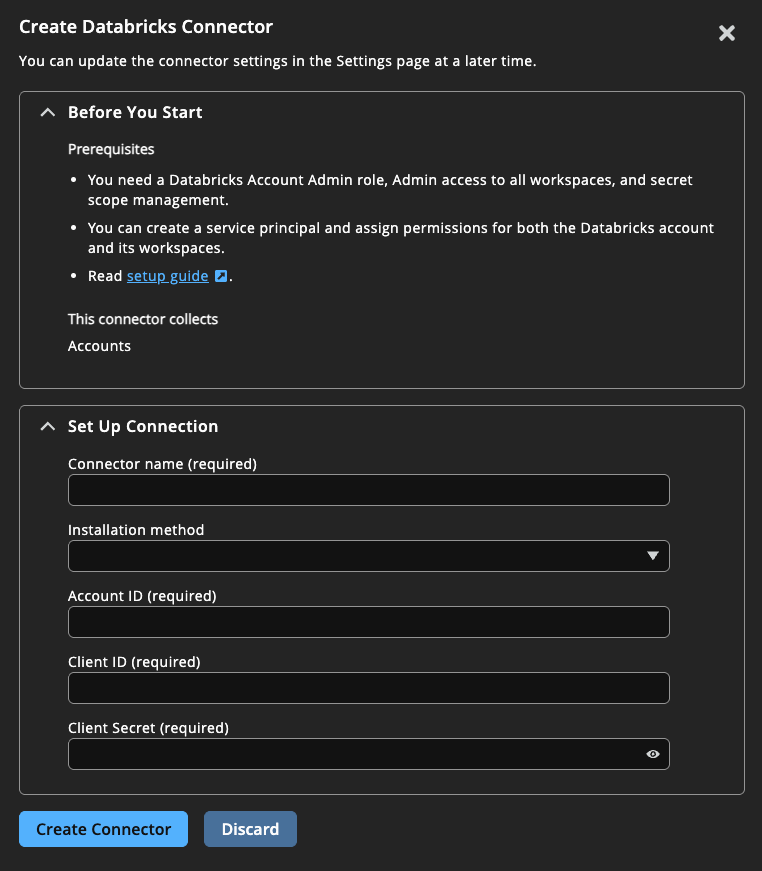
- In Step 2, select an installation method:
- Databricks CLI (recommended if you can install Databricks CLI)
- REST API
- In Step 3, download the PowerShell script and run it on local machine.
- The script will create the service principal in Databricks if it does not exist yet, create secret for service principal (optional), and assign the following permissions to the service principal:
- Account Admin in Databricks account
- Admin role in all Databricks workspaces
- MANAGE scope for all workspaces' secret scopes
- Once the script completes, record the output value of Account Id, Client Id and Client Secret for the next step.
- If Databricks CLI script option is selected, ensure Databricks CLI is available on the machine (Install or update the Databricks CLI | Databricks Documentation)
- The script will create the service principal in Databricks if it does not exist yet, create secret for service principal (optional), and assign the following permissions to the service principal:
- Use the values recorded from the previous step and enter in Step 4:
- Account Id: Your Databricks account id, e.g., 123e4567-e89b-12d3-a456-426614174111.
- Client Id: Databricks service principal application Id.
- Client Secret: Databricks service principal secret value.
- Click Create Connector.
Create Databricks Service Principal
The following instructions for the Databricks console provide an alternative method for executing the setup script. If the setup script completes successfully, there is no need to perform the steps outlined here.
- Create Service Principal
- Click User management on the sidebar.
- On Service Principals tab, click Add service principal.
- Enter BT-Insights-Databricks-SP service principal’s name.
- Click Add service principal.
For more information, see Manage service principals | Databricks Documentation.
- Create Credentials for Service Principal
- In the sidebar, click User management.
- On the Service principals tab, find and click the username.
- Select Credentials & secret tab.
- Click Generate secret.
- Enter the secret lifetime, e.g.: 365 and click Generate.
- Record the Client Id and Secret.
Assign Databricks Service Principal Permission
Assign Account Admin role to Service Principal
- In the sidebar, click User management.
- On the Service principals tab, find and click the username.
- Select Roles tab.
- Select Account admin to activate.
For more information, see Manage service principals | Databricks Documentation.
Assign Admin role to service principals for all workspaces
- On the menu on the left, navigate to Workspaces.
- Do the following step for each workspace:
- Click on workspace name.
- Navigate to Permissions tab.
- Click Add permissions.
- Search for BT-Insights-Databricks-SP.
- Select Admin for Permission.
- Click Save.
Assign MANAGE Scope to all workspaces' secret scopes
- Ensure Databricks CLI is installed. For more information, see Databricks CLI documentation.
- Obtain the Databricks Account ID by clicking on the user profile located in the top right corner of the Databricks account portal.
- Log in to Databricks account:
databricks auth login --host <https://accounts.cloud.databricks.com> --account-id {AccountId} - List all workspaces:
databricks account workspaces list --output json - For each workspace that is not in FAILED state:
- Get workspace deployment_name from the output above
- Log in to each workspace
databricks auth login --host https://{workspace_deployment_name}.cloud.databricks.com --profile {workspace_deployment_name} - List all secret scopes
databricks secrets list-scopes --profile {workspace_deployment_name} - For each secret scope
- Assign secret scope MANAGE permission to service principal
databricks secrets put-acl {scope_name} {sp_client_id} MANAGE --profile {workspace_deployment_name}
- Assign secret scope MANAGE permission to service principal
Updated 11 days ago
