Policy management | EPM-L
Create, edit, and modify policies, users, groups, and endpoints.
What is a role-based policy?
A role-based policy (RBP) defines which users can use commands, and when they can perform these actions on endpoints. You can create, edit, and delete policies on managed policy servers.
How is a role-based policy useful to my organization?
By automating and centralizing access control, our role-based policies improve security posture, reduce administrative overhead, and ensure compliance, making them an essential tool for organizations managing privileged access.
Policy workflow
To create and deploy a policy, follow this workflow:
- Ensure you've created and downloaded your installer packages, and deployed them to your endpoints.
- Create and configure roles that you will apply to multiple secure users.
- Create your secure users and secure groups.
- Assign configured roles to your secure users and secure groups.
- Create your command groups to define the policy's allowed and rejected commands.
- Create your host groups to determine where to apply the policy.
- Schedule your secure, command, and host groups to manage when to apply the policy.
The Role Based Policy page
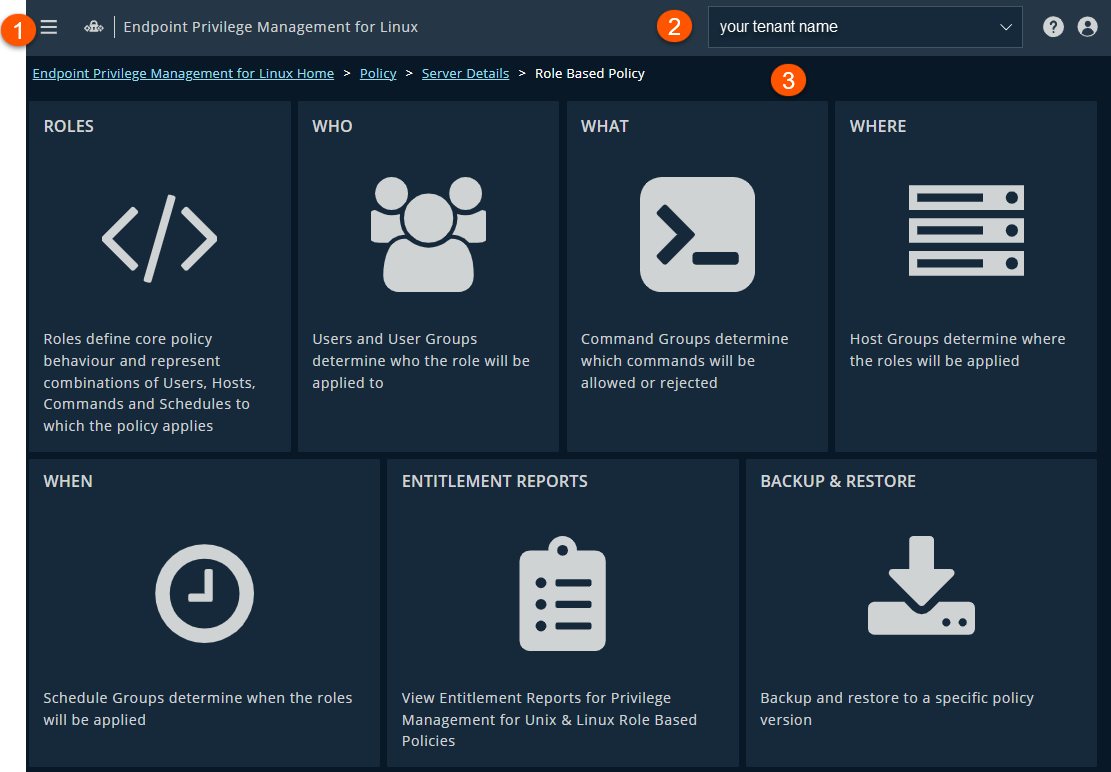
- Administration menu: Access Pathfinder administration pages if you are assigned as an administrator.
- Header: Select a tenant or Administration from the menu, manage your profile, and change the display theme.
- Select a tile to access policy settings: Roles, Who, What, Where, When, Entitlement reports, Backup and Restore.
Updated 3 months ago
