GROUP POLICY SETTINGS USER GUIDE | AD Bridge
What are AD Bridge group policy settings?
AD Bridge enables you to configure group policy settings for computers running Linux and Unix. AD Bridge includes more than 100 policy settings that are designed to manage non-Windows computers.
All the policy settings are integrated with the Microsoft Group Policy Management Editor, part of the Microsoft Group Policy Management Console (GPMC).
How are AD Bridge group policy settings useful?
You can use a group policy setting to control who can use sudo for access to root-level privileges by specifying a common sudoers file for target computers. You could create an Active Directory group called SudoUsers, add Active Directory users to the group, and then apply the sudo group policy setting to the container, giving those users sudo access on their Linux and Unix computers. In the sudoers file, you can specify Windows-style user names and identities. Using a group policy setting for sudo gives you a powerful method to remotely and uniformly audit and control access to Unix and Linux resources.
How to I access AD Bridge group policy settings?
AD Bridge stores its Unix and Linux policy settings in Group Policy Objects (GPOs) in the same location and in the same format as the default GPOs in Windows Server: in the system volume (sysvol) shared folder. Unix and Linux computers that are joined to an Active Directory domain receive GPOs in the same way that a Windows computer does.
AD Bridge Group Policy Agent
The AD Bridge Group Policy Agent is automatically installed when you install the AD Bridge agent.
To apply and enforce policy settings, the AD Bridge Group Policy Agent runs continuously as a daemon processing user policy and computer policy:
- Computer policy processing: The agent traverses the computer's distinguished name (DN) path in Active Directory.
- User policy processing: Occurs when a user logs on; the agent traverses the user's DN path in Active Directory.
The AD Bridge Group Policy Agent connects to Active Directory, retrieves changes, and applies them once every 30 minutes, when a computer starts or restarts, or when requested by the GPO refresh tool.
The AD Bridge Group Policy Agent uses the computer account credentials to securely retrieve policy template files over the network from the domain’s protected system volume shared folder.
The AD Bridge Group Policy Agent applies only AD Bridge Group Policy settings: those in the Unix and Linux Settings collection in the Group Policy Management Editor; it does not apply any other group policy settings that may be specified in the GPOs.
Inheritance
There are two types of policy settings:
- File-based: File-based policy settings, such as sudo and automount, typically replace the local file. File‑based policy settings are not inherited and do not merge with the local file.
- Property-based: Property-based policy settings are inherited, meaning that the location of a GPO in the Active Directory hierarchy can affect its application. Property-based settings merge with local policy settings. Local policy settings are not replaced by property-based settings.
Most policy settings are based on properties.
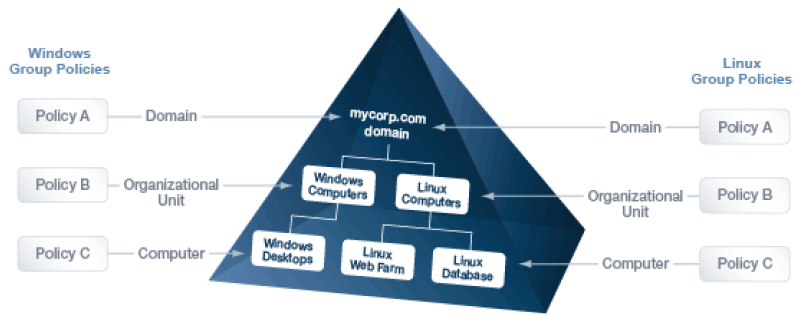
Filter by target platform
You can set the target platforms for a GPO. The GPO is applied only to the platforms that you select. You can select the target platforms by operating system, distribution, and version. For example, you can target a GPO at:
- Only computers running SUSE Linux Enterprise Server
- A mixture of operating systems and distributions, such as Red Hat Linux, Sun Solaris, and Ubuntu Desktop
Some policy settings, however, apply only to specific platforms.
For more information, see the Help for the policy setting that you want to use.
| Target Platforms | ||
|---|---|---|
| CentOS Linux | Debian Linux | Fedora Linux |
| IBM AIX | OpenSUSE Linux | Red Hat Linux |
| Red Hat Enterprise Linux (ES and AS) | Sun Solaris | SUSE Linux |
| SUSE Linux Enterprise Desktop | SUSE Linux Enterprise Server | Ubuntu Linux |
Go to the Target Platform Filter policy to select targets for the GPO.
AD Bridge GPO update tool
Use the AD Bridge GPO update tool to force a computer to pull the latest version of group policy settings. The tool includes the following options:
| Option | Description | Example |
|---|---|---|
| help | Displays the help for the tool . | gpupdate --help |
| verbose | Displays information on the policies that were added, updated, removed. | gpupdate --verbose |
| rsop | Displays the Resultant Set of Policy (RSoP) information. The RSoP is the set of group policy settings the group policy agent will apply, either when it runs as part of periodically applying settings or when gpupdate is run. gpupdate --rsop does not apply group policy settings. | gpupdate --rsop |
| no-pager | Do not page output. By default, gpupdate automatically pages output using the command set in the PAGER environment variable. | gpupdate --no-pager |
The --verbose command provides details on the group policy extensions being run, whether settings were added, modified or removed and whether those changes were successfully applied.
Run the following command at the shell prompt: /opt/pbis/bin/gpupdate --verbose
The command returns a success or failure result similar to the following:
- On success: GPO Update succeeded
- On failure: GPO Update was unsuccessful, error code <code> (<error message>)
On target computers, AD Bridge stores policy settings in /var/lib/pbis/grouppolicy.
Manage Group Policy Objects (GPOs)
You can create or edit Group Policy Objects (GPOs) and configure policy settings for computers running Linux and Unix by using the Group Policy Management Console (GPMC).
To manage a GPO, you must log on as a member of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security group.
You can download the Microsoft Group Policy Management Console at https://www.microsoft.com/en-us/downloads/.
To create a GPO using GPMC:
- Navigate to Start > Administrative Tools and click Group Policy Management.
- Right-click the organizational unit, and then select Create a GPO in this domain, and Link it here.
- Type a name for your GPO.
- Click OK.
- Right-click the GPO that you created, and then click Edit.
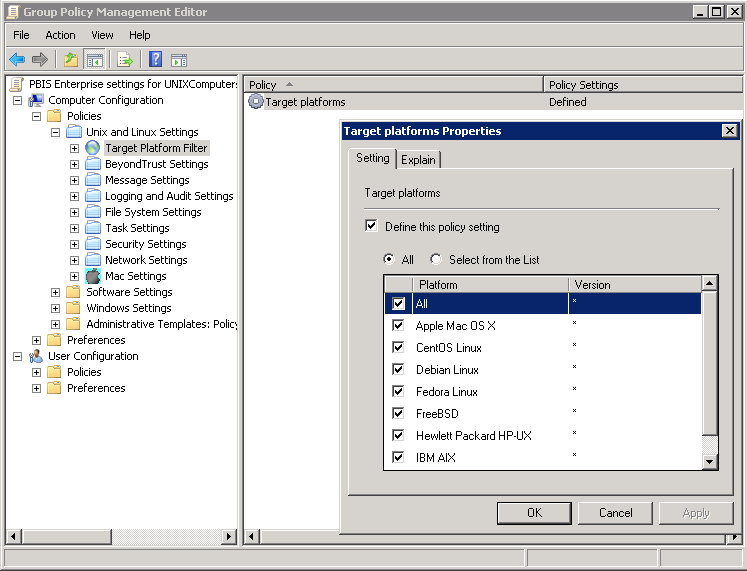
The AD Bridge Group Policy settings are in the Unix and Linux Settings collection. For more information about each policy, see the Help for the policy setting that you want to use.
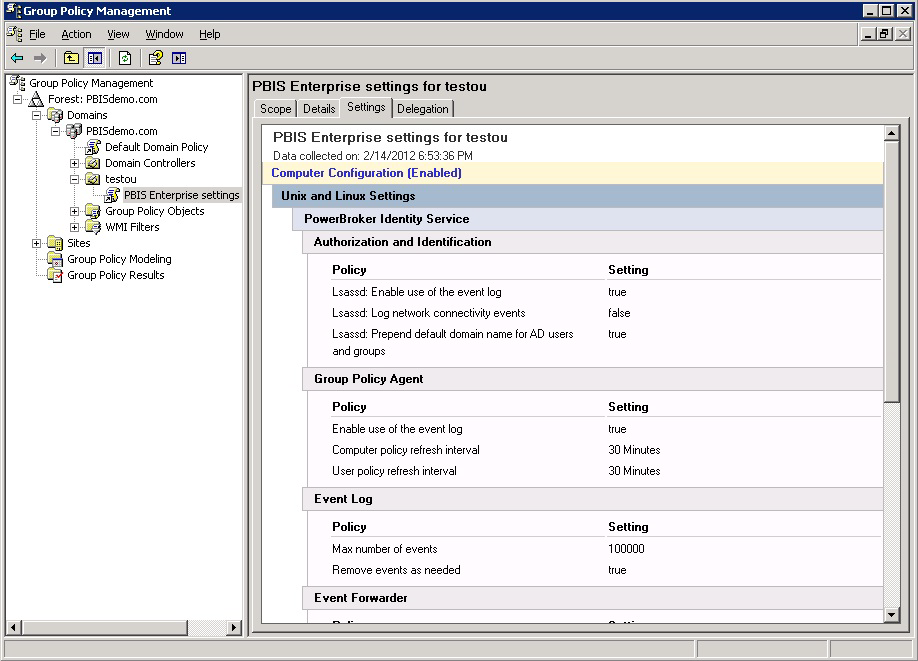
View a report on a GPO's policy settings
In GPMC, you can view details on AD Bridge policy settings defined in a GPO. Go to the GPO and select the Settings tab. The image depicts an example.
Walkthrough: create a sudo GPO
You can create a GPO to specify a sudo configuration file for target computers. Sudo, or superuser do, allows a user to run a command as root or as another user. You can use this GPO to control sudo access in a centralized and uniform way.
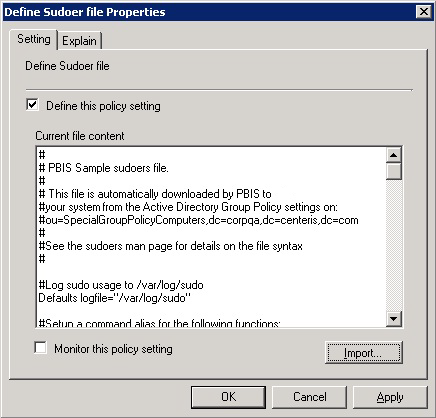
The sudo configuration file is copied to the local computer and replaces the local sudoers file. A sudo file can reference Active Directory users and groups. For more information about sudo, see the man pages for your system.
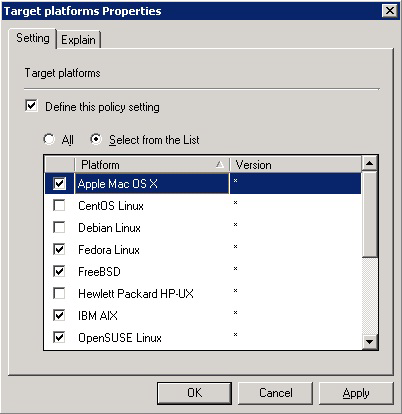
When you define the GPO, you can also set its target platforms. The GPO settings are applied only to the operating systems, distributions, and versions that you choose.
The AD Bridge entries in your sudoers file must conform to the rules set in "Configure Entries in Your Sudoers Files" in the AD Bridge Administration Guide.
Create a sudo GPO
To create or edit a GPO, you must log on as a member of the Domain Administrators security group, the Enterprise Administrators security group, or the Group Policy Creator Owners security group.
-
In the Group Policy Management Editor, expand either Computer Configuration or User Configuration, expand Policies > Unix and Linux Settings.
-
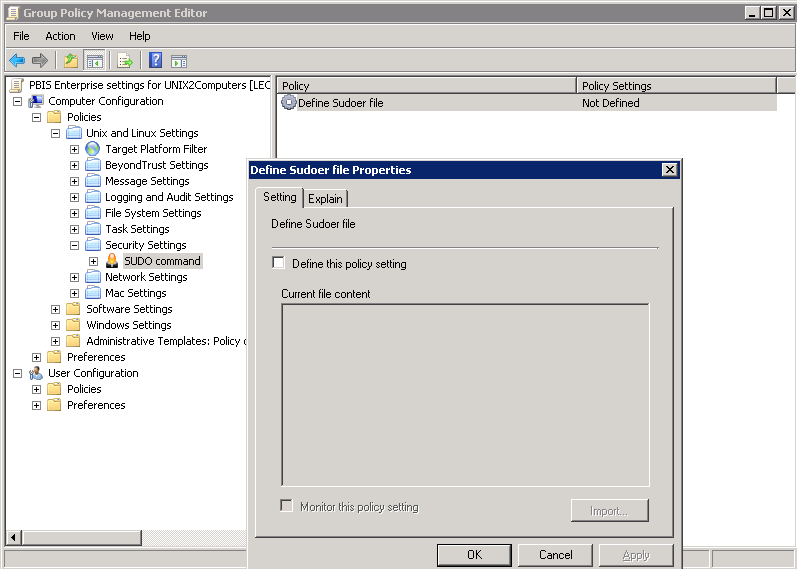
Expand Security Settings, and then select SUDO command.
-
Double-click Define Sudoer file.
-
Check the Define this Policy Setting box, and then in the Current file content box, type your commands. Or, to import a sudo configuration file, click Import.
-
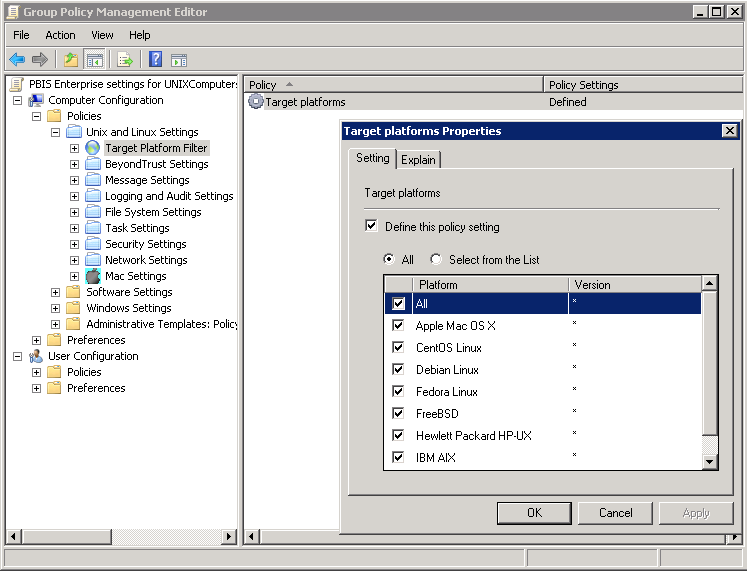
Select Target Platform Filter.
-
Double-click Target platforms.
-
To target all the platforms, select All. To choose platforms, click Select from the List, and then select the platforms.
Test the sudo GPO
After you set the sudo GPO, you can test it on a target computer. The target computer must be in a cell associated with the organizational unit where you linked the sudo GPO.
-
On a target Linux or Unix computer, log on as an administrator and execute the following command to force AD Bridge Group Policy settings to refresh:
/opt/pbis/bin/gpupdate -
Check whether your sudoers file is on the computer:
cat /etc/sudoers
The location of the sudoers file varies by platform. For example, on Solaris it is in /opt/sfw/etc or /opt/csw/etc. On other platforms, it is in /usr/local/etc.
- Log on to the Unix or Linux computer as a regular user who has sudo privileges as specified in the sudoers configuration file.
- Try to access a system resource that requires root access using sudo. When prompted, use the password of the user you are logged on as, unless targetpw is set in the sudoers file. Verify that the user was authenticated and that the user can access the system resource.
Test sudo security
- Log on as a user who is not enabled with sudo in the sudoers file that you used to set the Group Policy Object (GPO).
- Verify that the user cannot perform root functions using sudo with their Active Directory credentials.
Updated about 1 month ago
