Identity Security Insights 25.06
June 3, 2025
🆕 New features
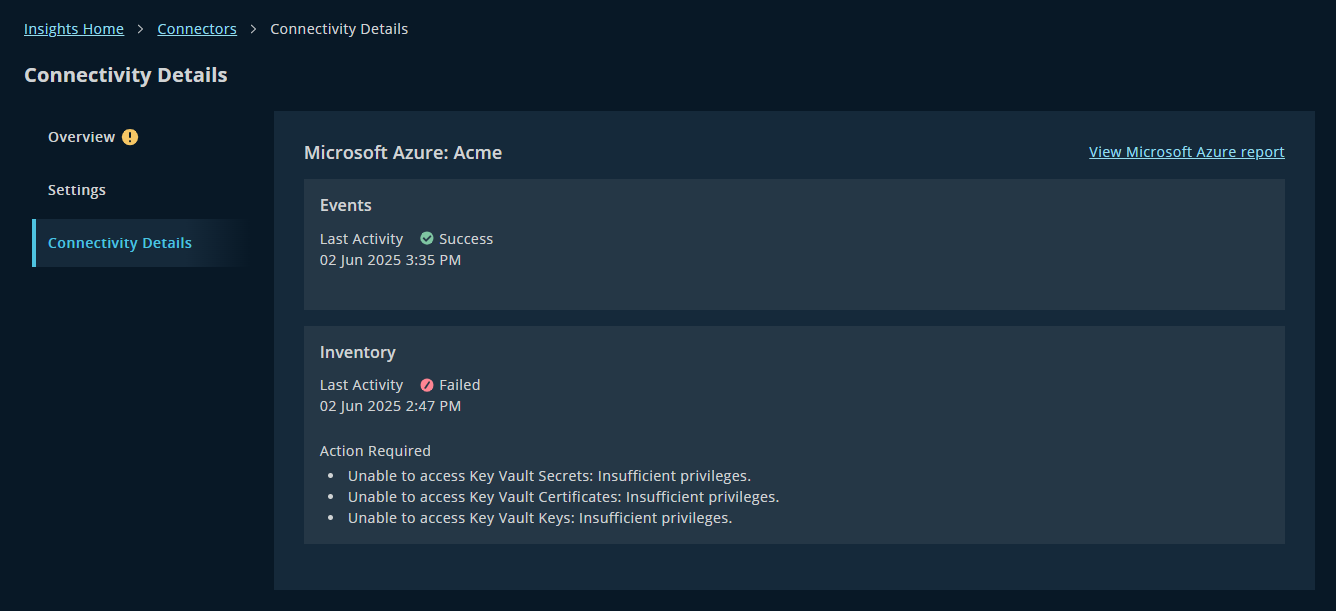
Connectivity Details
We’ve given the Connectors grid and Activity History a new look making it easier to spot what’s working, what’s not, and what needs your attention.
Updated Connectivity Statuses
Four clear statuses added to the Connectivity column:
- Connected: The connector is functioning normally; no action is needed.
- Off: Indicates the connector was either manually disabled or automatically deactivated due to invalid credentials persisting for over a week.
- Pending: Applies to new connectors that have not finished a first event or inventory scan. Additionally, applies to the Insights Collector when no data has yet been received from the on-prem agent after setup.
- Action Required: Customer action is needed to resolve an issue. Clicking this status opens the Overview page, where a banner provides clear guidance.
We’ve retired the Warning and Failed statuses and rolled them into the more actionable Action Required.
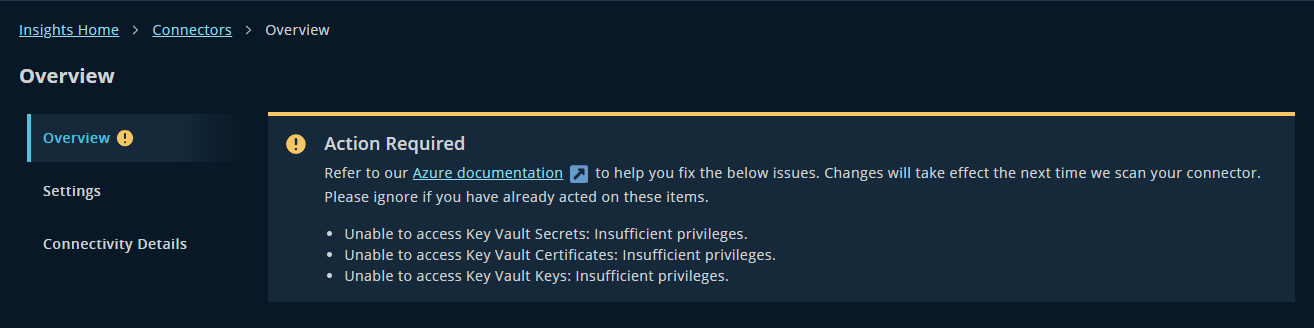
Introducing: Connectivity Details
Say goodbye to the old Activity History grid and hello to Connectivity Details - a cleaner, smarter way to see what’s happening:
- Shows only the latest status for each job type (like Inventory or Events).
- Surfaces issues and next steps right away - no more digging through 30 days of logs.
✨ Enhancements
Azure Entitlements Just Leveled Up
We’ve reimagined how Azure entitlements come to life in Insights – bringing sharper visibility, smarter escalation mapping, and a more accurate view of privilege across your environment.
What’s Changing
Insights environments with an enabled Azure connector will notice some big shifts in entitlement data:
- Increased counts for:
- Directory Roles – including both assigned and eligible roles via PIM
- RBAC Roles – scoped to specific Azure resources
- Escalations – including new paths involving service principals
- Decreased counts for:
- Group Memberships are no longer shown as standalone entitlements. Instead, they are now visualized within the True Privilege Graph and the Path to Privilege escalation graph – only when they contribute to a valid entitlement or escalation, including nested group scenarios.
Entitlement Types and Examples
Permission
These represent direct access assignments
| Description | Example Use Case |
|---|---|
| Directory Role (Assigned) – Surfaces if an Azure account has a Directory Role, including custom roles. | User assigned Global Administrator role |
| Directory Role (Eligible via PIM) – Surfaces if a user or service principal is eligible for a directory role via PIM (Privileged Identity Management). | User eligible for User Administrator role via PIM, requiring request and approval for access |
| RBAC Role – Surfaces if a user or service principal has an RBAC Role, scoped to a specific Azure resource. | User assigned Virtual Machine Contributor role on a specific VM, allowing management of the VM |
| API Permission (Service Principal)– Surfaces if an Azure Service Principal has any API permissions assigned to it. | Service Principal with Microsoft Graph API permission User.ReadWrite.All |
Escalation
These represent potential privilege elevation paths
| Description | Example Use Case |
|---|---|
| Service Principal Escalation – New escalation path involving service principals with API permissions that allow assigning authentication methods. | Service Principal with permissions like UserAuthenticationMethod.ReadWrite.All to assign Temporary Access Passes (TAP) or FIDO2 keys to users |
| Cross-domain Escalation – Considered an escalation when the Okta account has lower privilege than the Azure account it accesses. | Basic Okta user signs into Azure and receives high-privilege role |
Cross-domain (Informational Only)
These are surfaced for visibility only
| Description | Example Use Case |
|---|---|
| Federated Access – Highlights federated access from Okta to Azure. Not considered an escalation. | User signs into Azure using Okta credentials |
