What's new in this release | Insights
For additional releases, see the full list of Identity Security Insights release notes.
February 3, 2026
✨ Enhancements
AI security detections & recommendations
Insights now provides 76 new detections and recommendations for security misconfigurations and risky behaviors across AI agents, models, and platforms, including Microsoft Azure, AWS Bedrock, ServiceNow, Salesforce, OpenAI Admin and Projects, GitHub, ChatGPT Enterprise, and Google.
What’s covered
- Agents with autonomous execution, excessive permissions, or role impersonation
- Unmanaged credentials, API keys, and OAuth tokens (unused, non-expiring, or over‑privileged)
- Knowledge bases with insufficient access controls or content filtering
- Weak or missing guardrails and logging configurations
- Governance gaps in tenant settings and environment controls
Where you'll see this
Navigate to AI Security to explore new findings across AI Agents and AI Inventory pages for 8 providers.
Use the Detections & Recommendations pages to filter by provider and severity/priority to review and prioritize.
By provider
Microsoft Azure (2 Detections, 22 Recommendations)
Microsoft 365 (2 Detections, 2 Recommendations)
| Detections | - Copilot Studio Trial License Assigned via License Change Event - Copilot Studio Trial License Assigned via Self-Signup Service |
| Recommendations | - Entra Authorization Policy Allows For Email-Based Sign-Ups - Active Copilot Studio Trial Licenses Assigned to Users |
Power Platform (20 Recommendations)
| Recommendations | - Dormant Power Platform Environment Detected - Broken Power Platform Connection Detected - Copilot Studio Agent Using Custom Connector - New Custom Power Platform Connector Detected - New Power Platform Admin Application Registered - Power Platform AI Agent Authentication Allows Non‑Entra ID Access - Power Platform AI Agent Publishing Channels Unrestricted - Power Platform App‑Based Access Control Disabled - Power Platform Dataverse Auditing Disabled - Power Platform Tenant Allows Developer Environment Creation by Non‑Admins - Power Platform Tenant Allows Environment Creation by Non‑Admins - Power Platform Environment Without Global Secure Access Enabled - Power Platform Guest User Access Not Restricted - Power Platform IP‑Based Cookie Binding Disabled - Power Platform IP‑Based Firewall Rules Disabled - Power Platform Tenant Allows Trial Environment Creation by Non‑Admins - Power Platform AI Agent Sharing Mode Set to Unlimited - Shared Power Platform Connection Detected - Unmanaged Power Platform Environment Detected - Power Platform Environment Has Excessive System Administrator Accounts |
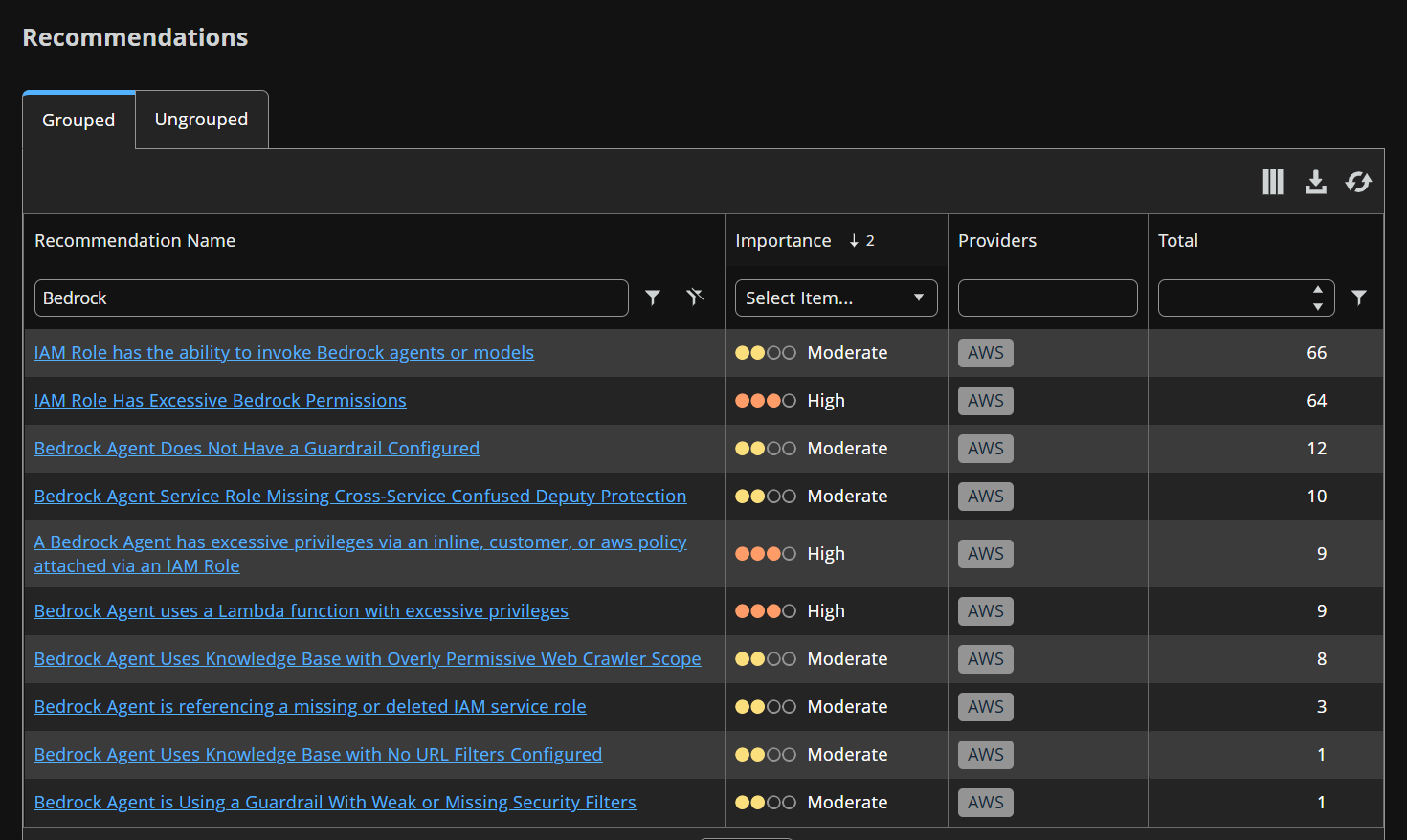
AWS Bedrock (6 Detections, 9 Recommendations)
| Detections | - Bedrock Guardrail Was Deleted - Bedrock Model Invocation Logging Configuration Was Deleted - Bedrock Long‑Term API Key Created Without Expiration Date - Bedrock Long‑Term API Key Created With Expiration Date - Bedrock Invocations Without Guardrails - Multiple Denied Bedrock Invocation Attempts |
| Recommendations | - Bedrock Agent Uses Knowledge Base with Overly Permissive Web Crawler Scope - Bedrock Agent Uses Knowledge Base with No URL Filters Configured - IAM Role Has Excessive Bedrock Permissions - Bedrock Agent Without Guardrails - Bedrock Agent With Weak Guardrails - Bedrock Agent Missing Confused Deputy Protection - Bedrock Agent Missing Service Role - Bedrock Custom Model Trains From Publicly Writable S3 Bucket - Bedrock Custom Model Outputs to Publicly Accessible S3 Bucket |
ServiceNow (11 Recommendations)
| Recommendations | - ServiceNow AI Agent set with autopilot execution - ServiceNow AI agent is deployed in the global scope - ServiceNow Agent is externally discoverable - ServiceNow AI agent tool uses role impersonation - ServiceNow AI agent tool accesses sensitive system tables - ServiceNow AI agent tool can decrypt stored secrets - A ServiceNow LLM model has logging disabled - A ServiceNow external AI model is enabled - A ServiceNow AI agent can perform live web searches - A public ServiceNow OAuth client allows password‑based token issuance - A ServiceNow AI agent can trigger a flow that runs as system |
Salesforce (10 Recommendations)
| Recommendations | - Agent Bot User Can Transfer Record Ownership - Salesforce Agent Bot User Has API Access Enabled - Salesforce AI Agent Has No Session Timeout Configured - Salesforce Site Allows All Framing - Salesforce Connected App Allows Access Without Admin Approval - Overly Permissive Salesforce Agent - Stale OAuth Token - Salesforce Agent Owns OAuth Token - Dormant Salesforce Agent - Salesforce Security Question Can Contain Password |
OpenAI Admin and Projects (7 Recommendations)
| Recommendations | - OpenAI Assistant Created Without Instructions - OpenAI Assistants API Scheduled for Deprecation - Assistant Using Outdated Model - Unused OpenAI User Project API Key - User With Unused OpenAI Admin API Key Detected - User with Multiple OpenAI Admin API Keys Detected - Multiple OpenAI Project API Keys Per User Detected |
GitHub (4 Detections, 2 Recommendations)
| Detections | - GitHub Copilot‑Initiated Pull Request Merged By User - GitHub Copilot Organizational Instructions Revoked - GitHub Copilot Repository Content Exclusion Revoked - GitHub Copilot Organizational Content Exclusion Revoked |
| Recommendations | - User with Dormant GitHub Copilot License Detected - User Administers GitHub Organization with Public Code Matching Enabled in Copilot |
ChatGPT Enterprise (2 Recommendations)
| Recommendations | - GPT with Excessive Sharing Permissions Detected - User Owns ChatGPT Project with Excessive Sharing Permissions |
Google (1 Recommendation)
| Recommendation | - GCP Principal can Execute Arbitrary Code |
Why it matters
These findings help identify over-privileged AI identities, unused credentials, uncontrolled access paths to sensitive data, and governance gaps that can lead to unauthorized access, data exposure, privilege escalation, and resource misuse across AI systems.
Updated 26 days ago
