Endpoint Privilege Management for Linux 25.1.7
December 15, 2025
✨Enhancements
Eventlog rotation is now set to a 8G size
-
Eventlog rotation is now enabled by default and set to 8G. The size cannot be changed. When a fixed size is reached the current event log is renamed with a date/time tag, and a new event log is created with the specified event log name.
Select event logs from the Event Log Database drop-down in the Audit section.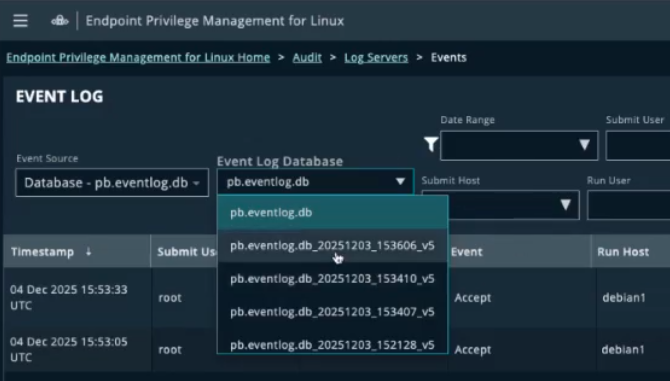
-
Name format for event logs
When an eventlog using the old name format (pre-v25.1.7) rotates, the new naming convention is applied. If the rotated eventlog has the pre-25.1.7 schema, it will be migrated after the rotation.
For more information, see View event details.
Updates to EPM-L Settings defaults
- policyacktimeout
The keyword policyacktimeout is now changeable and has a default of 30 seconds. - Added allowsni to ssloption
The setting ssloptions now allows a new value, allowsni, that can be added to the existing “ssloptions requiressl sslfirst allowsni”. When present, pbrun includes the SNI extension in TLS Client Hello packets and facilitates the traffic through proxies requiring SNI.
allowsni is optional.
Splunk enhancements
Unset (comment out) invalid Splunk and ELK configurations in pb.settings
When editing “splunk*” keywords in EPM-L Settings, the keywords are now validated and not used if the entry is invalid. A notification displays when the entry is not valid.
If sending the events to Splunk or ElasticSearch fails due to misconfiguration of the corresponding settings, the settings are commented out in pb.settings to prevent repeated failures.
Role-Based policy (RBP) transactions and change management
Transaction workflows now run more reliably with improved clarity. Enjoy a better experience with helpful confirmation pop-ups and easier navigation.
We’ve strengthened change management to keep everything consistent across environments.
For more information, see Role-Based Policy transactions.
Improvements to database performance
Updates to the eventlog table schema greatly improve the search performance.
Improvements on keystroke event filtering
The filterable columns in event log records for “keystroke” events are now fully populated. This means you can easily filter and find keystroke events, making your event searches faster and more efficient.
Issues resolved
| Description |
|---|
| The warning message, ypcat is not in the path, will no longer be displayed when installing endpoint packages. |
| The field uniqueid in the eventlog record is always unique on a specific host. However, in certain rare situations uniqueid was the same across different machines. |
| Moving and unlinking files is now properly blocked on all RedHat versions, when using the ACA rule in the policy to block “unlink” (mv) of a file, example: “aca('file','/root/file','all!write!unlink','protect shadow');” |
| Fixed an issue with closed file descriptors causing seek and audit problems. |
| When ACA is requested to exec a script, the interpreter shell in the script (“#!<shell>”) is now also run through the ACA policy. |
| When rbptransactions is enabled and a transaction is not committed yet, the role matching will no longer use the uncommitted changes into consideration. |
| The role-based policy entitlement reporting, pbrun -e, now shows commands that include a ‘%’ |
