GitHub | Insights
Configure a new GitHub app
A GitHub organization owner is required to install a new GitHub app.
-
Log in to GitHub as an organization owner.
-
In the upper-right corner, select your profile photo, and click Your organizations.
-
To the right of the organization where the Insights app will be installed, click Settings.
-
In the left sidebar, click Developer settings, and select GitHub Apps.
-
Click New GitHub App.
-
Provide the following information to create your new app:
- GitHub App name: A unique name for your new application.
- Homepage URL: https://app.beyondtrust.io
-
Under Webhook, uncheck Active.
-
Under Repository permissions, set the following resources to Read only:
- Administration
- Actions
- Codespaces lifecycle admin
- Metadata
- Secret scanning alerts
- Webhooks
-
Under Organization permissions, set the following resources to Read only:
- Administration
- Blocking users
- Custom organization roles
- Custom repository roles
- Events
- Members
- Organization codespaces secrets
- Organization dependabot secrets
- Secrets
- Self-hosted runners
- Webhooks
Secret related permissions do not allow retrieval of the encrypted values.
- Under Where can this GitHub App be installed?, select Only on this account.
- Click Create GitHub App.
- GitHub generates a new App ID. Save this for use when creating your Insights GitHub connector.
- Under Private Keys, click Generate a private key.
- A PEM file downloads to your local system. Save the contents of this file for use when creating your Insights GitHub connector.
- In the left-hand menu, navigate to the Settings page, and click Install App.
- Click Install. Review your settings and permissions, then click Install again.
- Copy the URL string from your web browser's address bar. Save this for use when creating your Insights GitHub connector.
- Navigate to the settings area for your organization.
- In the left sidebar, click Archive > Logs, and select Audit Log.
- Select Settings from the top navigation section of the log area.
- Check the box Enable source IP disclosure and click Save.
Create a GitHub connector
- From Insights Home, select
 > Connectors.
> Connectors.
The Connectors page displays. - Click Total configured.
- Click Create Connector and select GitHub from the list.
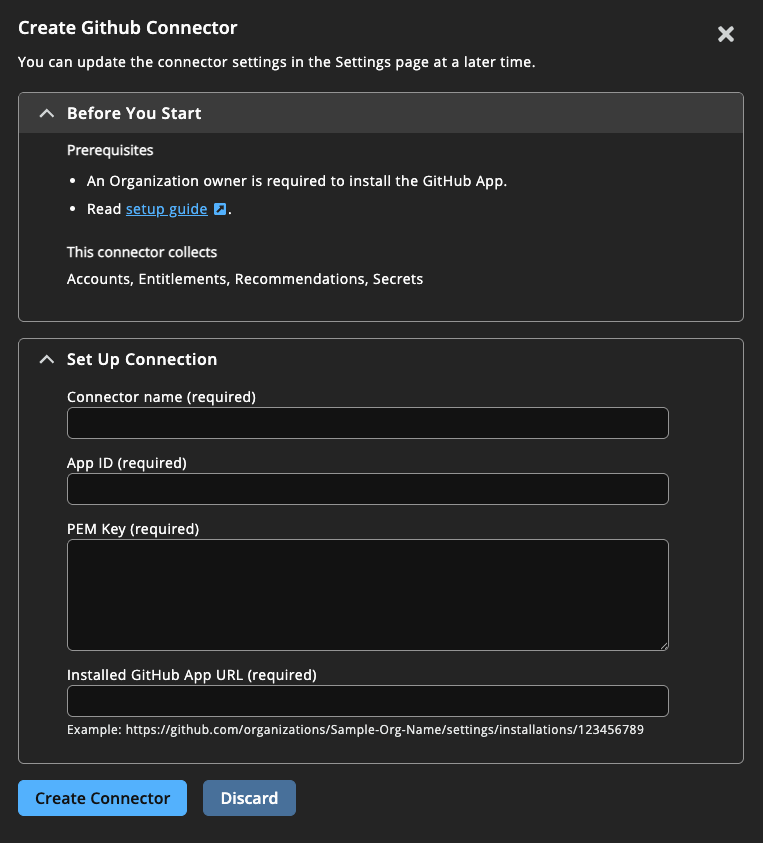
- Enter a human-readable name for your GitHub connector.
- Provide the following information from your GitHub app:
- App ID: The app ID generated in step 11.
- PEM Key: The contents of the PEM file downloaded in step 12.
- Installed GitHub App URL: The URL string saved in step 15.
- Click Create Connector.
Navigate to the Configured Connectors panel (Menu > Connectors > Configured) to confirm that connector creation was successful and review any connector settings.
Upgrade GitHub Identity Security Insights app
Update Permissions
If you installed the GitHub app before Insights version 24.08, follow these steps to upgrade your GitHub app with new permissions that enable future enhanced detections and recommendations.
- Go to your Installed GitHub Apps. Follow steps 1-4 to Configure a new GitHub app for detailed navigation steps.
- Select the GitHub app configured for Insights and select Edit.
- Select Permissions & events.
- Under Repository permissions, set the following resources to Read only:
- Administration
- Actions (new)
- Codespaces lifecycle admin
- Metadata
- Secret scanning alerts
- Webhooks
- Under Organization permissions, set the following resources to Read only:
- Administration
- Blocking users
- Custom organization roles
- Custom repository roles
- Events
- Members
- Organization codespaces secrets
- Organization dependabot secrets
- Secrets
- Self-hosted runners (new)
- Webhooks
Secret related permissions do not allow retrieval of the encrypted values.
- Select Save changes.
- An Update Permissions Request email may be sent to review the changes made to the app.
- The changes can also be viewed here: https://github.com/settings/installations
- The permission update to the app must be reviewed and accepted for the changes to take effect.
Enable Audit Logs
Insights supports GitHub and uses the GitHub audit logs to develop recommendations and detections content. Several of these detections rely on the inclusion of IP addresses in the GitHub audit logs, which are not enabled by default. Note that IOP addresses are only included for an event if the actor is an organization member or owner or if the target is either an organization-owned repository that is private or internal or an organization resource that is not a repository, such as a project. Follow these steps to enable Audit logs for this feature.
- In GitHub, navigate to the settings area for your organization.
- In the left sidebar, click Archive > Logs, and select Audit Log.
- Select Settings from the top navigation section of the log area.
- Check the box Enable source IP disclosure and click Save.
Updated 10 days ago
