Identity Security Insights 26.01.1
January 20, 2026
✨ Enhancements
Stacked side panels for enhanced context
We’ve enhanced navigation by making side panels stackable, allowing users to open multiple panels without losing their original context.
How it works
- Side panels can now stack on top of one another, so you can view multiple details without leaving the current page.
- Internal links inside side panels now open as additional stacked panels instead of navigating away, across the following pages:
- Identities and Privileges: Identities, Accounts, Entitlements
- Secrets Security: Secrets, Secrets Inventory
- AI Security: AI Agents, Agent Inventory
- Insights: Detections, Recommendations
- Detections and Recommendations findings have been converted into side panels, eliminating the need for separate pages.
Why it matters
This update keeps you in context while you investigate, reducing navigation friction and speeding up exploration of related data.
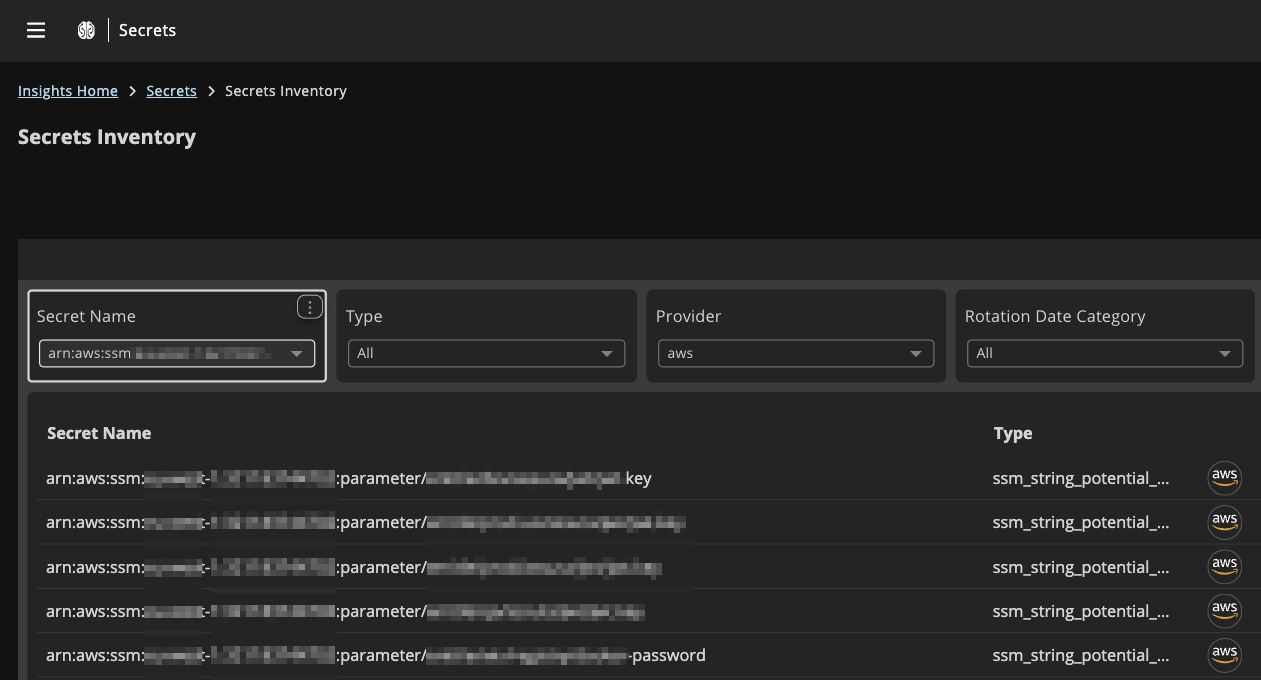
AWS SSM parameter store: Secrets visibility & access analysis
Insights now models AWS Systems Manager (SSM) Parameter Store resources and their access relationships, providing visibility into who can read sensitive configuration and secrets.
SSM coverage highlights
- Parameter visibility: SSM parameters are ingested and classified by type: String, StringList, SecureString.
- Access path mapping: Entitlements show all paths from IAM/Identity Center/Bedrock to SSM parameters.
- Secret identification: Parameters likely to contain secrets are automatically identified.
Where you'll see this
Secrets security: Displays in metrics, visuals, and filtering for sensitive parameter types:
- ssm_string_potential_secret - Plaintext parameters likely to contain secrets.
- ssm_secure_string - Encrypted parameters.
Entitlements: Accounts show SSM parameter access categorized as:
- "Permission" for regular config access (ssm_string).
- "Secret" for sensitive parameter access (ssm_string_potential_secret, ssm_secure_string).
Graph Coverage: Insights adds nodes for SSM parameters and edges mapping access relationships:
- IAMUser/IAMRole/IAMGroup → hasAccess → SSMParameter
- IdentityCenterUser → hasAccess → SSMParameter
- BedrockAgent → hasAccess → SSMParameter
Why it matters
- Insecure storage identification: Find secrets stored as plaintext String/StringList that should be SecureString
- Stale or overexposed secrets: Detect parameters not rotated in over a year and see accessor counts to prioritize risky items
- Complete access visibility: View all direct and indirect access paths to SSM parameters