Microsoft Azure | Insights
The Azure connector provides a script to retrieve the tenant ID, directory name, client ID, and client secret. For tenants with more than 100,000 users, set up the connector with Azure Event Hub.
Prerequisites
-
Enable auditing in Azure (Microsoft's Audit documentation)
-
Azure Global Administrator privileges (to create the connector)
-
Minimum Microsoft Entra ID P1 license
Required PowerShell Modules
- Az (Microsoft documentation: How to install Azure PowerShell)
- Microsoft.PowerApps.Administration.PowerShell (Microsoft documentation)
For each environment in your Power Platform admin center:
- Dataverse is enabled in the environments being added (Microsoft documentation: Add a Microsoft Dataverse database)
- You must be a System Administrator for the environment. To elevate your user to System Administrator in an environment. (Microsoft documentation)
Required roles and permissions
The following read-only roles are required for this connector. You do not need to manually grant these roles, as this is managed by the connector install script.
| Microsoft Graph | - Application.Read.All - AuditLog.Read.All - DelegatedAdminRelationship.Read.All - DeviceManagementApps.Read.All - Directory.Read.All - EntitlementManagement.Read.All - Group.Read.All - IdentityProvider.Read.Al - ldentityRiskEvent.Read.All - IdentityRiskyServicePrincipal.Read.All - IdentityRiskyUser.Read.All - MailboxSettings.Read - OnPremDirectorySynchronization.Read.All - Policy.Read.All - Reports.Read.All - RoleManagement.Read.All - Sites.Read.All - TeamsAppInstallation.ReadForUser.All - User.Read.All - UserAuthenticationMethod.Read.All |
| Office 365 management APIs | - ActivityFeed.Read |
| Management groups | - Reader role - Key Vault Reader role |
| Custom RBAC Role | - BT Insights Custom AI Reader role |
| Power Platform Security Role | - Service Reader role for app user |
Create the connector
-
From Insights Home, select
 > Connectors.
> Connectors.
The Connectors page displays. -
Click Total configured.
-
Click Create Connector and select Microsoft Azure from the list.
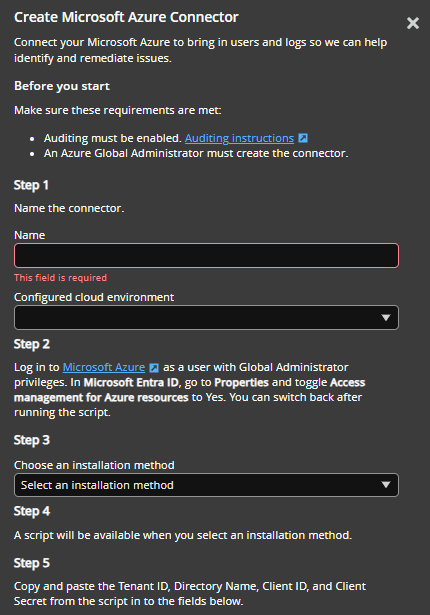
- Enter a human-readable Name for the connector.
- Select your cloud environment:
Use the login URL of the Azure portal to identify your environment:
| Azure Portal URL | Cloud Environment |
|---|---|
| https://portal.azure.com | Commercial / GCC |
| https://portal.azure.us | GCC High / DoD |
FedRAMP Compliance NoticeInsights Commercial is not FedRAMP-compliant. Using it in combination with the following cloud environments may result in data residency issues and loss of compliance:
- Azure Government Community Cloud (GCC)
- Azure GCC High
- Azure Government Department of Defense (DoD)
-
Use the link on-screen to sign in to the Microsoft Azure Portal as a user with Azure Global Administrator privileges.
-
In Entra ID, navigate to the Properties page and toggle Access management for Azure resources to Yes.
You can toggle this back to No after running the script.
-
In Insights, select an installation method from the drop-down and follow the associated instructions:
Install using PowerShell
-
Ensure you installed Azure PowerShell on Windows. For more information, see the Azure PowerShell documentation.
-
Once installed, open PowerShell as a standard user and log in to Azure by running the command Connect-AzAccount. Enter your login credentials in the following window.
-
Ensure you are connected to the correct Azure tenant and directory, and run the following commands:
- Get-AzTenant to see all the directories you have access to.
- Set-AzContext -Tenant "TenantID", where TenantID is the ID of the directory where the script will be installed.
- Get-AzContext to verify your selection.
- Set-ExecutionPolicy -Scope Process -ExecutionPolicy Bypass, which is necessary if scripts must be digitally signed in your environment.
-
Download the Azure onboarding script and run with the given command provided for your selection.
-
In Insights, copy the tenant ID, directory name, client ID, and client secret from the script into the appropriate fields.
-
In the Microsoft Azure Portal:
- Navigate to Azure Services > Microsoft Entra ID.
- Select App Registrations in the left menu.
- Select the BT-SP-Connector application.
- In the API permissions section, select Grant admin consent.
- Confirm your selection.
In Insights, if you:
- Have less than 100,000 users or are not subscribed to Azure Event Hub, select No from the Use Azure Event Hub dropdown.
- Have 100,000 users or more and access to Azure Event Hub, select Yes from the Use Azure Event Hub dropdown.
Set up Azure Event Hub
If you selected No in the previous step, skip these instructions.
-
In Insights, copy the Insights-generated Azure Event Hub script.
-
In the shell environment, paste and run the Insights-generated Azure Event Hub script.
-
Once complete, copy the Fully Qualified Hub Namespace, Blob Container Url, and Hub Name in a secure location for use in the following step.
-
Follow Microsoft's procedure to stream logs to an event hub.
-
Within the Azure Diagnostics settings, select the following log Categories to stream:
- SignInLogs
- NonInteractiveUserSignInLogs
- ServicePrincipalSignInLogs
- ManagedIdentitySignInLogs
-
Within Azure's Destination details section, select Stream to an event hub, and select the Fully Qualified Hub Namespace and Hub Name you saved in step 3, above.
-
In Insights, enter the Fully Qualified Hub Namespace, Blob Container Url, and Hub Name in the appropriate fields.
-
Click Create Connector.
The connector is created and displays in your Configured tab on the Connector page.
Ensure the connector is turned on. You can verify and enable it on the Overview page of the connector.
Update the Microsoft Azure connector client secret
These steps are used when it is time to refresh the app registration secret.
Microsoft Azure steps
- In Microsoft Azure, use the search box to search for Microsoft Entra ID and select it from the results.
- Under the Manage section in the left menu, select App registrations.
- Locate and select the BT-SP-Connector application under All applications. Note the Application (client) ID for reference.
- Under the Manage section, select Certificates & Secrets.
- Select + New client secret, provide a description and set an expiry date according to your company's guidelines, then click Add.
- Copy the Secret Value and store it in a secure location.
Insights steps
- From the top left of any page in Insights, click
 > Insights > Connectors. The Connectors page displays.
> Insights > Connectors. The Connectors page displays. - Locate and select the Microsoft Azure connector in the Configured Connectors list that requires attention.
- Navigate to the Settings tab, confirm the Client ID matches the one from the Azure steps, and paste in the Secret Value.
- Select Save Changes.
Updated 11 days ago
