Identity Security Insights 25.07
8 months ago
July 3, 2025
🆕 New features
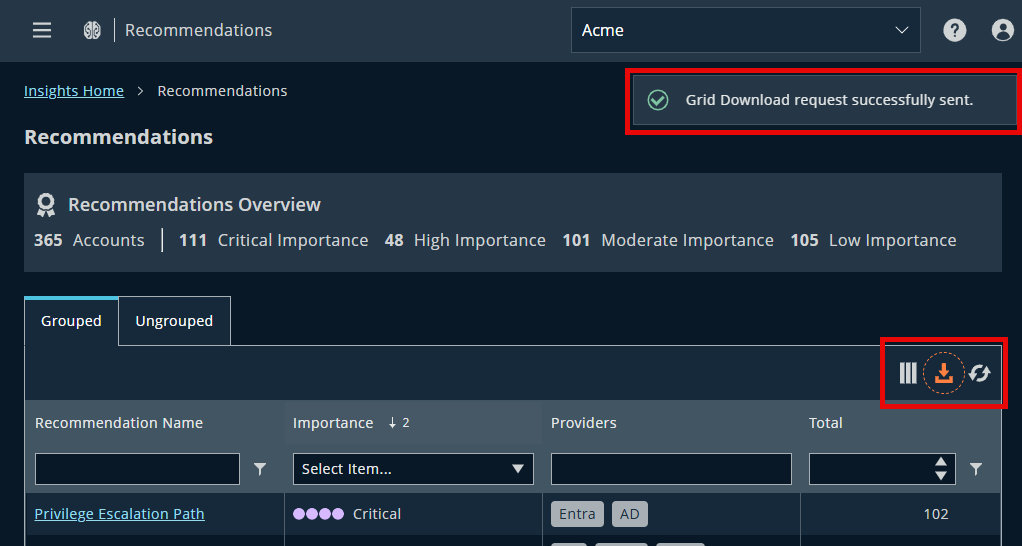
Full grid downloads for Detections and Recommendations
You can now download the entire dataset from the Detections and Recommendations grids, across both grouped and ungrouped views—enabling more complete exports for analysis and reporting.
Key Improvements
- No row limit: Export full results, regardless of dataset size.
- Background processing: Downloads are prepared in the background, allowing you to continue navigating the product.
- Session-aware delivery: If you're logged out during processing, the download will resume automatically once you log back in (within a short period).
For more information, see Recommendations and Detections.
New detections and recommendations for Active Directory, AWS, Privileged Remote Access, and Remote Support
These additions help identify risky configurations and excessive privileges across AD, AWS, PRA, and RS environments.
Active Directory
- Computer Account With Unconstrained Delegation Enabled (Recommendation)
Flags computer accounts with unconstrained delegation, which could allow attackers to impersonate users and request service tickets using cached credentials. - Suspicious Computer Account Creation (Detection)
Detects 4741 events that may indicate unauthorized creation of computer accounts, potentially signaling attacker persistence or lateral movement.
Amazon Web Services (AWS)
- A potentially highly privileged IAM policy has been attached to an IAM user (Detection)
Detects when a potentially high-privilege IAM policy is attached to a user, which could lead to privilege escalation or unintended access.
Privileged Remote Access (PRA)
- Default Jump Item Roles Are Resulting in Excessive Admin Jump Item Access in PRA (Recommendation)
Identifies accounts with excessive admin access via default roles, increasing the risk of unauthorized access and poor role segregation. - Unassigned Jump Item Roles Are Resulting in Excessive Admin Jump Item Access in PRA (Recommendation)
Highlights accounts with admin access through unassigned roles, which act as fallbacks and may unintentionally grant broad privileges. - Vendor Account Has Been Granted Broad Admin Access via 'unassigned' Role (Recommendation)
Detects vendor accounts with admin access through unassigned roles, potentially exposing sensitive systems to external users. - Vendor Account Has Been Granted Broad Admin Access via 'default' Role (Recommendation)
Flags vendor accounts with admin access via default roles, which may unintentionally grant elevated privileges without explicit assignment.
Remote Support
- Default Jump Item Roles Are Resulting in Excessive Admin Jump Item Access in RS (Recommendation)
Identifies excessive admin access in RS via default roles, which can lead to unauthorized access and lack of role control. - Unassigned Jump Item Roles Are Resulting in Excessive Admin Jump Item Access in RS (Recommendation)
Highlights admin access granted through fallback roles in RS, increasing the risk of privilege misuse.
For more information, see Recommendations and Detections.
✨ Enhancements
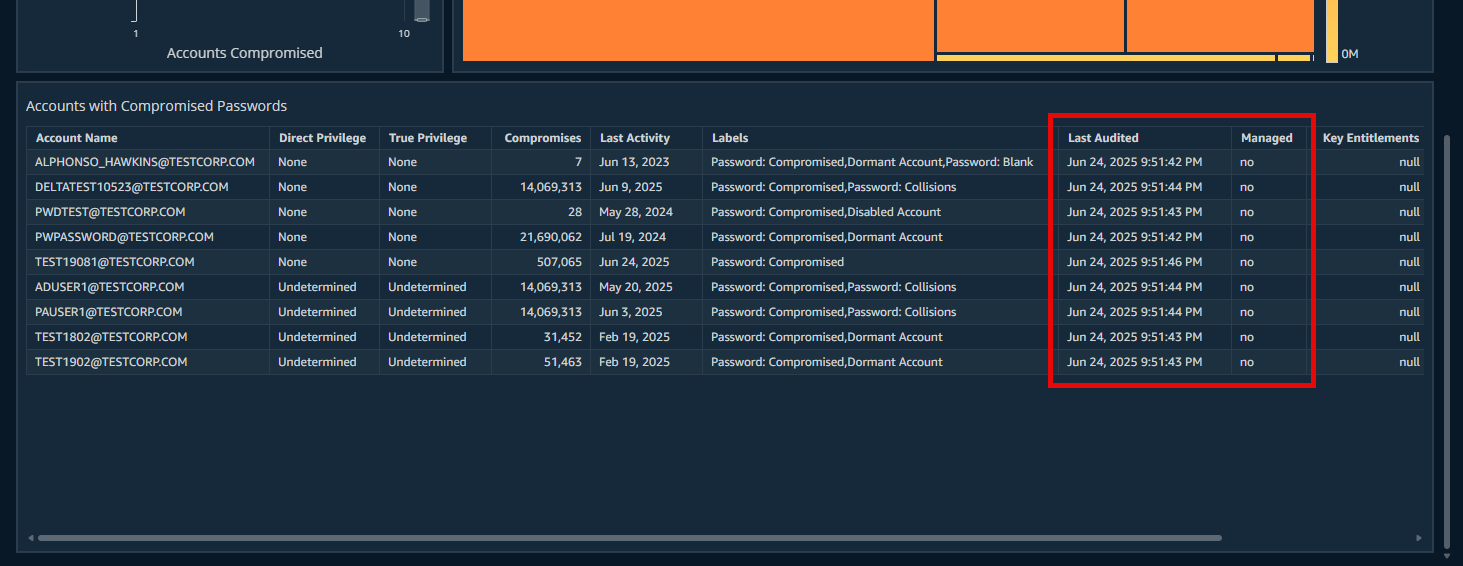
Clarity in password audits
The following reports now include two new columns:
- Blank Passwords
- Compromised Passwords
- Shared Passwords
- Password Health Overview
New Columns:
- Last Audited: Timestamp of the last password audit by Insights Collector.
- Managed: Indicates if the account is managed by Password Safe (Yes/No).
For more information, see Password Integrity reports.
