Roles | EPM-L
What are roles?
Roles are a set of permissions, responsibilities, or actions assigned to a user, process, or system component in EPM for Linux that can control access, manage frameworks, and help define what entities can and cannot do in the software.
Available roles
| Role name | Typical responsibilities | Key functions | Access rights |
|---|---|---|---|
| sysadmin | Configures and manages the Endpoint Privilege Management system. Sets up users, groups, and roles. Defines and enforces privilege policies. Monitors system health and usage logs. | Policy creation and deployment. Integration with directory services (e.g., LDAP, Active Directory). System updates and maintenance. | Full access to all pages in EPM for Linux. Full rights (create, view, update, and delete) to all pages in EPM for Linux. |
| policyadmin | Designs and implements policies for managing privileges on Linux endpoints. Ensures compliance with organizational and regulatory requirements. | Defines rules for privilege elevation or restriction. Creates workflows for just-in-time access requests. Audits policies for effectiveness and compliance. | Full access to all policy management pages (Roles, Secure Users, Secure Groups, Command Groups, Host groups, Schedule Groups, Entitlement Reports) in EPM for Linux. Full rights (create, view, update, and delete) to the above pages in EPM for Linux. |
| auditor | Reviews logs and audit trails to ensure adherence to privilege policies. Identifies anomalies or potential misuse of privileges. | Analyzes user activity and system logs. Prepares reports for audits or security reviews. Flags potential policy violations for investigation. | Full access to all audit pages (Unified Search, Events, and Search and Replay) in EPM for Linux. Full rights (create, view, update, and delete) to the above pages in EPM for Linux. |
| accountadmin | Day-to-day use of the Linux system with role-appropriate privileges. Requests temporary privilege escalation when needed. | Manages users and role assignments. | Full access to the EPM-L Settings page. EPM for Linux. Full rights (create, view, update, and delete) to the above page in EPM for Linux. |
| apiuser | Connects the privilege management system to other tools and platforms. Ensures seamless functionality across systems. | Configures APIs for custom integrations. Synchronizes data with SIEM tools, ticketing systems, or identity providers. Troubleshoots connectivity or integration issues. | Minimal access to the EPM for Linux pages. |
| softwareadmin | Provides first-line support for users experiencing issues with privilege management. Facilitates access requests or resolves minor system issues. | Assists with privilege elevation requests if automated mechanisms fail. Escalates complex issues to administrators or policy managers. Educates users on the privilege management system. | Full access to the Installers page in EPM for Linux. Full rights (create, view, update, and delete) to the above pages in EPM for Linux. |
| Custom role | Organizations may define custom roles tailored to their specific needs. | Examples: DevOps Role: Manages privileges specific to development and operations teams. Incident Responder: Has temporary elevated access for responding to security incidents. |
How are roles useful?
Use roles to streamline operations, enforce security policies, and effectively manage access for your EPM for Linux users.
Important information about roles
When you edit an existing role, the edits apply to all users, hosts, and groups with the role.
Edit and assign allowed users (Who), command groups (What), hosts (Where), and schedule (When) to a role.
Each role can have zero to many relationships with each entity type. This is managed using the lists matching the appropriate entity. The following configuration sections are available when editing role assignments:
WHODefines which users the policy applies to. This item is divided into two user types, Submit Users and Run Users, and these lists contain the user entities.
Select Use Default Group and Working Directory to automatically populate the run users in a script block on the Script Policy page. Changing the block properties is not recommended.
WHATDefines which commands the policy applies to. This list contains the command entities.
WHEREDefines which hosts the policy applies to. This item is divided into two host type, Submit Hosts and Run Hosts, and these lists contain the host entities.
WHENDefines which schedule the policy applies to. This list contains the schedule entities.
Add a new role
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Select Start Policy Edits.
The Start Policy Edits page displays. - Enter a reason for the edits and select Continue Editing.
- Select Add Role.
The Roles panel displays. - Enter a Role name and Description.
- Click Create Role to create the role, or click Create And Edit the Role to configure it.
If you create the role, the role displays in the list on the Roles page.
If you create and edit the role, the Edit Role page displays. - Click Save.
The role and its configuration saves, and the role displays in the Role list on the Roles page.
View a role's details
View a snapshot of a role's configurations.
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to view.
- Click
 > View Role Details.
> View Role Details.
The Roles panel displays with a snapshot of the role's configurations.
Edit a role's general details
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page opens and the General tab displays.
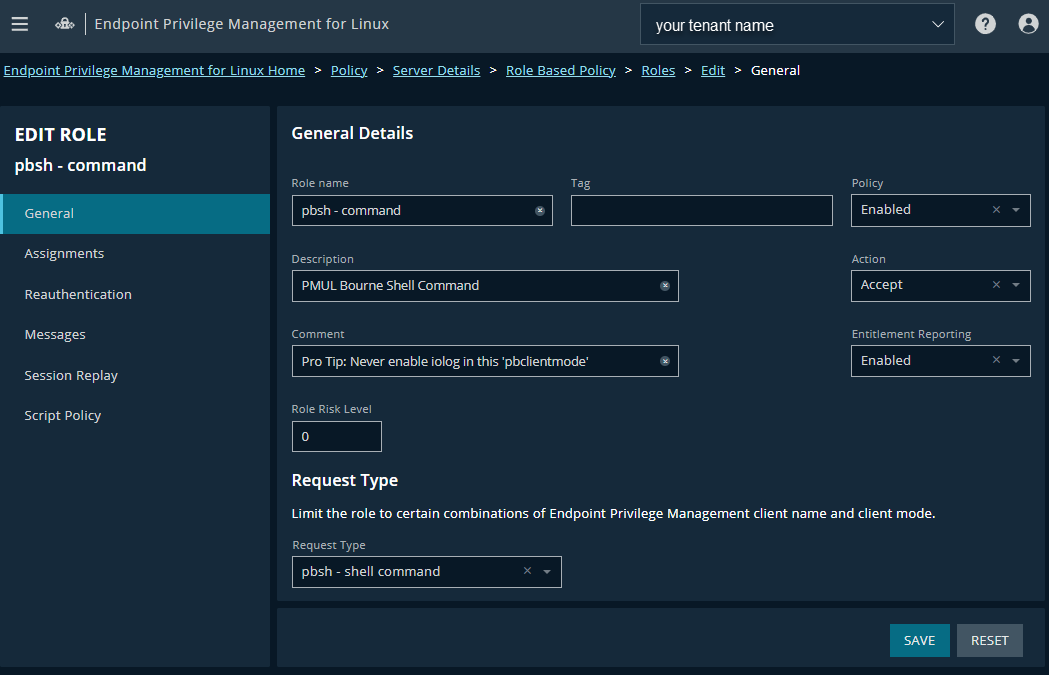
- Modify any of the following:
- Role name: A unique name.
- Tag: Tags function as a filter. Use them to sort through policy roles.
- Description: A brief description to identify the role.
- Comment: Comments are only visible to users with the Administrator role.
- Role Risk Level: The perceived risk level of the policy, from 0 - 50.
- Request Type: Allows the administrator to specify which request types this policy will apply to (for example, a policy might apply to commands issued only by pbrun invocations).
Use the dropdown to select the appropriate request type, or select Any. The default value is to allow any request type. - Policy: Enable or disable the role (default is Enabled).
- Action: Select whether this role triggers an Accept or Reject action (default is Accept).
- Entitlement Reporting: Enable or disable entitlement reporting on this role (default Disabled).
- Click Save.
Changes apply immediately to the role and affect all users, hosts, and groups with the role.
Edit role assignments
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page displays. - In the left panel, click Assignments.
The Assignments page displays. - Modify the Who (users and groups), What (command groups), Where (hosts), and/or When (schedule) for the role.
- Click Save.
The role assignments save and apply to all users, groups, and hosts with that role.
Edit a role's reauthentication
If configured, this feature requires users to reauthenticate themselves when this policy is invoked. Only one reauthentication method can be configured per policy. Most reauthentication options allow for customization of messages and prompts to be displayed to the user as well as logs. Reauthentication can be enabled in a number of configurations:
- None: Reauthentication is not required.
- Shared Secret: Create a shared secret value. The user must provide the secret to reauthenticate.
- Privilege Access Management (PAM): A number of PAM modules can be selected, or a custom one can be provided. Additionally, most options allow the user to configure where the authentication will occur.
Configure a Shared Secret reauthentication option
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page displays. - From the left panel, click Reauthentication.
The Reauthentication page displays. - In the Type dropdown, select Shared Secret.
- Enter the Shared Secret and confirm it.
- Enter a Reauthentication Prompt message, or use the default.
- Enter the Number of attempts (retries) before reauthentication locks the user out.
- Enter the Failure Message the user sees if reauthentication fails, or use the default.
- Enter the Log Message you want recorded in the log when reauthentication fails, or use the default.
- Click Save.
The reauthentication method and details save and are applied to all users, groups, and hosts with the role.
Configure a PAM reauthentication option
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page displays. - From the left panel, click Reauthentication.
The Reauthentication page displays. - In the Type dropdown, select PAM.
- Select the PAM Service to use for authentication.
- Select the Location to use, where the authentication happens.
If you select the Run Host option, you only need to complete the next two steps, then click Save.
- Select the User To Be Authenticated.
If you select Custom, enter a custom user name. - Enter a Reauthentication Prompt message, or use the default.
- Enter the Number of attempts (retries) before reauthentication locks the user out.
This may depend on the policies imposed by the authentication services that EPM for Linux accesses through PAM.
- In the Valid for (seconds) box, enter the length of time you want the reauthentication attempts cached before a login is required again.
- Enter the Failure Message the user sees if reauthentication fails, or use the default.
- Enter the Log Message you want recorded in the log when reauthentication fails, or use the default.
- In the Change requested by [loggedInUserName] field, enter a reason for the assignment or change.
- Click Save.
The reauthentication method and details save and are applied to all users, groups, and hosts with the role.
Add or edit a role message
Use messages to output a message to the user when this policy is processed. This field can use variables to provide a custom, context-specific message using the EPM for Linux template syntax of %\<variable>%. A few options are available using buttons to quickly insert the most popular options. Values can also be entered freely.
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page displays. - In the left menu, click Messages.
The Messages page displays. - Enter a message in the Accept and Reject Messages field.
- Optionally, click one of the standard messages to the right of the Accept and Reject Messages field.
- Click Save.
The message saves and is applied to all users, groups, and hosts with the role.
Edit a role's Session Replay settings
Use the session replay settings to preview the file location for your iologs, which log standard input, standard output, and standard error information that is associated with the current task request.
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page displays. - From the left menu, click Session Replay.
The Session Replay page displays. - Toggle the Session Replayon to save iologs logs.
The file location for your iologs displays in the Preview section.
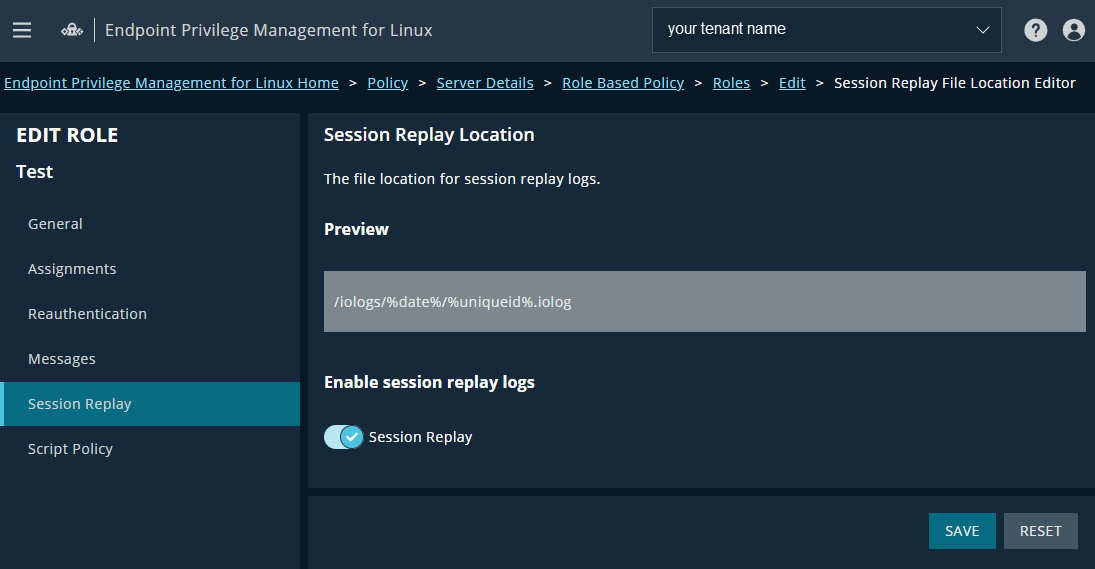
- Click Save.
Create or edit a custom script policy for a role
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to modify.
- Click
 > Edit Role.
> Edit Role.
The Edit Role page displays. - From the left menu, click Script Policy.
The Script Policy page displays. - Enter your script policy.
- Click Save.
The policy saves and is applied to all users, groups, and hosts with the role.
Duplicate a role
Duplicate a role to create a new role with all field values (including assignments of host groups, command groups, user groups, and schedule groups) retained from the original role.
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to duplicate.
- Click
 > Duplicate Role.
> Duplicate Role.
The Duplicate Role page displays with the General tab open by default. - Rename the Add a new role name. Duplicate role names are not permitted. By default, the name is Copy of (original role name).
Delete a role
WARNINGDeleting a role is an unrecoverable operation.
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Locate the role you want to delete.
- Click
 > Delete Role.
> Delete Role.
A confirmation message displays. - Click DELETE.
The role is immediately removed and all users, groups, and hosts with that role are no longer assigned to it.
Move roles
Change the ordering of roles on the Roles page using cut and paste options.
Roles can also be moved by selecting and dragging the role to the preferred location in the list.
- Sign into app.beyondtrust.io.
The BeyondTrust Home page displays. - Click
 > Endpoint Privilege Management for Linux > Policy.
> Endpoint Privilege Management for Linux > Policy.
The Role Based Policy page displays. - Click the Roles tile.
The Roles list displays.
- Select a role in the list and select
 > Cut Role.
> Cut Role. - Navigate to the location in the Roles list.
- Select
 > Paste Role Above or
> Paste Role Above or  > Paste Role Below.
> Paste Role Below. - To cancel, select Clear Clipboard.
Updated 19 days ago
