Identity Security Insights 25.08
August 5, 2025
🆕 New features
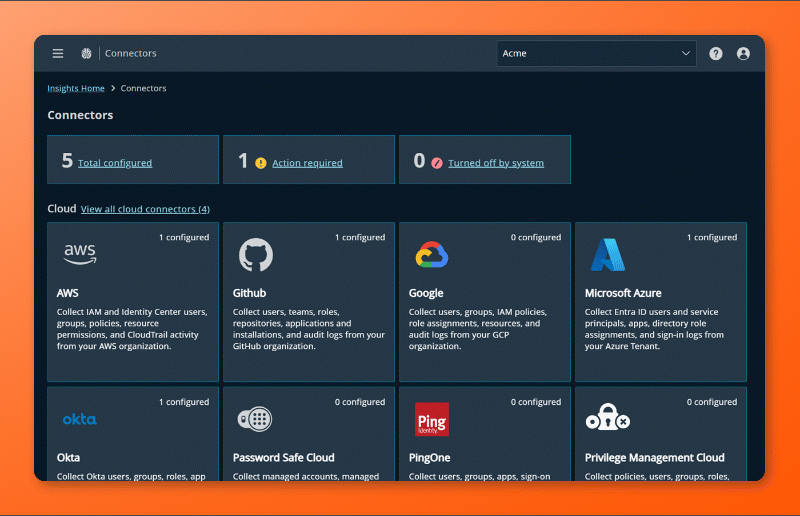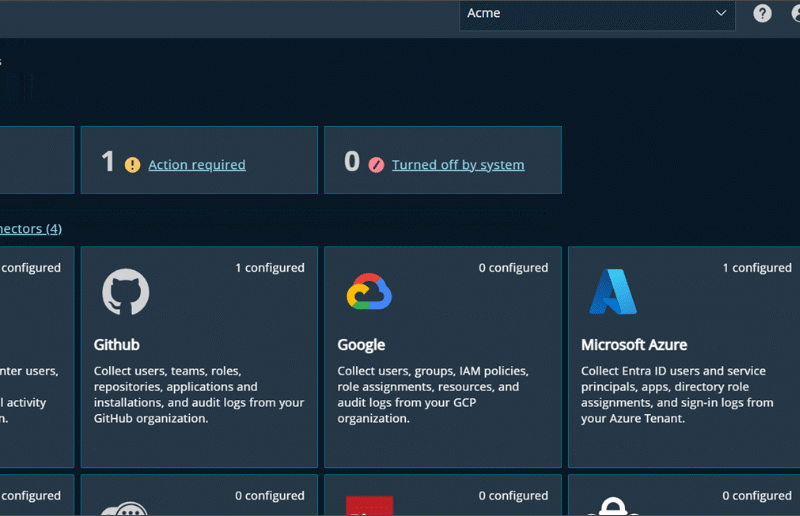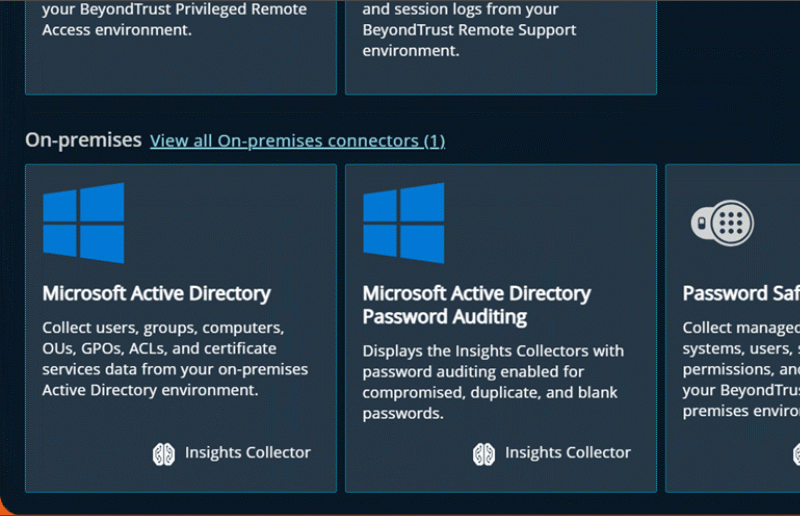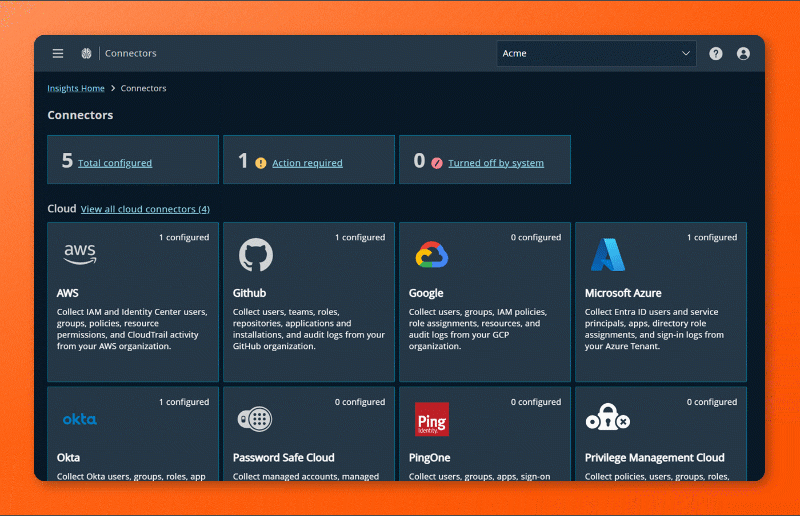
Tile-based layout for the Connectors page
The Connectors page has been reimagined with a new tile-based layout for easier navigation and quicker configuration. Here’s what’s new and how it works:
| Feature Area | Details |
|---|---|
| Overview Tiles | At the top, three summary tiles show:
|
| Connector Grouping | Connectors are grouped into two sections:
|
| Tile Interactions |
|
| Simplified Connector Creation |
|
Optimized Active Directory syncs with Insights Collector
We've identified the optimal timing to achieve both high performance and precise results. The Insights Collector has updated its inventory collection schedule for Microsoft Active Directory data. Full inventory collection now occurs every 24 hours, instead of every 2 hours. Delta changes are still collected and sent to Insights every 2 hours, ensuring no data is missed between full syncs.
This update reduces system load while maintaining accurate, up-to-date visibility across your environment.
Expanded connector permissions and metadata coverage for Azure and GitHub
We have expanded connector permissions and metadata coverage for Azure and GitHub. These updates don’t introduce new insights yet, but they’re key steps toward unlocking future visibility and risk detection.
| Azure: Storage Metadata Access | The Azure connector now uses the user_impersonation permission for Azure Service Management to access storage account metadata, including the allowSharedKeyAccess property. This will enable Insights to identify whether Shared Key authentication is enabled – a setting Microsoft recommends disabling unless explicitly required.Note: This update does not access or collect blob contents – only metadata is collected. |
| Azure: Key Vault Visibility | The Azure connector now uses the Key Vault Reader role at the management group level to collect metadata across all Key Vaults. This includes key lifecycle indicators (e.g., rotation status) and configuration properties such as access controls and network settings. |
| GitHub: Automation Visibility | The GitHub connector now requests two additional permissions: the Actions permission at the repository level and the Self-hosted runners permission at the organization level. These permissions help surface automation components that, if misconfigured or abused, could introduce risk. |
Learn more about Microsoft Azure and GitHub
Expanded AD entitlement coverage
Our latest update surfaces key entitlements across Microsoft identity systems, making privilege paths clear and traceable. This includes:
- Tier0 Group Membership entitlements for accounts with privileged access to core AD infrastructure
- All Group Membership - Includes all custom and non-privileged group memberships.
- Cross-domain Escalation paths from Azure Entra ID to Active Directory with an increase in privilege
- Cross-domain Lateral Escalation paths from Azure Entra ID to Active Directory with the same level of privilege
Each entitlement type is detailed below, with examples to illustrate how access is surfaced and categorized.
Tier0 Group Membership Entitlements
Tier0 entitlements identify accounts with privileged access to core AD infrastructure - such as domain controllers, schema, or critical admin groups. These are surfaced when a user is a member of one of these high-privilege groups.
| Example Tier0 Group Membership Path | Real-World Example |
|---|---|
User → MemberOf → Administrators | [email protected] → MemberOf → [email protected] |
All Group Membership Entitlements
Surfaces all group memberships for AD accounts, including custom and non-privileged groups, to provide complete visibility into group-based access.
| Example Group Membership Path | Real-World Example |
|---|---|
User → MemberOf → Okta_Group | [email protected] → MemberOf → [email protected] |
Cross-Domain Escalation Entitlement Details
Insights now brings visibility to cross-domain escalation paths between Microsoft Active Directory and Microsoft Azure Entra ID. These are categorized as Escalation type entitlements and are prefixed as either:
- Cross-domain - when privilege increases across identity systems.
- Cross-domain Lateral - when privilege remains equal across systems.
| Example Cross-domain Escalation Path | What It Means |
|---|---|
Cross-domain: Azure User (privilege: 3) → SyncedTo → AD User (privilege: 10) → MemberOf → Domain Admins | A lower-privileged Azure user is synced to a higher-privileged AD user, gaining indirect access to Domain Admins. |
Cross-domain Lateral: AD User (privilege: 7) → GenericAll → AD Computer (privilege: 7) → WriteProperty → AD Org Unit | A user moves laterally to a computer account with equal privilege, then modifies an organizational unit. |
