Policy rules for Endpoint Privilege Management for Unix and Linux settings and policy rules | AD Bridge
Endpoint Privilege Management for Unix & Linux Servers settings and policy rules
This page describes how to use Endpoint Privilege Management for Unix & Linux Servers to configure policy settings to support Endpoint Privilege Management for Unix & Linux Servers.
Using the Endpoint Privilege Management for Unix & Linux Servers Rule Editor and configuration file, you can create and change simple Endpoint Privilege Management for Unix & Linux Servers policy rules.
Using the Rule Editor, you can enable or disable specific rules.
Endpoint Privilege Management for Unix & Linux Servers policy data can be exported to a local file, edited manually, and imported to Active Directory from a local file.
Policy rules data
The policy data is saved to a .csv file. When the client-side agent applies the data from this Group Policy setting to an Endpoint Privilege Management for Unix & Linux Servers Policy Server, the resulting collection of policy rules data will be at the following location: /etc/pb/Policy.csv.
If more than one Group Policy Object (GPO) has defined Policy Rules Data in the Active Directory policy hierarchy that applies to a given Endpoint Privilege Management for Unix & Linux Servers Policy Server computer, the client-side agent determines which of all the policy settings should be applied based on targeting (filtering by host, system type), and precedence (link order and hierarchy). The resultant set of policy rules data is combined and written to the final /etc/pb/Policy.csv file to represent the union of all rules.
Priority of rules within a GPO
Priority of rules within a GPO is defined in the Endpoint Privilege Management for Unix & Linux Servers GPO Properties dialog box. If multiple GPOs containing Endpoint Privilege Management for Unix & Linux Servers policy settings are applicable to an Endpoint Privilege Management for Unix & Linux Servers Policy Server, the processing order of the GPOs is defined by their relative position in the Active Directory hierarchy. The closer a GPO is to the Endpoint Privilege Management for Unix & Linux Servers Policy Server, the higher priority it has.
Create or modify a PMUL servers rule
Before Endpoint Privilege Management for Unix & Linux Servers rules can be deployed, an Endpoint Privilege Management for Unix & Linux Servers configuration file must be defined.
- In the Create Policy Rules Properties dialog box:
- To create a new Privilege Management for Unix & Linux Servers rule, click Add.
- To modify an existing Privilege Management for Unix & Linux Servers rule, select the rule and then click Edit.
- Enter a name for the rule.
- On the Conditions tab, select the rule type radio button. Choose from Accept or Reject.
- To add a user or group to be managed by the rule, click Add Submitter.
- Select a type of user or group to add. If adding an Active Directory user or group, click OK, enter the name of the user or group, and then click OK.
- If adding a local user or group, type the name in the box and click OK.
- Click Add Command and select from the following:
- Submit Command: Enter the command as a submitter would type it. You can include arguments. If you want to allow the user to include additional arguments with the command at runtime, check the Allow Argument box.
- Run Command: Enter the command that runs when a submitter types the Submit Command. You can include arguments.
- Run Command the same as submit: Check the box when you want the command the same as Submit Command.
- Run Command the same as Submit: If this is not selected, you can effectively create an alias for a command for submitters.
- Save As User Command: Check the box to use the command with other PBUL rules.
- Click OK to add the command.
You can remove commands that you add, but you cannot remove the default commands provided with AD Bridge.
- Select the commands that you want to run when the rule is activated.
- Click >> to move the command to the Current Active Commands list.
- To remove the command from the Current Active Commands list, click <<.
- Select the computers that will be Submit Hosts (commands in the rule are run by submitters) and Run Hosts (commands entered by submitters are run).
- Run Host is the same as Submit Host: (Optional). The computer used as the Run Host must be the same computer used as the Submit Host; check the box.
- Run Host pool is the same as Submit Host pool: (Optional). The selected computers are used as both Submit Hosts and Run Hosts; check the box.
- Submit Hosts and Run Hosts: In the Submit Hosts or Run Hosts areas, click Add. Type a computer name or click ADD to search Active Directory for a computer. You can enter multiple computer names separated by commas.
- (Optional). You can limit when the rule is active to between specified dates or times of day, delay when a rule will become active, or specify an expiration for a rule. For example, to make the rule active only between 8:00AM and 7:00PM, check the Time Start box and enter 8:00:00 AM. Then check the Time End box and enter 7:00:00 PM.
- Optional. Click the Environment tab, and then enter information for the following:
- Run User: Enter the user account to use to run the commands in this rule on the Run Host. The default account is root. If you change the account, ensure that the account has the permissions necessary to run the commands in the rule and that the account exists on the Run Hosts.
- Preserve Environment : (Optional). List any Unix or Linux environment variables that you want to remain unchanged by the effect of this rule when commands are run. Environment variables can alter which libraries are loaded for the session.
- Define Environment: (Optional). Enter the names and values of any Unix or Linux environment variables that you want to explicitly define when this rule is used to run commands.
- Enable Keystroke Logging: (Optional). To enable keystroke logging, check this box. If selected, by default, keystrokes are logged to a separate log file for each command instance. Advanced administrators can change the path and file name format of these log files by changing the pb.conf file. If the default pb.conf file is used, keystroke log files are saved to file names beginning with /var/adm/pb.iolog.
- Authenticate User: (Optional). To display a password prompt to the user and authenticate the user before a command is run, check this box. Select where authentication occurs: Submit Host, Run Host, or the Master Server. This setting can provide additional protection against unauthorized users if an authorized user neglects to lock their computer before stepping away from it.
- Idle Timeout: (Optional). To force a timeout so that a long-running command cannot continue indefinitely, check this box and enter the maximum number of minutes. For example, if you are configuring rules that allow users to create a shell session using pbsh or pbksh, you can use this setting to ensure that this elevated access eventually expires if idle.
- Click OK.
Change the priority of Endpoint Privilege Management for Unix and Linux servers rules
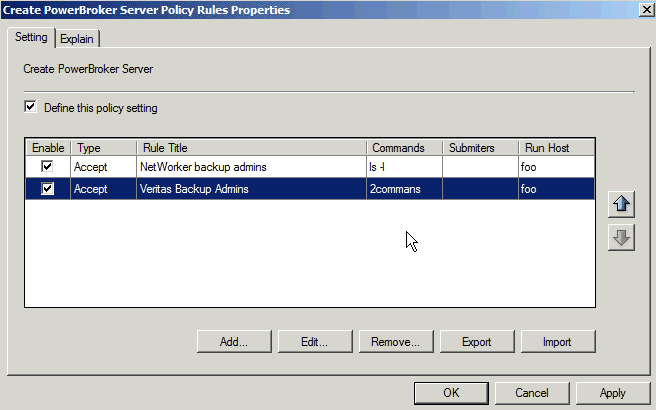
The priority of Endpoint Privilege Management for Unix & Linux Servers rules in a GPO is determined by their order in the list on the Create PowerBroker Server Policy Rules Properties dialog box.
To change the priority of Endpoint Privilege Management for Unix & Linux Servers rules, on the Create PowerBroker Server Policy Rules Properties dialog box, select a rule and click one of the arrows to move the rule to a higher or lower priority.
Disable or enable Endpoint Privilege Management for Unix and Linux servers rules
You can enable and disable Endpoint Privilege Management for Unix & Linux Servers rules from the Create PowerBroker Server Policy Rules Properties dialog box. Check the Enable box to enable the rules you want to be active. Clear the Enable box to disable a rule.
Export, manually edit, and import PMUL rules
You can export Endpoint Privilege Management for Unix & Linux Servers rules from Active Directory to a local file, manually edit the rules, and then import the edited rules from a local file into Active Directory.
Export Endpoint Privilege Management for Unix & Linux Servers rules to a local file
You can export Endpoint Privilege Management for Unix & Linux Servers rules from Active Directory to a local file so that you can manually edit the rules or to archive the rules.
To export Endpoint Privilege Management for Unix & Linux Servers rules from Active Directory to a local .csv file:
- On the Create PowerBroker Server Policy Rules Properties dialog box, select the rules that you want to export.
Use the CTRL key to select more than one rule.
- Click the Export button.
- Indicate where to save the .csv file, enter a name for the file, and click Save.
Import Endpoint Privilege Management for Unix & Linux servers rules to Active Directory
If you manually edited PBUL rules or previously saved PBUL rules to a .csv file, you can import those rules to Active Directory.
To import PBUL rules from a local .csv file to Active Directory:
- On the Create Server Policy Rules Properties dialog box, click the Import button.
- Select a local .csv file from which to import data and click Open.
- Click Apply to save the data to Active Directory.
To ensure that rules are not inadvertently overwritten, rules in the .csv file that you import will not overwrite existing rules, even if the rule names are the same. If you want a rule that you imported to replace an existing rule, select the existing rule and click Remove.
Updated 19 days ago
