Identity Security Insights 25.05.1
May 20, 2025
🆕 New features
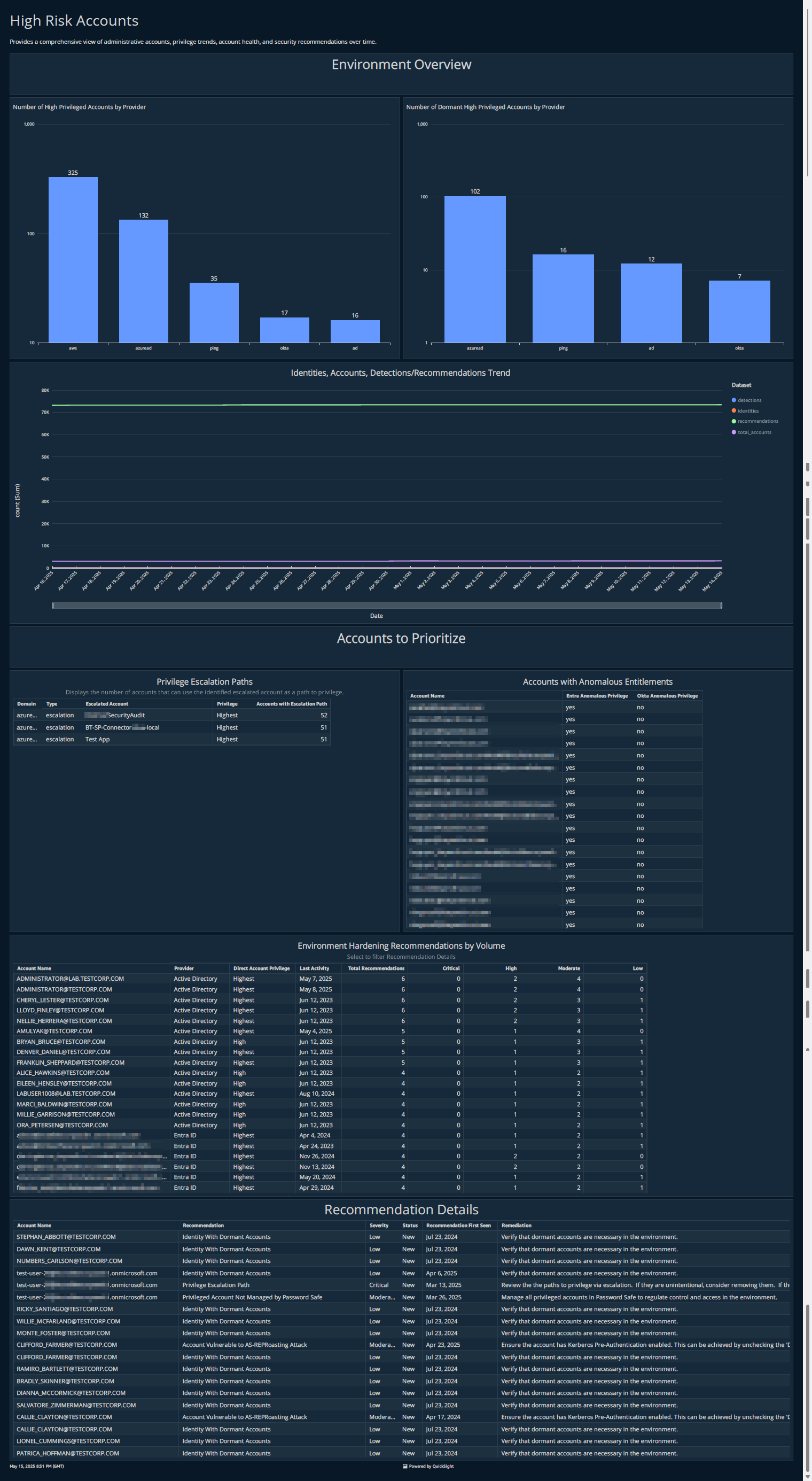
New dashboard: High Risk Accounts
A new High Risk Accounts dashboard is now available from the Home page dropdown and in the Reporting > Dashboards section.
This dashboard provides a focused, visual summary of identity and access risks across your environment. It highlights key areas such as:
- Privileged Account Distribution across identity providers
- Dormant High-Privilege Accounts that may pose security risks
- Privilege Escalation Paths showing how access can be abused
- Anomalous Entitlements across platforms like Entra ID and Okta
- Environment Hardening Recommendations prioritized by severity
The dashboard also includes an interactive triage experience: selecting an account from the recommendations view filters the detailed triage panel, helping teams investigate and take informed action more efficiently.
AWS entitlements overhaul: Introducing permission-based analysis
We’ve introduced a new “Permission” entitlement type for AWS, powered by novel privilege scoring technology that analyzes and ranks IAM policies based on the level of access they grant. This helps identify users and roles with high-impact permissions, making it easier to assess and prioritize risk.
The examples below illustrate the different types of IAM policies and scenarios now supported such as AWS-managed policies, customer-managed policies, inline policies, and assume role permissions. All of these are surfaced under the unified “Permission” entitlement type.
| Policy type | Description |
|---|---|
| AWS Managed Policy | Permissions granted via AWS-managed policies attached to users, groups, or roles (including Identity Center permission sets). Example: arn:aws:iam::aws:policy/AWSManagedPolicy |
| Customer Managed Policy | Permissions granted through customer-created IAM policies. Example: arn:aws:iam::123456789012:policy/CustomPolicy |
| Inline Policies | Permissions defined directly within an IAM user, IAM group, or IAM role. These include inline policies in IAM roles that are managed by AWS Identity Center (via Permission Sets). Example: Inline Policy arn:aws:iam::123456789012:user/User_01 Inline Policy arn:aws:iam::123456789012:role/Role_01 |
| Assume Role Permissions | Indicates the ability to assume roles based on permissions granted via policies. Also surfaces even when the sts:AssumeRole action is granted implicitly through a wildcard (e.g., "Action": "*"). Example: sts:AssumeRole in : arn:aws:iam::aws:policy/AWSManagedPolicy sts:AssumeRole in : arn:aws:iam::123456789012:policy/CustomerPolicy sts:AssumeRole in : Inline Policy arn:aws:iam::123456789012:user/User_01 sts:AssumeRole in : Inline Policy arn:aws:iam::123456789012:role/aws-reserved/sso.amazonaws.com/AWSReservedSSO_PermissionSet... |
As part of this update, we’ve removed the Group member entitlement type, which previously surfaced AWS Identity Center group memberships associated with Identity Center users. This change reflects our shift toward a more granular and policy-based entitlement model, focusing on permissions derived from IAM policies and assume role capabilities.
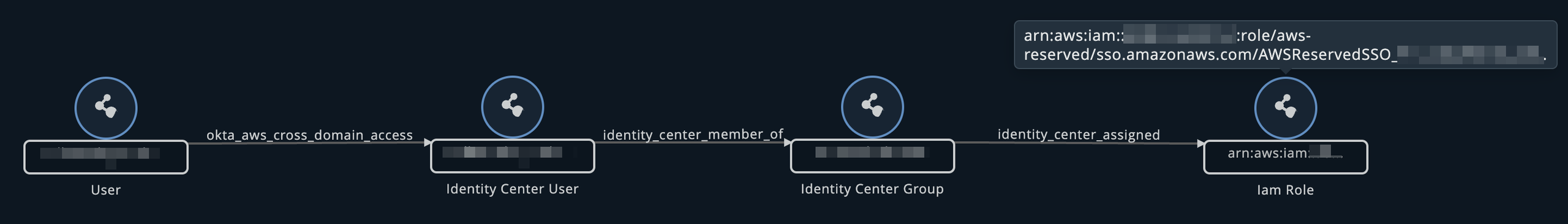
New Okta escalation entitlements: Cross-Domain access visibility
A new “Escalation” entitlement type is now available to surface Okta to AWS cross-domain access enabled through SCIM provisioning in AWS Identity Center. This update provides visibility into which AWS accounts and IAM roles an Okta user can access, helping to triage detections and understand privilege escalation paths more effectively.
Insights now shows:
- The True Privilege of the Okta user, scored based on the destination IAM role.
- The Identity Center group that facilitates the access path.
New entitlement types
| Name prefix | Description |
|---|---|
| Cross-domain | Indicates that an Okta user has access to an AWS IAM role via SCIM provisioning through AWS Identity Center. The entitlement reflects the privilege level of the destination IAM role. Example: Cross-domain arn:aws:iam::123456789012:role/aws-reserved/sso.amazonaws.com/AWSReservedSSOPermissionSet... |
| Cross-domain lateral | Used when the Okta user’s Direct Privilege in Okta is equal to or lower than their True Privilege in AWS. Highlights lateral movement potential across domains. Cross-domain lateral arn:aws:iam::123456789012:role/aws-reserved/sso.amazonaws.com/AWSReservedSSOPermissionSet... |
✨ Enhancements
Password audits now run daily
The Insights Collector now performs password audits daily, allowing faster identification of password-related issues such as compromised, blank, or duplicate passwords.
When these issues are addressed, the changes will be reflected in the application the next day, with related labels automatically removed.
Report Renamed: “Security Analysis Overview” is now “Identity Threats”
A change in forecast calls for a clearer name. The Security Analysis Overview report has been renamed to Identity Threats to better reflect its focus on detection trends, recommendation statuses, and severity insights.
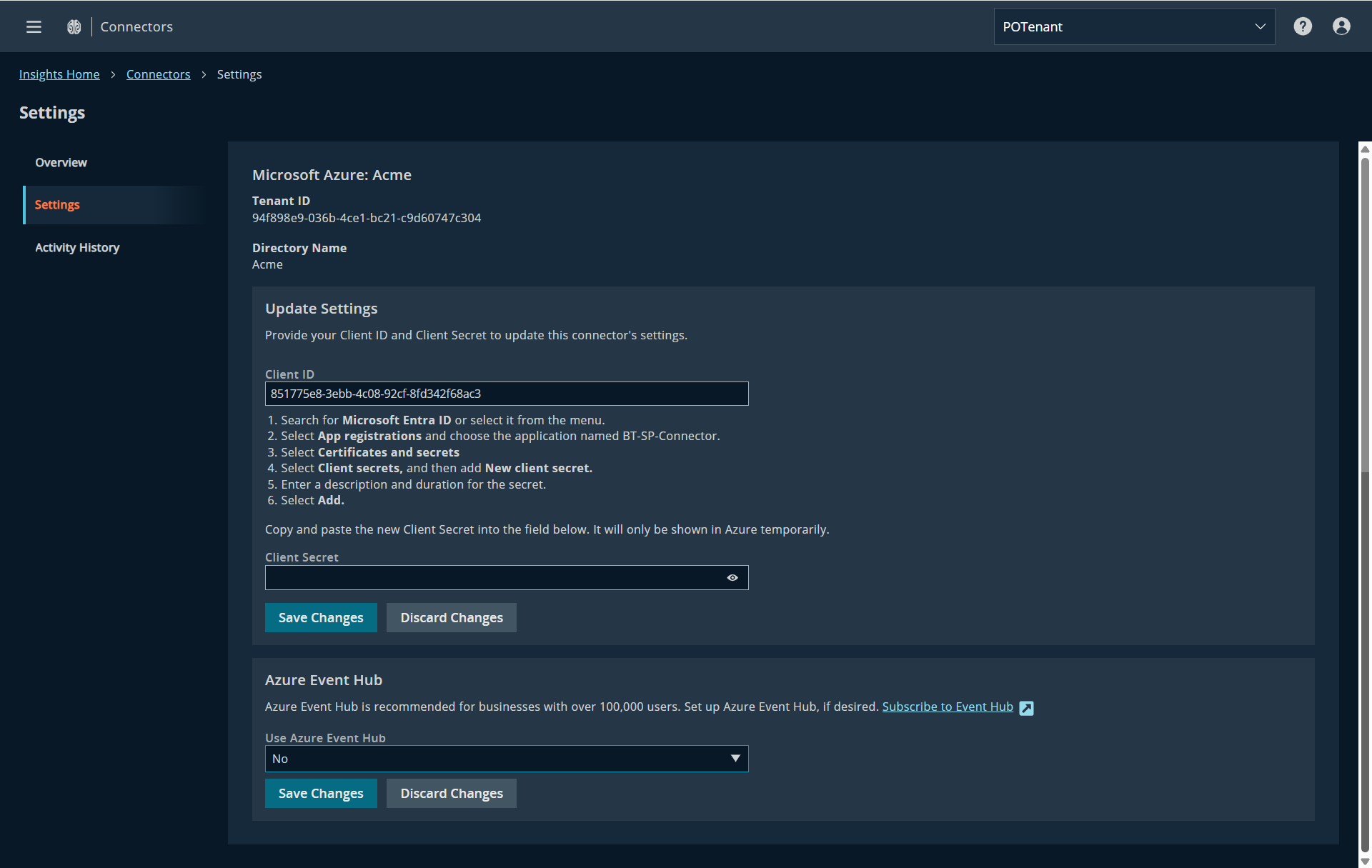
Azure Connector Settings update
The Microsoft Azure Connector Settings page has been updated to improve usability and flexibility.
The configuration form is now split into two sections:
- Update Settings: Manage your Azure credentials (Client ID and Client Secret).
- Azure Event Hub: Configure Event Hub integration independently, without needing to re-enter credentials.
This change simplifies setup - especially for organizations enabling Event Hub after initial connector configuration.