Identity Security Insights 25.11
November 4, 2025
🆕 New features
New reports in Security Frameworks
Two new reports are now available in the Security Frameworks section, giving security teams deeper visibility into compliance and threat activity. These reports will also be made accessible from the Dashboard drop-down on the Insights homepage, providing quick entry points for ongoing monitoring.
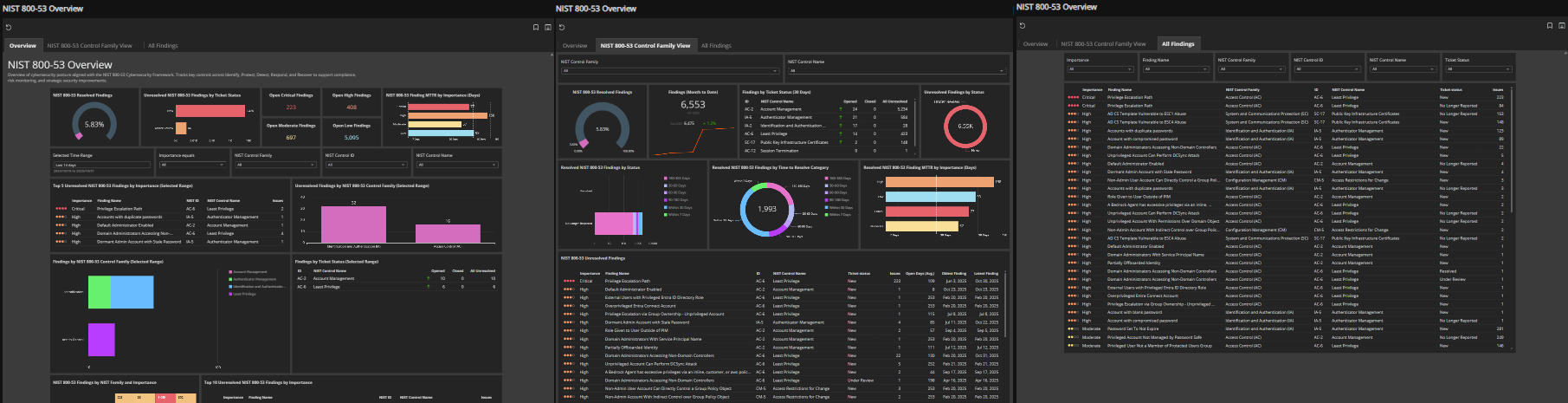
NIST 800-53 overview
This report gives you a clear view of how your organization measures up against the NIST 800-53 Cybersecurity Framework. Developed by the U.S. National Institute of Standards and Technology, this framework provides widely adopted security and privacy controls to help organizations manage risk. The report covers 20 control families (such as Access Control, Risk Assessment, Incident Response), which are tactical domains grouping specific controls – essentially the “how” you implement security and privacy measures. Where findings exist, you can drill into those families to see gaps and areas needing attention.
Tabs
- Overview: High-level view of control coverage and posture trends, with filters for date ranges, control categories, and importance levels.
- Control Family View: Analyze individual control families for detailed coverage and performance.
- All Findings: A filterable list of findings. Many datapoints from other tabs link directly here, and you can navigate to related detection and recommendation pages for deeper investigation.
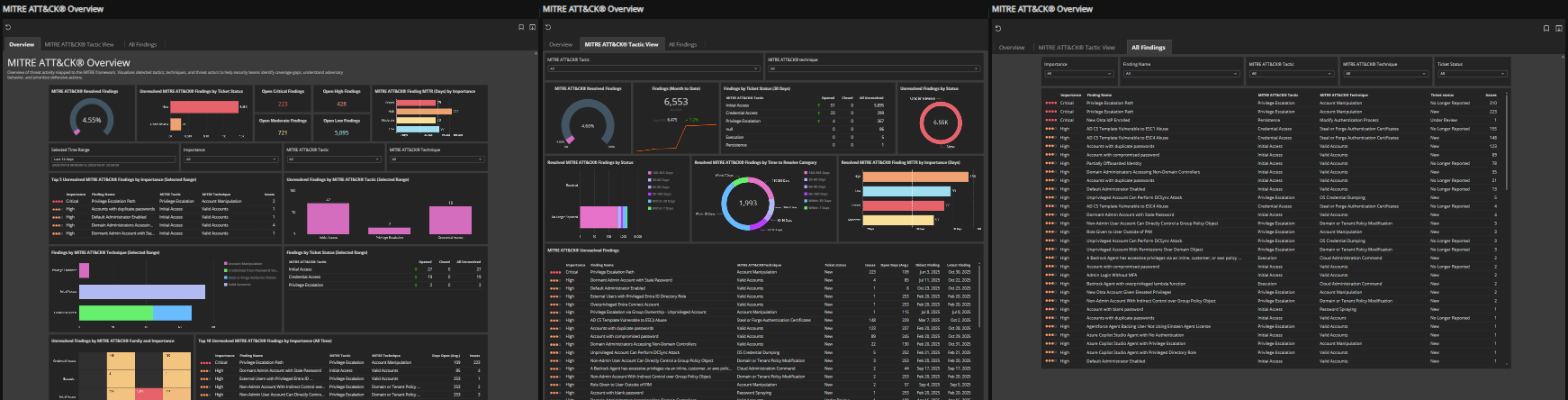
MITRE ATT&CK® overview
This report visualizes detected threat activity mapped to the MITRE ATT&CK® framework, helping you identify coverage gaps, understand adversary behavior, and priorities defensive actions.
Tabs
- Overview: High-level distribution of tactics, techniques, and threat actors, with filters for date ranges, severity, and tactic/technique selection.
- Tactic View: Drill into individual MITRE tactics to see associated techniques and threat actor activity.
- All Findings: A filterable list of findings. Many datapoints from other tabs link directly here for focused analysis.
GitHub Secrets and escalation entitlements in action
We’ve enhanced GitHub entitlement coverage to improve visibility into secrets and privilege escalation risks for the GitHub provider so that it can quickly be identified of who can access secrets and assess escalation risk across domains.
- Escalation entitlements
Highlights scenarios where exposed AWS IAM credentials (Access Key ID + Secret Key) in GitHub code could allow a member to escalate privileges to the associated IAM User. Insights surfaces an ML-calculated Privilege Score for that IAM User, showing effective permissions across all IAM policies (custom and AWS-managed). - Secret entitlements
Represents secrets detected in GitHub repositories via GitHub Code Scanning alerts. These are credentials or tokens embedded in code that could be accessed by GitHub members.
Each secret is displayed with a prefix:
Secret in code ({status}, {resolution_reason}: {type} at {url}) - status: Current state of the alert (e.g., open, closed, resolved).
- resolution_reason: Why the customer resolved the alert (e.g., false positive, revoked). Blank for untriaged secrets.
- type: Type of secret (e.g., AWS Access Key, Azure DevOps PAT, API Token).
- url: Link to the GitHub secret scanning alert.
Example of Resolved secret:
Secret in code (resolved, revoked): Application API Token at <https://github.com/ExampleOrg/sample-app/security/secret-scanning/1>Viewing details
To explore these details, go to Entitlements, filter by Provider = GitHub, then focus on Secrets or Escalation.
- Selecting a secrets entitlement opens the side panel, which shows all other GitHub members who have access. For most secrets, privilege will display as “Undetermined” unless an escalation path exists.
- Clicking a member takes you to their Accounts page, where you can drill into Entitlements to view:
- All GitHub Code Scanning Alert secrets that member can access.
- Any linked AWS IAM Users for escalation mapping across domains.
- Clicking a member takes you to their Accounts page, where you can drill into Entitlements to view:


