What you can do | Insights
How Insights delivers value
Insights helps you:
- Uncover hidden privilege escalation paths
- Detect identity-based threats with context
- Improve your identity security posture with guided remediation
By connecting identity, privilege, and activity data across systems, Insights gives you the visibility to act with confidence.
The examples below use demonstration data to illustrate how Identity Security Insights works. Access to the Pathfinder portal, the Insights application and tile, and a connected identity source is required to explore similar views in your own environment.
The big picture
Before diving into specific investigations and examples, the Insights dashboard gives you a high-level view of your identity risk surface.
You’ll see key metrics like:
- Total number of accounts
- Accounts with high-risk privileges
- Detected paths to admin-level access
These tiles help you quickly assess where privilege is concentrated — and where to start investigating.
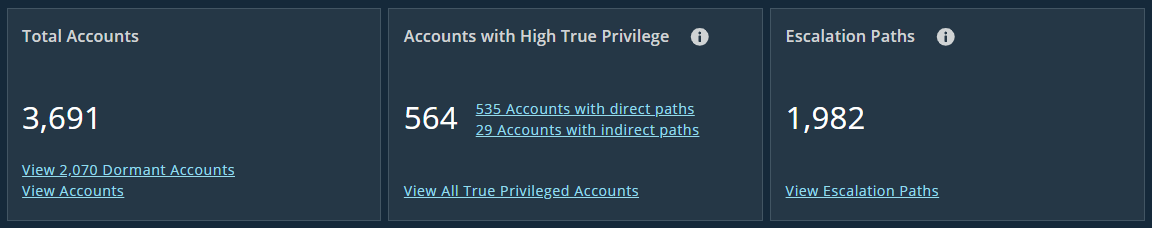
Key dashboard tiles highlight total accounts, high-privilege identities, and escalation paths.
Hidden privilege escalation paths
Most identity attacks don’t start with a privileged user, they end with one.
Insights helps you uncover how privilege can be reached, not just who’s privileged now, but who could be. These hidden escalation paths are often missed by traditional tools — but they’re critical to reducing identity risk.
Understand your identity blast radius
Some identities accumulate access across roles, groups, and systems creating a much larger blast radius if compromised.
Insights calculates True Privilege™ by analyzing:
- Assigned privileges: Roles, groups, or policies directly linked to an identity.
- Inherited access: Nested group memberships or role hierarchies.
- Shadow privileges: Indirect access paths, like policy attachments or trust relationships.
Together, these form a complete picture of what an identity can do, not just what it has on paper.
Key Concept: True Privilege™Most identity tools only analyze direct assignments. Insights calculates True Privilege™ by combining direct, inherited, and shadow access into a single view.
Investigate specific identities
Once you understand how privilege accumulates, the next step is to investigate who has the most access and how they got it.
Start by opening the Identities view from the dashboard. This table is sorted by True Privilege level, so you can quickly spot the riskiest users.
Select an identity to open the Identity Details page. In this example, we are selecting Amy Miller.
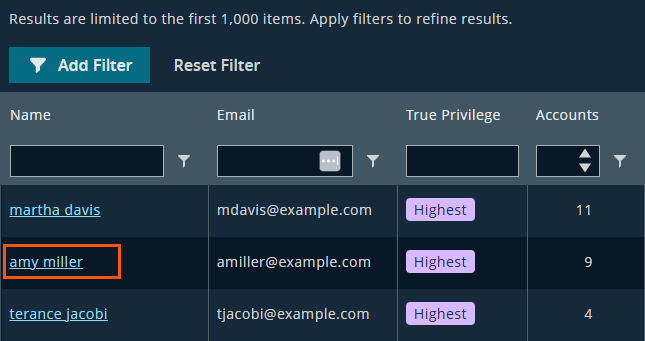
The Identities table groups accounts under a single identity, sorted by True Privilege level.
Visualize escalation paths
Once you’ve identified a high-risk identity, you can explore exactly how it could escalate to admin-level access.
From the Identity Details page, click View True Privilege Graph to see how this identity can escalate to admin-level access.
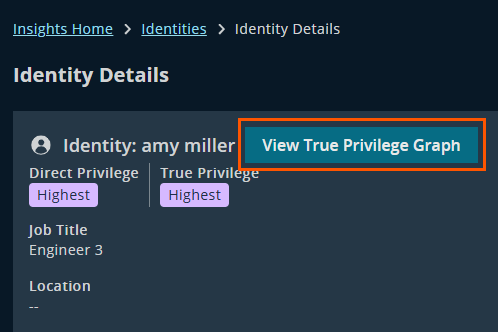
Access the True Privilege Graph from Identity Details.
The graph outlines all Paths to Privilege (both direct and indirect). In the example below, Amy Miller can escalate to the Global Administrator role through two layers of Azure Entra role assignments.
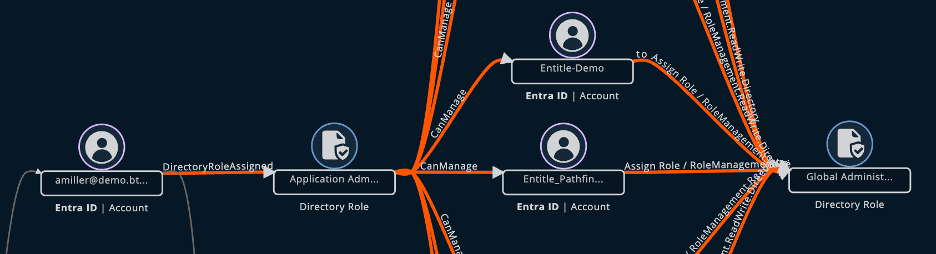
The True Privilege Graph highlights escalation paths discovered for a given identity.
Use the Entitlements table for deeper analysis
To view privilege relationships in a tabular format, open the Entitlements table — available as a standalone view or within the Identity Details page.
This table shows every instance where an entitlement (for example, a role assignment or policy attachment) is linked to an account.
- Select the graph icon in the Actions column to view a compact escalation graph for that entitlement.
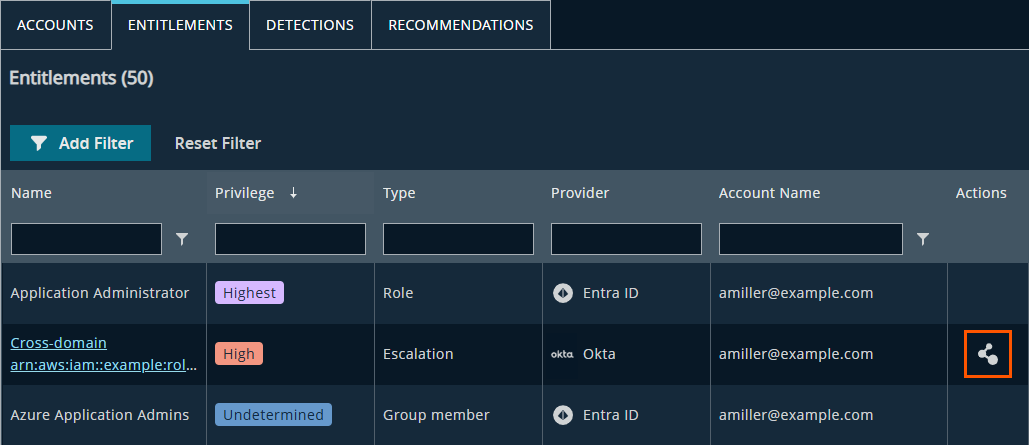
The graph icon in the Actions column will display a compact escalation graph.
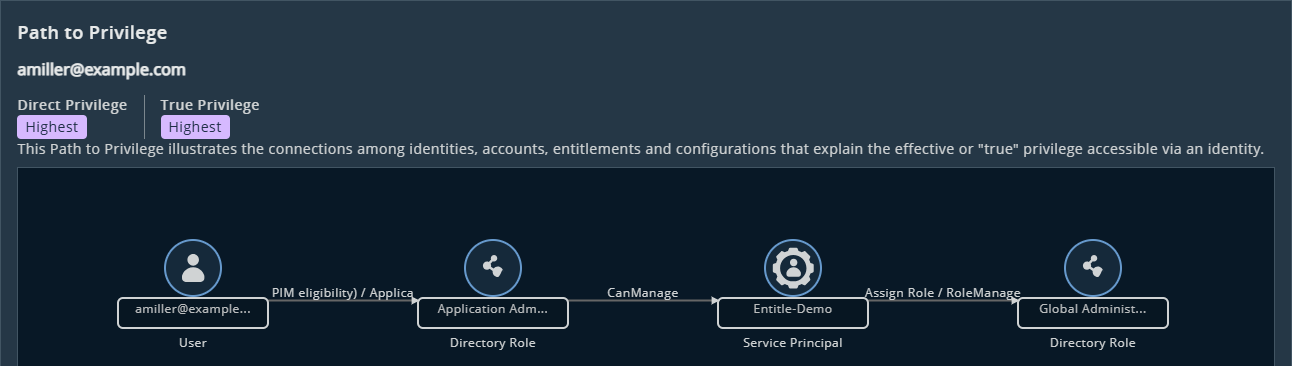
Isolated privilege escalation graph from the Entitlements page.
With the Identities and Entitlements views, you can:
- Investigate how specific users gain elevated access
- Visualize escalation paths in graph or table form
- Pinpoint and remediate risky privilege relationships
Identity-based threat detection and prioritization
Login anomalies are everywhere but without context, they’re just noise. Insights helps you focus on what matters by correlating:
- Who the user is
- How privileged they are
- What else they did
This lets you distinguish between harmless anomalies and real threats.
Example: A High-Risk Identity in Action
Start by navigating to the Identities page and selecting a high-risk identity. In this case, the identity’s True Privilege™ rating is Highest.
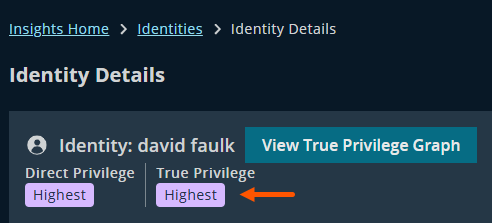
Identity with the highest True Privilege rating selected for investigation.
Open the Detections tab to view recent suspicious activity. In this example, the identity:
- Logged in from a Tor node: A sign of anonymized or evasive access
- Enrolled a new Okta IdP: Potentially introducing an unapproved identity provider
- Signed into Entra ID from a new country: Suggesting location-based risk
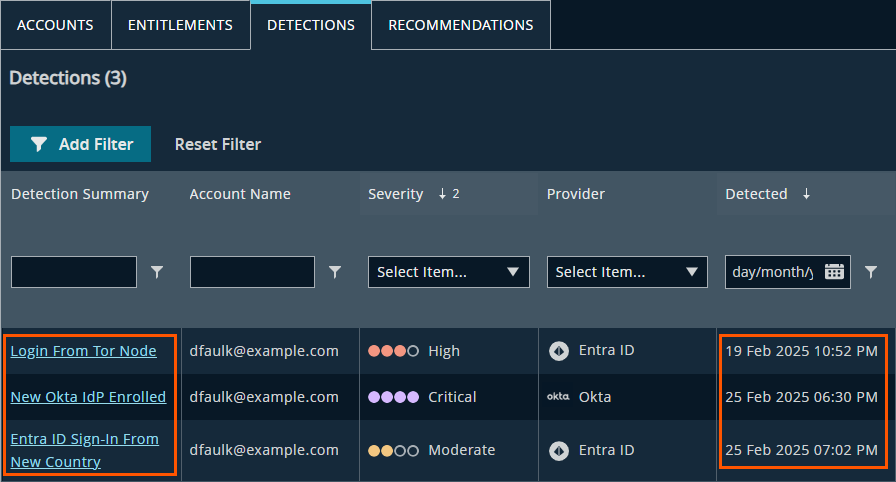
Detections table showing concerning behavior within a single week.
A week later, the identity continues to show suspicious behavior across multiple platforms.
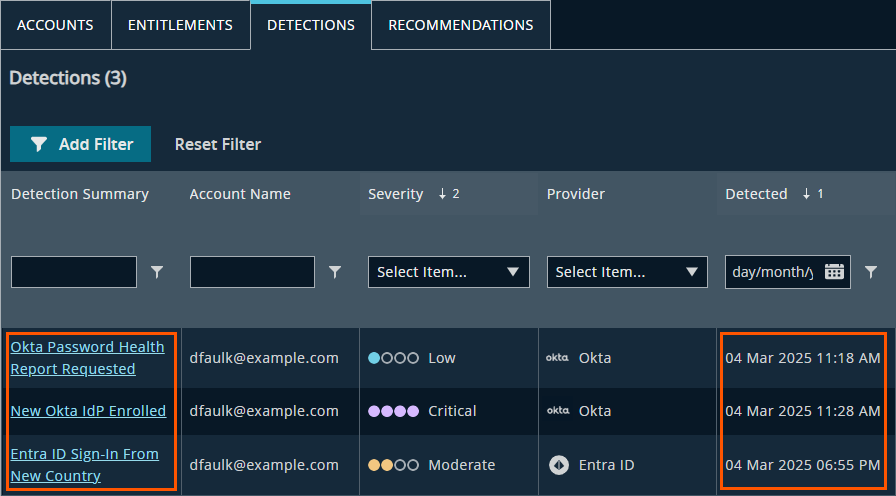
The user exhibits multiple signs of malicious behavior within a short time span, across multiple technology domains (Entra, Okta).
Each behavior is concerning on its own — but when chained together, the risk is greater than the sum of its parts.
Click into any detection row for full context, including timestamps, affected systems, and recommended actions.
What You Can Do
With Insights, you can:
- Correlate privilege and behavior to prioritize real threats
- Investigate suspicious identities across multiple platforms
- Act with confidence, knowing the full picture
Identity posture improvement
Reducing identity risk isn’t just about detecting threats — it’s about fixing what’s misconfigured. The Recommendations view helps you do exactly that.
Insights surfaces posture-related findings across your environment and provides guided remediation steps to address them.
Example: External Users with Privileged Roles
From the dashboard, open the Recommendations widget. In this example, we’re investigating the finding:
External Users with Privileged Entra ID Directory Role.
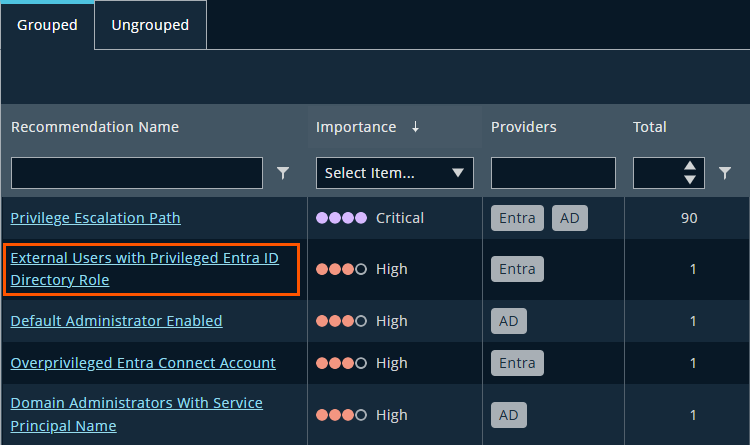
The Recommendations table contains a list of remediation activities that can improve your identity security posture.
Click into the finding to view:
- A summary of the issue
- Recommended remediation steps
- A list of affected identities
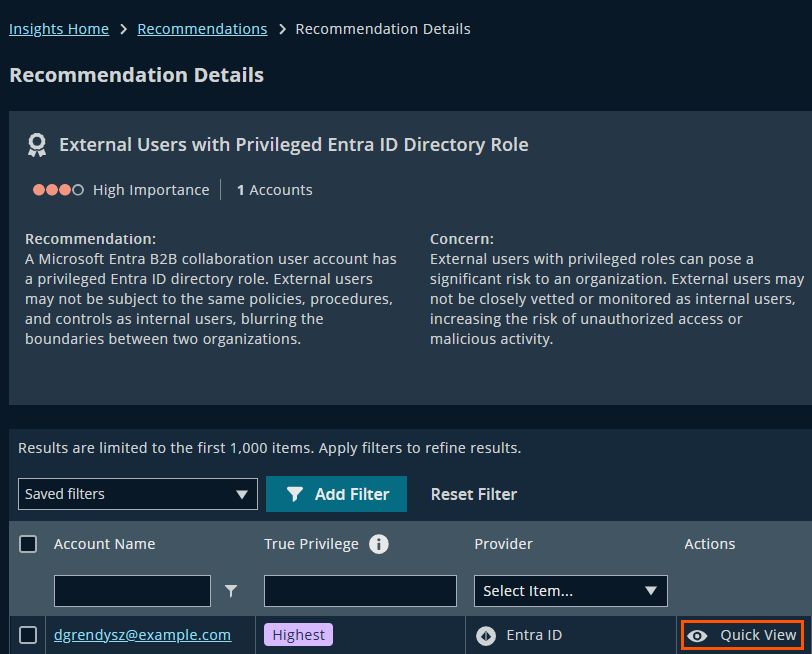
Recommendation Details outlines practical remediation steps to address the security misconfiguration or posture improvement.
Use Quick View in the Actions column to open a flyout with additional context.
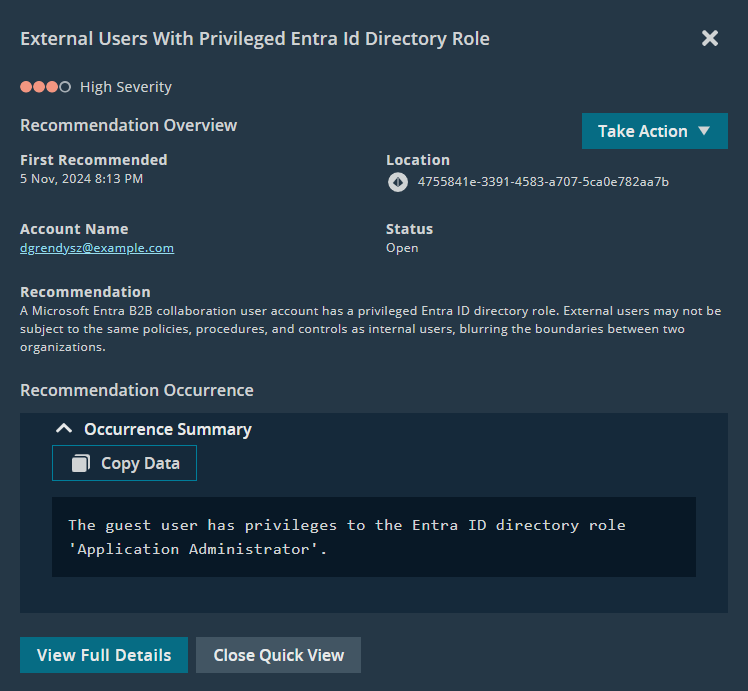
The Recommendation Details flyout provides additional context.
Take Action with Automation
Once you’ve identified a recommendation, you can streamline remediation using the Take Action button — but first, you’ll need to configure your integrations.
The dropdown includes options for:
- Triggering automation through your configured integrations (for example, ServiceNow, Teams, or Slack)
- Setting up new integrations via the Configure Webhook option
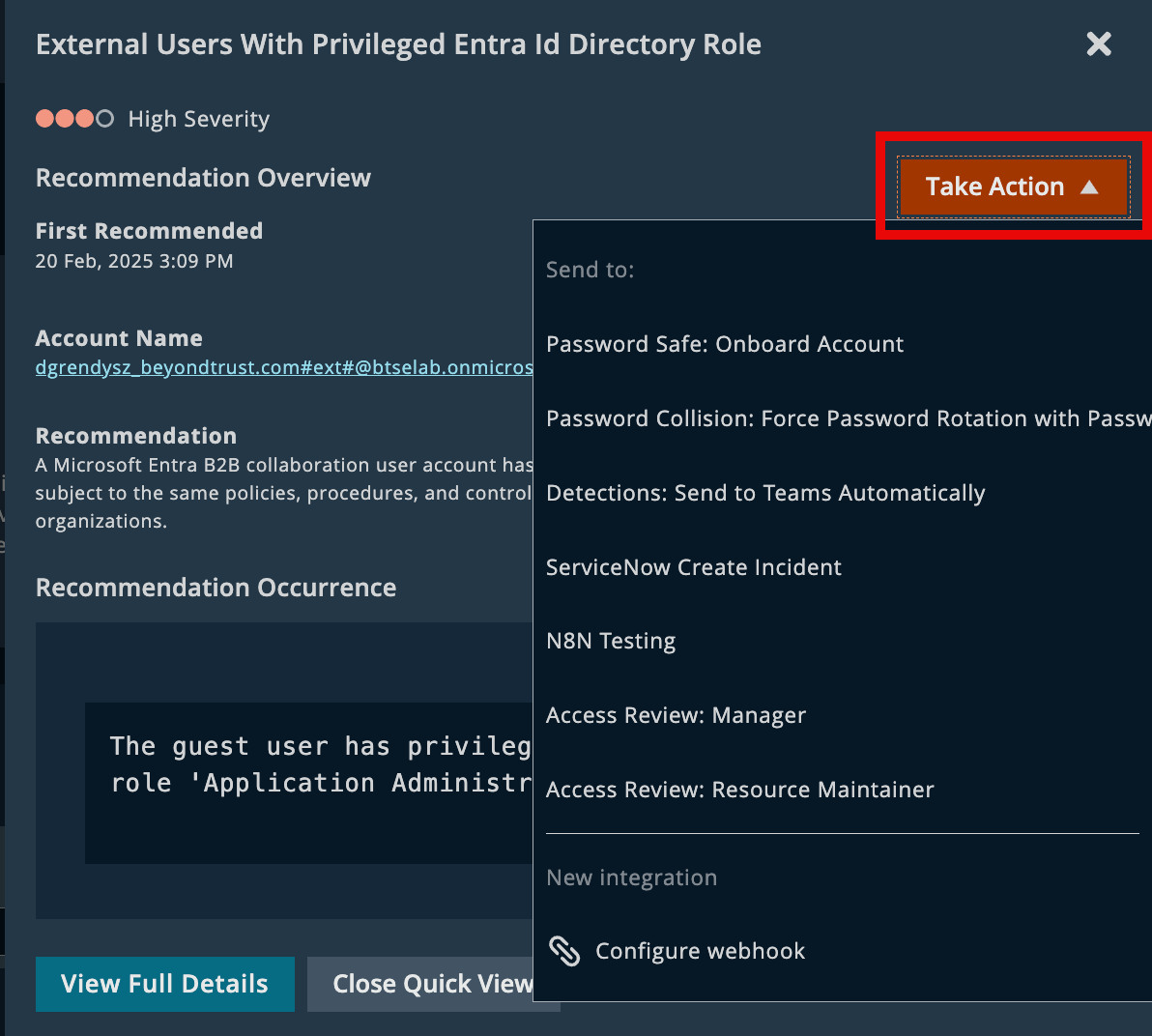
Set up integrations with notification apps, change management systems, or BeyondTrust products.
Note:Integrations must be configured before they appear in the Take Action menu. Supported destinations include ticketing systems, messaging platforms, SIEMs, and more.
What You Can Do
With Insights, you can:
- Identify posture gaps across identity systems
- Follow guided remediation for misconfigurations and risky setups
- Automate fixes using integrations with your existing tools
What you can do with Insights
Identity Security Insights gives you the visibility and context to take action — not just react.
Uncover hidden privilege escalation paths across cloud and on-prem environments
Detect identity-based threats with full context and correlation
Improve your identity posture through guided, actionable recommendations
Automate remediation using integrations with your existing tools
You can also:
- View identities stitched together from multiple sources
- Audit passwords and credential hygiene across platforms
- Explore tailored reports based on your role or use case
- Investigate all accounts across connected identity sources
- Track posture improvements over time
Whether you're investigating a threat, cleaning up privilege sprawl, or tightening posture, Insights helps you reduce identity risk with clarity and confidence.
System requirements
Identity Security Insights supports the following browsers:
- Microsoft Edge
- Google Chrome
- Apple Safari
- Opera
Updated about 1 month ago
