Google Cloud Platform | Insights
Requirements
Identity Security Insights requires a service account to access information in your Google Cloud Platform organization.
A service account can be created manually, via the Google Cloud Console, or via a script for Google Cloud Shell provided by Identity Security Insights.
Manually configure a Google Cloud Platform connector
Create a new project
- Within the Google Cloud Console, click the project selector in the top navigation bar, and select your organization.
- In the project window, click New Project.
- Enter a human-readable name for your project.
- Click Create.
Enable required services
- From your new project's navigation menu, go to APIs & Services > Library.
- Search for and enable the following APIs:
- Cloud Asset API
- Cloud Logging API
- Cloud Resource Manager API
- Admin SDK API
- Drive Labels API
- Google Drive API
- Google Drive Activity API
- Secret Manager API
- Cloud Key Management Service (KMS) API
- API Keys API
- Discovery Engine API
- Optional: If you chose Enable Vertex AI, enable the following API:
- API Discovery Service
- Discovery Engine API
- Vertex AI API
Ensure all projects within your organization have the same APIs enabled.
Create a service account
- From the navigation menu, go to IAM & Admin > Service Accounts.
- Click Create Service Account.
- Enter a human-readable display name for your new service account.
- Enter a unique service account ID.
- The Google Cloud console will generate an email address for this service account. This email address will be required in the next step.
- When finished, click Done.
Assign service account roles
- In the top navigation toolbar, click the project selector, and select your organization.
- Navigate to IAM & Admin > IAM, and click Grant Access.
- In the New principals field, enter the service account email generated by Google Cloud.
- Under Assign roles, select the following roles:
- Cloud Asset Viewer
- Security Reviewer
- Logs Viewer
- Organization Viewer
- Secret Manager Secret Accessor
- Secret Manager Viewer
- Cloud KMS Viewer
- API Keys Viewer
- Optional: If you chose Enable Vertex AI, select the following roles:
- Discovery Engine Viewer
- Storage Object Viewer (if you checked the box Allow access to agent model details)
- When finished, click Save.
Generate a key for the service account
- In the top navigation toolbar, click the project selector, and select your new project.
- From the navigation menu, go to IAM & Admin > Service Accounts, and select the created service account.
- Click the Keys tab.
- Click Add Key > Create new key.
- Select JSON as the key type.
- Click Create.
- A new key will be automatically downloaded to your local system. Ensure you keep the downloaded JSON key in a secure location.
Setup Google Workspace Permission (optional)
Configure Domain-wide Delegate
- Navigate to Admin Console > Security > API Controls > [Domain-wide Delegation](https://admin.google.com/ac/owl/domainwidedelegation)
- Click Add new and enter the service account's Client ID. This is the 21-digit number obtained from the key JSON file under the client_id field
- Add the following OAuth scopes (comma-separated):
https://www.googleapis.com/auth/admin.directory.user.readonly
https://www.googleapis.com/auth/admin.directory.group.readonly
https://www.googleapis.com/auth/admin.directory.orgunit.readonly
https://www.googleapis.com/auth/admin.directory.rolemanagement.readonly
https://www.googleapis.com/auth/admin.directory.customer.readonly
https://www.googleapis.com/auth/admin.directory.user.security
https://www.googleapis.com/auth/drive.readonly
https://www.googleapis.com/auth/drive.metadata.readonly
https://www.googleapis.com/auth/drive.activity.readonly
https://www.googleapis.com/auth/drive.labels.readonly
https://www.googleapis.com/auth/drive.admin.labels.readonly - Save the changes.
Create the Google Cloud Platform Connector
- From Insights Home, select
 > Connectors.
> Connectors.
The Connectors page displays. - Click Total configured.
- Click Create Connector and select Google from the list.
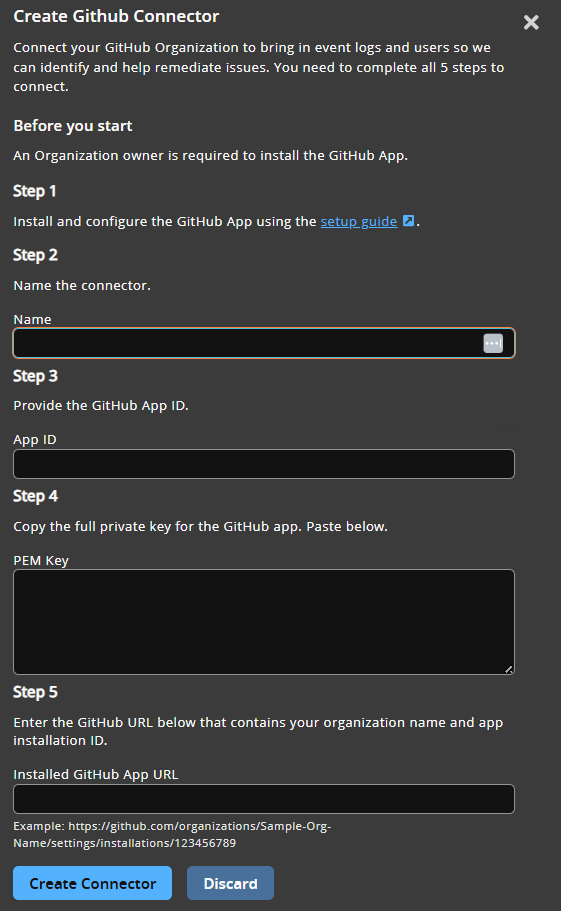
- Enter a human-readable name for your connector.
- Select your cloud environment
- Follow the guidance below to select the appropriate environment:
- If your organization operates any FedRAMP High assured workloads, select FedRAMP High.
- If your organization operates FedRAMP Moderate assured workloads only, select FedRAMP Moderate.
- Otherwise, select Commercial.
FedRAMP Compliance Notice
Insights Commercial is not FedRAMP-compliant. Using it in combination with the following cloud environments may result in data residency issues and loss of compliance:
- FedRAMP High
- FedRAMP Moderate
- Follow the guidance below to select the appropriate environment:
- Select Manual Configuration from the installation method drop-down menu.
- Provide the following information about your service account:
- Organization ID: Your organization ID can be found in the Google Cloud Console by selecting your organization from the drop-down menu, and navigating to IAM & Admin > Settings.
- Service Account Key: The JSON key created for your service account.
- (Optional) Configure Google Workspace
- Select Yes on the Use Google Workspace dropdown
- Input Admin User Email with an organization admin's email, who has the permissions to view all users, groups, admin roles, and role assignments.
- Click Create Connector.
Navigate to the Configured Connectors panel (Menu > Connectors > Configured) to confirm that connector creation was successful and review any connector settings.
Create a GCP connector with Google Cloud Shell
Create the Google Cloud Platform Connector
- From Home go to Menu > Connectors.
- Select the Available tab.
- Click Create Connector beside Google Cloud Platform.
- In the connection panel, enter a human-readable name for your GCP Connector.
- Select Google Cloud Shell from the installation method drop-down menu.
Configure Google Cloud Platform
- In a new window, sign into Google Cloud Platform Console.
- Click Activate Cloud Shell in the upper-right navigation menu to open the command line interface.
If you are prompted to authorize an action after running a command, authorize it. The command may need to be re-run after authorization.
Retrieve the organization ID
- Run the following command to retrieve your organization ID:
gcloud organizations list- Paste your organization ID in the Organization ID field in Identity Security Insights.
Create a new project
Run the following command to create a new project, replacing <Project-ID> with a unique ID of your choosing:
gcloud projects create <MDXishSnakeCase0>Set the current project
Run the following command to set your current project, replacing <Project_ID> with the ID you created:
gcloud config set project <MDXishSnakeCase0>Enable required services
Run the following command to enable necessary Google Cloud services:
project_ids=$(gcloud projects list --format json | jq -r '.[].projectId')
for project_id in $project_ids; do
gcloud services enable cloudresourcemanager.googleapis.com --project "$project_id"
gcloud services enable cloudasset.googleapis.com --project "$project_id"
gcloud services enable logging.googleapis.com --project "$project_id"
gcloud services enable admin.googleapis.com --project "$project_id"
gcloud services enable apikeys.googleapis.com --project "$project_id"
gcloud services enable cloudkms.googleapis.com --project "$project_id"
gcloud services enable secretmanager.googleapis.com --project "$project_id"
doneThis command enables the following APIs for all projects:
- Cloud Asset API
- Cloud Logging API
- Cloud Resource Manager API
- Admin SDK API
- Cloud Key Management Service (KMS) API
- API Keys API
- Secret Manager API
Create a service account
Run the following command to enable create a new service account, replacing <Service_account_ID> with a unique ID:
gcloud iam service-accounts create <MDXishSnakeCase1>Assign service account roles
Run the following command to assign necessary roles to your new service account, replacing <Organization_ID>, <Service_account_ID>, and <Project_ID> with the values set in earlier steps:
gcloud organizations add-iam-policy-binding <MDXishSnakeCase2> --role 'roles/iam.securityReviewer' --member serviceAccount:<MDXishSnakeCase1>@<MDXishSnakeCase0>.iam.gserviceaccount.com
gcloud organizations add-iam-policy-binding <MDXishSnakeCase2> --role 'roles/cloudasset.viewer' --member serviceAccount:<MDXishSnakeCase1>@<MDXishSnakeCase0>.iam.gserviceaccount.com
gcloud organizations add-iam-policy-binding <MDXishSnakeCase2> --role 'roles/serviceusage.apiKeysViewer' --member serviceAccount:<MDXishSnakeCase1>@<MDXishSnakeCase0>.iam.gserviceaccount.com
gcloud organizations add-iam-policy-binding <MDXishSnakeCase2> --role 'roles/cloudkms.viewer' --member serviceAccount:<MDXishSnakeCase1>@<MDXishSnakeCase0>.iam.gserviceaccount.com
gcloud organizations add-iam-policy-binding <MDXishSnakeCase2> --role 'roles/secretmanager.viewer' --member serviceAccount:<MDXishSnakeCase1>@<MDXishSnakeCase0>.iam.gserviceaccount.com
gcloud organizations add-iam-policy-binding <MDXishSnakeCase2> --role 'roles/secretmanager.secretAccessor' --member serviceAccount:<MDXishSnakeCase1>@<MDXishSnakeCase0>.iam.gserviceaccount.comGenerate a key for the service account
- Run the following command to generate a new key, replacing <Service_account_ID> and <Project_ID> with the values set in earlier steps:
gcloud iam service-accounts keys create /dev/stdout --iam-account=<Service account ID>@<Project ID>.iam.gserviceaccount.com- Copy the full JSON output, and paste it in Service Account Key field in Identity Security Insights.
- When finished, click Create Connector.
Navigate to the Configured Connectors panel (Menu > Connectors > Configured) to confirm that connector creation was successful and review any connector settings.
Updated 17 days ago
