Insights Collector (Microsoft Active Directory) | Insights
The Insights Collector is used to collect data from Active Directory and Active Directory Certificate Services. It provides two services related to Active Directory. Once for Inventory and Event Ingestion and one for Password Auditing.
Gaining visibility into your Active Directory landscape is critical to understand how to approach Identity Security in a proactive way. Insights will highlight potentially malicious events and hygiene recommendations in a prioritized way using True Privilege allowing you to focus on the risks that make the largest impact.
Architecture
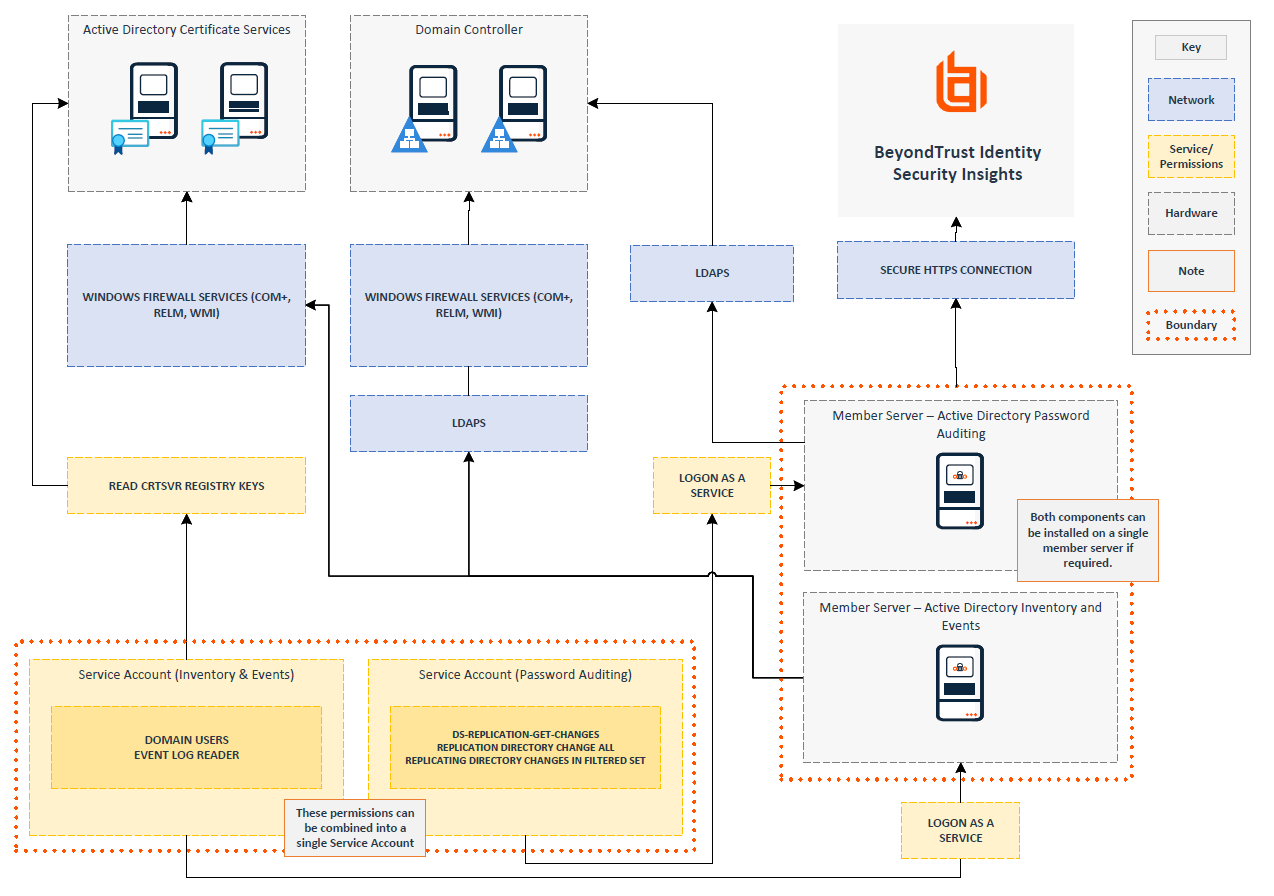
The architecture diagram shows individual servers hosting the Inventory and Events feature and the Password Auditing feature, with separate Service Accounts for each component.
If needed, these features can be combined onto a single server and use a single service account.
Active Directory inventory and event ingestion
Bring in users, groups, computers, group policy objects (GPOs), Access Control Lists (ACLs), and Active Directory Certificate Services (ADCS) data from your on-premises Active Directory.
BeyondTrust prerequisites
You must configure the Insights Collector in your Insights Tenant before you can install it on a member server within your Active Directory environment.
Active Directory prerequisites
| Requirement | |
|---|---|
| Hardware | 16 GB RAM, dual-core CPU 🚧 The Insights Collector is not supported when on a Domain Controller. |
| Service Account Group Membership | Domain UsersEvent Log Reader |
| Additional Service Account Permissions (If Active Directory has been hardened) | Read access to the following Active Directory attributes;
|
Outbound Network Connectivity (Member Server -> BeyondTrust) | Authentication: https://login.beyondtrust.io Ingestion Endpoint (Select your region): |
Internal Network Connectivity (Member Server -> Domain Controllers) |
|
Internal Network Connectivity (Member Server -> ADCS Enrollment Servers) |
|
| ADCS Enrollment Server Permissions | The Service Account must have Read access to the following registry keys;
|
| ADCS Configuration |
ℹ️ For more information on these configuration settings, refer to the Microsoft documentation. |
Active Directory password auditing
Enables support for password auditing capabilities, including identifying blank, duplicate/reused and compromised passwords within your Active Directory domain.
Any member server hosting the Insights Active Directory Connector with this Password Auditing feature enabled, and any service accounts which support its operation, must be treated as Tier 0 assets for the purposes of network segmentation, access control, and monitoring.
Due to its functionality, the member server can be more heavily isolated and restricted than a Domain Controller, but at the minimum classified and treated as such.
For more information on protecting Tier 0 assets, see Protecting Tier 0 the Modern Way.
BeyondTrust prerequisites
You must configure the Insights Collector in your Insights Tenant before you can install it on a member server within your Active Directory environment.
Active Directory prerequisites
The Password Auditing feature can be installed as a standalone component on a separate member server using its own Service Account or as part of the Active Directory Inventory and Event feature.
| Requirement | |
|---|---|
| Hardware | 16 GB RAM, dual-core CPU 🚧 The Insights Collector is not supported when on a Domain Controller. |
| Service Account Permissions | The following permissions are configured at the Domain level.
|
Outbound Network Connectivity (Member Server -> BeyondTrust) | Authentication: https://login.beyondtrust.io Ingestion Endpoint (Select your region): |
Internal Network Connectivity (Member Server -> Domain Controllers) |
|
Install the Insights Collector
If choosing to run the Password Auditing feature on a separate component be aware that only a single Insights Collector needs to be setup within Insights.
-
Navigate to Insights> Connectors from the top left menu
-
Click Available Connectors.
-
Find Insights Collector and click Create Connector
-
Enter a name for your connector and click Create Connector.
-
Copy the generated key and save it securely.
-
Click Download to get the installation file.
-
Run the installer on your member server.
-
When prompted, paste the installation key from step 5.
-
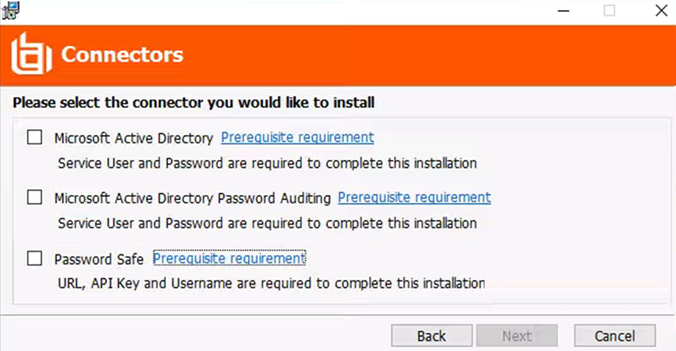
When prompted, select your required features.
If your deployment is Password Safe on-premises, select the Password Safe check box. If it is Password Safe Cloud, do not select the Password Safe check box and use the Password Safe Cloud connector.
-
After installation completes, return to Insights and click Close Key (or View Credentials if you need to access the key again).
-
Verify the connector appears in your Available Connectors list.
Update or reinstall the Insights Collector
Automatic updates
The Insights connector updates automatically when a new version becomes available, without any need for manual installation.
Reinstall the Insights Collector
- Navigate to Insights > Connectors from the top left menu.
- Find the Insights Collector you want to reinstall.
- Click the menu icon and select View Connector.
- Click Settings.
- Click the download the installer link.
- Run the installer on the member server and follow the on-screen prompts.
Troubleshooting
Common errors
| Error | Resolution |
|---|---|
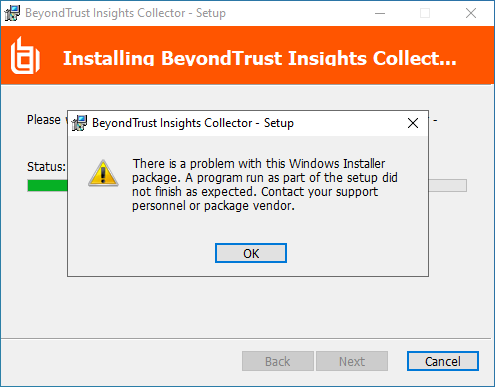 | Ensure the Registration Key within Insights has not expired. If it has please generate a new Insights Collector. Ensure the Member Server can communicate to https://login.beyondtrust.io |
| BeyondTrust Insights Collector Service not Starting | Ensure the service accounts are granted Log on as a Service rights on the member server. |
Log locations
| Management Service | C:\Program Files\BeyondTrust\Insights Collector\logs |
| Collectors running as Domain Users | %USERPROFILE%\AppData\Local\Temp\insightlogs |
Override registry keys
Override registry keys to fine-tune the behavior of the Insights collector, ensuring it operates optimally within your infrastructure. Adjust settings such as targeted forest, targeted domains, and job frequencies to enhance security, improve performance, and tailor the collector functionality to meet your needs.
Configuration
- Press Windows + R, type
regedit, and press Enter (click Yes if prompted). - Navigate to
HKEY_LOCAL_MACHINE\\SOFTWARE\\BeyondTrust\\Insights. - Right-click in the right pane and select New > String Value.
- Name the value (details below).
- Double-click your key and enter the setting (details below).
Active Directory inventory and event ingestion registry keys
The following registry keys are available to fine-tune the Active Directory Inventory and Event Ingestion component.
| Value | Type | Description | Example | Reason |
|---|---|---|---|---|
| Forest | String | Targeted forest name to use. | exampleForestName | To determine the AD forest context for LDAP queries for collecting ADCS-related information. |
| Domain | String | Targeted domain name to use. | exampleDomainName | To limit AD inventory collection to a specific domain. To enable targeted event collection from a specific domain (in combination with a domain controller). |
| DomainController | String | Targeted domain controller to use. Requires the Domain string value to be set. | exampleDomainController | To set the target LDAP server for AD inventory collection. To collect events only from specified domain and its controller(s), if configured. |
| SecurityLogsDomainControllersTargeted | String | Comma-separated list of DCs to target for event collection. Requires the Domain string value to be set. | dc1,dc2 | To collect events only from specified domain and targeted domain controller(s), if configured. |
| SecurityLogsDomainControllersExcluded | String | Comma-separated list of DCs to exclude from event collection. Requires the Domain string value to be set. | dc3,dc4 | To exclude specific domain controller(s) for event collection. |
| SkipDomains | String | Comma-separated list of domains to skip collecting from. | domain1,domain2 | A setting to exclude specific domains from data collection processes such as Active Directory password auditing. |
| CollectADCS | String | Values: true(default) or false (default: true). | true | Flag to enable the collection of Active Directory Certificate Services (ADCS) data. |
| ADInventoryJobFrequency | String | Frequency of AD inventory job in minutes (default: 120). | 120 | Override the job frequency using a registry setting (if present). |
| DomainControllerEventJobFrequency | String | Frequency of domain controller event job in minutes (default: 10). | 10 | Override the job frequency using a registry setting (if present). |
| InventoryThreads | String | Number of inventory threads (default: 25). | 25 | Maximum number of parallel threads used for processing ADInventory data, to optimize performance. |
| UseSSL | String | Toggles the use of SSL for LDAP connections (default: true) | false | If LDAP does not use SSL in your environment (ie LDAPS) |
Active Directory password auditing registry keys
The following registry keys are available to fine-tune the Active Directory Password Auditing component.
| Value | Type | Description | Example | Reason |
|---|---|---|---|---|
| PasswordAuditingJobFrequency | String | Frequency of password auditing job in minutes (default: 10080). | 10080 | Override the job frequency using a registry setting (if present). |
| CachePurgeJobFrequency | String | Frequency of cache purge job in minutes (default: 1440). | 1440 | Override the job frequency using a registry setting (if present). |
| CachePasswordAuditFiles | String | true(default) or false Local cache of audit database during audit. | true | Override the default behavior of using a local cache on disk of the database audit. If disk space is a concern this can be disabled. |
Information collected and polling periods
The Insights Collector accesses a variety of information. It uses store and forward techniques to store event data locally in the event of a connection issue with a member server.
| Data Collected or Accessed | Default Poll Period | |
|---|---|---|
| Domain Controller Event Log |
| 10 minutes |
| Active Directory Inventory |
| 2 hours - Delta 24 hours - Full |
| Active Directory Certificate Services (ADCS) |
| 2 hours - Delta 24 hours - Full |
| Active Directory Password Auditing | The service account retrieves Active Directory password hashes to the member server, where they stay—they're never transmitted elsewhere or saved to disk. These hashes are compared locally against the Insights password audit database (including haveibeenpwned.com) to check for weak, shared or compromised passwords. The audit results show pass or fail for each account without including the actual password hash. | 24 hours |
The Insights Collector gathers information from Active Directory, and sends this information to Insights for analysis. Some security solutions may detect this as an attack pattern after the connector is installed.
Security alerts you may see include:
- Suspicious LDAP search
- A service account is authenticating over Kerberos
- A device is sending data externally
Event ID details
| Event ID | Detail | Feature |
|---|---|---|
| 4768 | A Kerberos authentication ticket (TGT) was requested. This event generates every time Key Distribution Center issues a Kerberos Ticket Granting Ticket (TGT). | Security |
| 4769 | A Kerberos service ticket was requested. This event generates every time Key Distribution Center gets a Kerberos Ticket Granting Service (TGS) ticket request. | Security |
| 4770 | A Kerberos service ticket was renewed. This event generates for every Ticket Granting Service (TGS) ticket renewal. | Security |
| 4771 | Kerberos pre-authentication failed. This event generates every time the Key Distribution Center fails to issue a Kerberos Ticket Granting Ticket (TGT). This problem can occur when a domain controller doesn't have a certificate installed for smart card authentication (for example, with a "Domain Controller" or "Domain Controller Authentication" template), the user's password has expired, or the wrong password was provided. | Security |
| 4776 | The computer attempted to validate the credentials for an account. This event generates every time a credential validation occurs using NTLM authentication. It occurs only on the computer that is authoritative for the provided credentials. For domain accounts, the domain controller is authoritative. For local accounts, the local computer is authoritative. | Security |
| 4624 | An account was successfully logged on. This event generates when a logon session is created (on destination machine). It generates on the computer that was accessed, where the session was created. | Security |
| 4662 | An operation was performed on an object. This event generates whenever an operation was performed on an Active Directory object. This event generates only if appropriate SACL was set for Active Directory object and performed operation meets this SACL. | Security |
| 4740 | A user account was locked out. This event generates every time a user account is locked out. This account lockout event ID is very helpful when troubleshooting. | Security |
| 4742 | A computer account was changed. This event generates every time a computer object is changed. | Security |
| 5136 | A directory service object was modified. This event generates every time an Active Directory object is modified. To generate this event, the modified object must have an appropriate entry in SACL: the "Write" action auditing for specific attributes. | Security |
| 4741 | This event generates every time a new computer object is created. This event generates only on domain controllers. | Security |
| 4670 | Permissions on an object were changed | Windows Server |
| 4717 | System security access was granted to an account | Windows Server |
| 4720 | A user account was created | Windows Server |
| 4722 | A user account was enabled | Windows Server |
| 4727 | A security-enabled global group was created | Windows Server |
| 4728 | A member was added to a security-enabled global group | Windows Server |
| 4732 | A member was added to a security-enabled local group | Windows Server |
| 4735 | A security-enabled global group was changed | Windows Server |
| 4738 | A user account was changed | Windows Server |
| 4764 | A group’s type was changed | Windows Server |
| 4886 | Certificate Services received a certificate request | Certificate |
| 4887 | Certificate Services approved a certificate request and issued a certificate | Certificate |
| 5145 | A network share object was checked to see whether the client can be granted desired access. | Certificate |
Updated about 1 month ago
