Identity Security Insights 25.08.1
August 21, 2025
🆕 New features
Added Google Workspace to Google Connector
The Google Connector now supports Google Workspace, enabling organizations to ingest identity data from all Workspace account types directly into Insights. This enhancement gives teams stronger visibility and a more complete understanding of their identity landscape.
A new drop-down menu in the Google Connector setup allows you to select Workspace as an option. Whether you're configuring a new connector or updating an existing one via the Settings area, the setup guide outlines the required read-only scopes and additional steps to complete the configuration.
At this time, only account data is surfaced. Support for entitlements will be introduced in a future update.
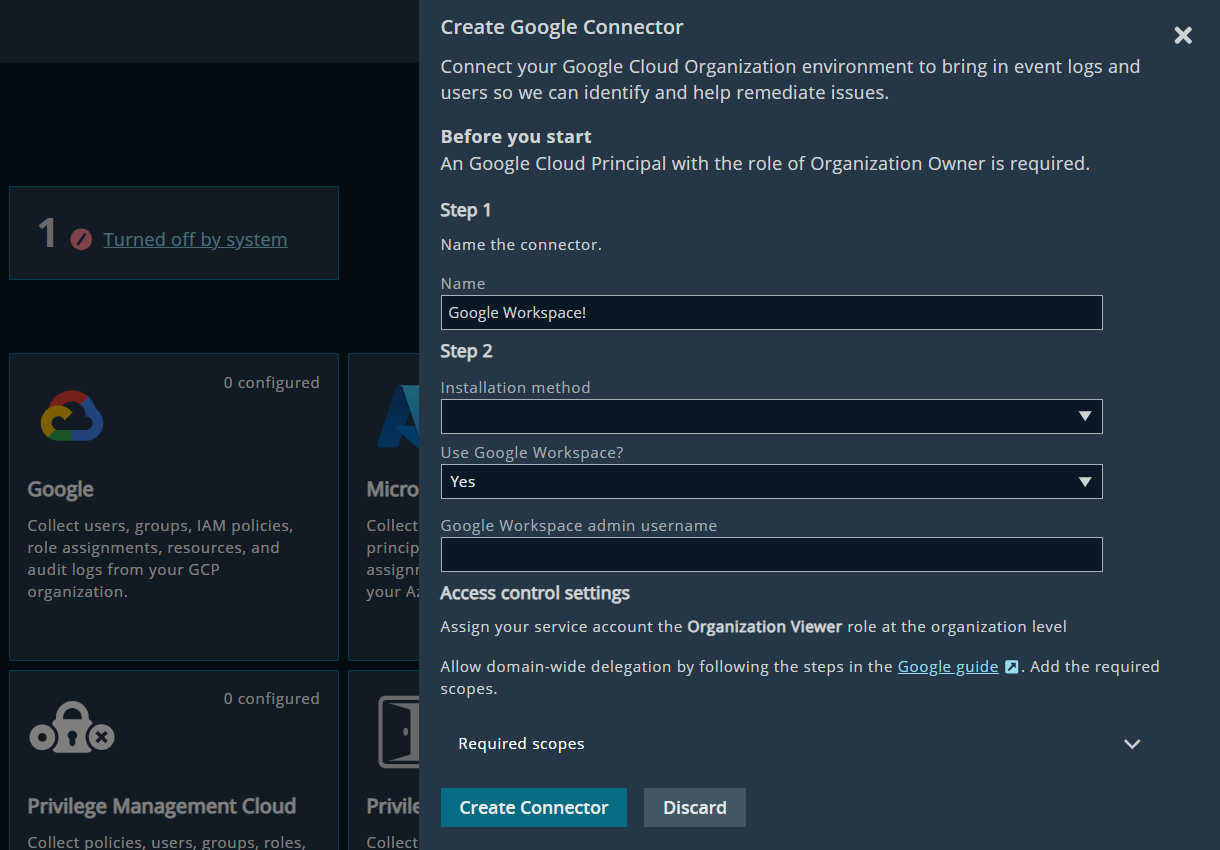
Surfacing AWS Secrets Manager Access
Access to AWS Secrets Manager Secrets is now surfaced as Entitlements. This enhancement enables visibility into which accounts – across IAM Users, IAM Roles, and AWS Identity Center Users – can read secrets, improving posture analysis and incident response workflows.
Key Enhancements
Entitlement Types
| Type | Description |
|---|---|
| Secret | A newly introduced entitlement type that identifies when IAM Users or IAM Roles can read a secret. Example: Read: : arn:aws:secretsmanager:us-east-1:123456789012:secret:example-secret |
| Escalation | An existing entitlement type, now extended to include cases where AWS Identity Center Users can access a secret via an associated IAM Role. (Select Escalation entitlements within the Entitlements Details grid.) |
Graph Visualizations
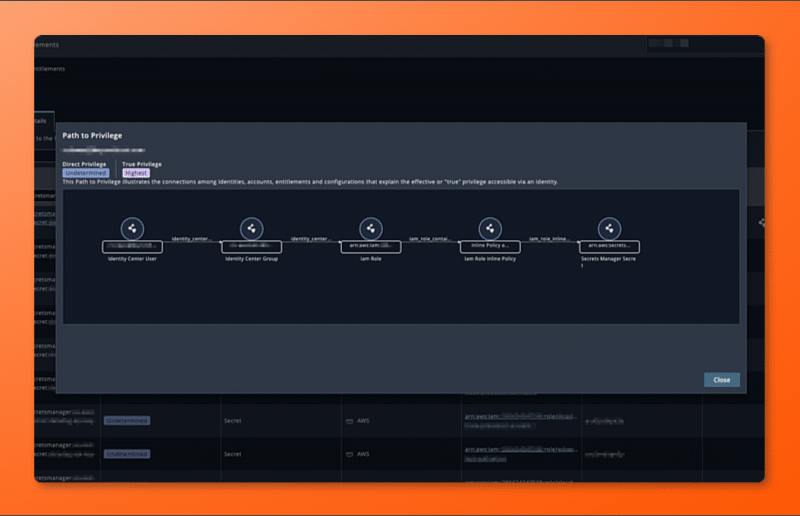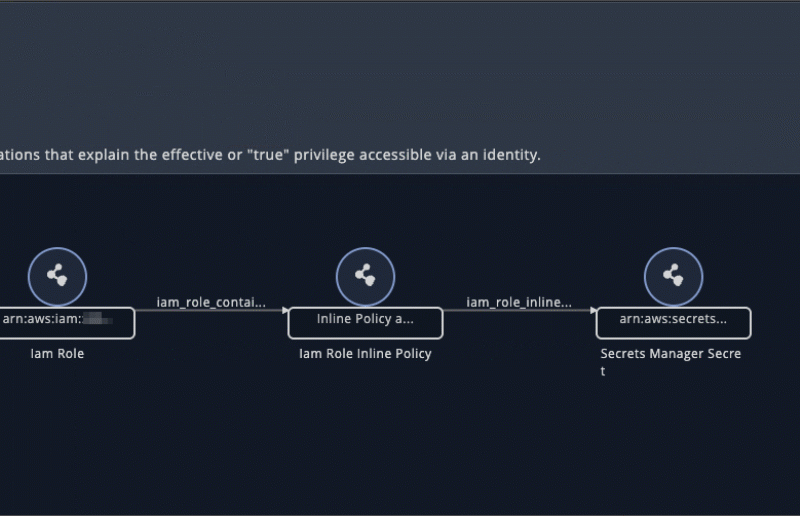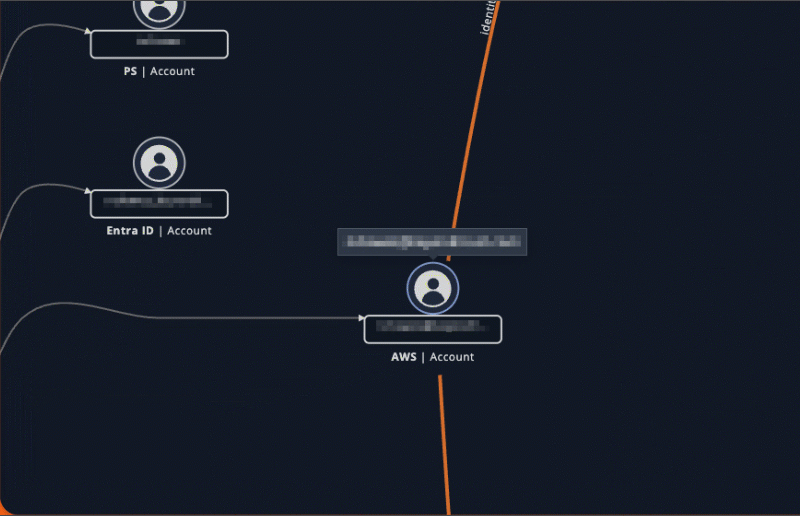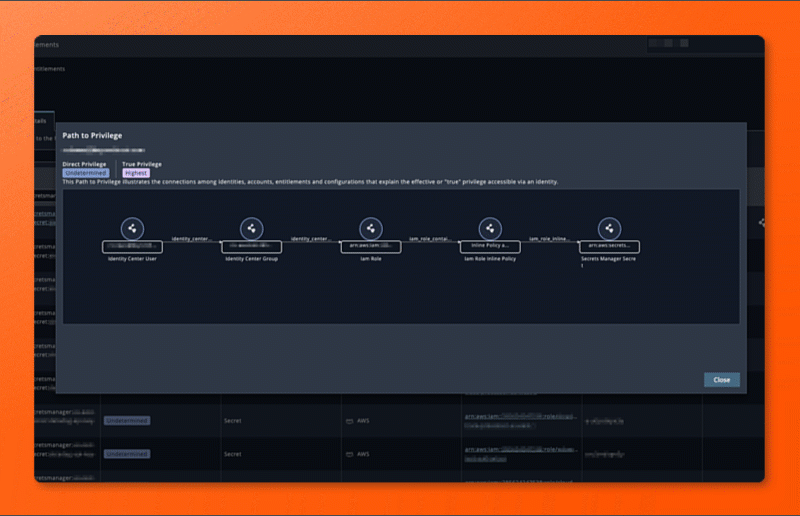
- The True Privilege Graph now shows paths to Secrets for AWS Identity Center Users.
- In the Entitlements page, Escalation paths are selectable when the starting node is an AWS Identity Center User.
Conditional Logic Handling
Entitlements are surfaced when:
- No condition is present (null)
- A supported condition type is used (all except ResourceTag)
All other condition types are included, but not fully evaluated. This means entitlements may still appear even if access is restricted – leading to potential false positives. Support for deeper conditional logic is planned for a future release.
User Journey
- Posture: Overly Broad Secret Access
- Go to the Entitlements Summary page and search for arn:aws:secretsmanager: in the Name column.
- Secret type: Shows IAM Users and IAM Roles with access.
- Escalation type: Shows AWS Identity Center Users with access.
- The Accounts column shows how many identities have access – useful for spotting secrets with broad accessibility.
- Go to the Entitlements Summary page and search for arn:aws:secretsmanager: in the Name column.
- View Who Can Access a Specific Secret
Enter the full ARN of the secret in the Name field on the Entitlements Details tab. This will display all accounts with access across both entitlement types. - Incident Response: Blast Radius
If an identity or account is compromised, go to the corresponding Identity or Account page, search for "arn:aws:secretsmanager:" on the Entitlements tab, and filter by both Entitlement types: Secret and Escalation.
Sumo Logic Webhook Integration
Insights now includes a dedicated Sumo Logic Webhook tile. You can configure it to automatically forward detection events and manually send recommendations to your Sumo Logic environment.
Sumo Logic is a cloud-native analytics platform that helps teams monitor, investigate, and visualize data. We provide all the setup details needed – both in Insights and in Sumo Logic – to get you up and running quickly.